How to Prevent Malware Infections with Falcon Endpoint Protection

Introduction
In this document, you are going to see how to prevent malware with CrowdStrike Falcon®. Falcon uses multiple methods to prevent and detect malware. These methods include Machine Learning, exploit blocking, custom blacklisting and behavioral analysis with what we call Indicators of Attack (IOAs). This unified combination of methods protects you against known malware, unknown malware and file-less malware. This document will show you how to configure each method.
Video
Instructions
1: Go the prevention settings of the Falcon User Interface
You can configure prevention features in the Configuration App. Once in the App, make sure you are in Prevention Policy. Please note that you need Admin privileges to configure the prevention features on the Prevention App settings page. Also, the configuration changes are almost immediate and only take a couple of seconds to be updated on the endpoints.
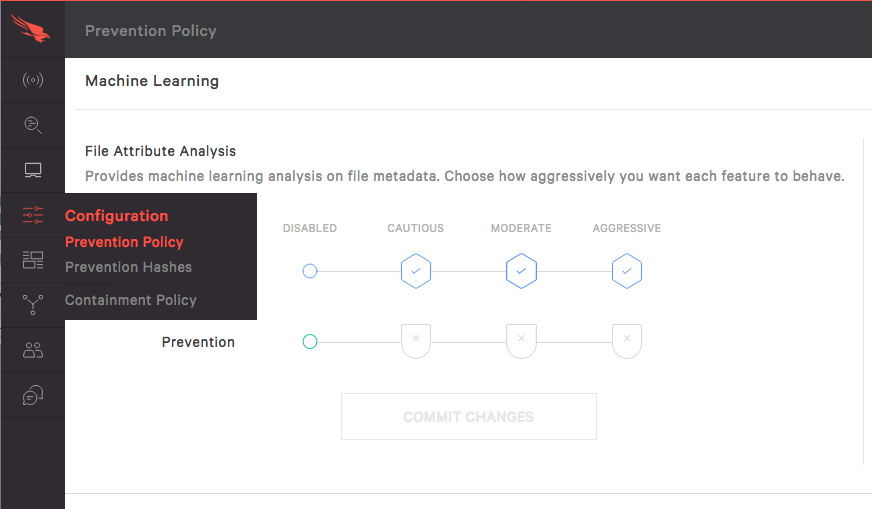
2: Configure Machine Learning
Let’s start by configuring Machine Learning. Machine Learning allows Falcon to block malware without using signatures. Instead, it relies on mathematical algorithms to analyze files.
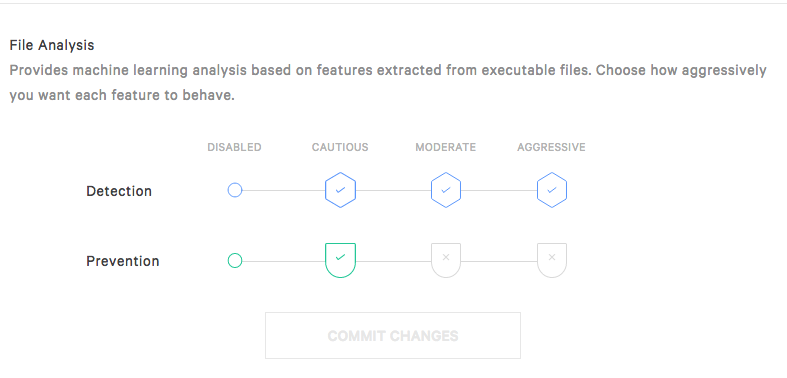
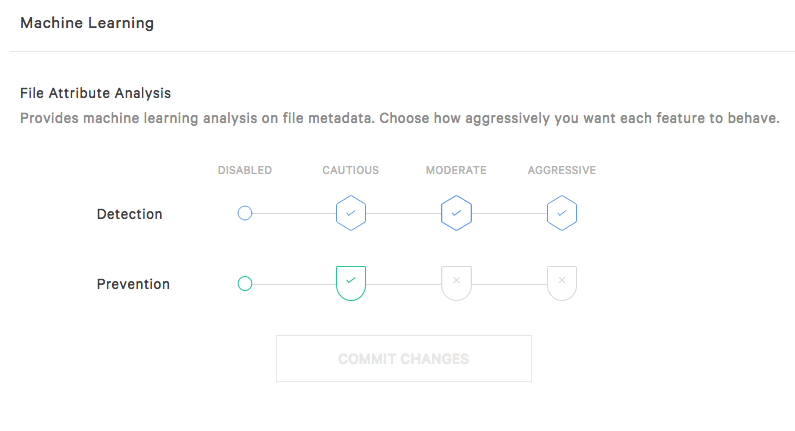
The File Attribute Analysis provides machine learning analysis on file metadata, while Static File Analysis provides analysis on features extracted from executable files.
Notice that you can set up independent thresholds for detection and for prevention. So, you could for example choose to receive detection alerts for any suspicious files, even if it’s a just a little bit suspicious by selecting Aggressive, but you can choose to automatically prevent only if the machine learning is very sure that it’s malicious, by selecting Cautious.
To edit those settings, click Edit and then chose the setting you want. You can set prevention and detection separately to either Disabled, Cautious, Moderate, or Aggressive, but logically, the Detection settings always have to be stronger or equal to the Prevention setting.
Click Save when you are done
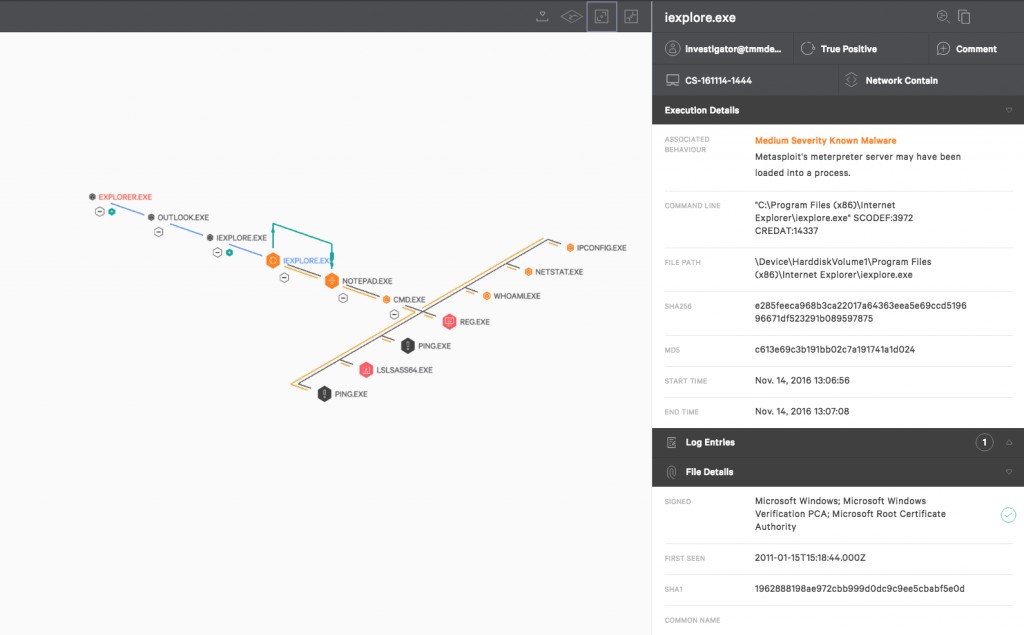
This is what a Machine Learning Block will display in the Falcon User Interface.
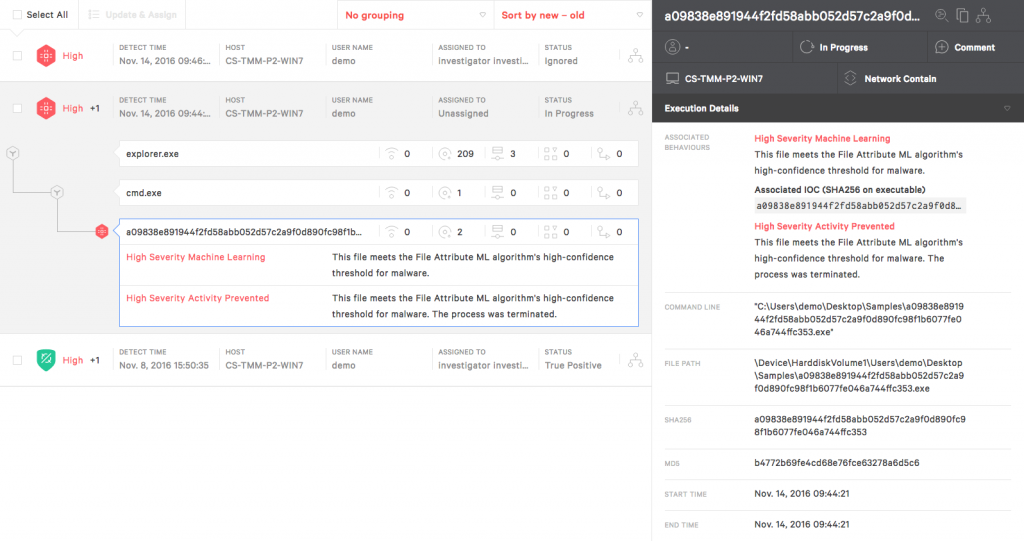
Below is an example of ransomware being caught by machine learning.
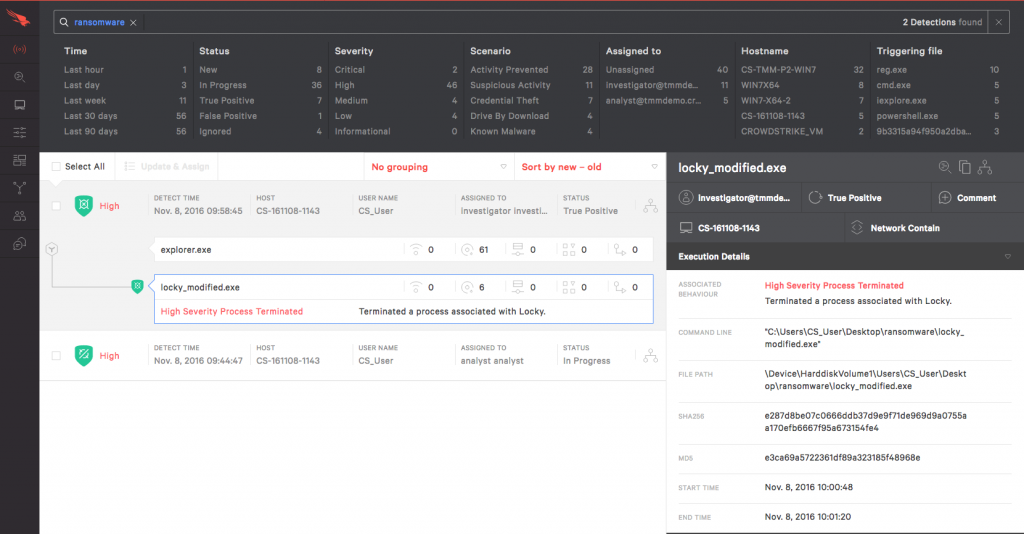
3: Preventing file-less malware with exploit blocking
The Falcon machine learning engine is great to block known and unknown malware but, malware does not always come in the form of a file that can be analyzed by machine learning. Malware can be deployed directly into memory using exploit kits. This is why Falcon also includes an exploit blocking function.
Note:
File-less malware is malware that is not written to disk but is run straight into memory. This is different from malware-free attacks where the adversary do not use malware. Instead they might, for example, use social engineering, exploits or credentials thefts. Falcon also prevents malware-free attacks with exploit blocking and Indicators of Attacks.
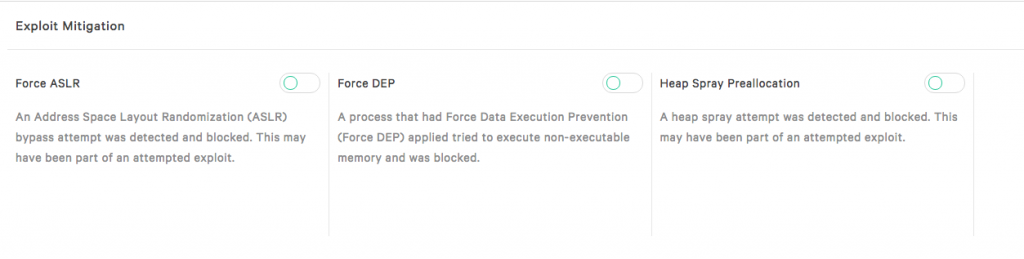
Each of the exploit protection can be turned on or off in the same window as the machine learning configuration.
To turn an exploit mitigation on or off, just slide the toggle for the exploit mitigation you want to change.
In our example we are going to turn on Force ASLR mitigation.
Let’s slide the toggle to the right and confirm the changes.
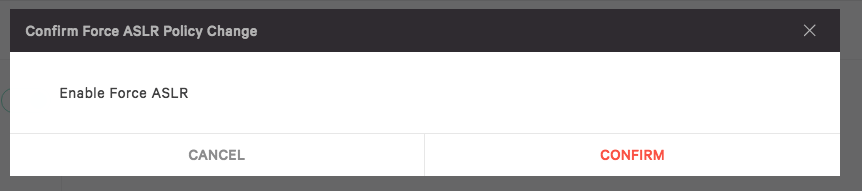
The toggle is changed to green and enabled.
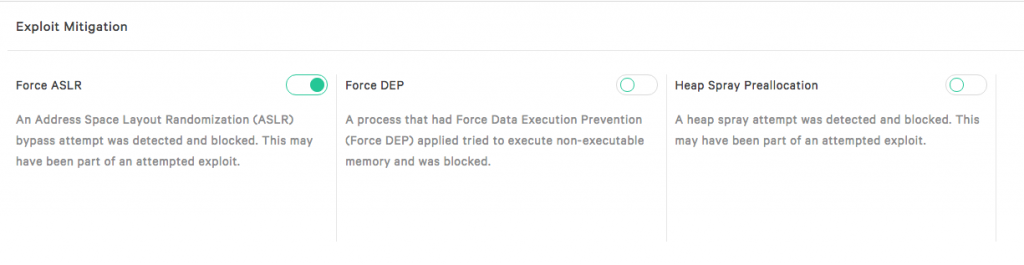
If you want to disable the prevention for that exploit, slide to toggle to the left and confirm that you want to disabled.
Here is an example of exploit blocking detection in the Falcon User Interface.
4: Preventing malware with Indicators of Attacks
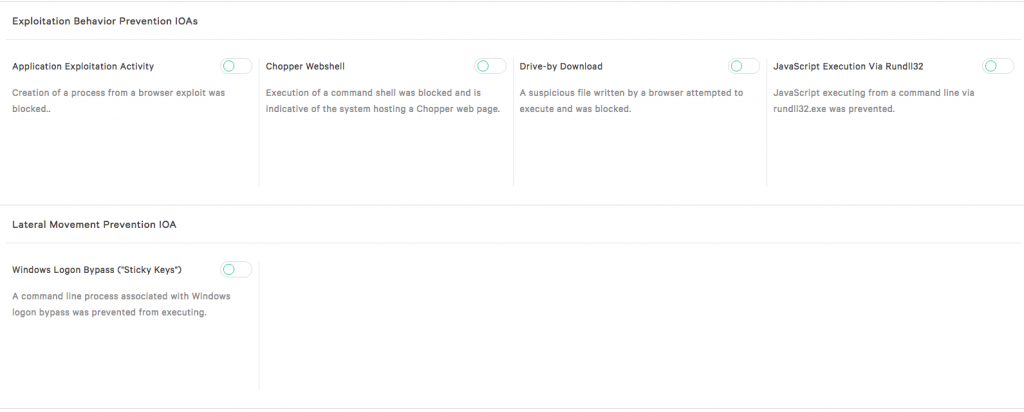
Exploit blocking provides another layer of protection but may not be sufficient at times because some file-less malware do not use exploit kits. Ransomware, for example, has some infamous examples of file-less ransomware that does not use exploits. This is why Falcon also uses Indicators of Attacks, or IOAs, to protect the systems. IOAs look across both legitimate activity and suspicious activities and detect stealthy chains of event that indicate malware infection attempts. Because most IOAs also prevent attacks that do not use malware, they are enabled by default. But some, such as adware and ransomware specific IOAs can be configured.
You can enable or disable them in the current window by sliding the toggles just like we did for exploit blocking.
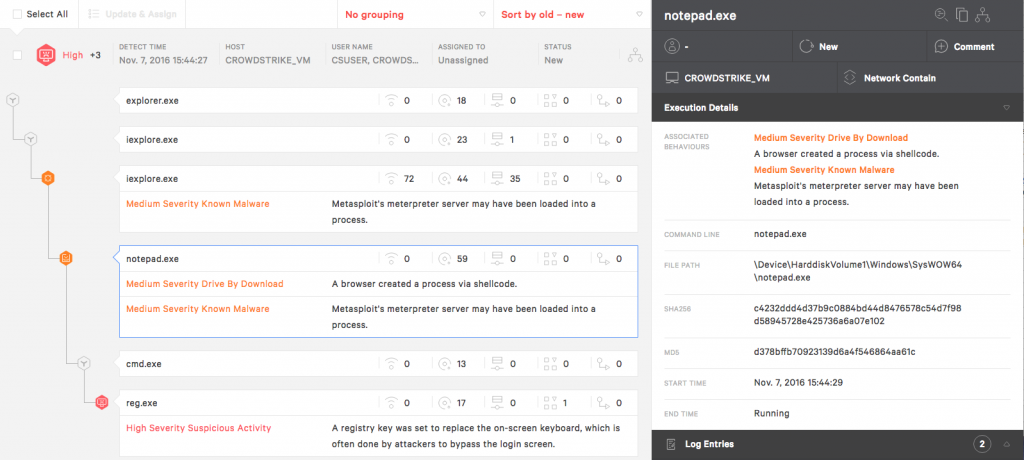
Remember, earlier we saw an example of ransomware blocked by machine learning. Now we can see another ransomware, blocked, but this time, it was prevented by an Indicator of Attack.
5: Preventing malware with custom Blacklisting
There are cases when you might want to blacklist some applications because you are certain that you never want them to run in your environment.
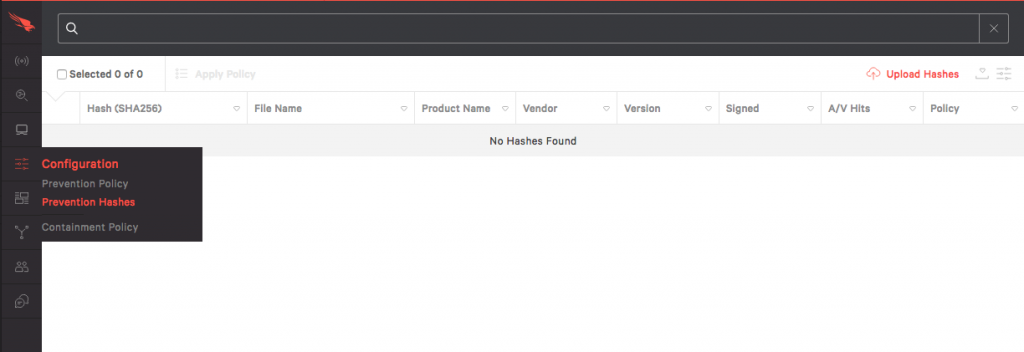
Falcon allows you to upload hashes from your own blacklists or whitelists. For that, we have to be in the Configuration App, Prevention Hashes window. To add hashes to our blacklist select the “Upload Hashes” in the upper right hand corner. Note, you’ll need admin privileges.
Then we’ll drag and drop the list. The list can be a text file with one MD5 or SHA1 hash per line. All valid MD5 and SHA256 hashes will be uploaded. Rows with non-MD5/SHA256 hash format will be ignored.
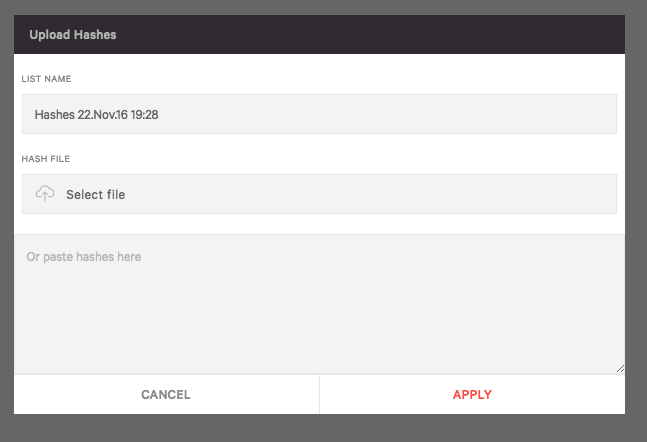
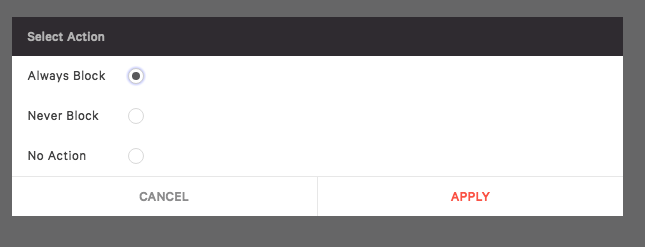
After clicking “Apply” an action to take when hashes are encountered in the environment needs to be selected. If creating a whitelist select “Never Block”. In this case I’ll select “Always Block” and then “Apply”
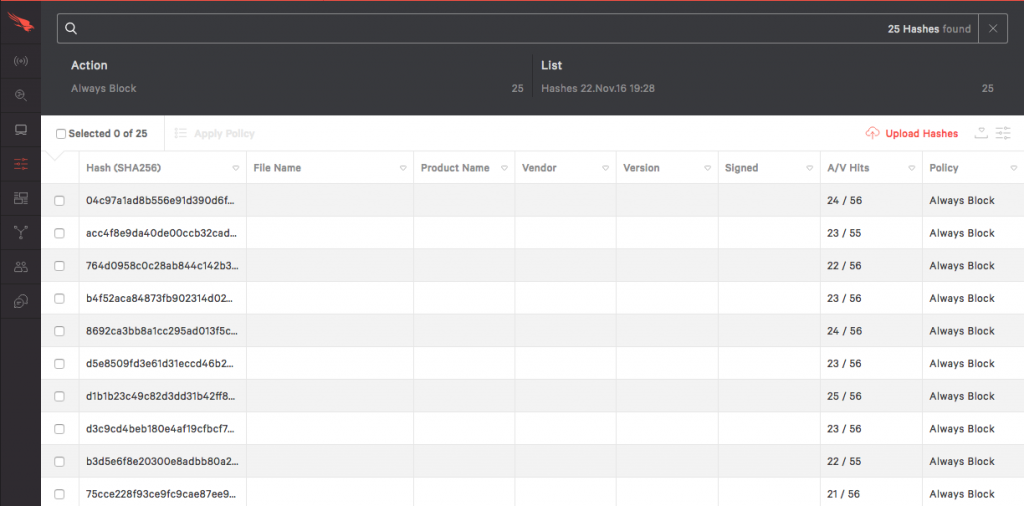
You can see that the hash has been uploaded. If you want to upload more hashes later, click on the upload icon on the top right corner of the window.
Now we also need to make sure that custom blacklisting prevention is enabled.
For that, let’s go back to the settings page and check. If it’s not enabled, you can use to toggle to enable it.
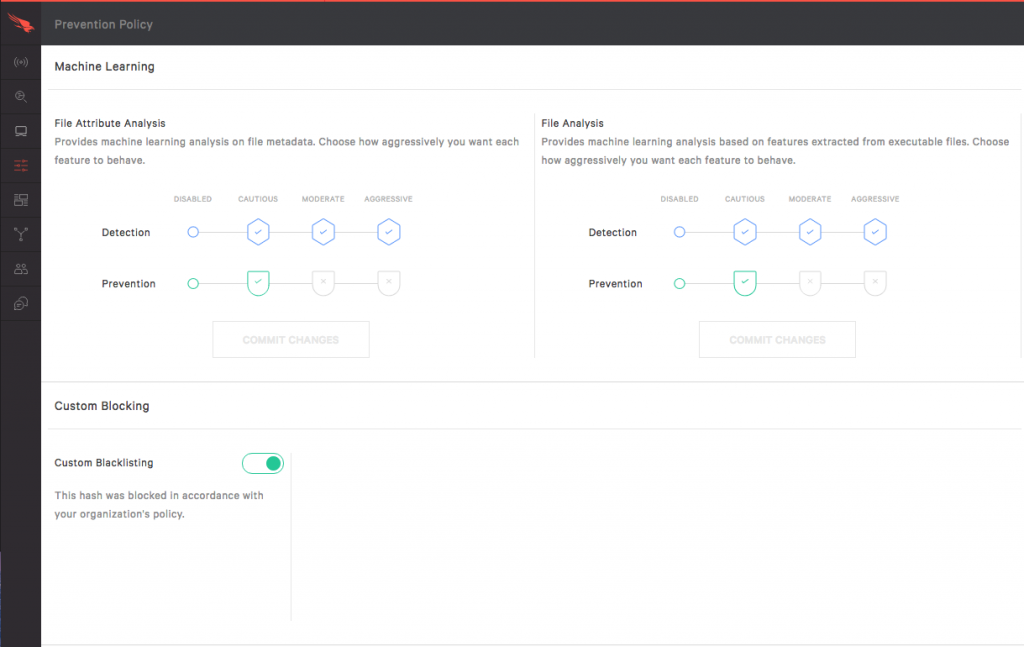
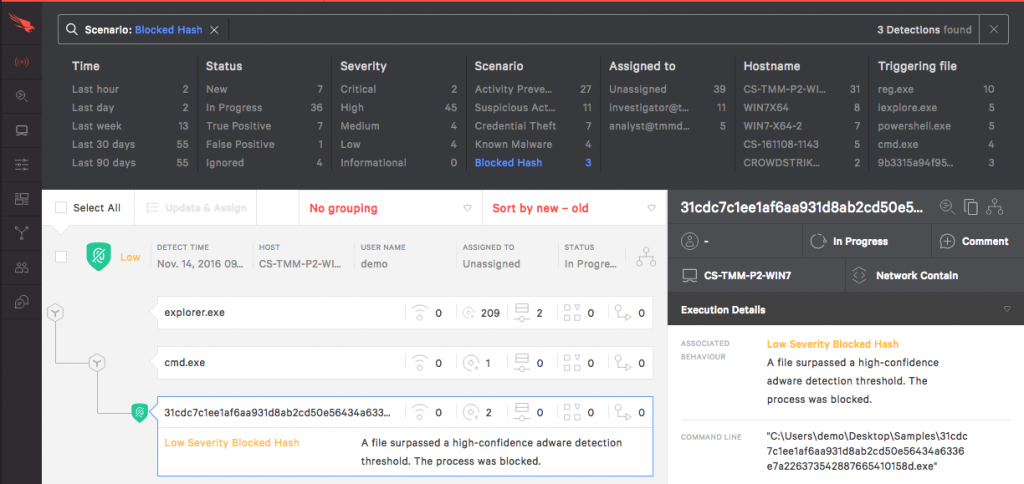
This is how this prevention shows up in the Falcon User Interface. It will show as being blocked according to your organization policy.
Conclusion
Falcon uses an array of methods to protect you against known malware, unknown malware and file-less malware. These methods include:
- Machine Learning
- Exploit Blocking
- Indicators of attack
- Blacklisting and whitelisting
Falcon uniquely combines these powerful methods into an integrated approach that protects endpoints more effectively against both malware and breaches.