Building a String-Based Machine Learning Model to Detect Malicious Activity
Working with text data (which we often refer to as “strings”) is common in cybersecurity applications. For example, suppose we…
Gimme Shellter
Red team penetration testers very often add tools to their arsenal that borrow techniques originating in malicious software. Shellter is…
CrowdStrike’s Approach Echoed in RSA 2020 Theme, “Human Element”
Another year has raced by, and RSA 2020 is only weeks away. CrowdStrike® is gearing up for our best event…
Common Attacks and Effective Mitigation: 2020 CrowdStrike Services Report Key Findings (Part 2 of 2)
Your organization is constantly under attack, and every day, adversaries are developing new ways to breach your network. How can…
Know Your Attackers: 2020 CrowdStrike Services Report Key Findings (Part 1 of 2)
The cybersecurity landscape is always evolving, but one thing remains constant: Cyber adversaries continue to be relentless and innovative in…
CrowdStrike Delivers Protection for Critical Windows Certificate Spoofing Vulnerability
Microsoft recently disclosed a critical vulnerability (CVE-2020-0601) that could be leveraged for a wide range of malicious actions including spoofing…
Large-Scale Endpoint Security MOLD Remediation
While adversaries continue to evolve their cyberattacks, CrowdStrike® scientists and engineers keep pushing the boundaries of what’s achievable in malware…
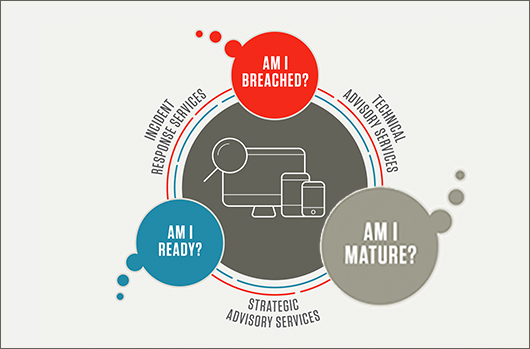
A Roadmap to Cybersecurity Maturity, Part 2: Am I Mature?
A new report from CrowdStrike® Services titled “Achieving Security Maturity: A Roadmap to Building a Robust Cybersecurity Capability” addresses the…