CrowdStrike Scores Highest Overall for Use Case Type A or “Forward-Leaning” Organizations in Gartner’s 2019 Critical Capabilities for Endpoint Protection Platforms
Gartner just released its 2019 Critical Capabilities for Endpoint Protection Platforms (EPP) report, showing CrowdStrike® with the highest overall score…
Hardening Neural Networks for Computer Security Against Adversarial Attack
Machine learning has demonstrated dramatic effectiveness in a wide range of fields, including computer security. However, machine learning for computer…
Falcon Complete and CrowdStrike Adversary Emulation Pen Testing Recognized as “Cyber Catalysts” in Marsh Cyber Risk Evaluation
Marsh, one of the world’s leading insurance broker and risk adviser, has named CrowdStrike® as a recipient of its first-ever…
How CrowdStrike Uses SHAP to Enhance Machine Learning Models
At CrowdStrike®, machine learning is a major tool for detecting new malware families and keeping our customers safe. We utilize…
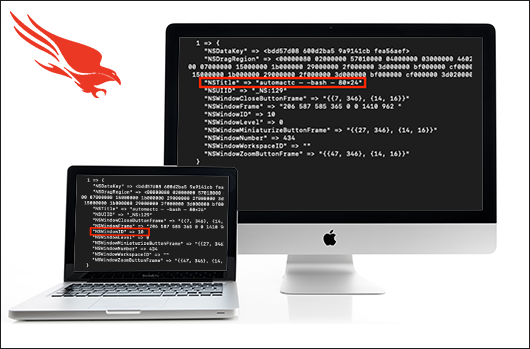
Saved by the Shell: Reconstructing Command-Line Activity on MacOS
In Mac OSX Lion (10.7), Apple introduced a feature called “User Interface (UI) Preservation”, intended to save the state of…
Falcon OverWatch Threat Hunting Report Finds an Increase in eCrime as Adversaries Mature Their Skills
The CrowdStrike® Falcon OverWatch™ elite threat hunting team has released a new report, The 2019 OverWatch Mid-Year Report: Observations from…
How to Leverage CrowdStrike Integration with Dragos
Introduction In this video and article, we will look at the integration available between CrowdStrike and Dragos - a CrowdStrike…
CrowdStrike Named a Leader in the 2019 Forrester Wave for Endpoint Security Suites
CrowdStrike secures the highest possible score in seventeen criteria and the top score overall in the strategy category. “CrowdStrike has…
Video: How CrowdStrike’s Vision Redefined Endpoint Security
The CrowdStrike® “Vision” video features Co-founders George Kurtz, CEO, and Dmitri Alperovitch, CTO, offering a look at the driving forces…