CSO Australia: The Importance of Incident Response in Ensuring Compliance and Security
A recent article in CSO Australia titled “Incident Response in the Age of New Compliance Requirements”, by CrowdStrike APJ Services…
Why Machine Learning Is a Critical Defense Against Malware
Dr. Sven Krasser, CrowdStrike® chief scientist, has called machine learning (ML) the first line of defense against modern threats. That…
Getting Access to the CrowdStrike API
Introduction CrowdStrike’s Falcon Platform is developed as an “API First Platform”, so as new features are released, corresponding API functionality…
How to configure Manual Updates
Preface Organizations have different policies regarding endpoint software updates. Falcon Agent Updates are configurable via the Sensor Update Policies. Within…
5 Tips for a Happy Marriage Between IT Cybersecurity and Operational Technology Teams
We sit in a dusty break room, notepads in hand, and nervously watch the corporate IT cybersecurity and industrial operational…
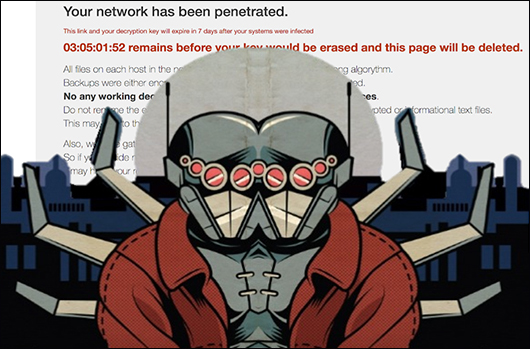
BitPaymer Source Code Fork: Meet DoppelPaymer Ransomware and Dridex 2.0
CrowdStrike® Intelligence has identified a new ransomware variant identifying itself as BitPaymer. This new variant was behind a series of…
CSO Magazine Reviews CrowdStrike Endpoint Detection and Response: “Falcon Breaks the EDR Mold”
A recent product review in CSO Magazine titled, “CrowdStrike Falcon Breaks the EDR Mold,” explains how the CrowdStrike® Falcon endpoint…
Where Do CISOs Belong in the IT Org Chart?
This article originally appeared on InformationWeek.com and is published here with their permission. As security breaches continue to impact the…
CrowdStrike EMEA’s John Titmus Offers Insights on Protecting Against Today’s Biggest Threat Actors
CrowdStrike Director of Engineering for EMEA (Europe, Middle East and Africa) John Titmus shared his insights with SC Magazine recently…
How to Fill the Cybersecurity Skills Gap With Homegrown Talent
The Challenge The increasing sophistication and frequency of adversary infiltration and exploit attacks has forced many organizations to play a…