How to Integrate CrowdStrike with ServiceNow

Introduction
CrowdStrike has crafted a highly extensible platform that allows customers and partners alike to leverage APIs with other existing security solutions products. In this video and article, we will take a look at our integration with the ServiceNow platform.
Video
Getting Started
Before setting up the integration in your ServiceNow instance, there are a few prerequisite steps.
- To get started with the CrowdStrike API, you’ll want to first define the API client and set its scope. Refer to this guide to getting access to the CrowdStrike API for setting up a new API client key. For the new API client, make sure the scope includes the following.
- Detection – Read, Write
- Visit the ServiceNow Store to view more info on the integration as well as download a user guide. There are other guides available as well.
- CrowdStrike Falcon® Endpoint: Link
- Have an administrator of your instance install the Application(s).
Once the app is installed, enter the API information in the ‘Configurations’ section found by searching CrowdStrike in the Navigator. Configurations allow you to select several options such as incident creation and assignment groups.
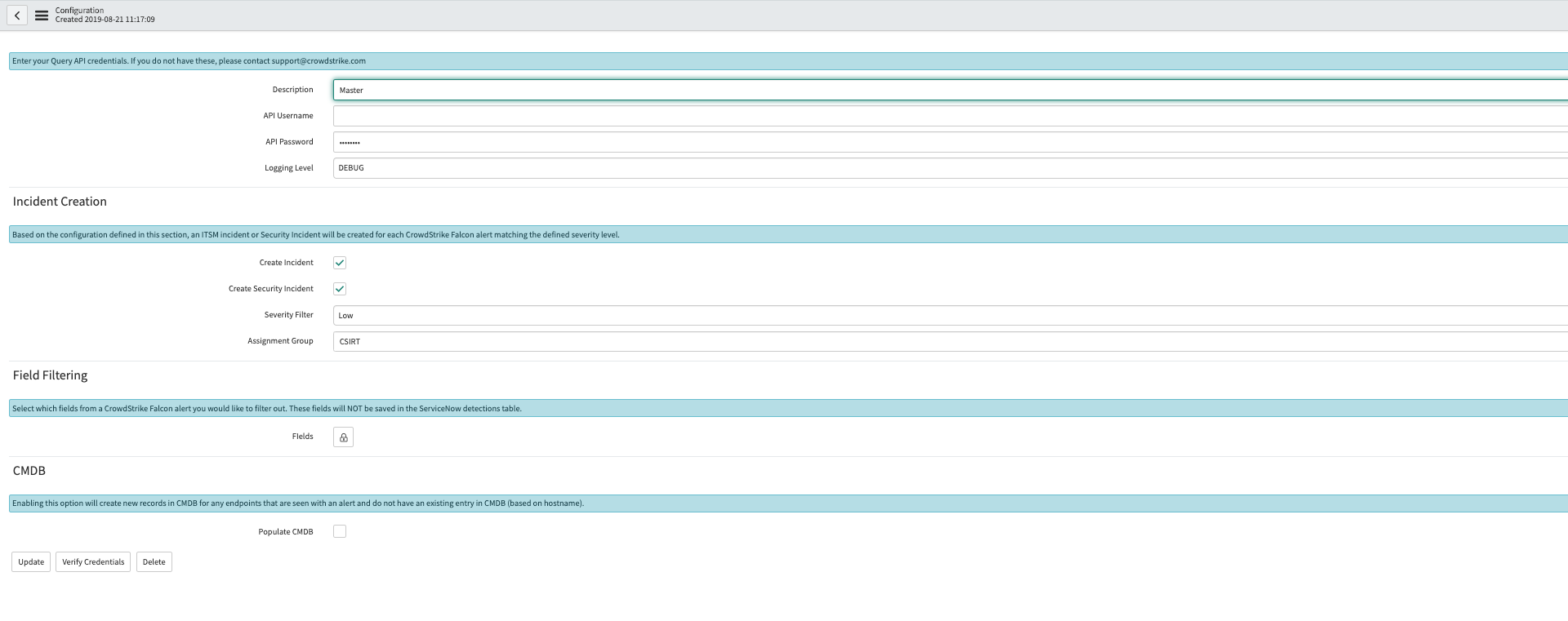
How can customers use CrowdStrike event data within the ServiceNow interface?
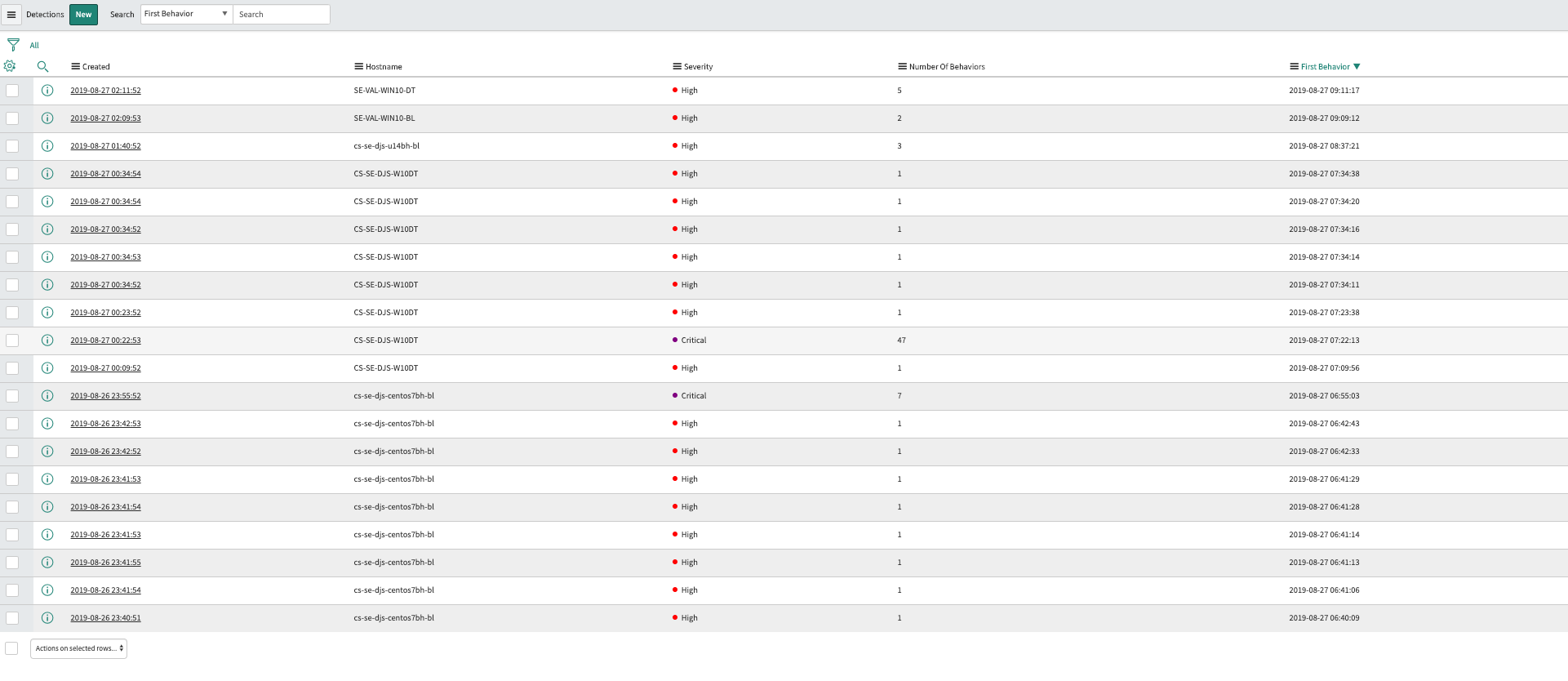
Once you have installed and configured the ServiceNow integration, you will begin to receive a feed that will populate the “Detections” module within the CrowdStrike application. This allows you to view new threats at a glance.
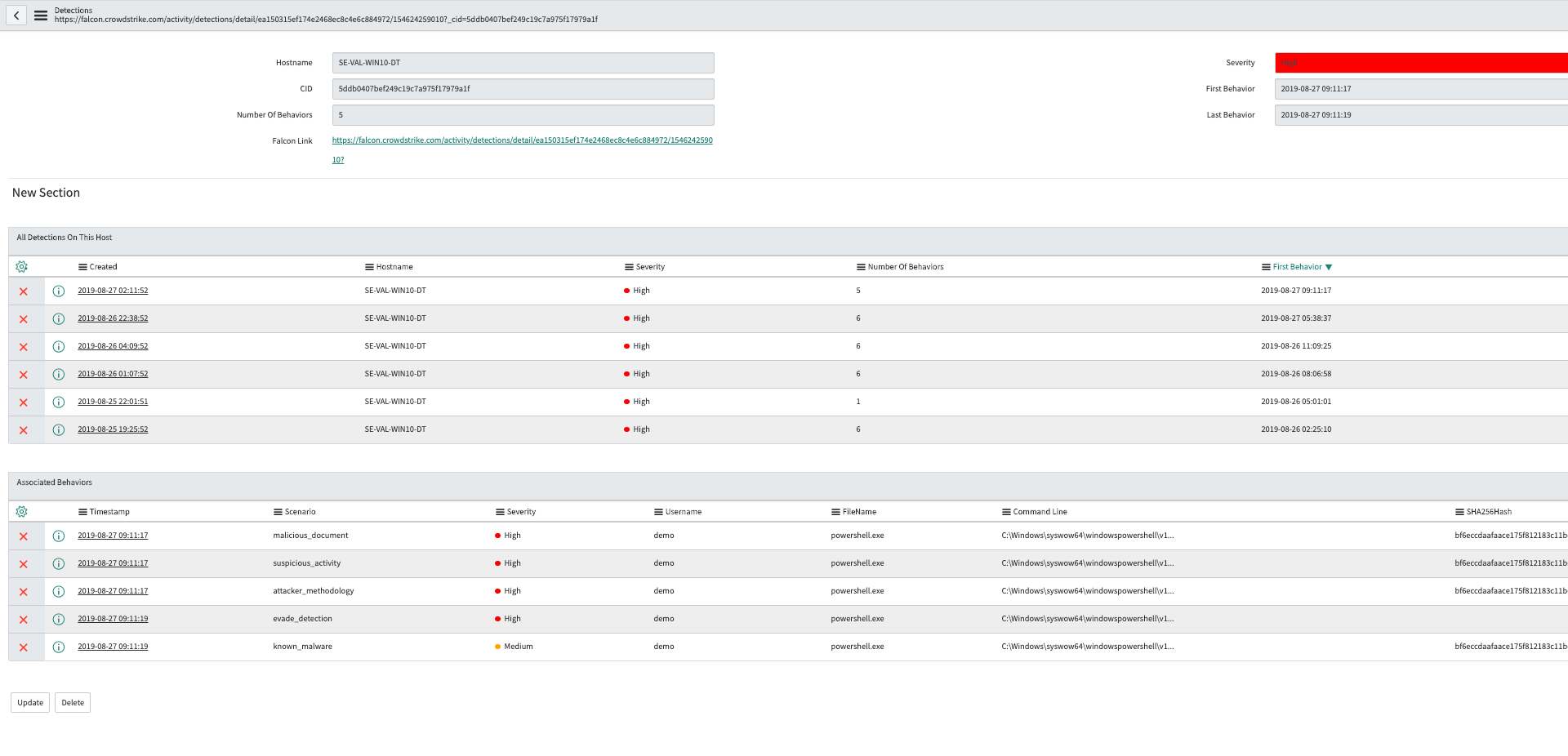
You will be able to click into a detection to view more information about it, such as its severity and relevant metadata surrounding the event.
Conclusion
CrowdStrike’s ServiceNow integration heightens the usability of Falcon event data allowing your incidents responders to quickly identify and complete remediation of threats on your endpoints. Our API first approach makes it possible for you to leverage the CrowdStrike event data as needed to optimize your workflows and maximize the efforts of your overworked security staff.
More resources
- CrowdStrike 15-Day Free Trial
- Request a demo
- Guide to AV Replacement
- CrowdStrike Products
- CrowdStrike Cloud Security
Content provided by Dixon Styres


