Hunting pwnkit Local Privilege Escalation in Linux (CVE-2021-4034)

In November 2021, a vulnerability was discovered in a ubiquitous Linux module named Polkit. Developed by Red Hat, Polkit facilitates the communication between privileged and unprivileged processes on Linux endpoints. Due to a flaw in a component of Polkit — pkexec — a local privilege escalation vulnerability exists that, when exploited, will allow a standard user to elevate to root.
Once initial access has been achieved through other means, exploitation of CVE-2021-4032 — nicknamed “pwnkit” — is trivial and a public proof of concept is available. Mitigation and update recommendations can be found on Red Hat’s website.
Pwnkit was publicly disclosed on Jan. 25, 2022.
Hunting Using CrowdStrike Falcon®
To hunt pwnkit, we’ll use two different methods. First, we’ll profile processes being spawned by pkexec and second, we’ll target a signal absent from pkexec process executions that could indicate exploitation has occurred.
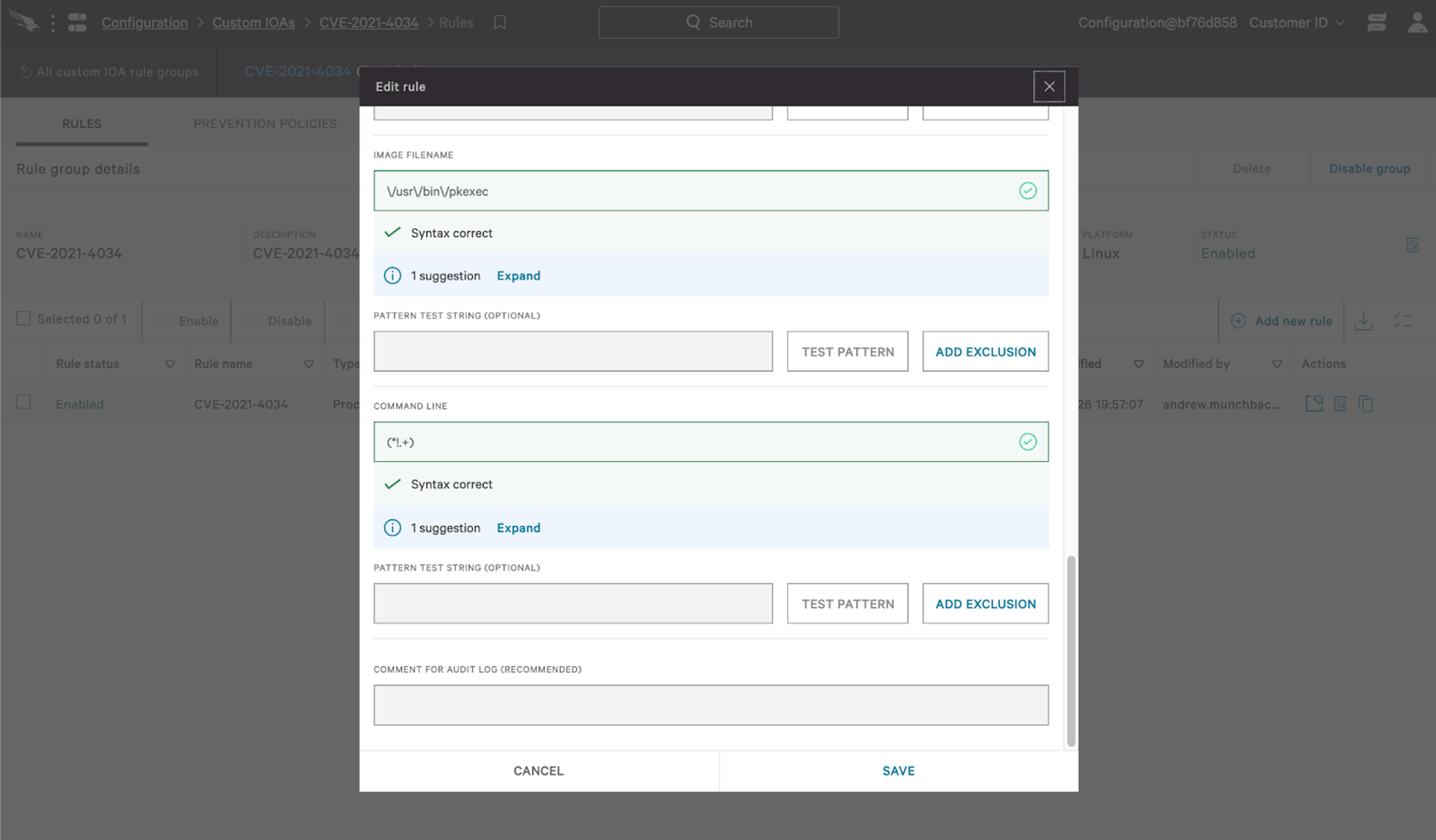
Profiling pkexec
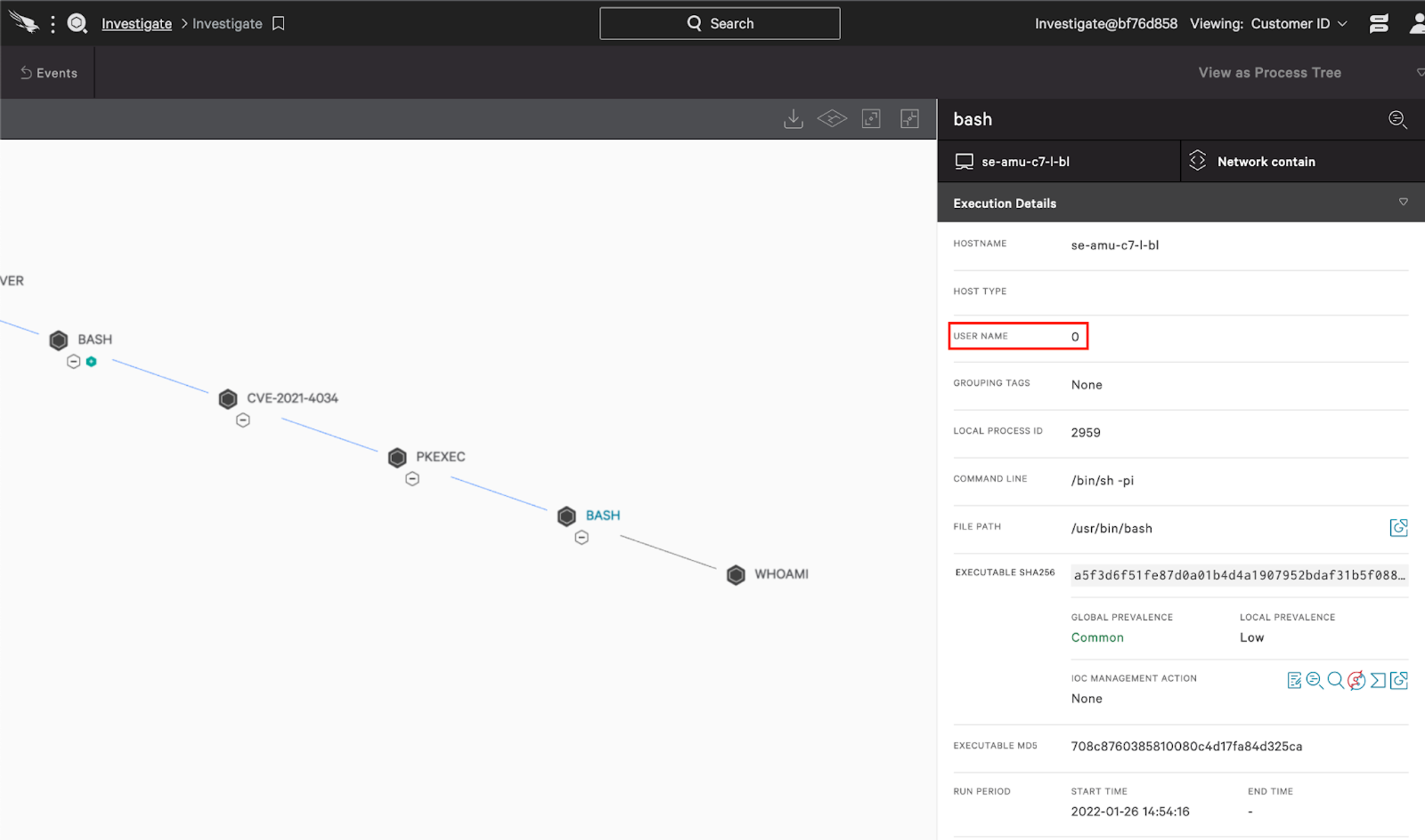
When pwnkit is invoked by a non-privileged user, pkexec will accept weaponized instructions and spawn a new process as the root user. On a Linux system, the root user has a User ID (UID) of 0. Visualized, the attack path looks like this:
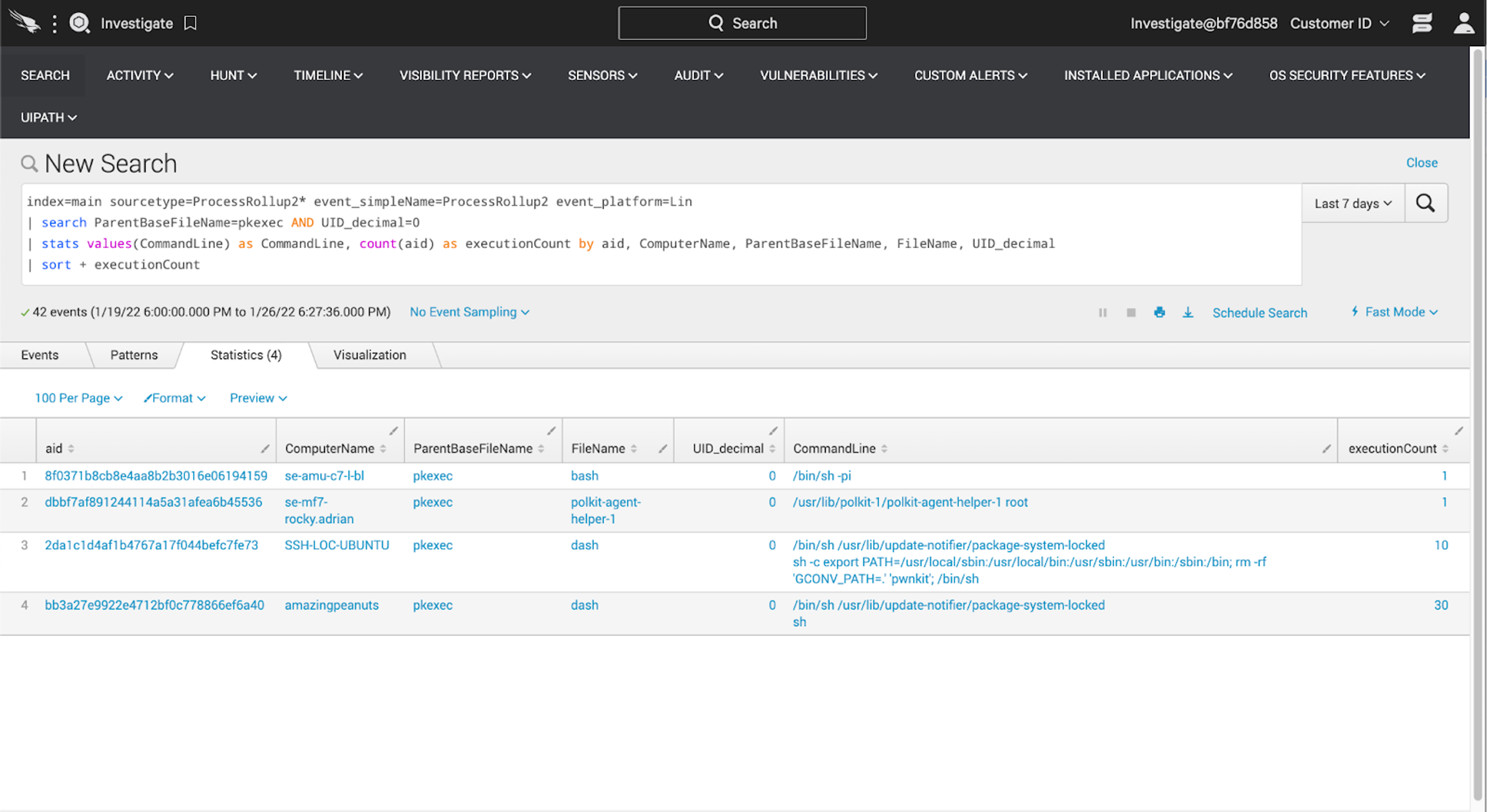
To cast the widest possible net, we’ll examine the processes that pkexec commonly spawns and look for outliers. Our query will look like this:
index=main sourcetype=ProcessRollup2* event_simpleName=ProcessRollup2 event_platform=Lin
| search ParentBaseFileName=pkexec AND UID_decimal=0
| stats values(CommandLine) as CommandLine, count(aid) as executionCount by aid, ComputerName, ParentBaseFileName, FileName, UID_decimal
| sort + executionCountThe output of that query will be similar to this:
Right at the top, we can see two low-velocity executions of interest. The second we immediately recognize as legitimate. The first is an exploitation of pwnkit usage and deserves further attention.
The public proof of concept code used for this tutorial issues a fixed command line: /bin/sh -pi. Hunting for this command line specifically can identify lazy testing and/or exploitation, but know that this string is trivial to modify:
index=main sourcetype=ProcessRollup2* event_simpleName=ProcessRollup2 event_platform=Lin
| search ParentBaseFileName=pkexec AND UID_decimal=0 AND CommandLine="/bin/sh -pi"
| stats values(CommandLine) as CommandLine, count(aid) as executionCount by aid, ComputerName, ParentBaseFileName, FileName, UID_decimal
| sort + executionCountEmpty Command Lines in pkexec
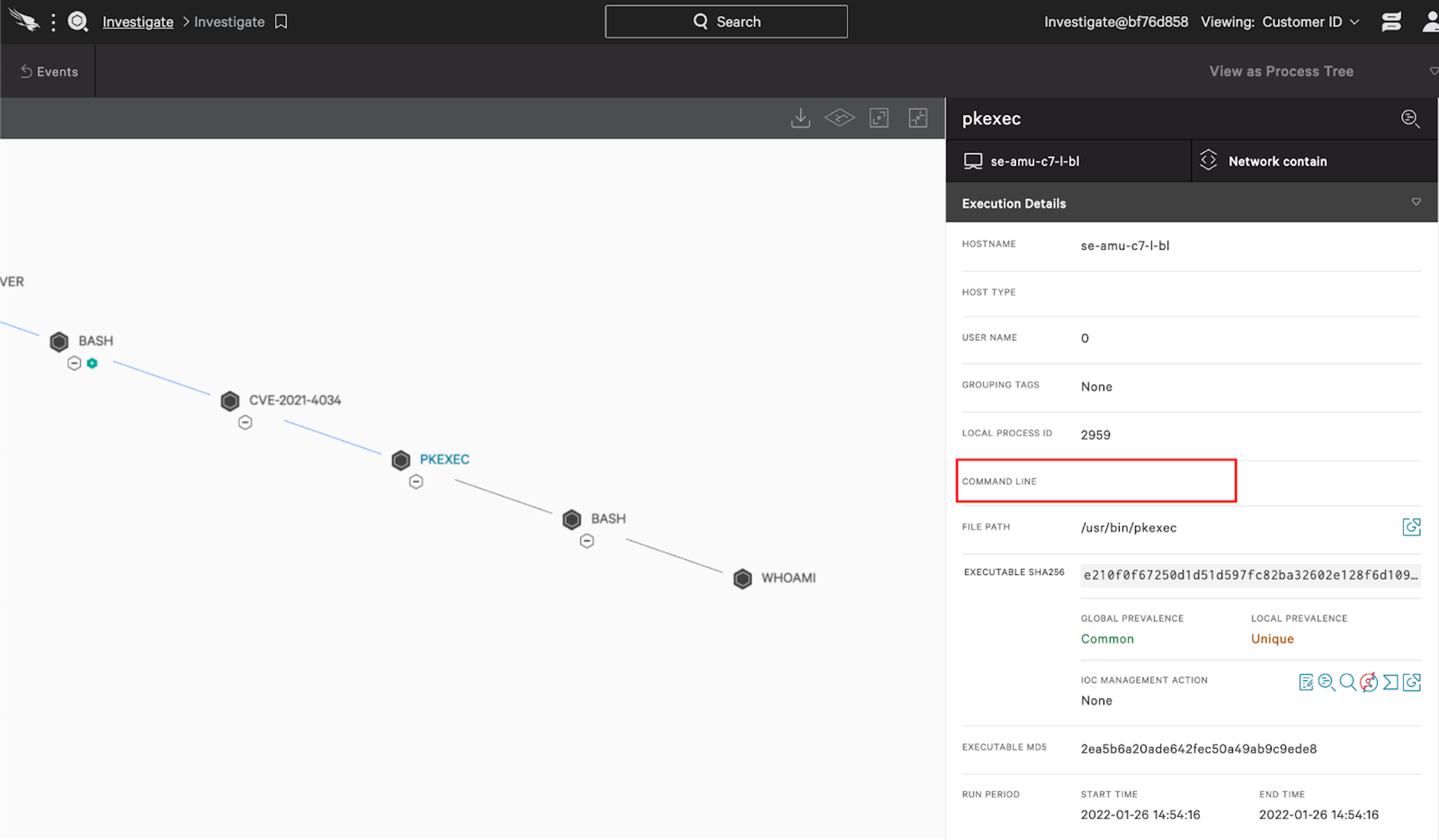
One of the interesting artifacts of pwnkit exploitation is the absence of a command line argument when pkexec is invoked. You can see that here:
What’s more, the process requesting elevation and leveraging pwnkit will not have a UID of 0. As such, an abused pkexec execution will have Real User ID (RUID) value that is not 0. With this information, we can hunt for instances of pkexec being invoked with a null value in the command line and an RUID other than 0.
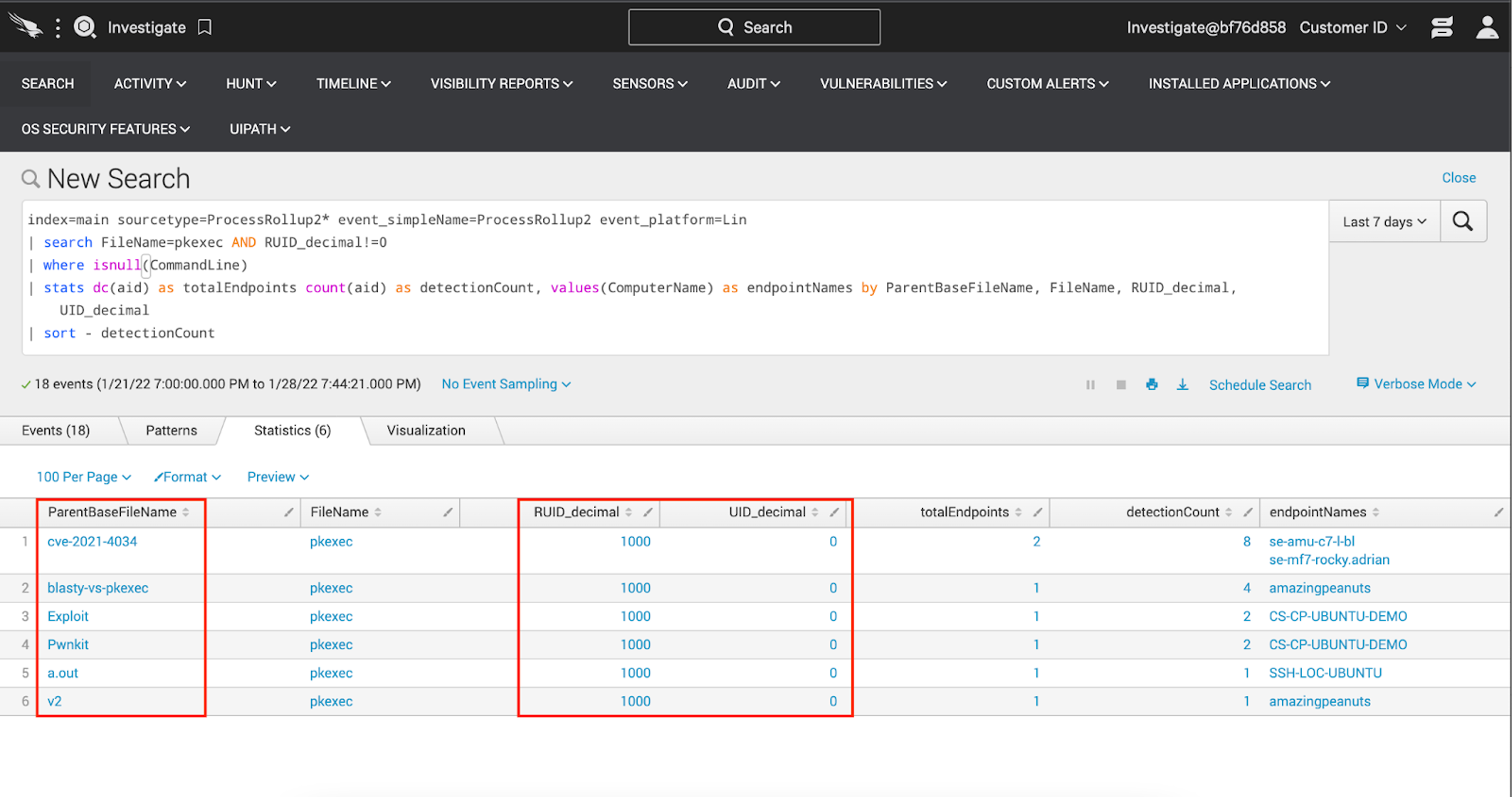
index=main sourcetype=ProcessRollup2* event_simpleName=ProcessRollup2 event_platform=Lin
| search FileName=pkexec AND RUID_decimal!=0
| where isnull(CommandLine)
| stats dc(aid) as totalEndpoints count(aid) as detectionCount, values(ComputerName) as endpointNames by ParentBaseFileName, FileName, UID_decimal
| sort - detectionCountWith this query, all of our testing comes into focus:
Any of the queries above can be scheduled for batched reporting or turned into custom IOAs for real-time hunting, detection and/or prevention.
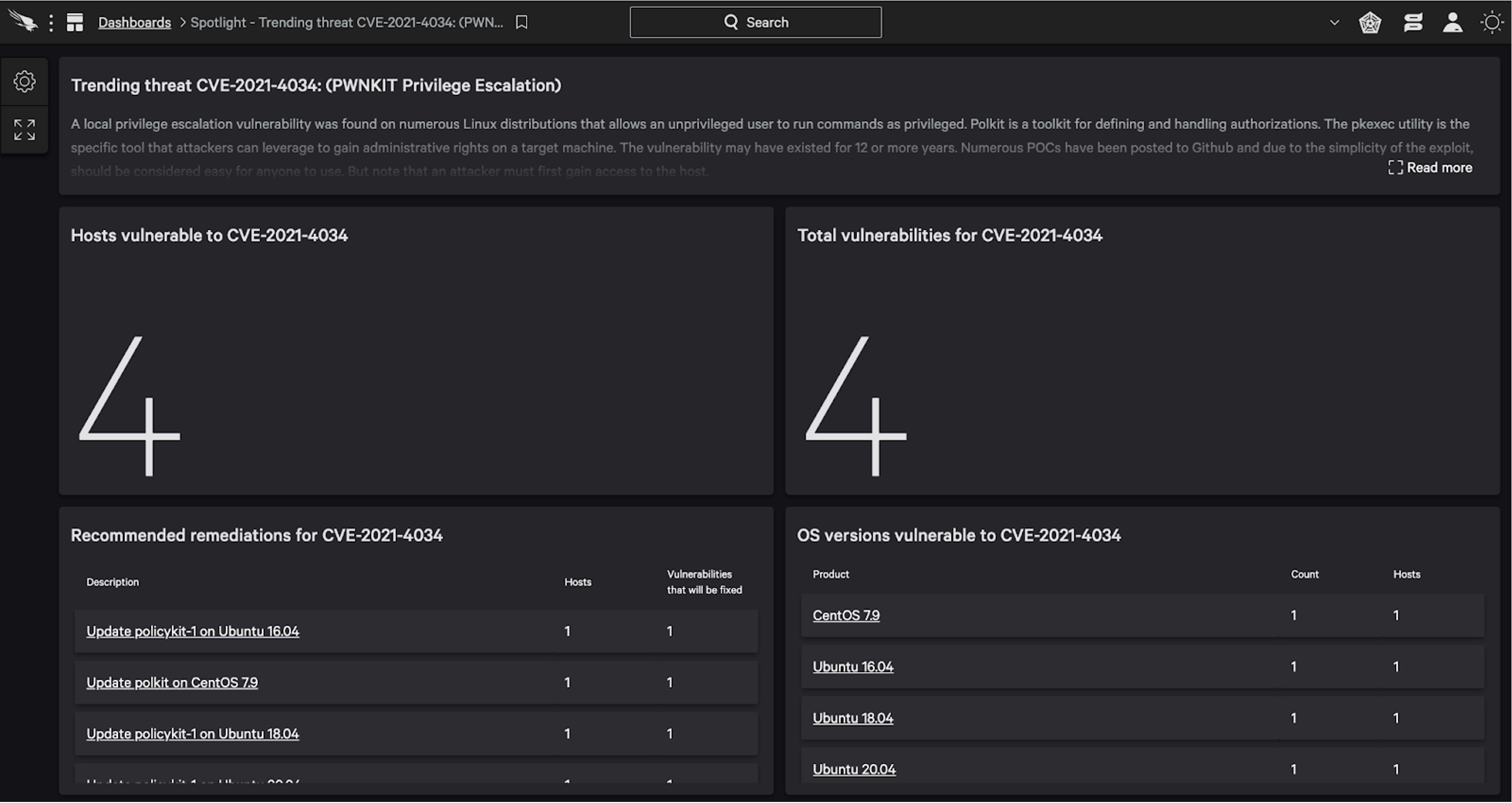
Falcon Spotlight Provides Custom Threat Dashboard for Linux Vulnerability — CVE-2021-4034
To enable customers to quickly see which Linux hosts are vulnerable, CrowdStrike developed a custom dashboard for Falcon Spotlight™ customers. The dashboard offers details on the threat analysis provided by researchers and includes at-a-glance views of detailed information on hosts and systems vulnerable to CVE-2021-4034, as well as the count of vulnerable product versions.
This custom dashboard enables Falcon Spotlight customers to identify instances of CVE-2021-4034, see affected hosts and vulnerable OS versions, view recommended remediations and track remediation progress.
The dashboard currently tracks the following distributions:
- Ubuntu 14.04, 16.04, 18.04 and 20.04
- Debian 9 and 10
- RHEL 7 and 8
- Amazon Linux AMI 2
More updates and distributions will be added to the dashboard as the situation unfolds. Falcon Spotlight customers can access this and other predefined dashboards by navigating to Dashboards > Spotlight > Trending Threat CVE-2021-4034 from the CrowdStrike Falcon®® platform menu.
Because the Falcon platform operates in the cloud via lightweight agent architecture, it can provide constant and immediate visibility to vulnerabilities such as CVE-2021-4034. Watch this video to see Falcon Spotlight in action and learn how you can quickly view and resolve any vulnerabilities in your environment.
Additional Resources
- Learn how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.