How to Prevent Malware-Free Attacks with CrowdStrike Falcon® Endpoint Protection

Introduction
In this document, we will see how to prevent malware-free attacks with CrowdStrike Falcon. Malware-free attacks are attacks that do not use malware.
Falcon uses multiple methods to prevent and detect those types of attacks and this unique combination allows Falcon to protect against even the most advanced attacks. This document will focus on Falcon’s exploit blocking and Indicators of Attack (IOAs) protection features.
Video
“How to Detect and Prevent Malware Free Attacks with CrowdStrike Falcon®”
Instructions
Policy Configuration Steps
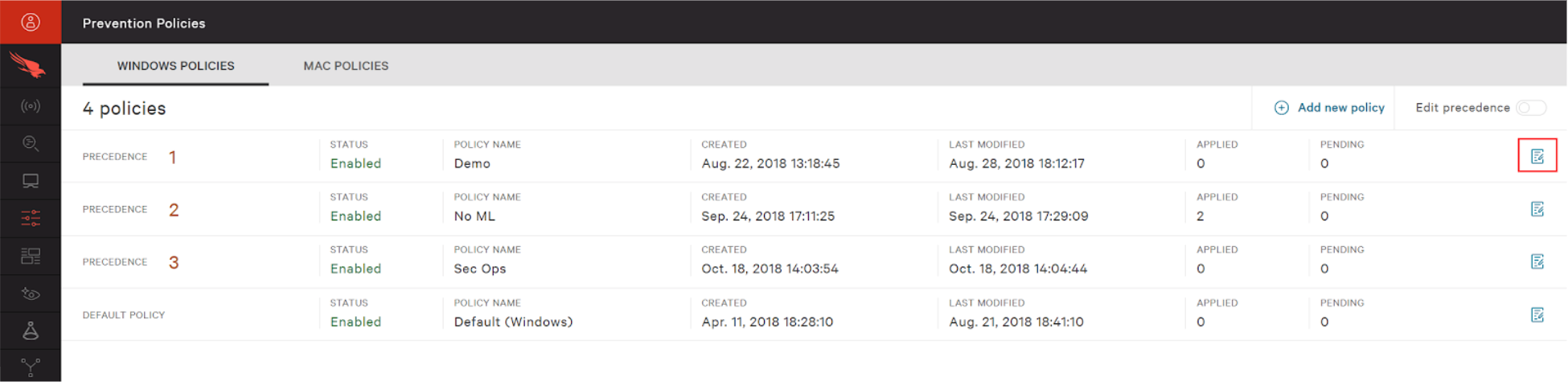
Navigate to the Configuration Policy. You can configure prevention features in the Configuration App. Once in the App, chose Prevention Policies. Please note that you need Admin privileges to configure the prevention features on the Prevention App settings page. Chose to edit an existing policy by clicking the icon on the right.
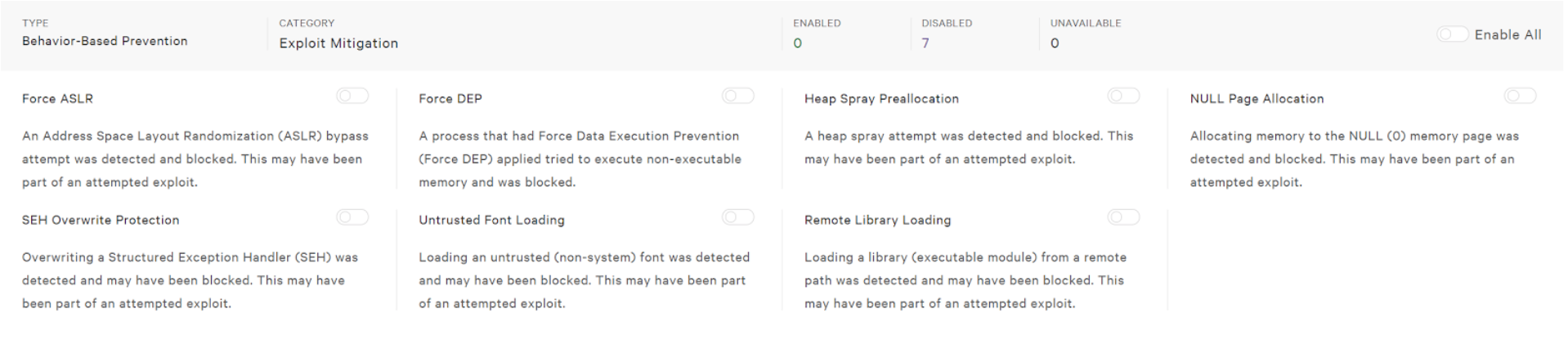
Enable Behavioral Exploit Mitigation
One of the challenges with attacks that do not use malware is that they can inject commands can directly into memory. Those attacks take advantage of vulnerabilities and make use of exploit kits. This is why Falcon provides an exploit blocking function. To turn an exploit mitigation on or off, just slide the toggle for the exploit mitigation you want to change. In our example we are going to turn on Force ASLR mitigation.
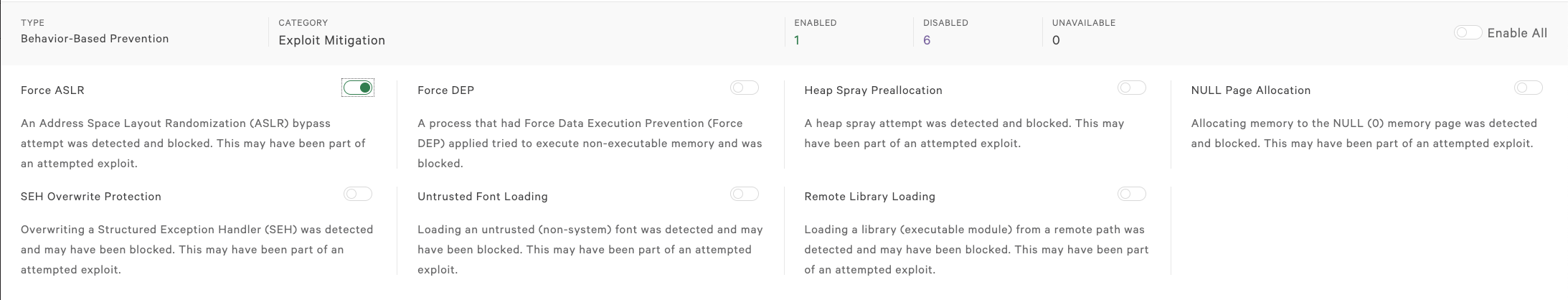
Let’s slide the toggle to the right, click “Save” and confirm the change.
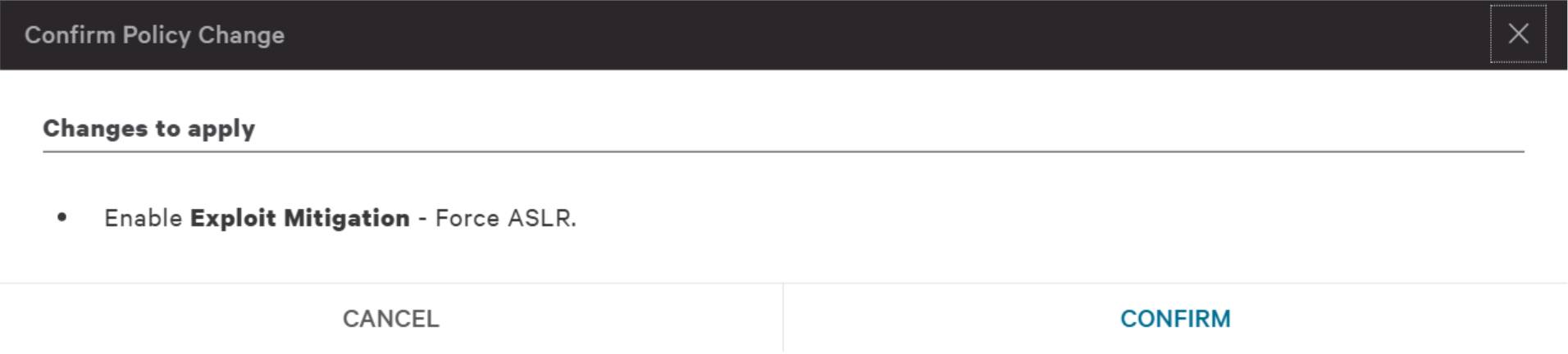
Green toggles indicated enabled.
If you want to disable the prevention for that exploit, slide the toggle to the left, click “save”, and confirm that you want to disable.
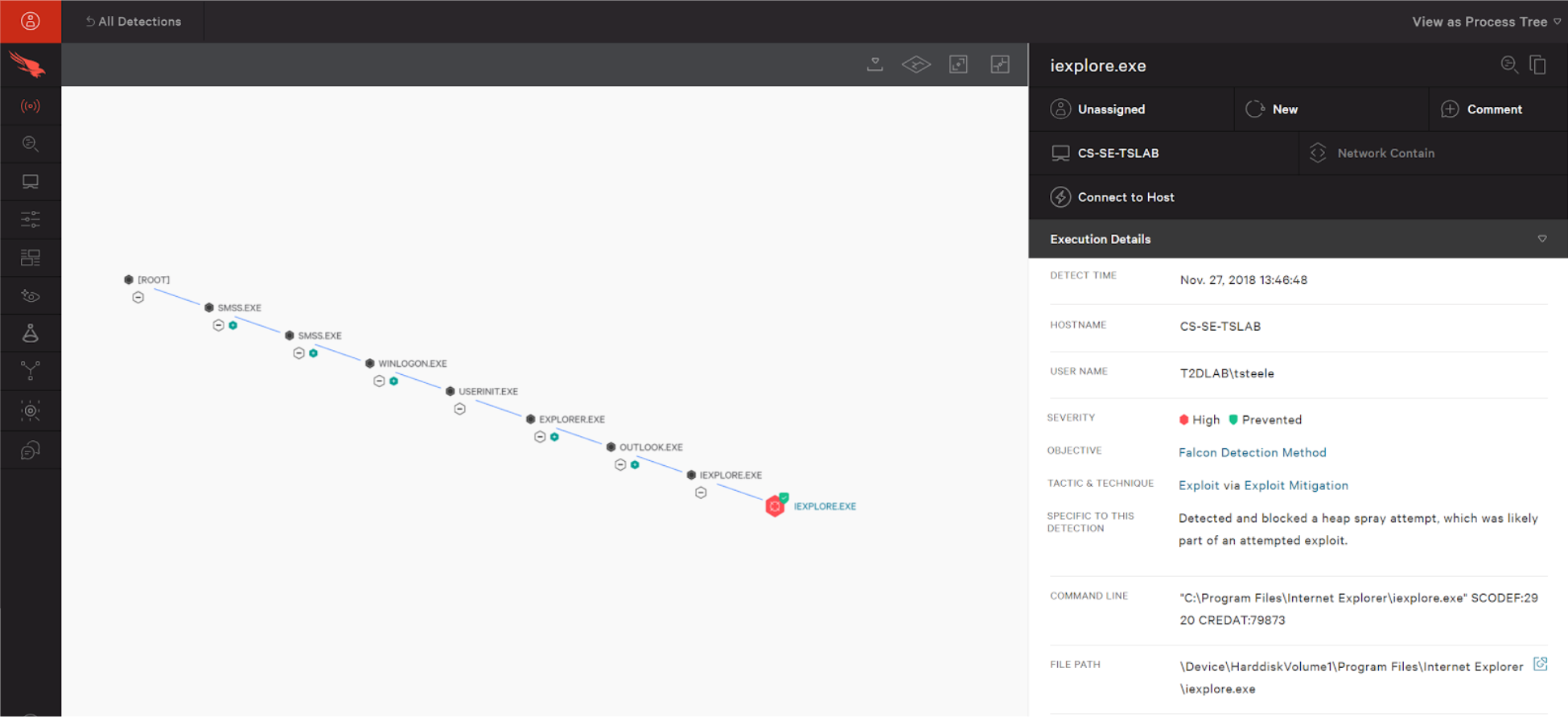
Here is an example of exploit blocking detection in the Falcon User Interface.
Prevention with Indicators of Attack
Exploit blocking provides another layer of protection but may not be sufficient at times. Some file-less malware do not use exploit kits, but rely on a user’s mistake to successfully compromise a system. Ransomware, for example, has some infamous examples of file-less ransomware that do not use exploits. Targeted attacks also fall into that category.
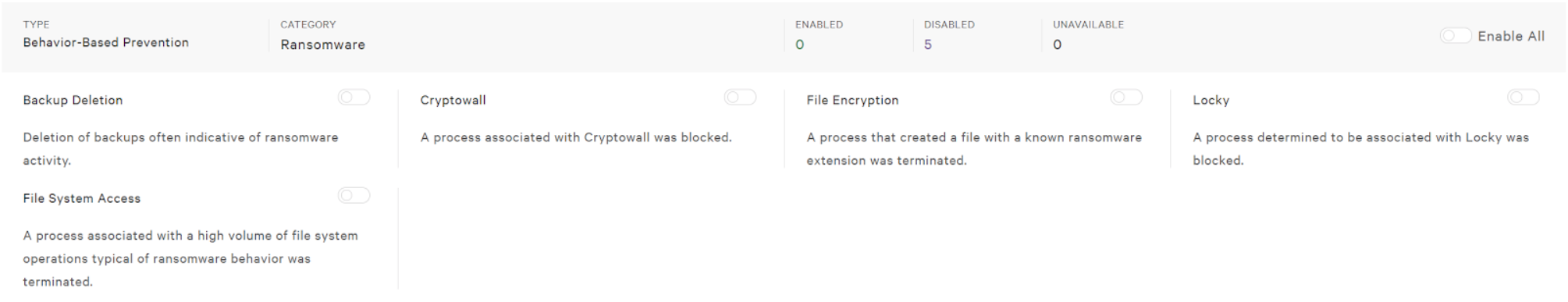
This is why Falcon also uses Indicators of Attacks (IOAs) to protect systems. IOAs look across both legitimate activity and suspicious activities to detect stealthy chains of events that indicate malware infection attempts. IOAs that prevent attacks which do not use malware are enabled by default. For attacks such as adware and ransomware, specific IOAs can be configured.
You can enable or disable them in the current window by sliding the toggles below similar to exploit blocking.
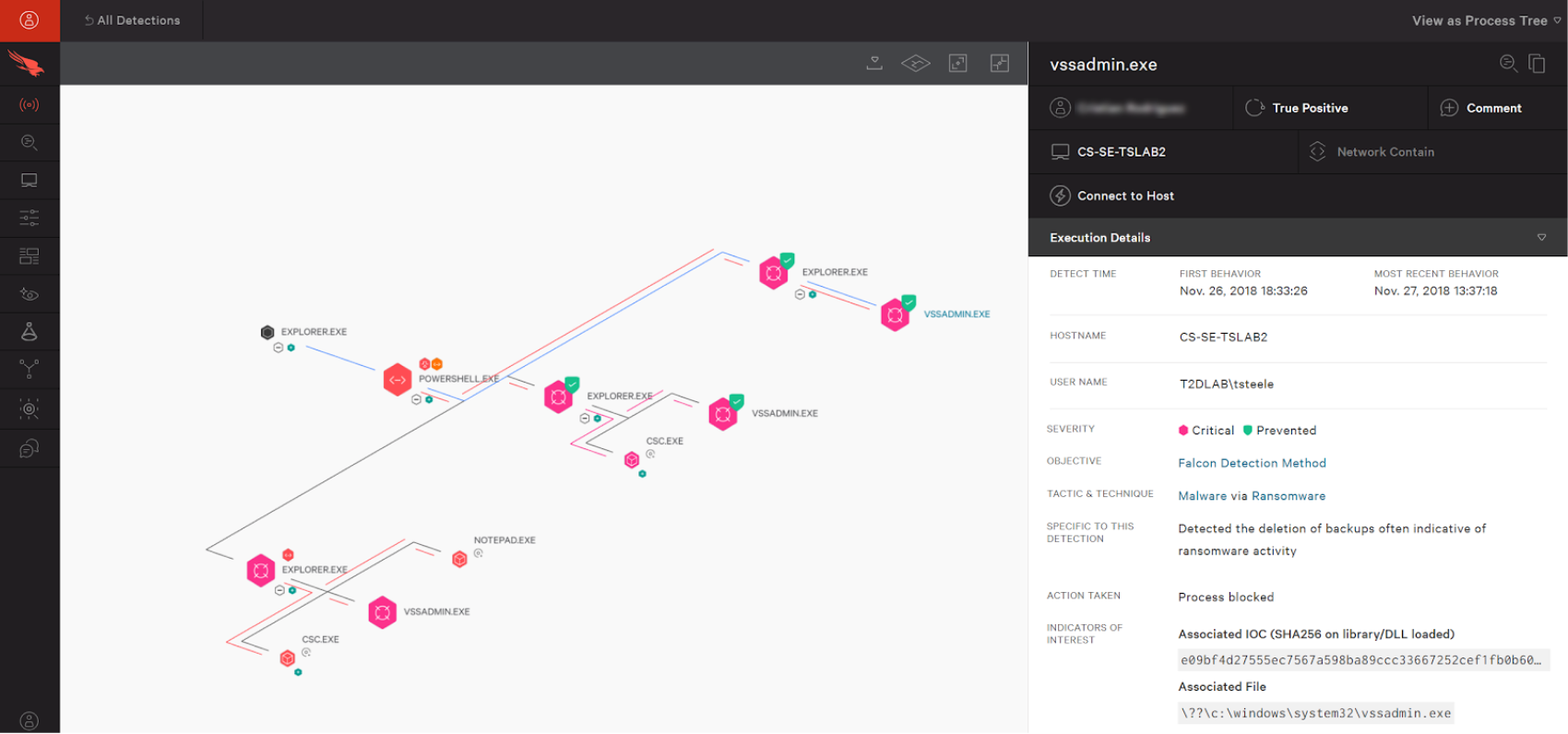
Below is an example of a ransomware prevented event based on an Indicator of Attack.
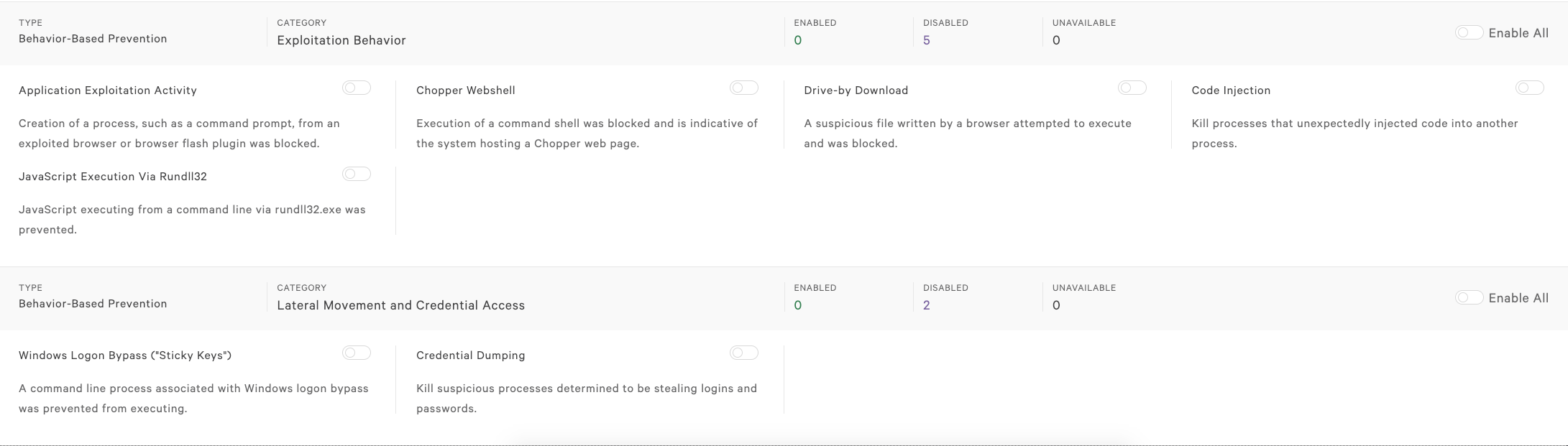
There are also policy options to configure behavioral detections around exploit behaviors, lateral movement and credential access.
Conclusion
CrowdStrike provides advanced prevention capabilities to help organizations protect their endpoints from more sophisticated, fileless attacks through simple configuration options.