How to Mature Your Threat Intelligence Program

With so many threat intelligence solutions on the market today, it raises the question: What is threat intelligence and why do you need it?
I won’t go into detail about what threat intelligence is; you can read about that here. Instead, I want to focus on the threat intelligence maturity journey — specifically, how advanced your organization is with respect to threat intelligence adoption and which CrowdStrike solution may be right for you.
Threat Intelligence Maturity Journey
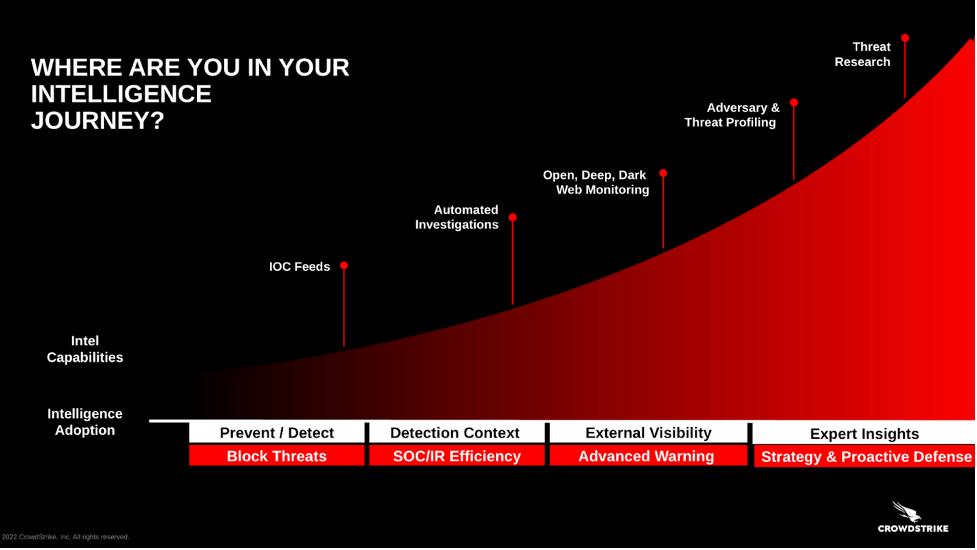
CrowdStrike describes the threat intelligence maturity journey as four steps, each of which represents movement toward a more complete threat intelligence strategy.
Why use a spectrum? Because threat intelligence isn’t binary. The market is saturated with 70+ solutions that each deliver a different use case. It can be confusing to know which one to use. By framing threat intelligence as a maturity journey, we help organizations understand which solution is right for them depending on their size, goals and current capabilities.
Step #1: Block Threats
Usually applies to: Small to midsize businesses without a security operations center (SOC)
Recommended CrowdStrike solution: The CrowdStrike Falcon® platform
While nearly every business needs cybersecurity, not every business needs a standalone threat intelligence solution. In fact, for most small to midsize businesses, the threat intelligence infused into the Falcon platform is sufficient.
It works like this: We ingest trillions of events per week into the CrowdStrike® Security Cloud, giving us clear visibility into real-time and zero-day attacks. We then supplement this information with raw intelligence from many other sources. Armed with this intelligence, the Falcon platform can automatically correlate and detect incidents faster and more precisely by eliminating the time and expertise needed to create new detection rules.
Not every cybersecurity provider infuses threat intelligence into their platform — but we do. And according to Frost & Sullivan, CrowdStrike has the best threat intelligence in the business.
Step #2: SOC Efficiency
Usually applies to: Companies with 250+ employees with a SOC
Recommended CrowdStrike solution: CrowdStrike Falcon® Intelligence
For larger companies that typically investigate more incidents than small businesses, CrowdStrike offers a threat intelligence solution that adds context to detections, automates investigations and helps prioritize vulnerability patching — helping you make better, faster decisions.
Falcon Intelligence enriches the events and incidents detected by the Falcon platform, helping you visualize relationships between indicators of compromise (IOCs) and adversaries found on your endpoints for more productive threat hunting and remediation.
The solution also automates investigations, accomplishing in minutes what can take a human hours or days. This speed is vital for security teams, as the average breakout time for eCrime intrusion activity dropped from 98 minutes in 2021 to 84 minutes in 2022, according to the CrowdStrike 2023 Global Threat Report.
The CrowdStrike 2023 Global Threat Report is the most anticipated cybersecurity report of the year — download it now.
Step #3: Advance Warning
Usually applies to: Organizations who want to identify and remediate online threats
Recommended CrowdStrike solution: CrowdStrike Falcon® Intelligence Recon
If you already have the Falcon platform and you’re using Falcon Intelligence to enrich threat detection inside the perimeter, the next step is looking outside your organization for threats.
Falcon Intelligence Recon helps you track adversaries and their activities outside the network perimeter. Do you have stolen data on the dark web? Do you have credentials for sale? Are people impersonating your brand or executives in phishing attacks? Falcon Intelligence Recon provides visibility into the cybercriminal underground so you can get advance warnings about imminent attacks and actively mitigate threats to your brands, employees and sensitive data.
The CrowdStrike 2023 Global Threat Report puts this capability into context, sharing how access broker services — threat actors who specialize in acquiring access to organizations and provide this access to other actors — increased by 112% in 2022. Falcon Intelligence Recon can expose these hidden threats and help you take decisive action to stop them.
Step #4: Proactive Defense
Usually applies to: Global 2000 organizations
Recommended CrowdStrike solution: CrowdStrike Falcon® Intelligence Premium
The world’s biggest organizations naturally have the biggest, most complex and potentially vulnerable IT ecosystems on the market. They need the best threat intelligence available. These companies typically have their own threat intelligence teams working around the clock to profile adversaries and understand the tools they use.
Falcon Intelligence Premium delivers world-class intelligence reporting, technical analysis and malware analysis to help these global organizations build cyber resiliency and proactively defend against sophisticated nation-state, eCrime and hacktivist adversaries.
With intrusion frequency gaining momentum, global organizations can turn to Falcon Intelligence Premium and CrowdStrike Falcon® Intelligence Elite (which includes a CrowdStrike intelligence analyst) for the best threat intelligence on the market today.
Get the Report
Threat intelligence can be valuable at any stage of the maturity journey. The challenge is understanding which solution is right for your business. Hopefully this post helps you understand where your organization is on the maturity journey and which CrowdStrike threat intelligence solution may be right for you.
Want to become a threat intelligence expert? Read the CrowdStrike 2023 Global Threat Report, cybersecurity’s definitive threat intelligence guide. Developed based on firsthand observations from our elite cyber responders and analysts, the report provides actionable intelligence to security professionals worldwide.
You can learn more about the value of threat intelligence and how it applies to your organization in an upcoming LinkedIn Live session, “Defining Threat Intelligence” with CrowdStrike SVP of Threat Intelligence Adam Meyers.
Additional Resources
- Register to attend the LinkedIn Live session, “Defining Threat Intelligence,” with CrowdStrike SVP of Threat Intelligence Adam Meyers on March 14 at 2 p.m. ET.
- Visit the CrowdStrike threat intelligence product page to learn more about our threat intelligence solutions.
- Attend a Falcon Encounter Hands-On Lab to experience Falcon Intelligence for yourself or request a free trial.


