How to use the CrowdStrike Message Center with Falcon Complete
Introduction In the event of a breach, every second counts making good communication imperative. In many cases teams struggle with…
CrowdStrike Falcon Scores 100% Protection in AV-Comparatives Real-World Protection Test (March-April 2021)
Recent high-visibility ransomware attacks — such as the disruption of a major U.S. East Coast fuel pipeline caused by DarkSide…
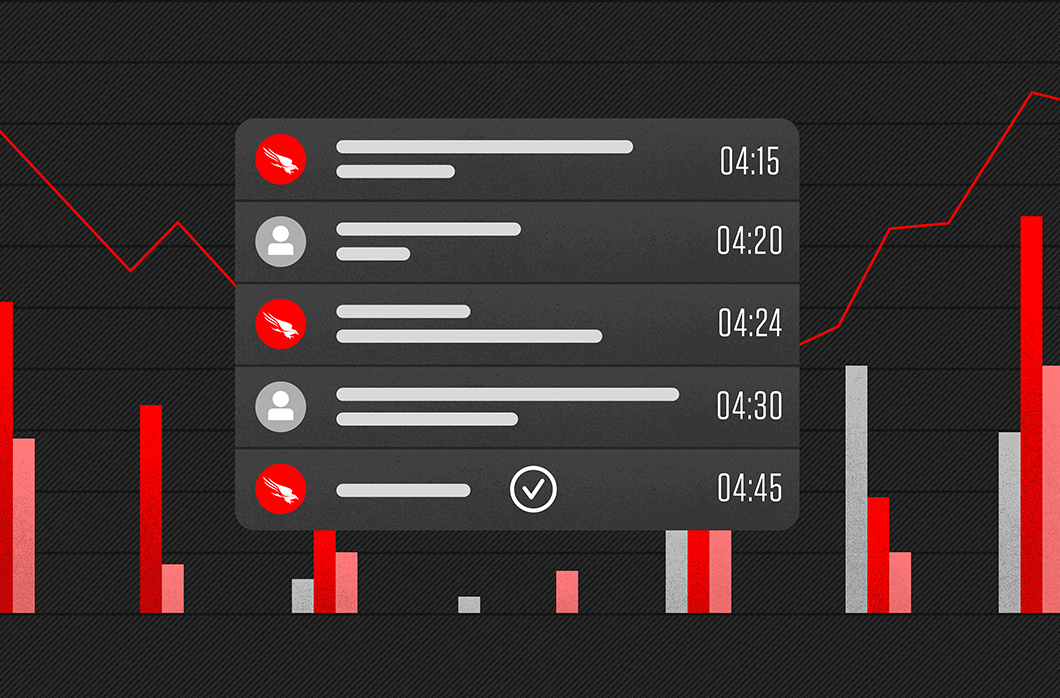
New Message Center Improves Response Time by Reducing Friction in MDR Collaboration
CrowdStrike has long emphasized the importance of identifying, triaging and remediating threats in line with our 1-10-60 framework. This framework…
Drex DeFord on Innovative Technology Meeting the Healthcare Industry’s Needs
Do you know that CrowdStrike is hiring a team of executives to partner with healthcare; federal, state and local government;…
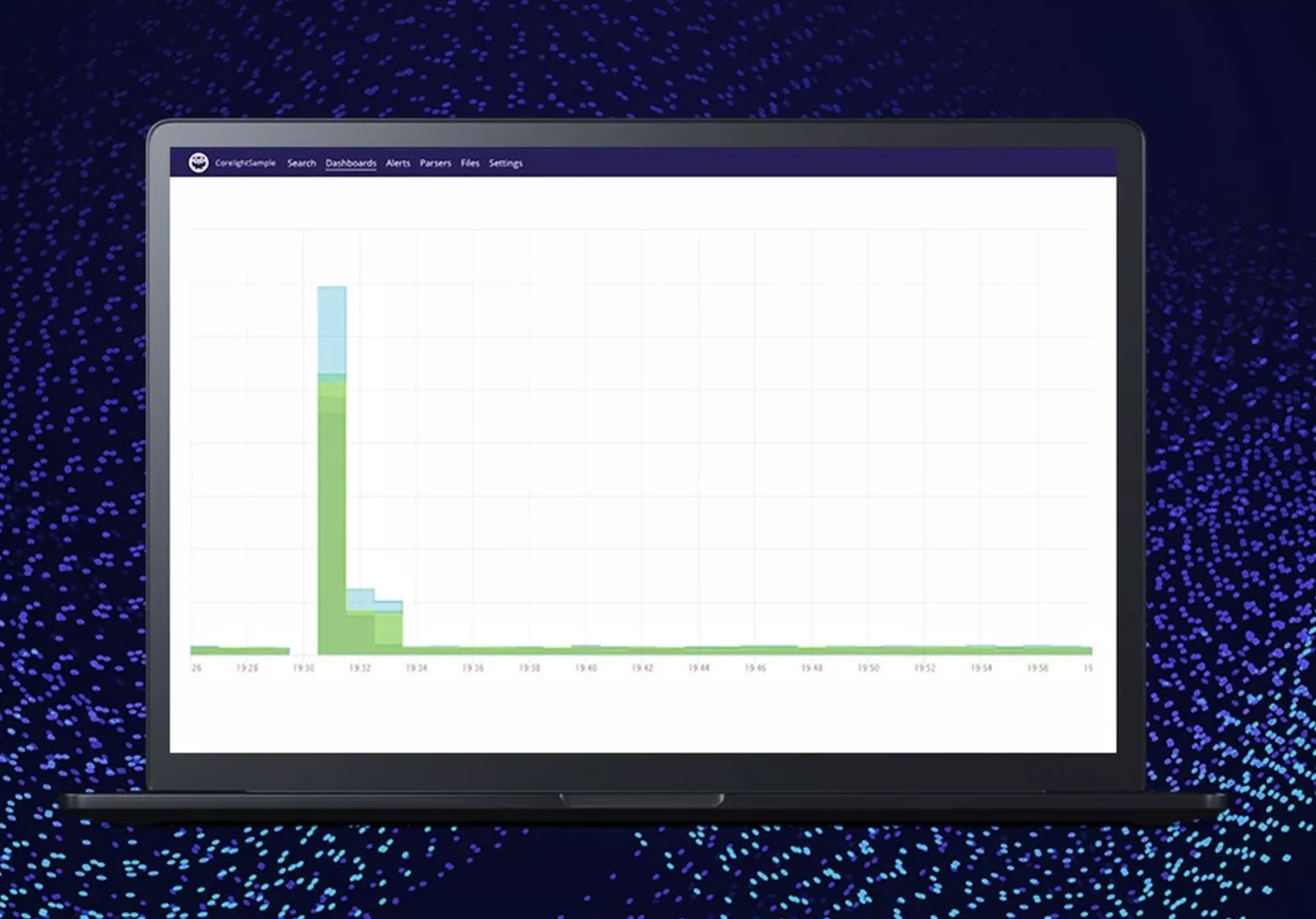
Streaming Live Data is the Heart of Observability
This blog was originally published Feb. 14, 2020 on humio.com. Humio is a CrowdStrike Company. As a security engineer working…
Cloud Engineer Alexandru Boieriu on the Challenge and Excitement of Working With Data at Scale
We’ve said it before and we’ll say it again: There’s big data, and then there’s CrowdStrike data. Our engineering team…
Under Attack: Protecting Against Conti, DarkSide, REvil and Other Ransomware
CrowdStrike predicted in 2020 that the ransomware threat would only worsen, and news reports since have borne this out. Stories…
Humio at Decisiv: An Industrial Internet of Things Company Reduces Log Management Costs by 37%
This blog was originally published on humio.com. Humio is a CrowdStrike Company. Decisiv’s self-hosted log management solution was taking up too…
Adversary Quest Walkthrough, Part 3: Four PROTECTIVE PENGUIN Challenges
At the end of January 2021, the CrowdStrike Intelligence Advanced Research Team hosted our first-ever Adversary Quest. This “capture the…
New Partner Applications to Accelerate Your SOC’s Security Transformation
Every security operations center (SOC) is different and has unique traits; however, most share similar challenges. Each SOC has its…