How to Manage a Host Firewall with CrowdStrike

Introduction
This document and video will demonstrate how CrowdStrike can manage the native Windows and Mac OS host firewall. Through the existing agent and cloud based platform, this option provides companies centralized management of enterprise firewall features on the endpoint.
Video
How are firewall rules defined?
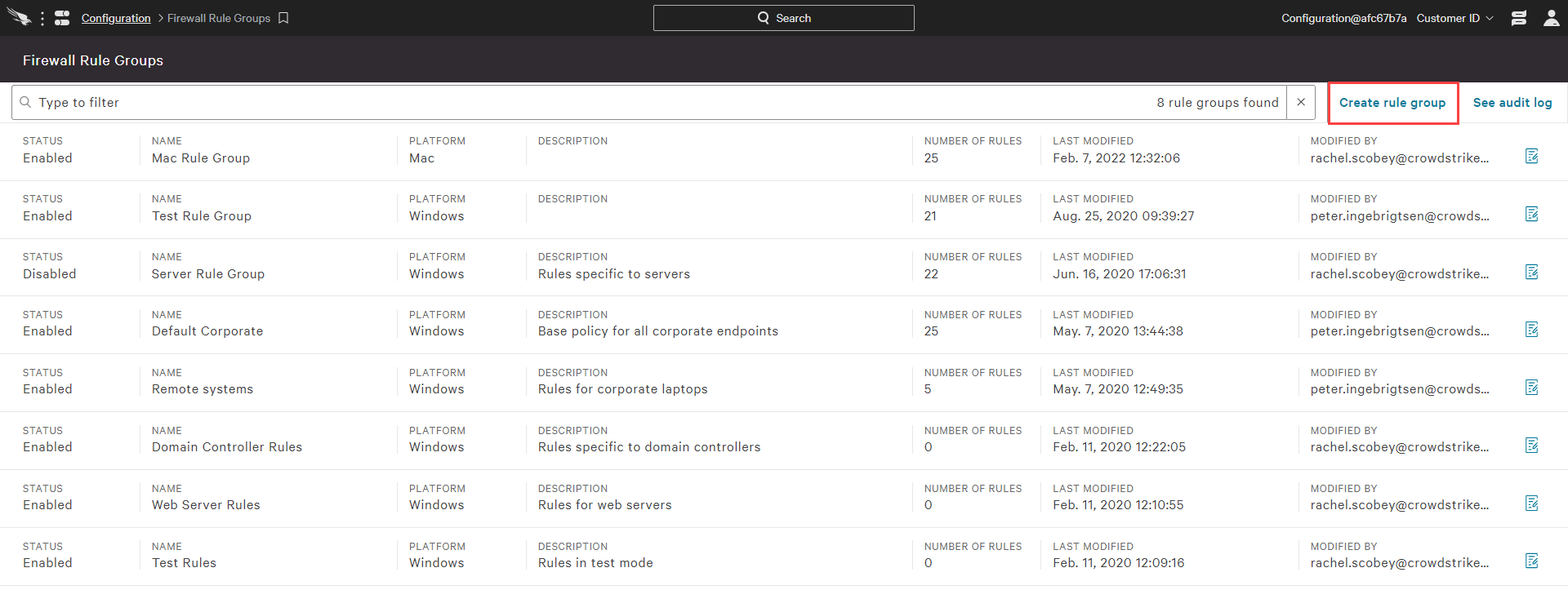
In the Crowdstrike UI under “Configuration”, the list of existing “Firewall Rule Groups” can be viewed including status and platform. From that screen, you have the option to edit existing groups or “Create rule group”.
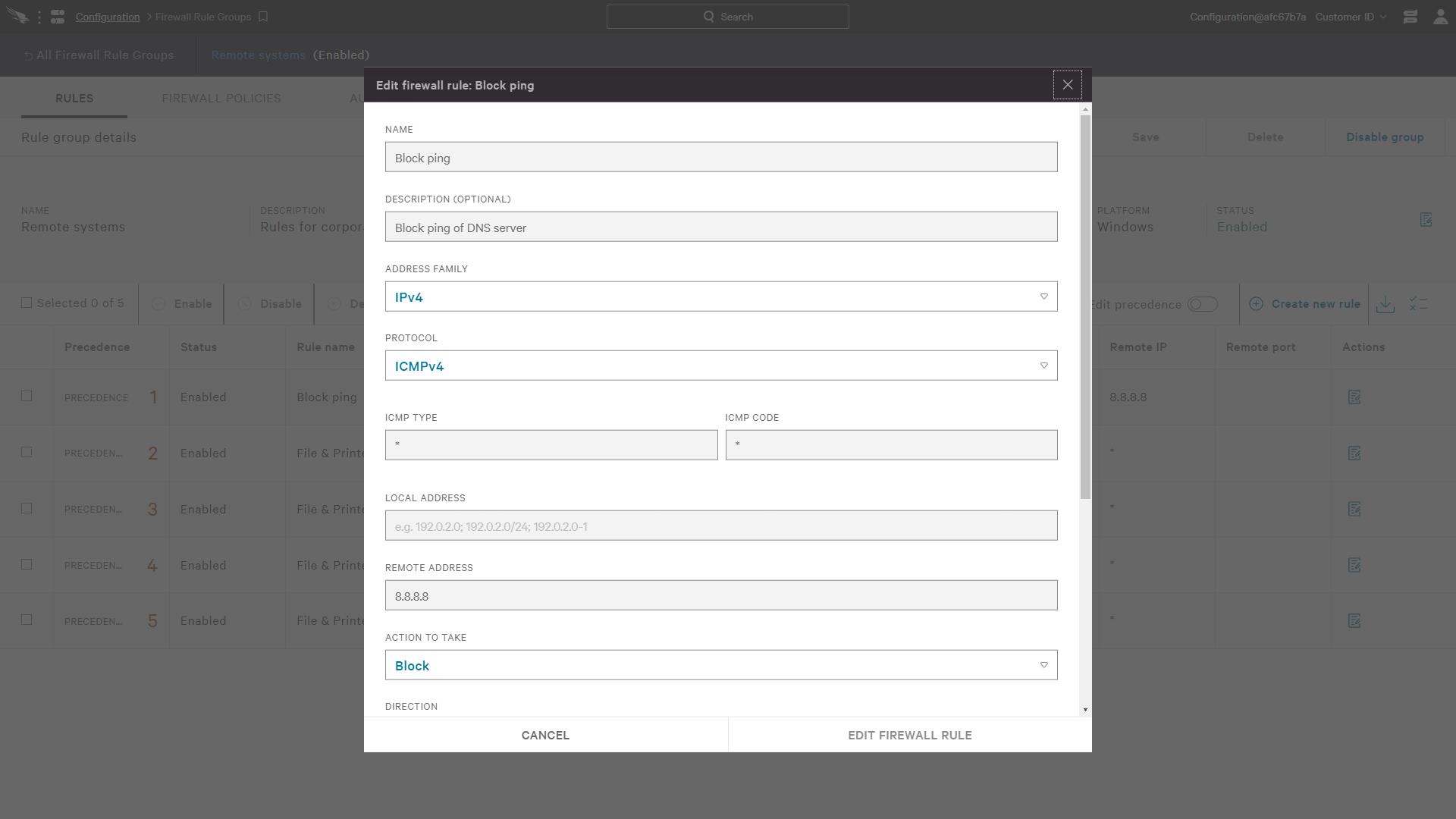
For each newly created group, there is an option to clone an existing group or start a new group. As new firewall rules are added, the name and description are entered along with configuration details such as network direction, protocol and applicable addresses.
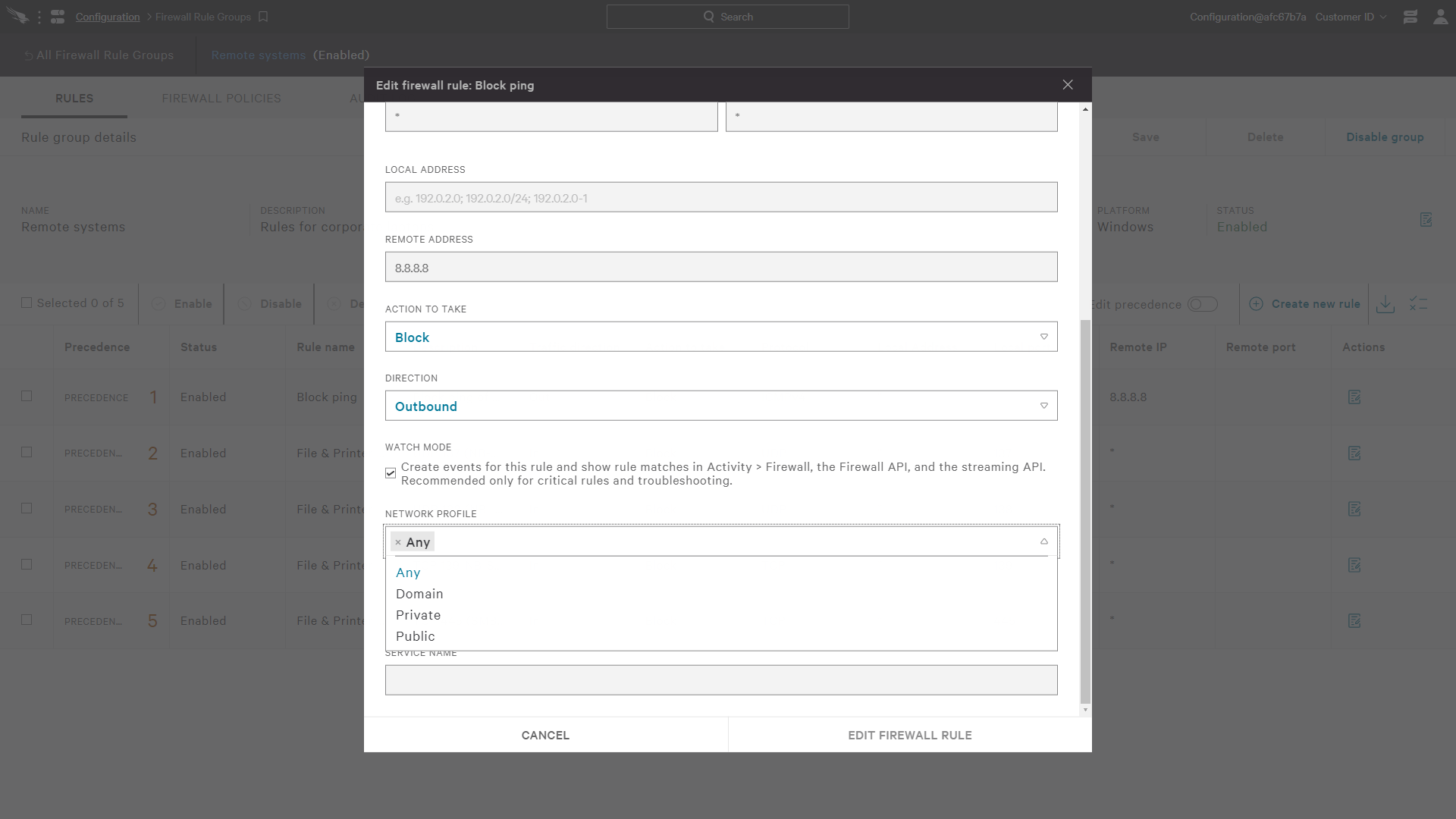
For each rule, there is an option to specify a network profile. This location awareness feature helps ensure that rules are applied in the right circumstances like when a user is on an internal network where the domain is reachable versus a public or private network.
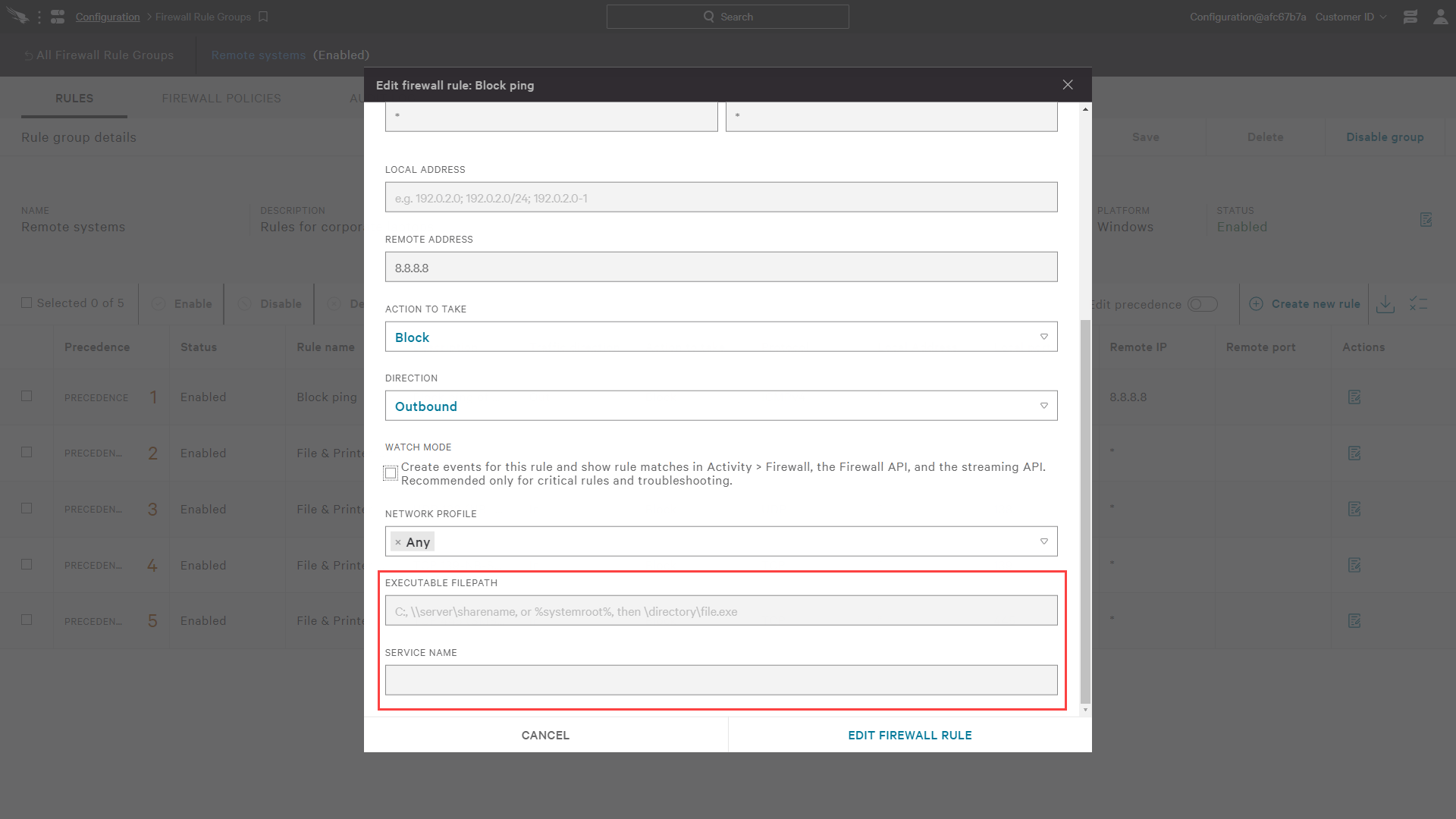
CrowdStrike also looks beyond simple network traffic and provides the ability to enforce rules based on the source process. This additional visibility gives administrators more granular control over how and when rules apply.
How are firewall rules incorporated into policies?
Once the rule groups are created and enabled, they can be added to firewall policies that are defined per platform. Creating a new policy is much like creating a new rule group. Upon creating a new policy, there is an option to clone an existing policy or start with a blank slate.
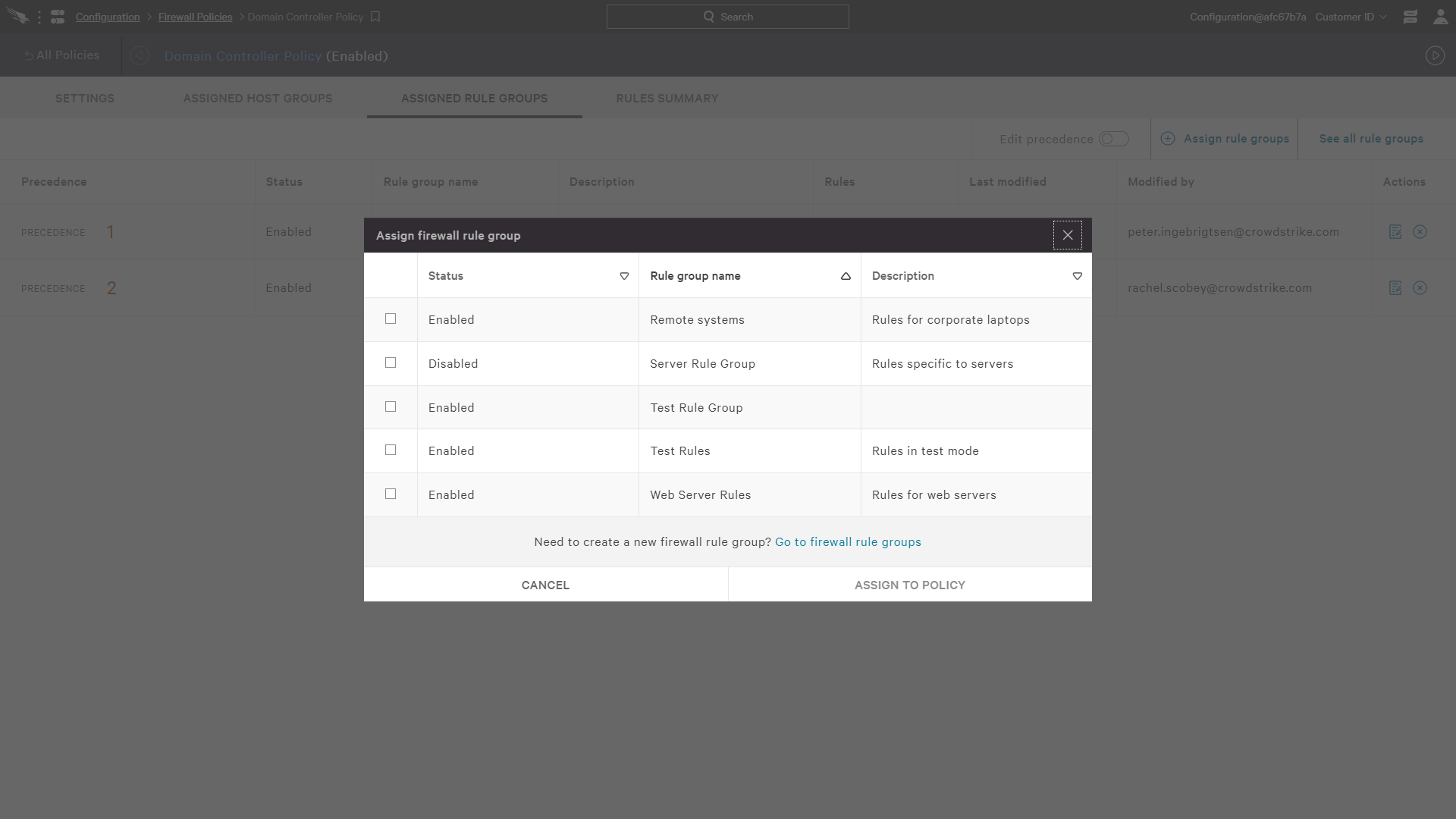
Once the policy created has been created, you can choose to assign rule groups to that policy.
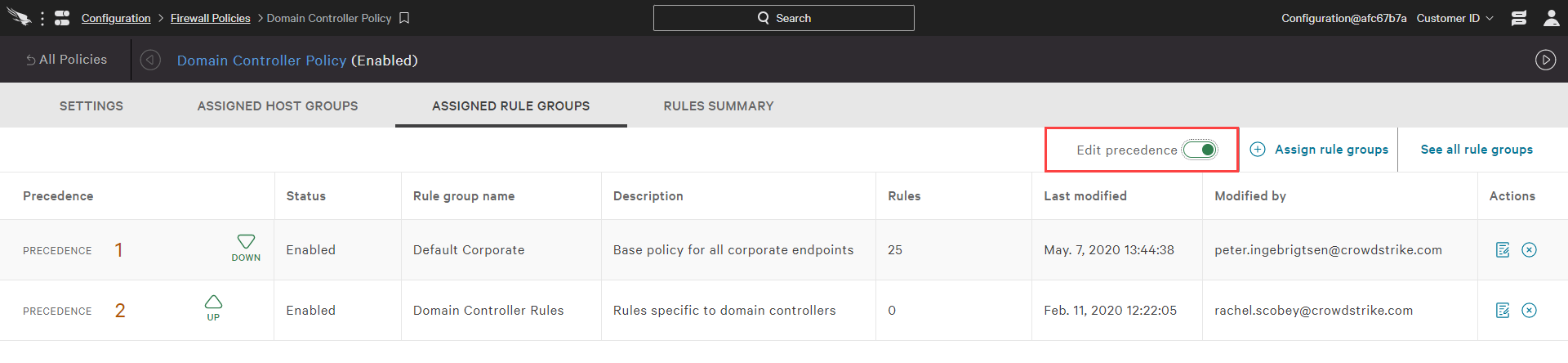
In both policies and rule groups, you have the option to edit the order of precedence.
How are firewall policies deployed to endpoints?
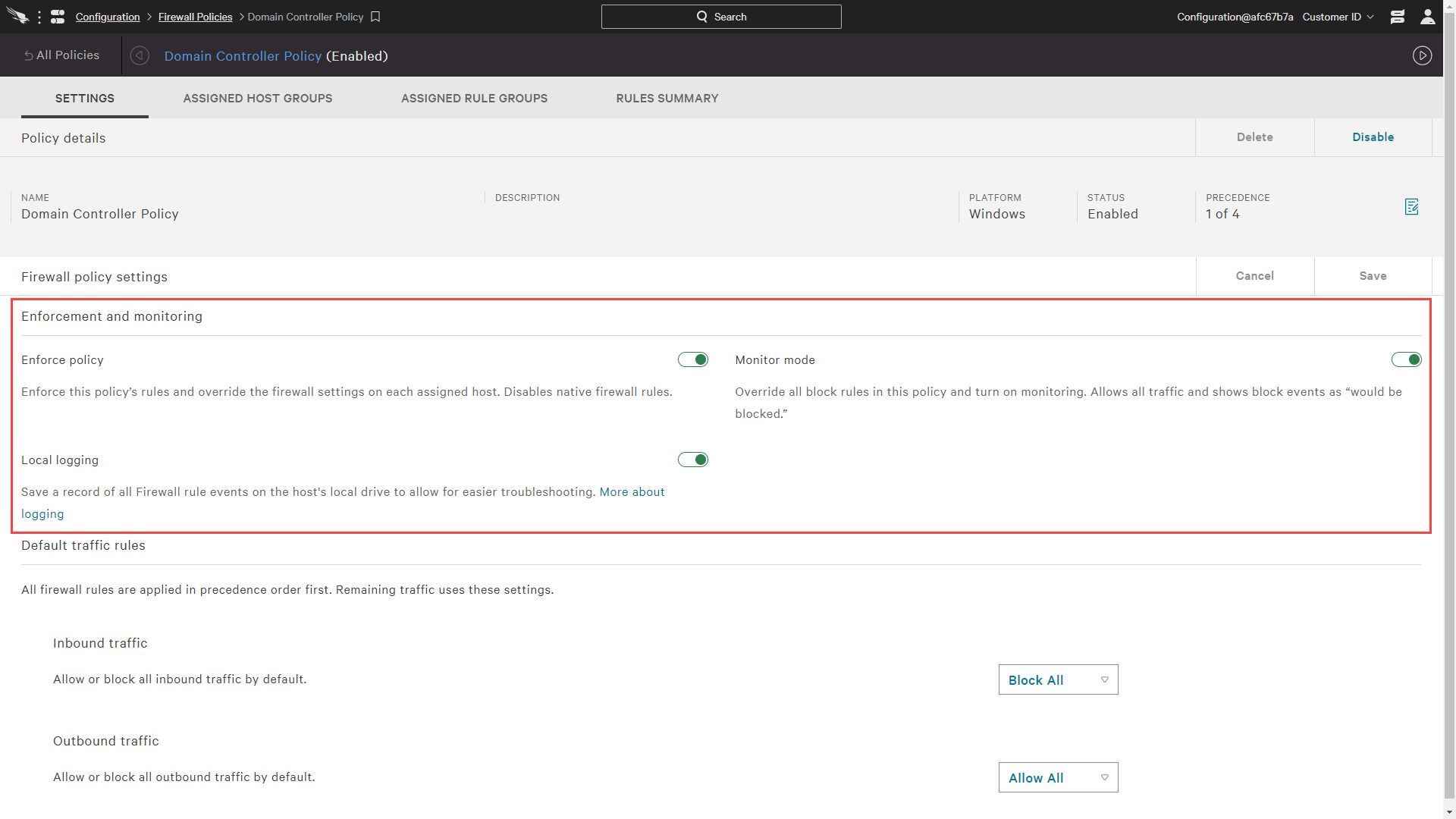
Before assigning host groups, it is important to confirm the policy is enabled with proper enforcement. Policies can be put in enforcement or monitor mode. Enforcement is required for Falcon to be seen as the firewall provider on the endpoint. There are also options for monitor mode and local loggings of firewall events.
Host groups can be added to the policy under the “Assigned Host Groups” tab.
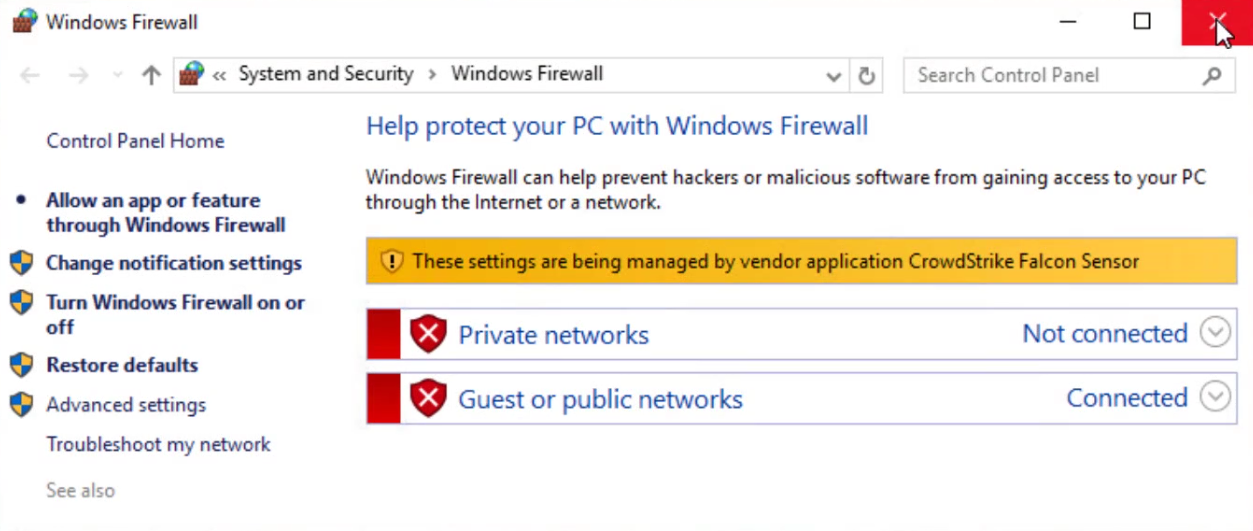
Once an enabled policy has been deployed to the endpoint, users would expect a status message like this for the Windows firewall.
How can firewall rules be tested?
For each firewall rule, there is an option to enable “Watch Mode”. This gives you visibility to rule matches through Falcon UI. This option is recommended for critical rules and troubleshooting only as it has the potential to generate an excessive number of events.
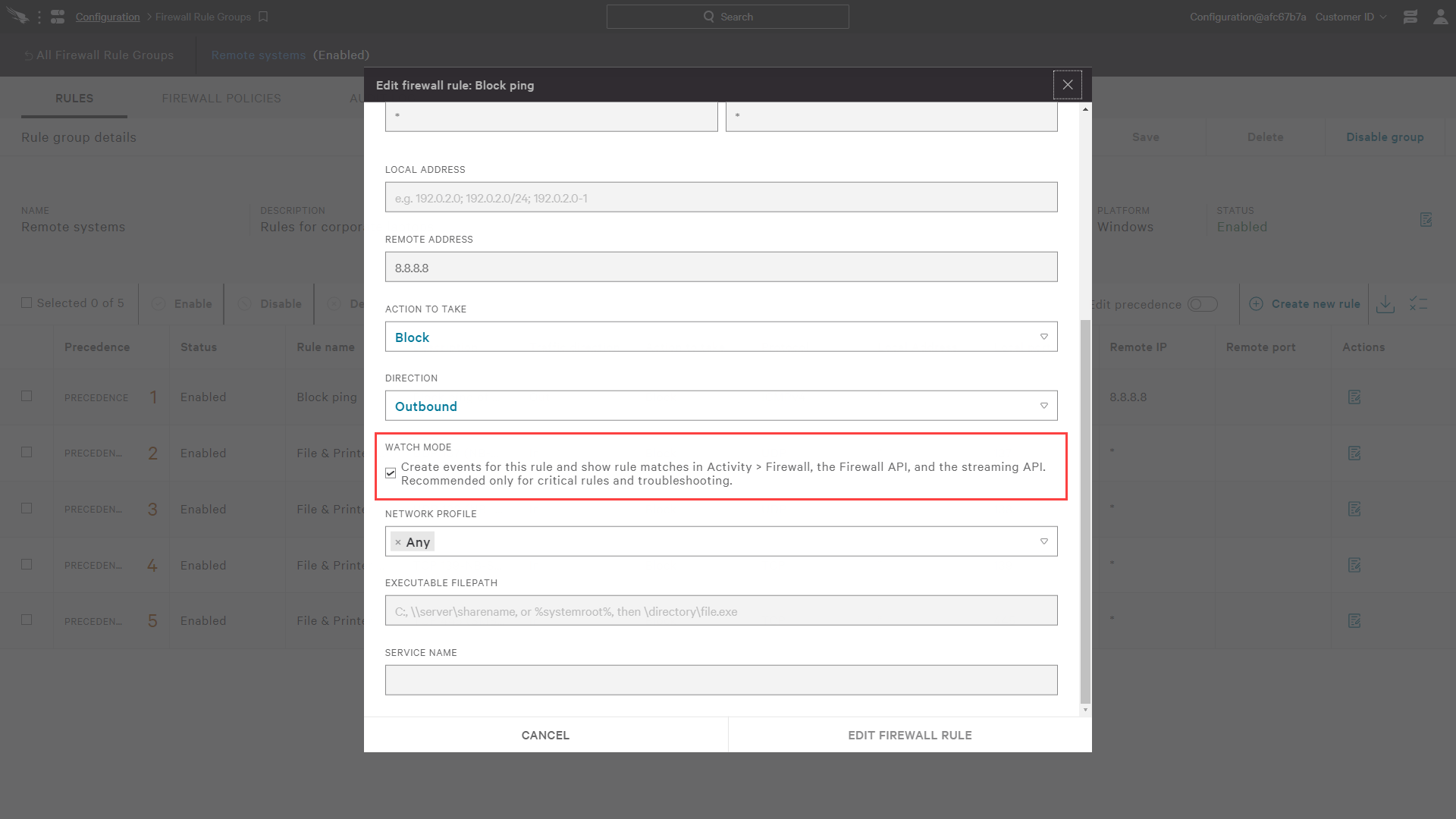
With “Watch Mode” enabled, any event that triggers the rule will be listed in the “Activity” app under “Firewall Events”.
Closing
CrowdStrike enables companies to manage native OS firewall capabilities through the power of the cloud native Falcon UI. This solution delivers central management of enterprise features including process based rule enforcement and location awareness through a single agent with no additional performance impact.