Know them. Find them. Stop them.
Discover the adversaries targeting your industry.

Adversaries targeting you:

Your Personalized Threat Landscape
Today’s threat actors are smarter, more sophisticated, and more well resourced than they have ever been. Only by understanding them can you remain one step ahead of today’s increasingly relentless adversaries.
Featured Adversaries
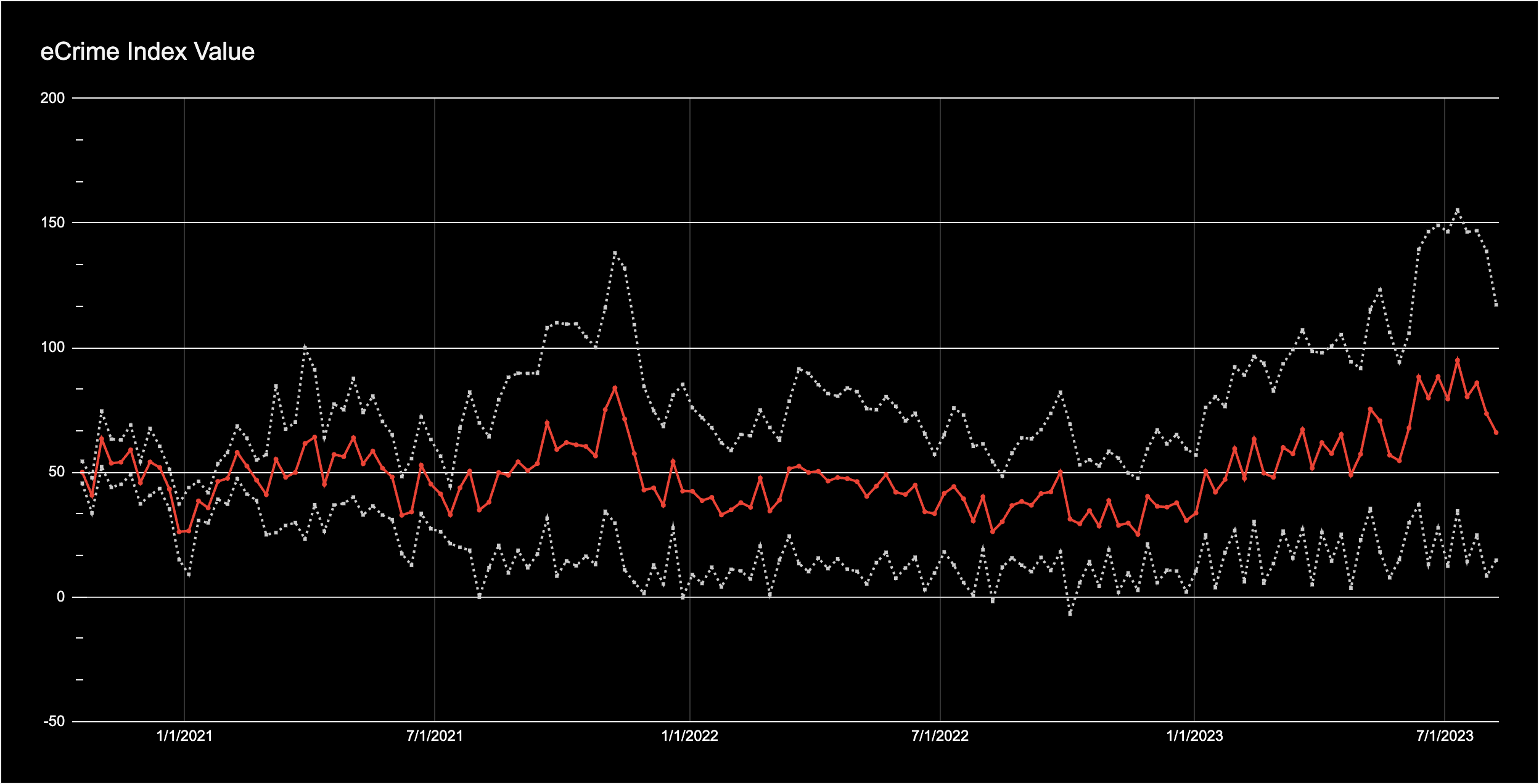
eCrime Index (ECX)
47.67
The eCrime ecosystem is an active and diffuse economy of financially motivated entities who engage in myriad criminal activities in order to generate revenue. With the eCrime Index (ECX), CrowdStrike’s Intelligence team maintains a composite score to track changes to this ecosystem, including changes in eCrime activity, risk and related costs.

Recommended solution:
CrowdStrike Falcon® Complete stops breaches on endpoints, workloads, and identities, with expert management, threat hunting, monitoring and remediation, and is backed by CrowdStrike’s Breach Prevention Warranty. *
This includes:
- Proactive platform management
- 24/7 monitoring
- Operated by experts
- Investigates all detections: critical, high, med, low
- 24/7 continuous threat hunting-based protection
- Proactive surgical remediation
- Backed by breach prevention warranty
Recommended solution:
CrowdStrike Falcon® Complete stops breaches on endpoints, workloads, and identities, with expert management, threat hunting, monitoring and remediation, and is backed by CrowdStrike’s Breach Prevention Warranty. *
This includes:
- Proactive platform management
- 24/7 monitoring
- Operated by experts
- Investigates all detections: critical, high, med, low
- 24/7 continuous threat hunting-based protection
- Proactive surgical remediation
- Backed by breach prevention warranty
Recommended solution:
CrowdStrike Falcon® Complete stops breaches on endpoints, workloads, and identities, with expert management, threat hunting, monitoring and remediation, and is backed by CrowdStrike’s Breach Prevention Warranty. *
This includes:
- Proactive platform management
- 24/7 monitoring
- Operated by experts
- Investigates all detections: critical, high, med, low
- 24/7 continuous threat hunting-based protection
- Proactive surgical remediation
- Backed by breach prevention warranty
Recommended solution:
This includes:
- Proactive platform management
- 24/7 monitoring
- Operated by experts
- Investigates all detections: critical, high, med, low
- 24/7 continuous threat hunting-based protection
- Proactive surgical remediation
- Backed by breach prevention warranty
The Latest Trends
2024 Global Threat Report
Uncover notable themes, trends and events
across the cyber threat landscape.
230+
total adversaries tracked by CrowdStrike
2 min
7 sec
fastest recorded eCrime breakout time
75%
increase in cloud intrusions
Adversary Tradecraft
2023 Threat Hunting Report
Get the latest adversary intelligence exposed by CrowdStrike’s Counter Adversary Operations team.
79 mins
average eCrime breakout time
7 mins
fastest breakout time recorded
62%
of interactive intrusions involved compromised identities
* Breach Prevention Warranty: Not available in all locations, see FAQ here for additional information.
Defend your business with precision
Unlock your custom threat landscape

Your Personalized Threat Landscape
Today’s threat actors are smarter, more sophisticated, and more well resourced than they have ever been. Only by understanding them can you remain one step ahead of today’s increasingly relentless adversaries.