CrowdStrike Falcon for AWS
The CrowdStrike Falcon® platform delivers end-to-end protection from the host to the cloud and everywhere in between, for workloads and containers on AWS.
Complete protection for AWS workloads
Complete visibility of all AWS cloud resources
Continuous and comprehensive workload monitoring, and container visibility, ensuring nothing is missed and stealthy attacks can be stopped.
Protection for AWS workloads, hosts, and containers
Protect against breaches with unparalleled coverage. Defend against threats from malware to the most sophisticated attacks.
Automate freely and eliminate complexity and friction
Built in the cloud for the cloud. Falcon for AWS reduces the overhead, friction and complexity associated with protecting cloud workloads and enables cloud security to keep up with the dynamic and flexible nature of AWS environments.
Features
How Falcon Protects AWS Workloads
Unrivaled visibility
Unrivaled visibility
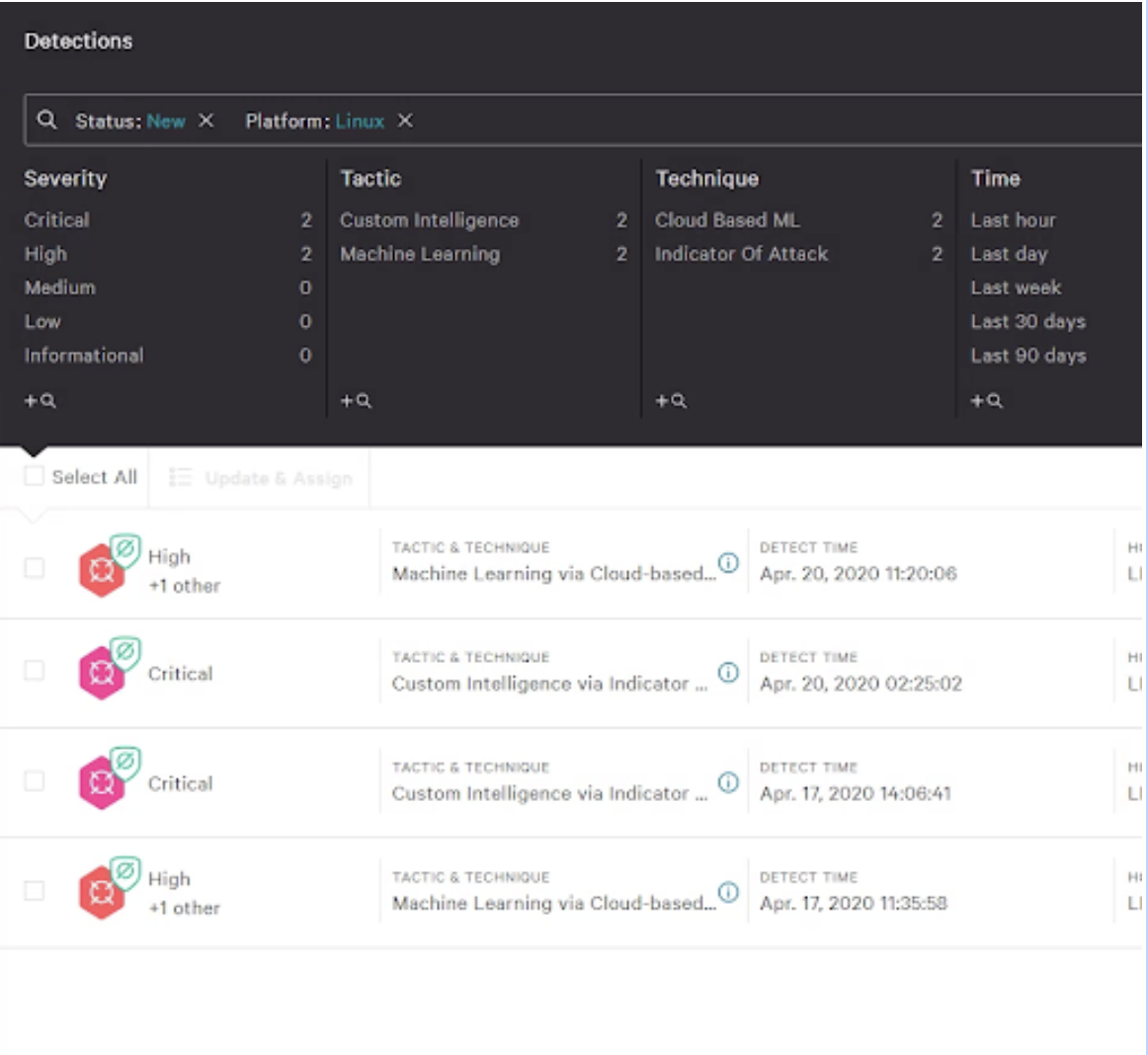
- Full EDR prevents silent failure by capturing raw events for complete visibility.
- You gain visibility into incidents involving containers, with process trees showing container IDs.
- Full attack visibility provides details, context and history for every alert.
- Event details and a full set of enriched data is continuously available, even for ephemeral and decommissioned workloads.
- Rogue instance detection is enabled.
- Extensive AWS visibility includes environment, accounts and instances.
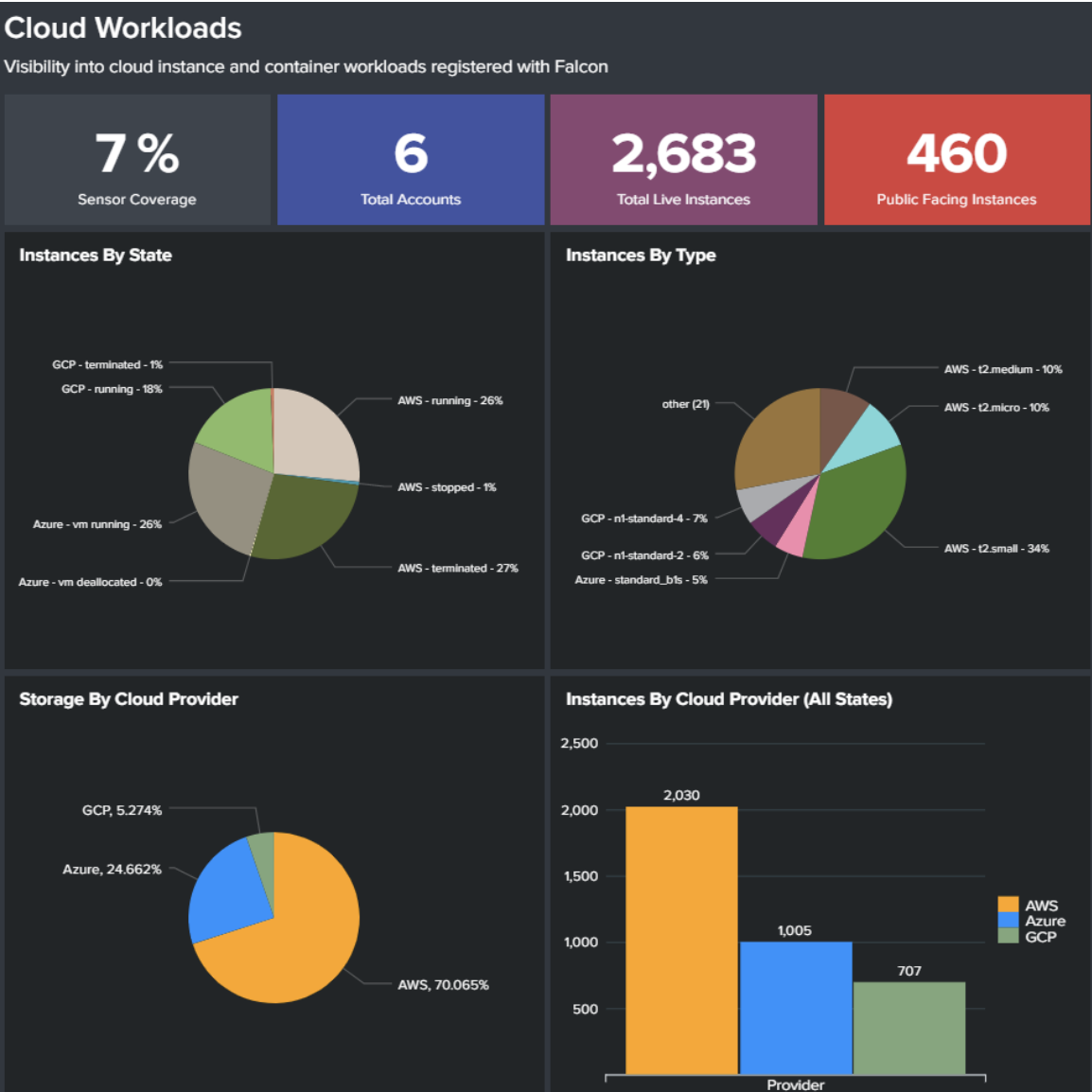
Amazon EC2 and container protection
Amazon EC2 and container protection
- Combines the best and latest technologies to protect against active attacks and threats when AWS workloads are the most vulnerable — at runtime.
- Machine Learning and AI protects against known and zero-day malware.
- Protection against prevalent cloud workload threats like web shells, SQL shells and credential theft.
- Behavior-based indicators of attack (IOAs) detect sophisticated attacks such as fileless and malware-free.
- Offers integrated threat intelligence to block known malicious activities and delivers the complete context of an attack, including attribution.
- Exploit protection and blocking.
- Delivers container security through a single agent running on the node that protects the instance itself as well as all containers running on it.
- Provides 24/7 managed threat hunting to ensure that stealthy attacks don’t go undetected.
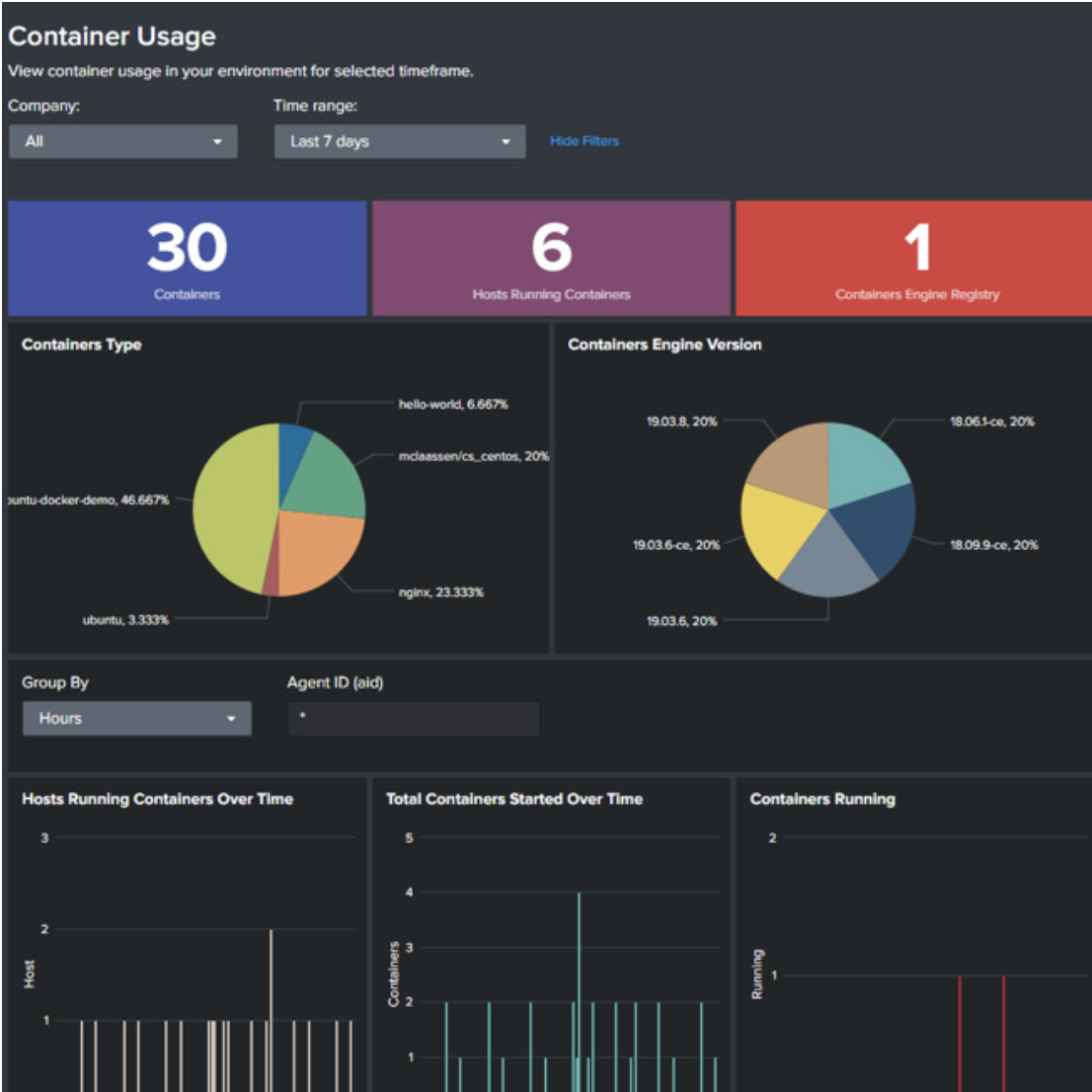
Seamless automation
Seamless automation
- Automatic detection of attacker behavior with prioritized alerts and severity eliminates time-consuming manual searches and assessments.
- Integration with CI/CD deployment workflows.
- Powerful APIs enable automation of all functional areas including detection, management, response and intelligence.
- Scales as cloud workloads expand — no need for additional infrastructure.
- Integrates to AWS Security Hub for centralized management of threat alerts from AWS services.
CrowdStrike Security Cloud
CrowdStrike Security Cloud
- CrowdStrike Security Cloud predicts and prevents modern threats in real time through the industry’s most comprehensive sets of endpoint and workload telemetry, threat intelligence and AI-powered analytics.
- CrowdStrike Security Cloud leverages enriched threat intelligence to deliver a visual representation of relationships across account roles, workloads and APIs to provide deeper context for faster more effective response.
- Deep AI and behavioral analysis identify new and unusual threats in real time and takes the appropriate action, saving value time for security teams.
- CrowdStrike Security Cloud puts this body of knowledge at the responder’s fingertips in real time, empowering responders to understand threats immediately and act decisively.
- Targeted threat identification and management approach cuts through the noise of multi-cloud environment security alerts reducing alert fatigue.

Simplicity and performance
Simplicity and performance
- Works everywhere: Amazon EC2 instances, Amazon ECS & Amazon EKS containers, Windows, Linux, Amazon Linux.
- One console provides central visibility over cloud workloads regardless of location.
- No reboots — No signatures — No scan storms — No disruption.
- Lightweight — Operates with only a tiny footprint on the host and Zero impact on runtime performance even when analyzing, searching and investigating.
- Automatically kept up to date with SaaS delivery.
- Complete policy flexibility — apply at individual server, group or data center level.

CrowdStrike and AWS: Better together
CrowdStrike and AWS: Better together
The CrowdStrike Falcon platform works with services from Amazon Web Services (AWS) that further protect customers from growing threats and increasingly complex cyber attacks. The integrations provide joint customers with comprehensive visibility, dynamic scale, automation and flexibility to better prevent, detect and respond to threats in the cloud and across endpoints.
CrowdStrike and AWS have the following free integrations for joint customers today:

Falcon Cloud Security solutions
Cloud Workload Protection
Provides comprehensive breach protection across private, public, hybrid and multi-cloud environments, allowing customers to rapidly adopt and secure technology across any workload.
Cloud Security Posture Management
Provides multi-cloud visibility, continuous monitoring and threat detection, and ensures compliance enabling DevOps to deploy applications with greater speed and efficiency — cloud security posture management made simple.
Container Security
Accelerates critical detection, investigation and threat hunting tasks performed on containers — even on ephemeral containers after they have been decommissioned — enabling security teams to secure containers at the speed of DevOps without adding friction.
Think it. Build it. Secure it.
CrowdStrike Support for AWS Compute Services
CrowdStrike Support for AWS Compute Services
As your company grows and you build and expand upon your AWS environment, CrowdStrike is there to secure many different AWS Compute Services. CrowdStrike provides breach protection and control for edge computing workloads running on cloud and customer-managed infrastructure, providing simplified infrastructure management and security consolidation, without impact to productivity. Currently we support and secure:
- Amazon EC2 instances – on all major operating systems including AWS Graviton processors
- AWS Fargate
- Amazon WorkSpaces
- AWS Outposts

CrowdStrike support for applications
CrowdStrike support for applications
CrowdStrike also supports customers modern container and Kubernetes applications through our support and integrations with the following:
- Amazon Elastic Container Service
- Amazon Elastic Kubernetes Service
- Amazon Elastic Container Registry
- Amazon EKS Anywhere

Customers trust CrowdStrike





Tested and proven leader
CrowdStrike is proud to be recognized as a leader by industry analyst and independent testing organizations.
Read the report to see why CrowdStrike was Named a “Leader” in Forrester Wave for Endpoint Detection and Response Providers, Q2 2022.
Read the report to see why CrowdStrike was named a Leader in the 2022 Gartner® Magic Quadrant™ for Endpoint Protection Platforms.

