How to Leverage Falcon Sandbox Analysis
Introduction
This document and video will illustrate the power of Falcon Sandbox and how it differentiates itself from other solutions in the market.
Video
Prerequisites
Subscription: Falcon Sandbox
What is Falcon Sandbox?
Falcon Sandbox is a malware analysis tool that can be delivered via the cloud or on premise. It provides a safe, complete malware analysis to help streamline investigations and enable security operations teams provide faster threat protection and response.
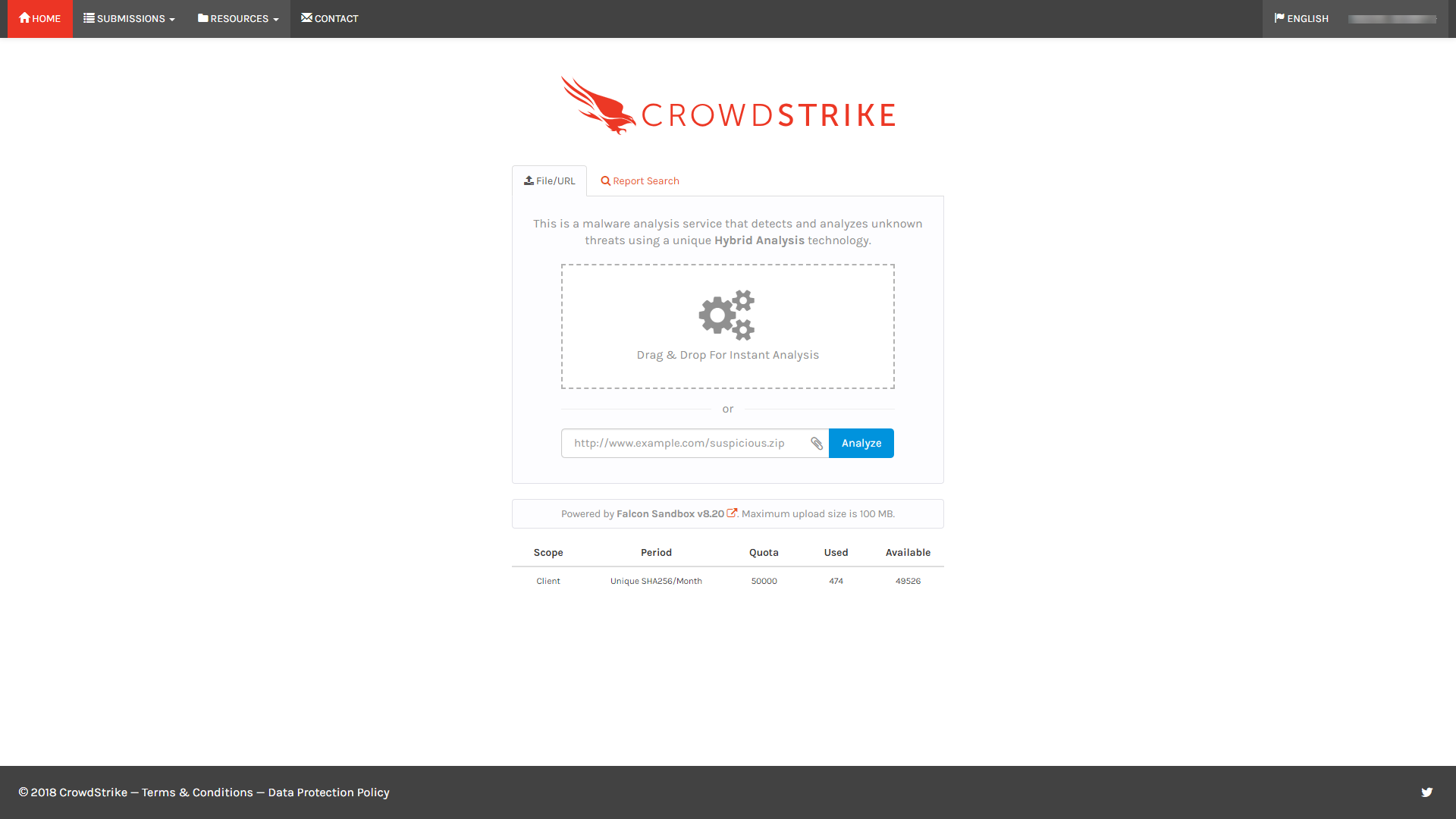
Falcon Sandbox also provides customization options such as operating systems for detonation, command line parameters, variables and passwords.
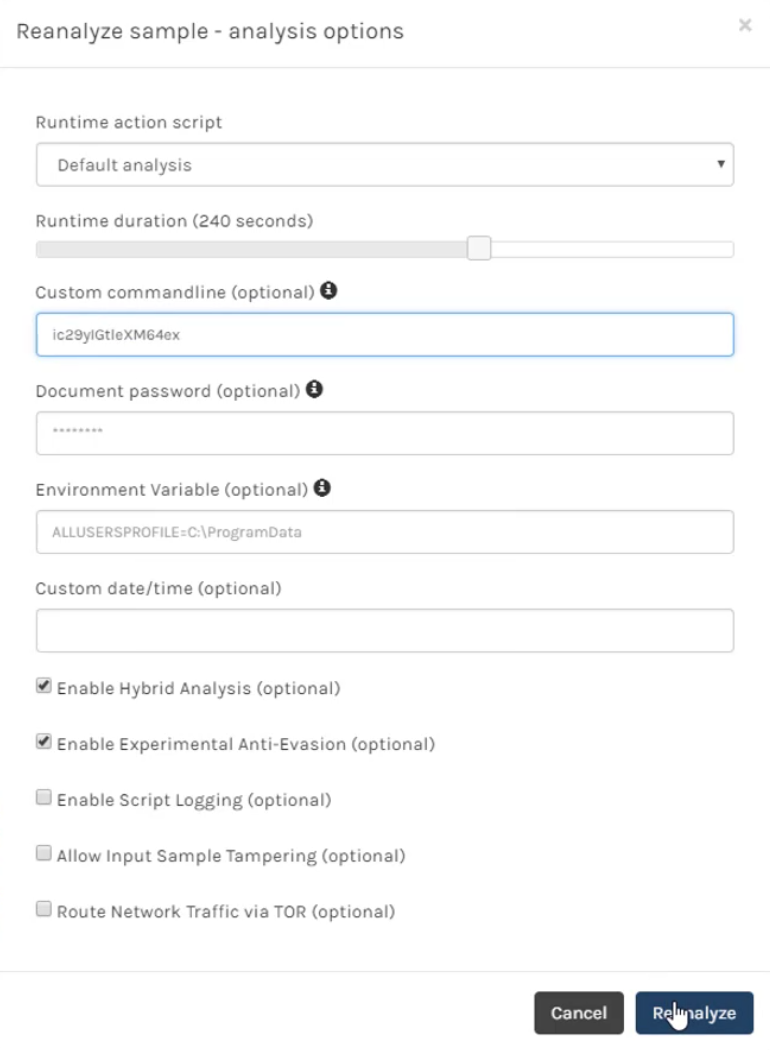
How does Falcon Sandbox analysis add value?
After submitting a sample for analysis, the sandbox will run the sample and collect critical information on its behavior.
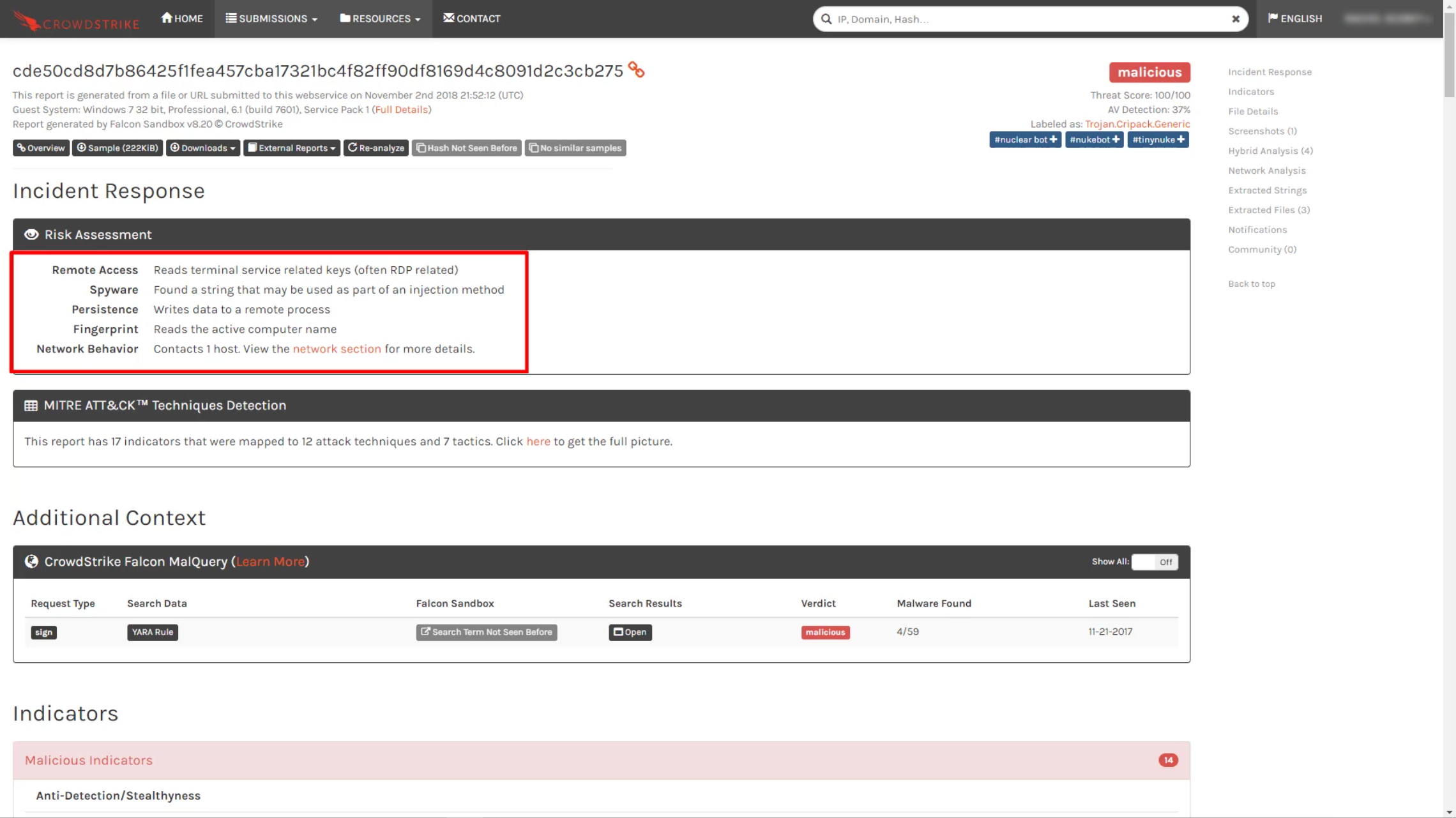
Immediately, you are presented with a threat assessment and score. In this case, the file was found to be malicious with a 100/100 score. The top of the report provides the hash of the file as well as a risk assessment overview.
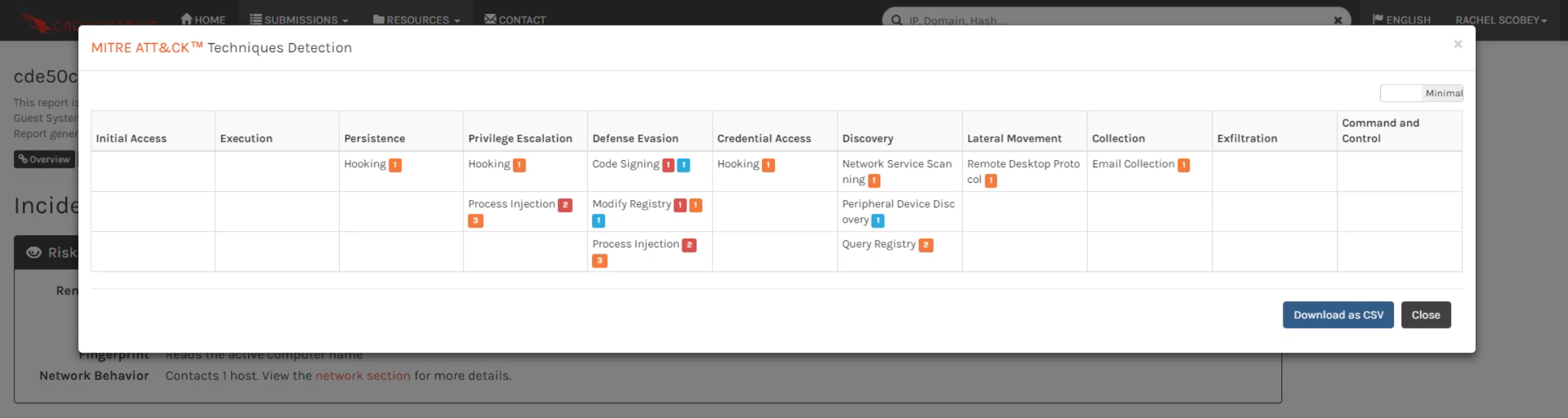
There is also a link to the MITRE ATT&CK techniques that are related to the sample. This information summarizes the likely objectives of the malware and the techniques used to accomplish those objectives.
Further down in the report is a complete breakdown of all of the observed indicators. They are categorized as malicious, suspicious and informative.
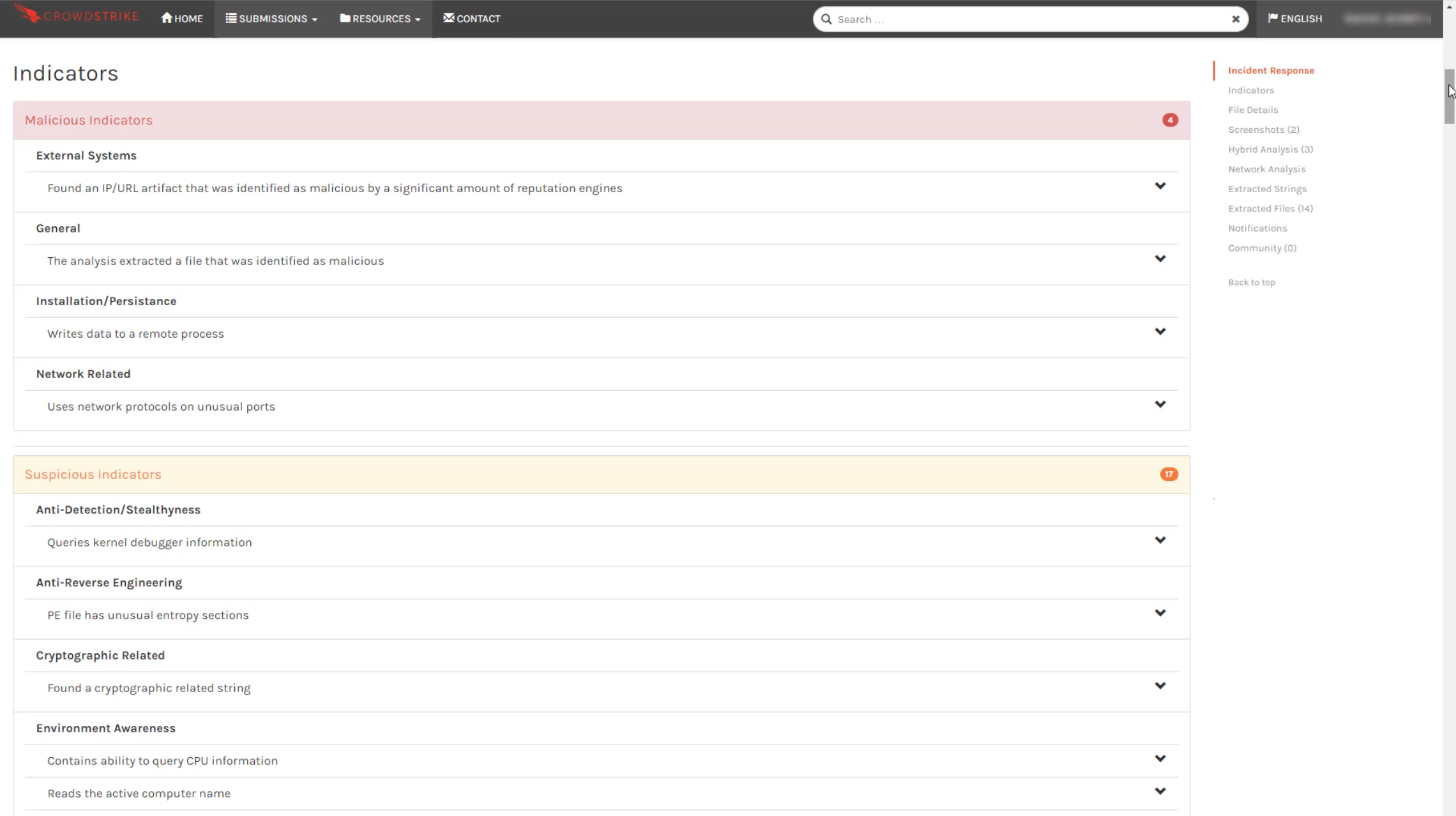
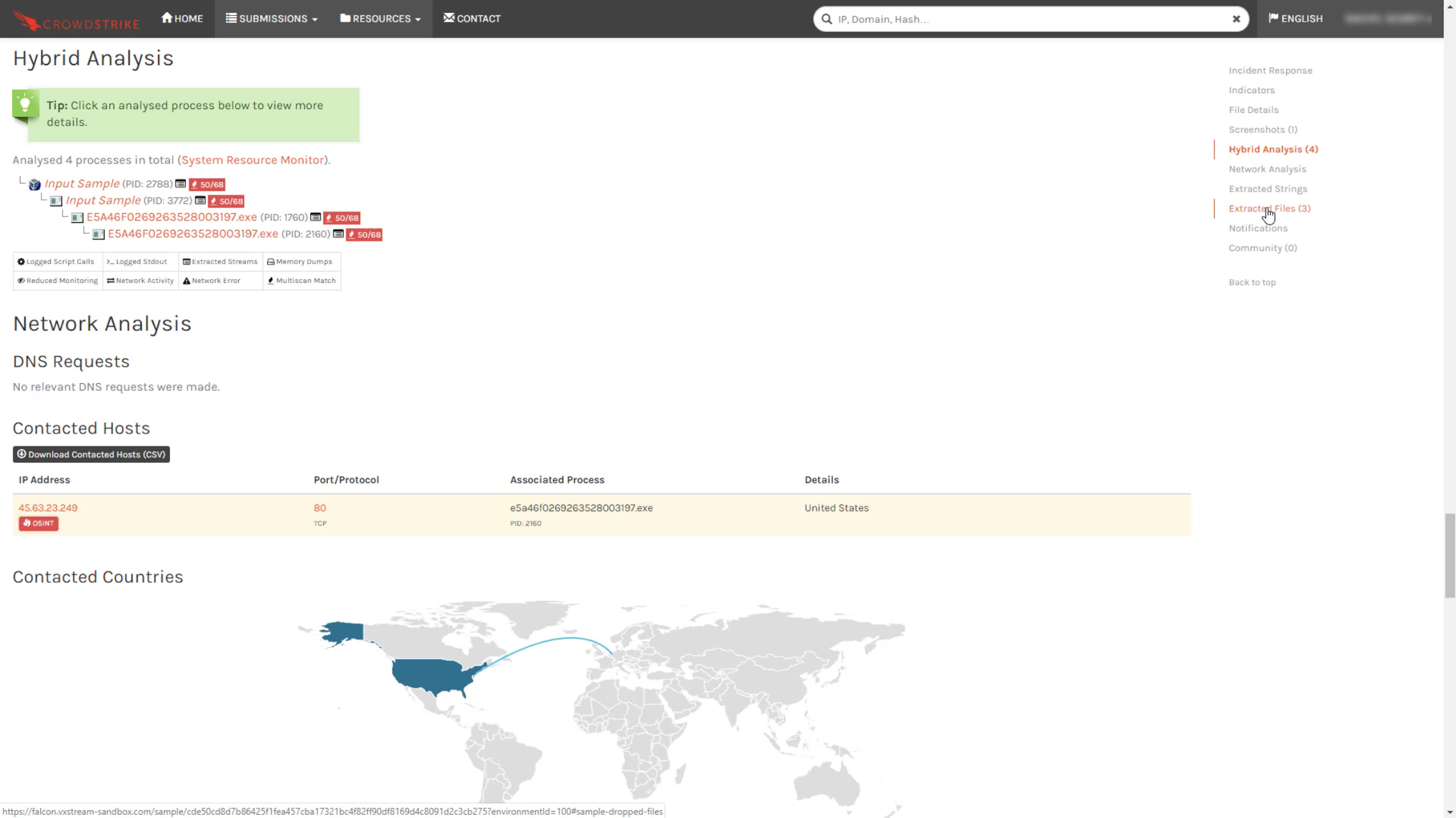
In addition to that, the hybrid analysis provides a process tree and access to additional information about how the sample behaved including details of any API calls, registry changes, etc.
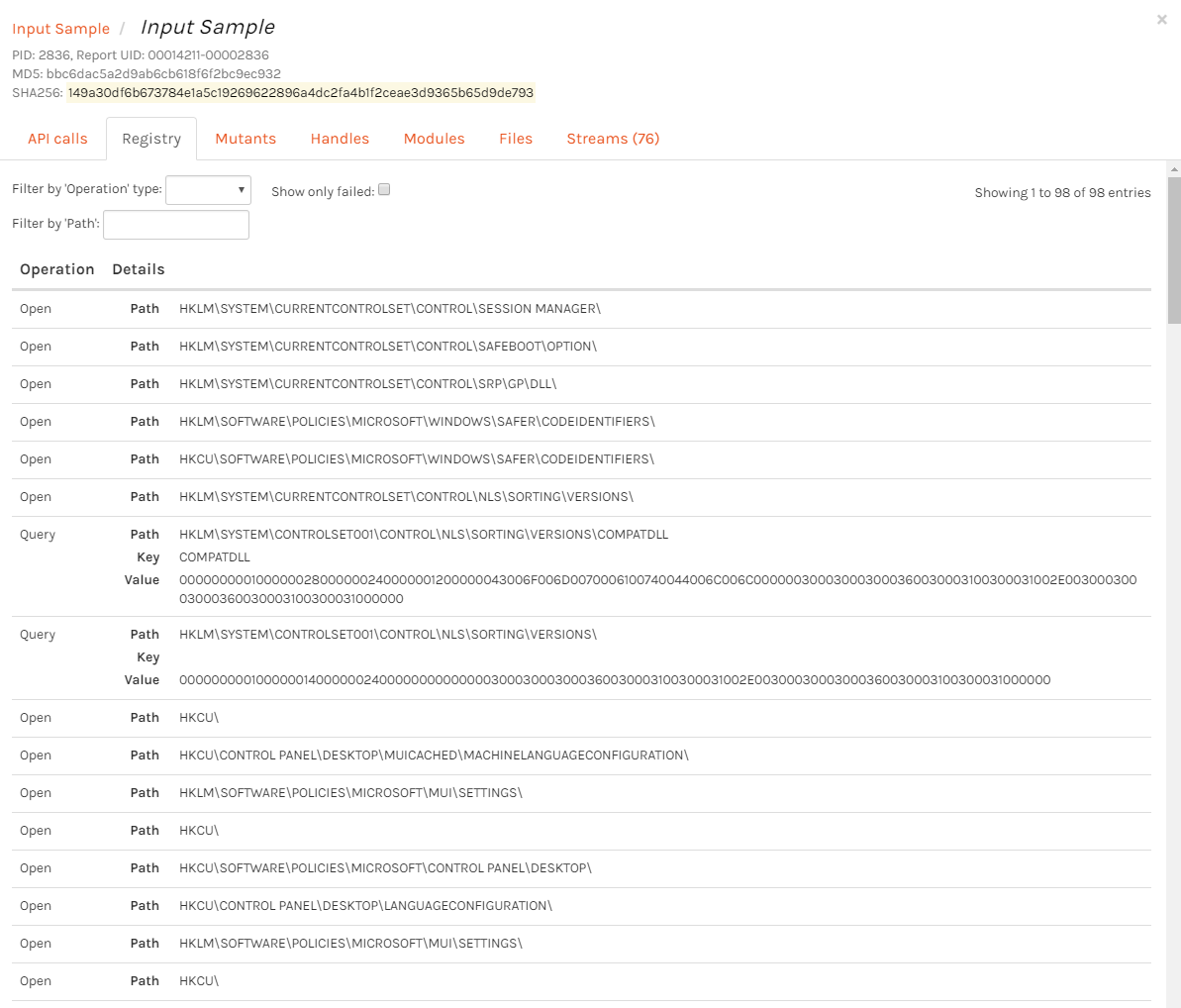
How can Falcon Sandbox improves overall security?
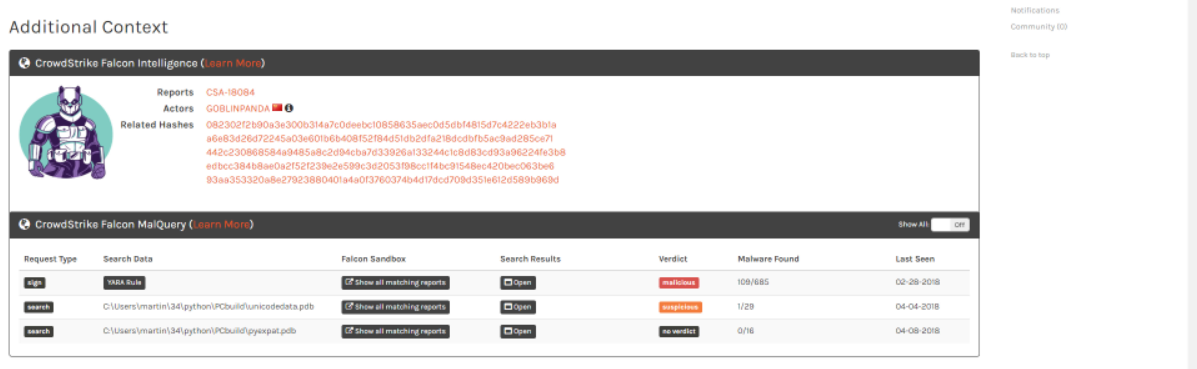
For samples that can be attributed to a bad actor, Falcon Sandbox will include that information in the sandbox report. This lets you know who is targeting your organization so that you can take steps to protect the organization accordingly.
The Sandbox can also provide actor attribution including a link to the full actor profile. With that attribution, you can see the larger picture and take action on indicators like known command and control domains and leveraged vulnerabilities.
Falcon Sandbox analysis also includes integration with CrowdStrike’s Malquery tool. This compares the provided sample against CrowdStrike’s unparalleled repository of malware to find potential commonalities and relationships. You can see the hash values of related malware and download Yara rules for your own investigations.
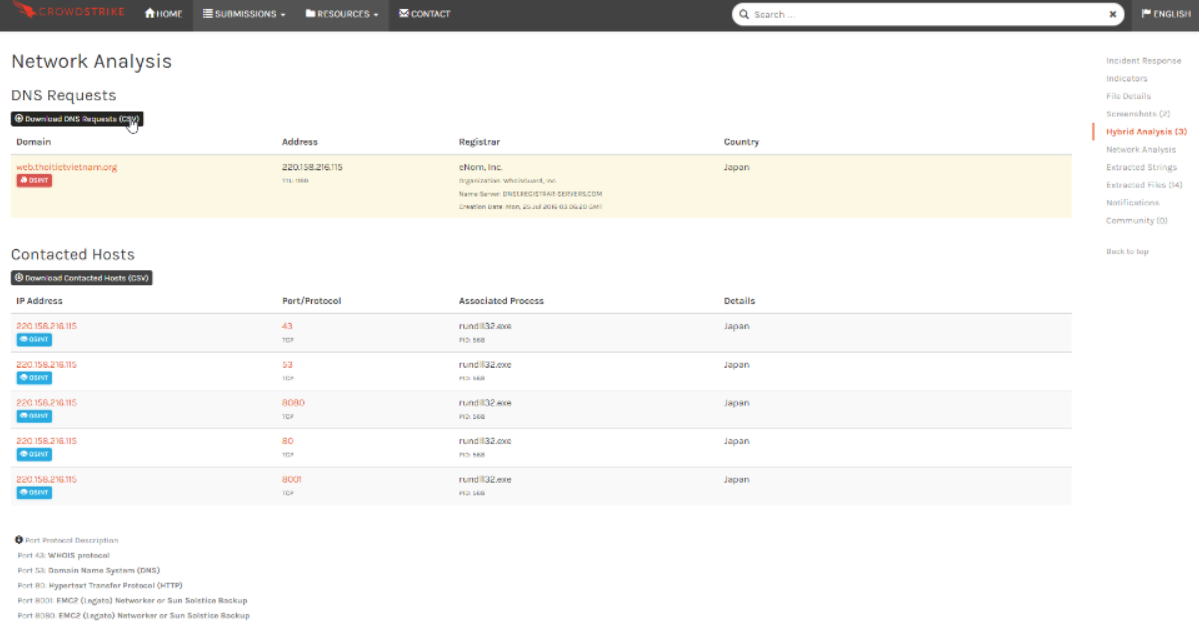
Lastly, under Network Analysis, you will find the option to download a list of resolved domains, IP addresses, and ports used by the sample the sample. That information can be shared with the perimeter security team to establish blocks against any such traffic in the future.
Conclusion
Falcon Sandbox gives malware researchers and security operations teams the information that they need to provide their organization with faster threat protection and response. Deployment options offer flexibility while the tool provides customization options, hybrid analysis and contextual information to provide your organization with actionable information.
More resources