How to Replace Symantec with CrowdStrike

Introduction
This document and video will demonstrate the simple process to replace your Symantec deployment with CrowdStrike’s endpoint protection solution to gain better protection, better performance and better value.
Video
CrowdStrike Overview
CrowdStrike is a proven leader in endpoint security. CrowdStrike has built the first cloud native endpoint security solution as an extensible platform that provides customers with proven NGAV prevention capabilities as well as a number of other modules. This provides customers with complete endpoint protection through a single lightweight agent and CrowdStrike’s event telemetry. Our award winning products are tried, tested and proven to stop breaches.
Migrating your environment from Symantec to CrowdStrike can be done in three simple steps.
- Install CrowdStrike in detect only mode
- Uninstall the Symantec agent
- Enable prevention mode for CrowdStrike
Installation Steps
1. Install CrowdStrike in Detect Only Mode
It is not recommended to install CrowdStrike Falcon® in prevention or blocking mode simultaneous with other AV solutions active on the endpoint. Instead, you can deploy CrowdStrike in detection only mode. This allows you to install CrowdStrike’s next generation AV solution on the endpoints without creating conflict with the existing Symantec solution for a seamless transition.
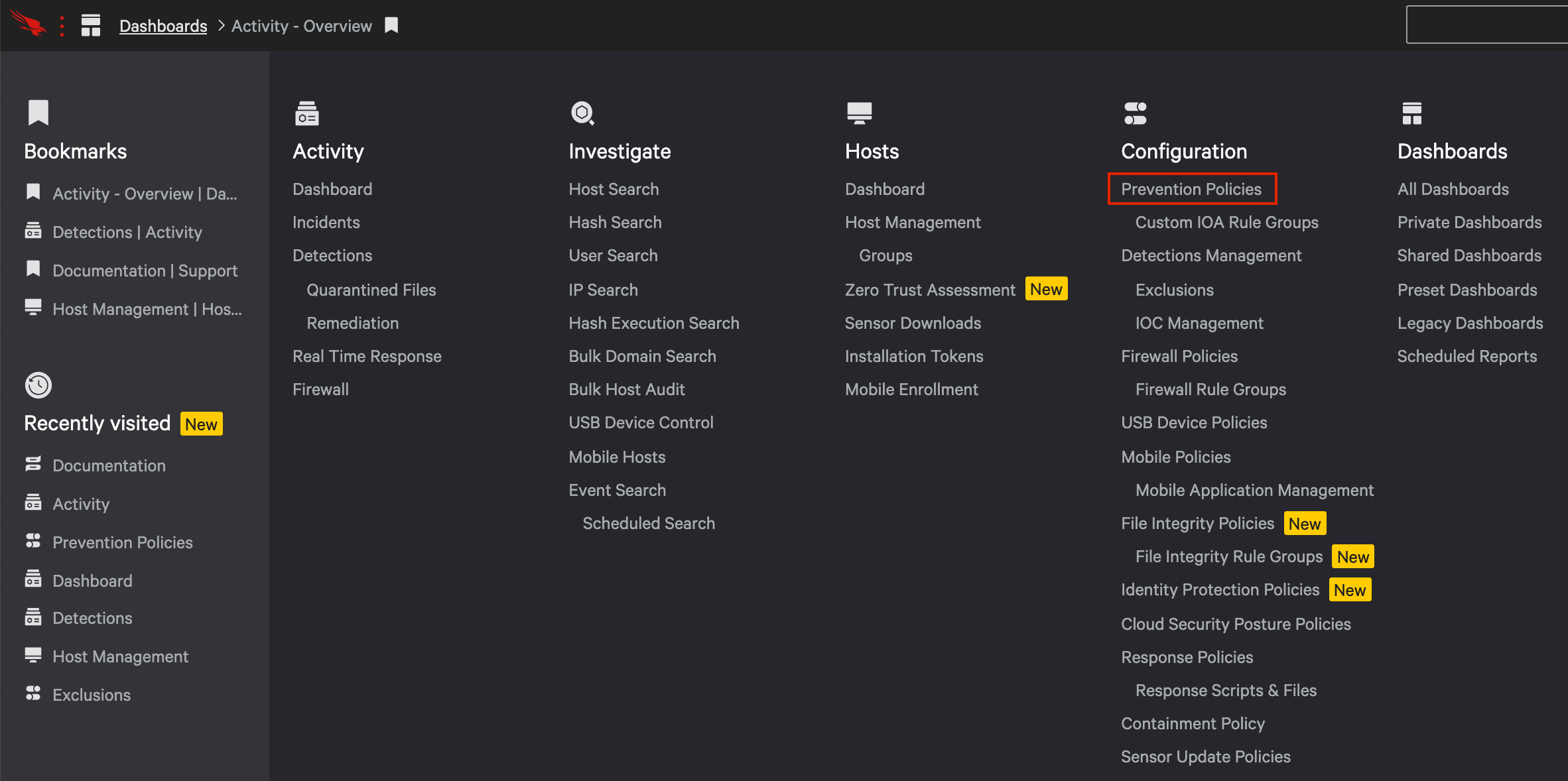
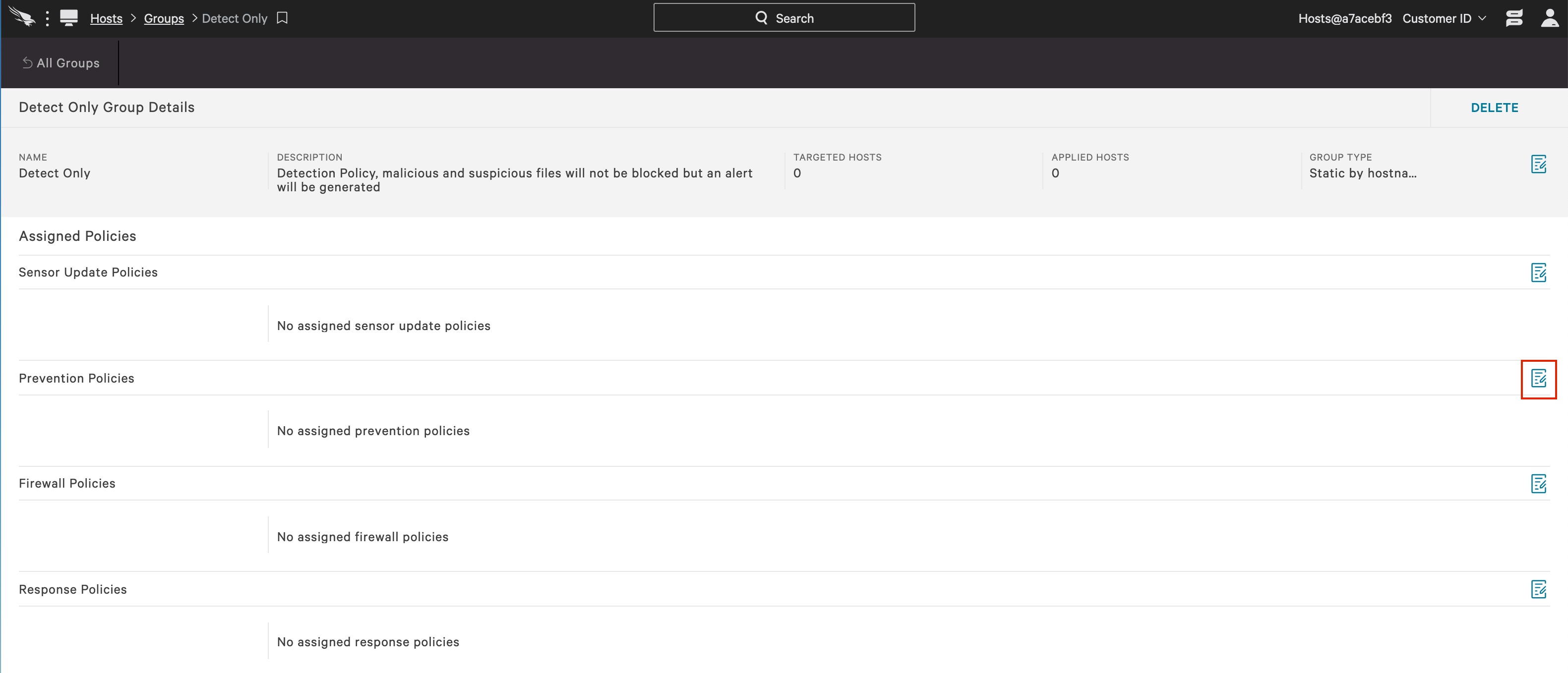
a. In the CrowdStrike UI, go to the Configuration app and chose “Prevention Policies”.
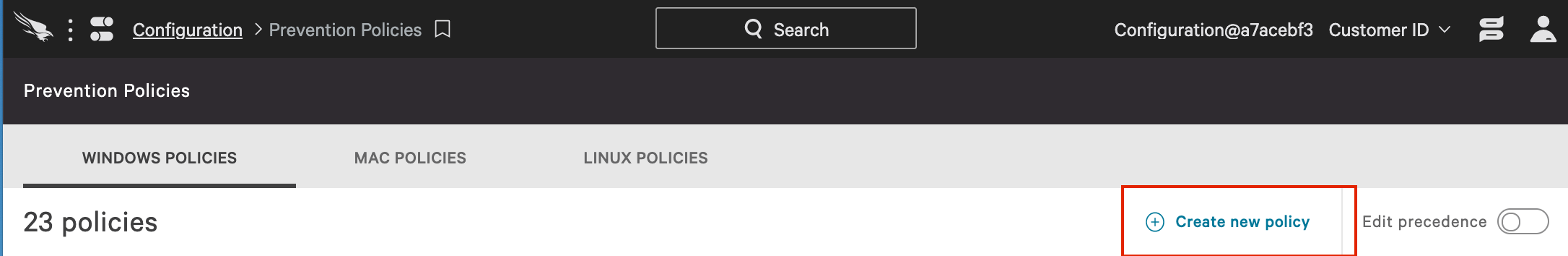
b. Then, click on “Add new policy”.
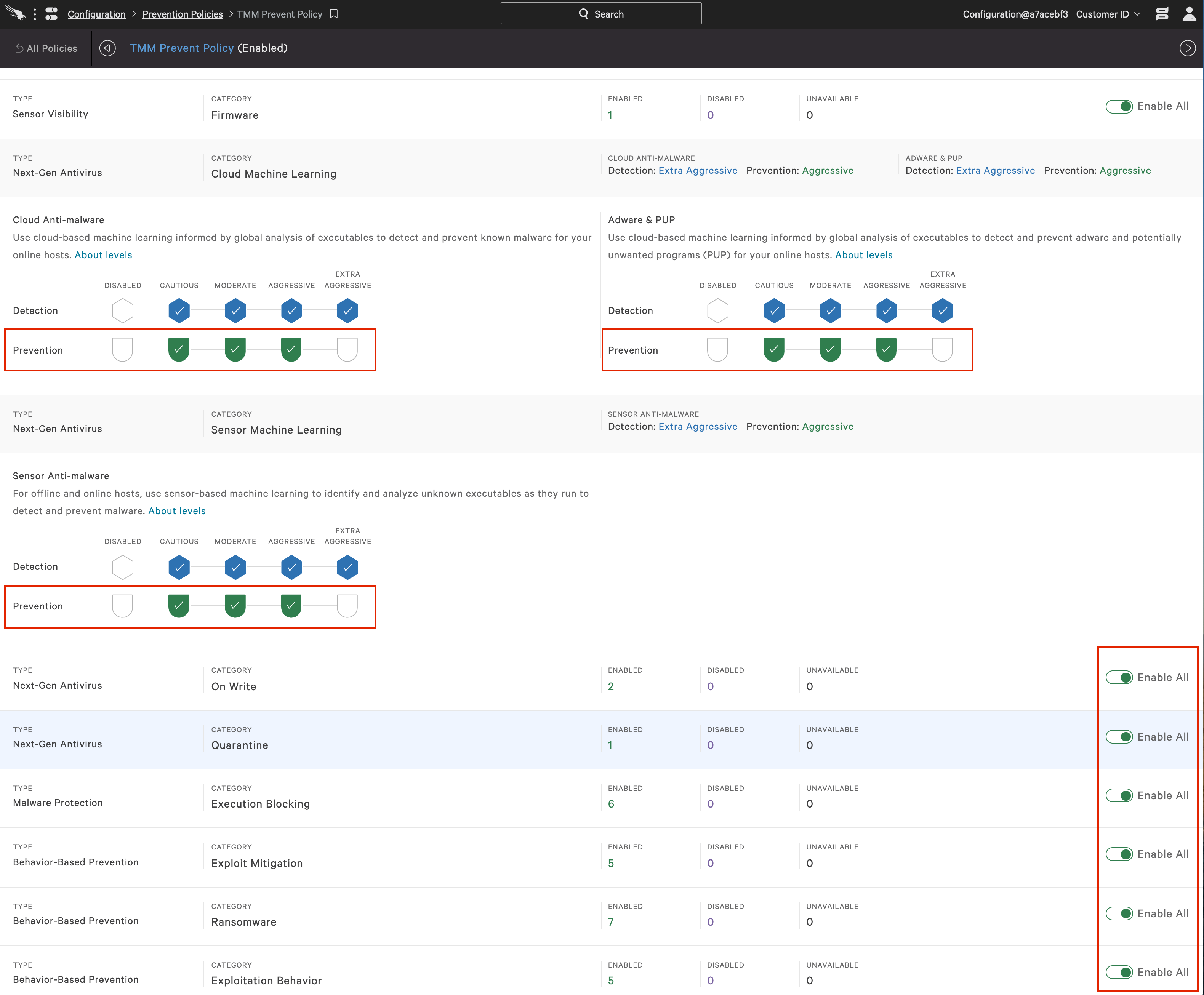
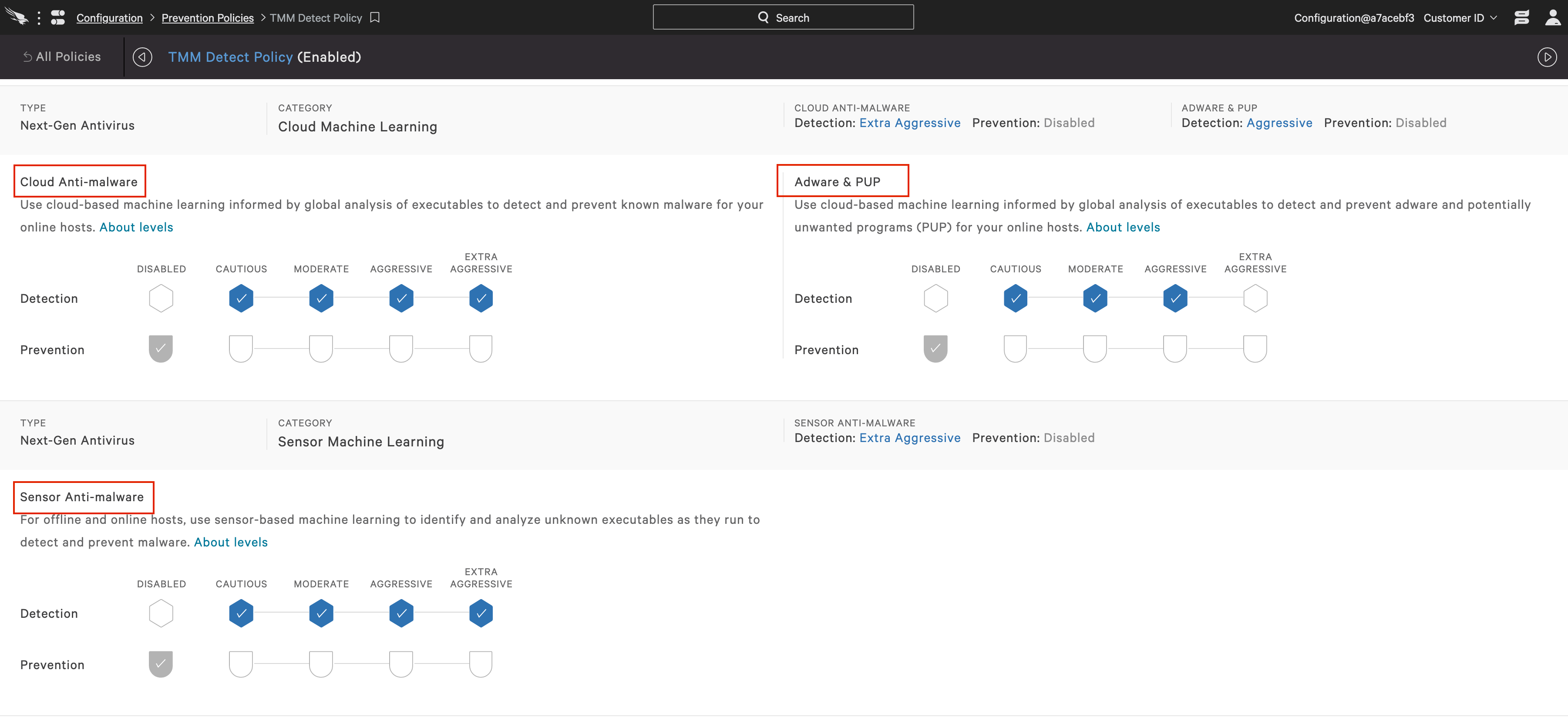
c. After giving the new detection policy a name and description, enable detection mode at your chosen level for next generation antivirus. You can elect a different levels for each of the three options: cloud machine learning, adware & PUP and sensor machine learning. In this case, prevention options should remain disabled.
d. You can then create a group of hosts that should be assigned to that or any policy. In this case, we will want to create a group of systems that should initially receive the detection only policy. Go to the Hosts app and chose “Groups”.
e. Then, click on “Add New Group”.
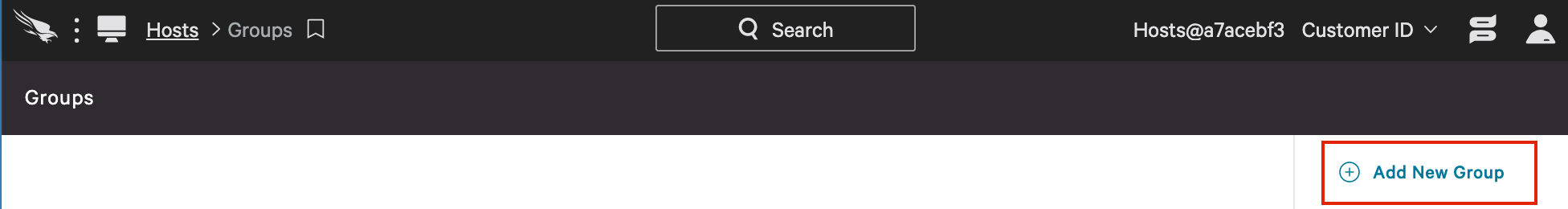
f. After giving the new group a name and description, you can chose to make the group static or dynamic. The hosts in a static group can be manually added and removed. Dynamic groups use filters to automatically sort hosts into groups. You can elect different levels for each of the three options: cloud machine learning, adware & PUP and sensor machine learning.
g. From the policy configuration screen, you can then assign hosts (scroll to the bottom). Then when you’re done adding hosts add the group of newly deployed systems to the detection only policy.
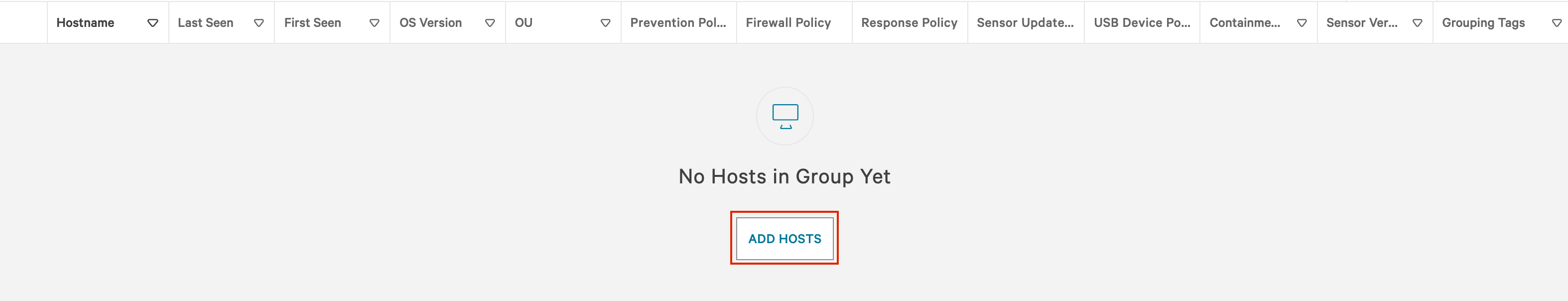
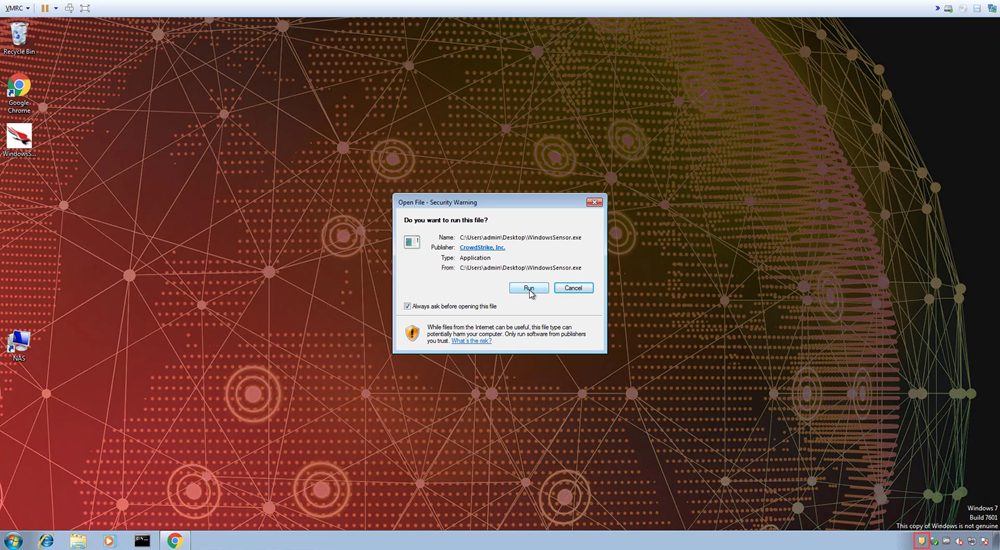
h. With the configuration complete, you are ready to install your first agent. The installer can be run while Symantec is still installed. With the detection only policy, there is no conflict having the two agents installed on the same system.
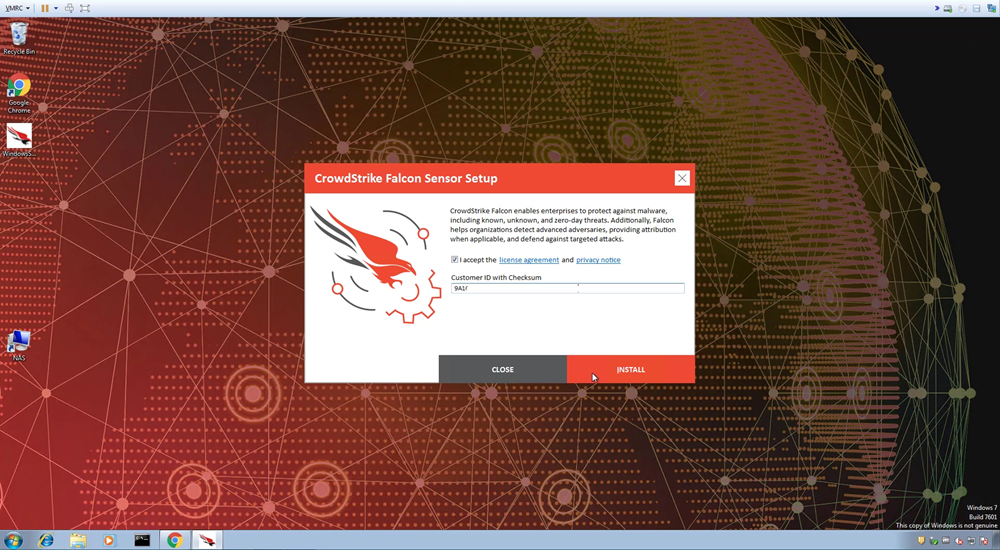
i. The Customer ID has to be entered, but that step can also be automated. The CrowdStrike agent does not require a reboot, complex tuning, or signature updates. It is always up to date and able to protect your endpoints without time consuming system scans.
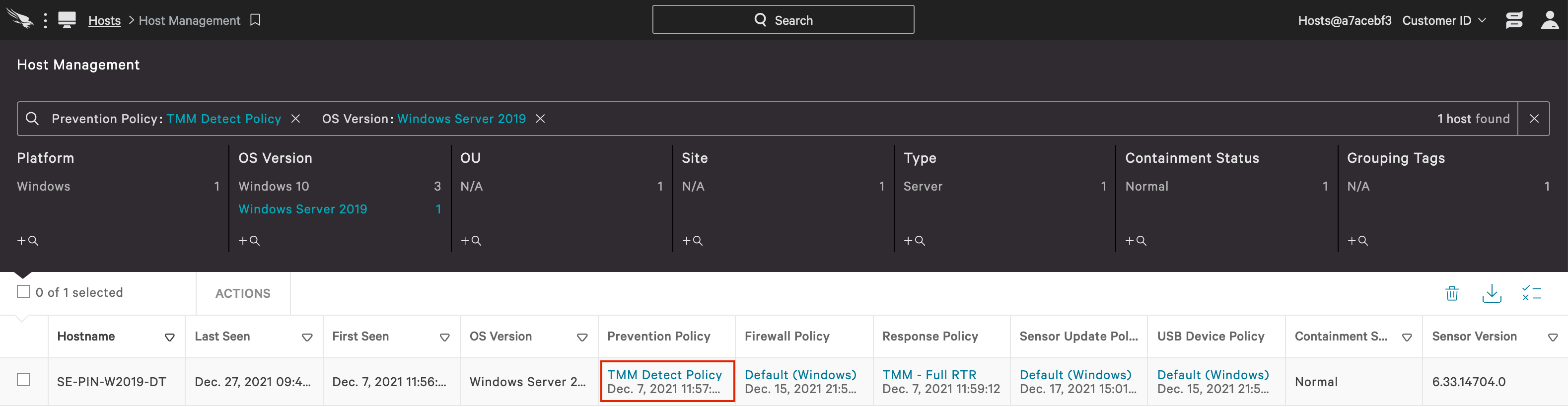
j. After installed, you can return to the Host Management and confirm that the system has been installed with the correct, detection only policy. Even in detection only mode, customers realize the immediate value of having visibility to the events on their endpoints.
2. Uninstall the Symantec Agent
For an organization wide removal, Group Policy, SCCM, or other utilities will likely be used to remove the Symantec agent from the production environment. To remove Symantec from an individual host, utilize the “Add/Remove Programs” feature in the Windows Control Panel. Select the Symantec agent and then select the “uninstall” option that appears above the list of installed programs.
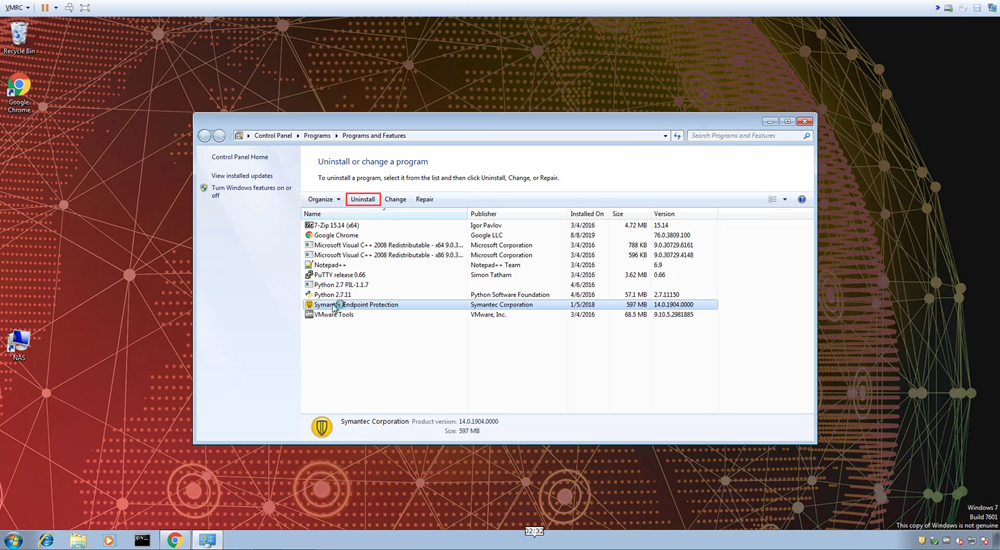
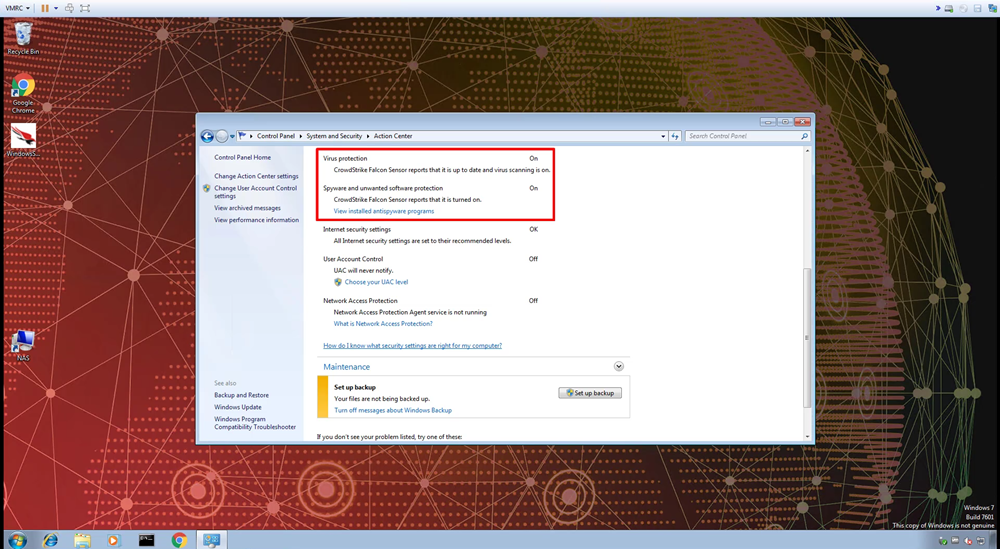
Note: A reboot after uninstall is generally recommended. You can also verify that the uninstall was successful in the Action Center. Open the Action Center and navigate to the Control Panel -> System and Security -> Action Center.
3. Enable Prevention Mode for CrowdStrike
To enable prevention mode, you have two options. You can edit your original, “detection only” policy to turn on preventions for all hosts under that policy. However, many organizations prefer a phased approach. We will walk through the phased approach by migrating systems to a second, prevention enabled policy.
a. We will follow the steps outlined in 1a and 1b to create a new prevention enabled policy. However, for this policy, we will enable prevention for cloud machine learning, adware & PUP and sensor machine learning.
b. There are also options to enable file quarantine and a number of other options including execution blocking and behavioral based preventions. These options can be enabled as desired.
c. After saving and enabling the new policy, create and assign a group of hosts as outlined in steps 1d through 1g.
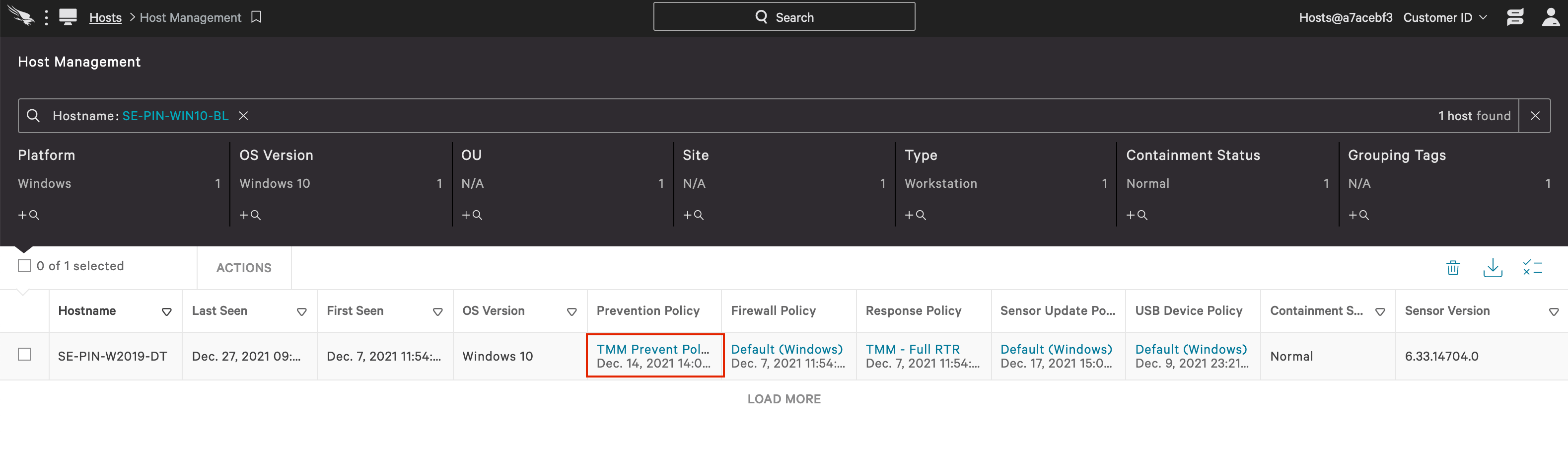
d. Once your system has been moved to the prevention group and policy, you will see the new policy applies in the Host Management app. This system is now protected by CrowdStrike’s proven, next generation antivirus solution.
e. Finally, you can look back to the endpoint and confirm that CrowdStrike Falcon® is now the registered antivirus protection for the system.
Conclusion
In this article we demonstrated a three step process to replace Symantec with CrowdStrike. We first deployed CrowdStrike in detection only mode to run alongside the Symantec agent. Second, we removed the Symantec agent. And finally, we enabled preventions for CrowdStrike.
CrowdStrike’s cloud native platform delivers proven prevention capabilities along with many other modules through one lightweight agent. Not only is it easy to replace Symantec with CrowdStrike, but organizations will ultimately benefit from better protection, better performance and better value.