Using Falcon Spotlight for Vulnerability Management
Introduction
This document and video will demonstrate how to use Falcon Spotlight to find vulnerabilities in your environment while overcoming the challenges with traditional vulnerability management solutions.
Video
Spotlight for Reporting
Falcon Spotlight leverages CrowdStrike’s single management platform and lightweight agent to provide organizations with access to vulnerability assessment information. The sensor provides real time results on protected systems with no time consuming, impactful system scans or a requirement for any network hardware. In this demonstration, we are going to review three different use cases for Falcon Spotlight and how this solution can add value to your organization.
To access Spotlight, find the Spotlight App in the menu on the left.
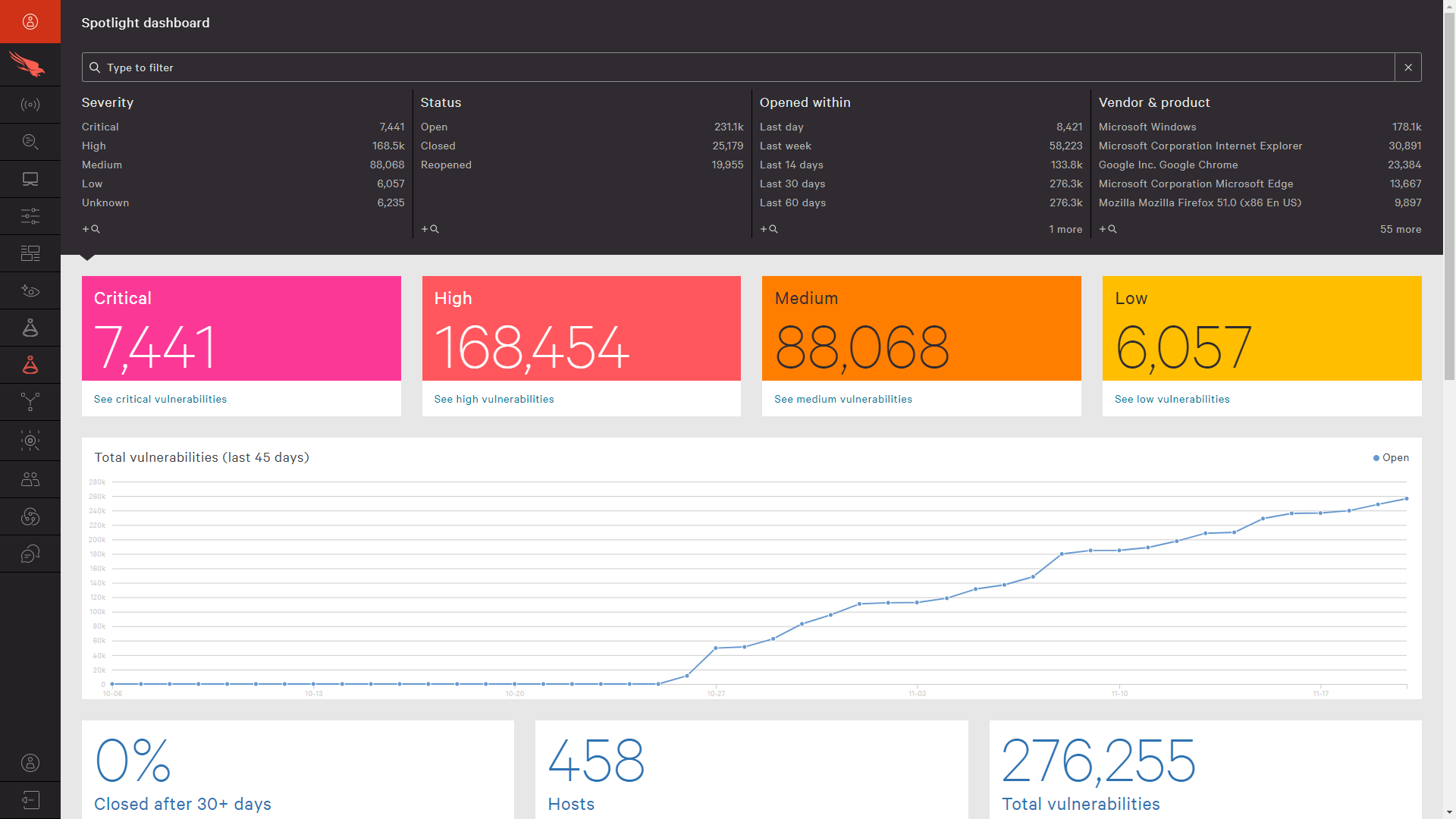
On the main dashboard, you have a top level overview of the vulnerabilities in your environment. The dashboard updates as you pivot and filter the vulnerability data with the Falcon search bar, providing the bigger picture. Clicking on the dashboard tables brings you into a detailed overview for that area of interest.
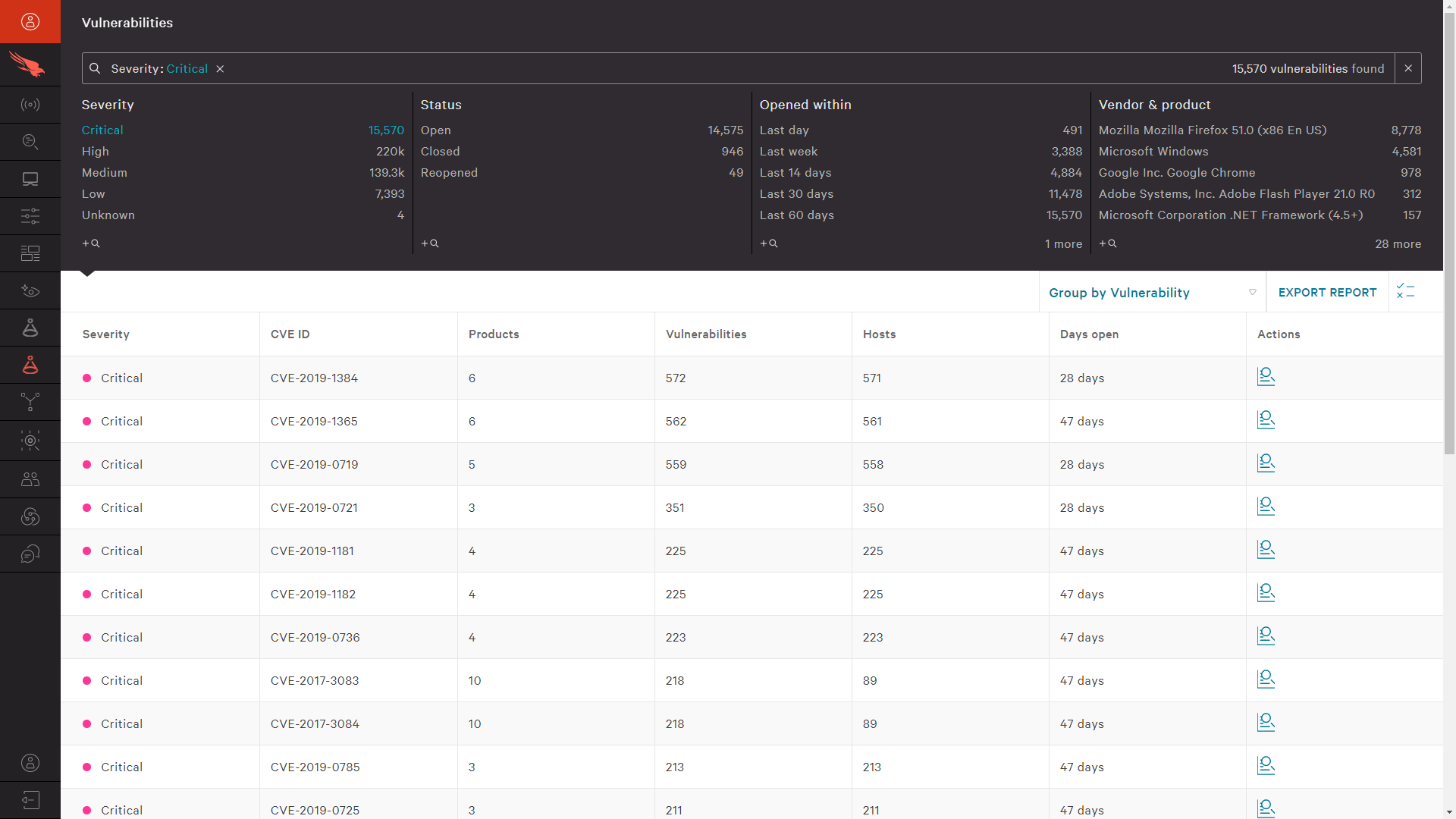
Clicking into the “Critical” CVEs, you are presented with the backing evidence – the list of applicable CVE’s being reporting in your environment. Those details include the specific CVE, a brief description, the published date and the count of vulnerable hosts in the environment. That report also offers the opportunity to drill down further to see a detailed list of vulnerable hosts. On each page, there is an option to export the list making it easy to share the information with patch management teams.
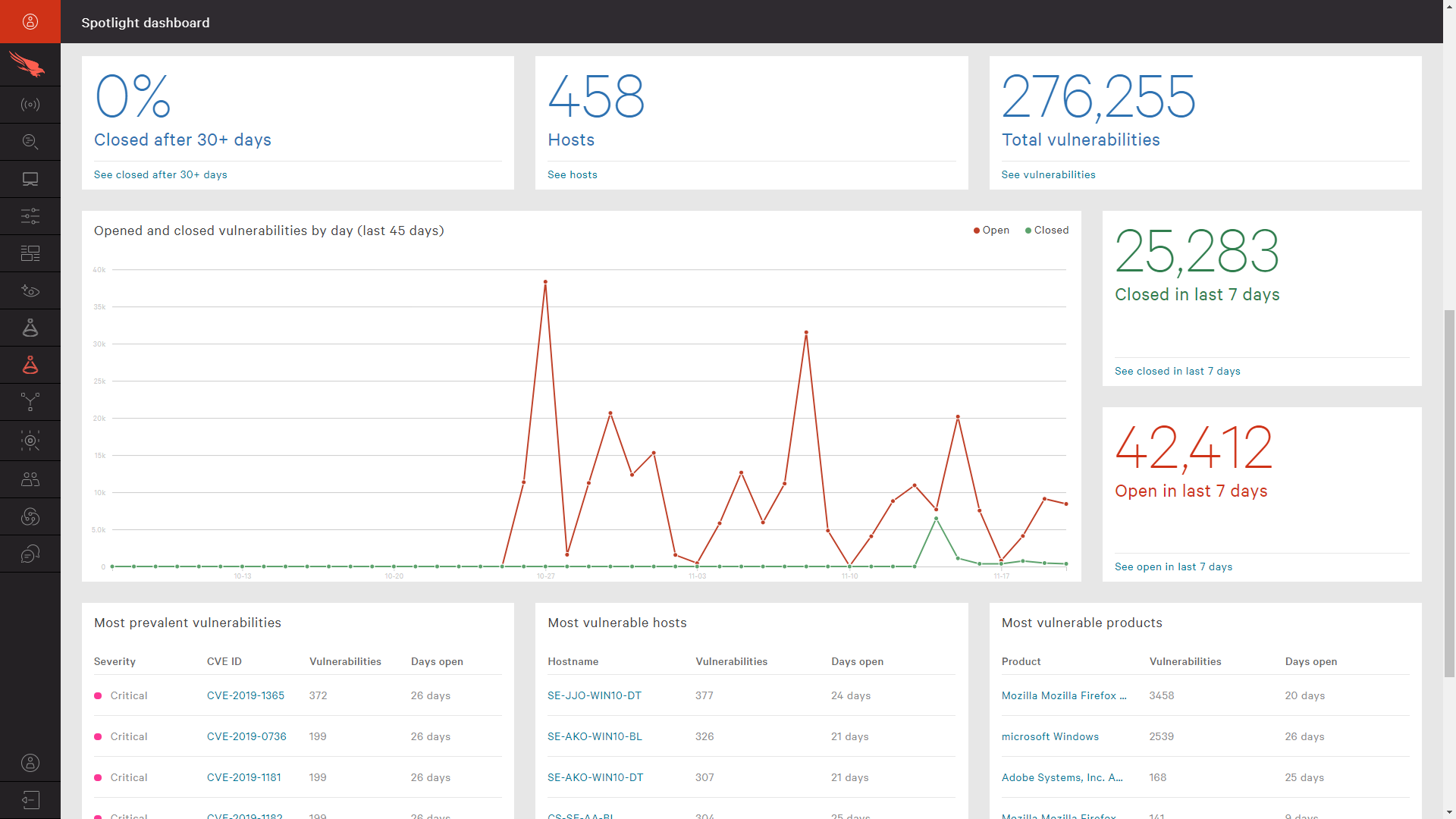
From the Falcon Spotlight Dashboard, statistics regarding “Closed vs Open” vulnerabilities is provided. These statistics give a good understanding of how quickly patches are being applied as well as vulnerability trends over time.
Spotlight for Research
Falcon Spotlight includes the functionality to research a specific vulnerability and the potential exposure in your environment. Here, we see the option to search by vulnerability. The results include the summary details of the CVE, a count of vulnerable hosts, and a detailed list of those systems that need to be patched.
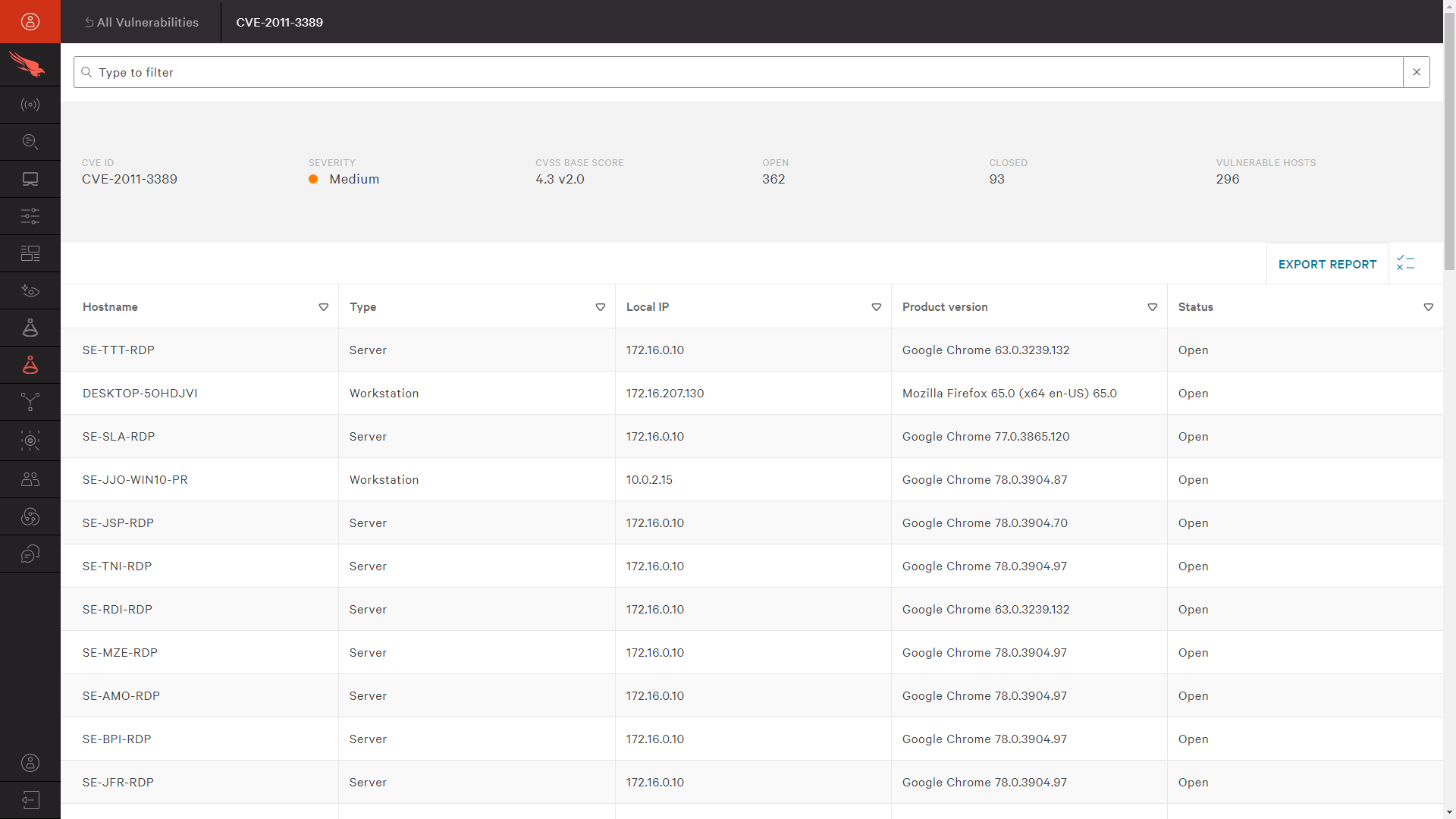
Like before, there is an option to download the list of systems that are lacking the required patch. Sharing this list with the patch management team would help them prioritize this patch and target the correct systems.
Spotlight for Investigations
In the situation of an incident or compromised system, Spotlight can also be used to assess the health of a given host. The search can be done by KB or CVE. Here, we see a search by hostname to understand what patches are missing from this specific system.
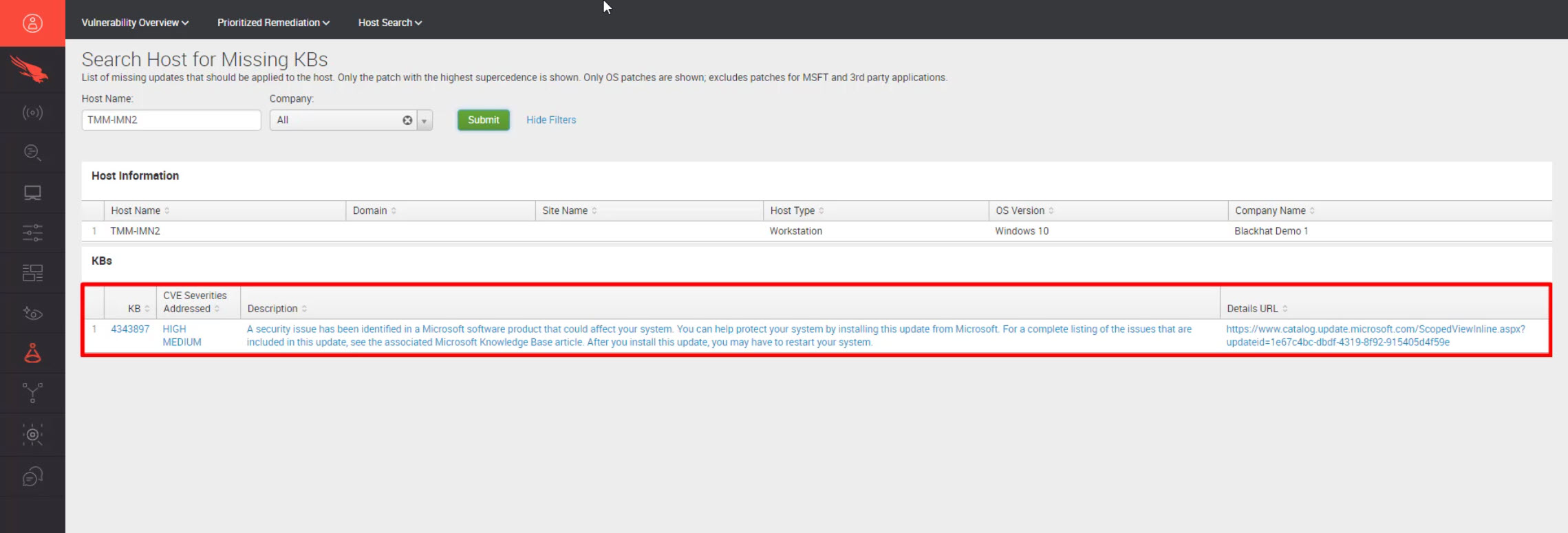
In this example, the system is missing one high – medium CVE. This information could provide insight into how the system was compromised and how it can be better protected in the future.
Conclusion
Falcon Spotlight provides holistic access to the vulnerability status of your environment with simple reporting and real time results without introducing complex hardware or time consuming scans. It provides complete, actionable reporting to help make your organization more secure.
More resources


