Spear-Phishing Definition
Spear-phishing is a type of phishing attack that targets specific individuals or organizations typically through malicious emails. The goal of spear phishing is to steal sensitive information such as login credentials or infect the targets’ device with malware.
Spear phishers carefully research their targets, so the attack appears to be from trusted senders in the targets’ life. A spear phishing email uses social engineering techniques to urge the victim to click on a malicious link or attachment. Once the victim completes the intended action, the attacker can steal the credentials of a targeted legitimate user and enter a network undetected.
Spear-phishing vs Phishing vs Whaling
These email examples below highlight the differences between phishing, spear-phishing, and whaling.
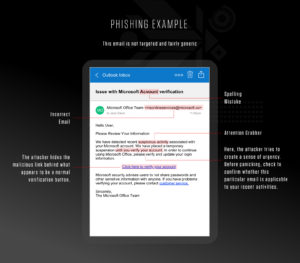
Phishing
Phishing attacks prioritize quantity. The messaging in phishing emails, texts or phone calls are generic and sent to a large group of individuals or organizations in hopes of increasing the chance of “catching” a victim. Phishing attacks via phone calls are often called vishing for voice-phishing. Attacks via text messages are known as smishing for SMS-phishing.
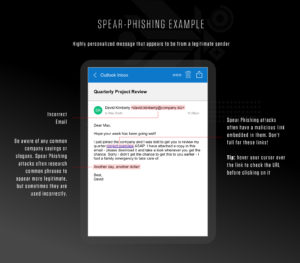
Spear-Phishing
Spear-phishing attacks prioritize quality. Spear-phishing emails, texts or phone calls are highly personalized for a specific organization or individual. Spear-phishing attacks are more likely to deceive potential victims due to the amount of research and time spent personalizing messages that appear to be from legitimate senders.
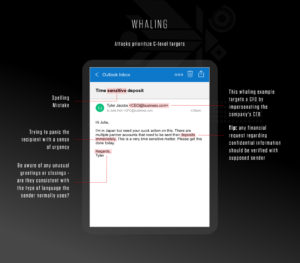
Whaling
A whaling attack prioritizes C-level targets. Whaling uses the same personalized strategy of spear-phishing attacks, except attackers specifically target higher level management to expose financial and confidential information. Whaling attacks hope to extract more valuable, classified information by taking down big targets, which can magnify the damage inflicted upon an organization.
The difference between phishing and spear-phishing is on the scale of personalization. Spear Phishing vs. PhishingLearn More
How a Spear-Phishing Attack Works
The personalized nature of spear phishing attacks is what makes them dangerous and easy to fall for. Hackers use reconnaissance methods in their research so they can increase the likelihood of a successful attack.
Spear phishers frequent social media sites like Facebook and LinkedIn to gather personal information about their target. They can also map out their target’s network of personal contacts, which gives them more context to crafting a trustworthy message. More sophisticated attackers may also use machine learning algorithms to scan through massive amounts of data and identify high level individuals they most want to target.
Being equipped with your personal data, spear phishers can then craft a seemingly legitimate email that grabs their target’s attention. Many people let their guard down because of the personalized messages and don’t think twice before clicking on a link or downloading an attachment. However, this mistake can lead to serious consequences such as stolen personal information or a malware infection.
Get a unique front-line view and greater insight into the cyber battle these seasoned security experts are waging against today’s most sophisticated adversaries.
Cyber Front Lines Report
Prevention Tips
Here are some common red flags of a spear phishing attempt:
- Unusual sense of urgency
- Incorrect email address
- Spelling or grammar mistakes
- Asks for Sensitive Information
- Contains Links that Don’t Match the Domain
- Includes Unsolicited Attachments
- Tries to Panic the Recipient
Security awareness training is fundamental in preventing any type of phishing attack, especially when many users are working from home. But even the best-trained and most security-conscious employees will occasionally click on a malicious link, either because they were in a hurry or it was very convincing.
To prevent spear phishing attacks, organizations should:
- Regularly conduct proactive investigations to find suspicious emails with content known to be used by attackers, such as subject lines referring to password changes.
- Ensure that remote services, VPNs and multifactor authentication (MFA) solutions are fully patched, properly configured and integrated.
- Educate employees on the various types of phishing attacks. Spear phishing knowledge will prepare employees to implement protective measures in real life
- Know how to validate an email IDs before replying to emails sent from outside the organization
- Know how to validate URLs before clicking on links
- Conduct phishing simulations within the company so that employees can practice what they learned from security awareness training. The company can also measure how well their employees understand spear phishing attacks to improve their training courses.
- Search for indications of malicious activity involving DMARC (Domain-based Message Authentication Reporting and Conformance), DKIM (Domain Keys Identified Mail) and SPF (Sender Policy Framework) failures.
- Scan properties of received messages, including the Attachment Detail property, for malware-related attachment types (such as HTA, EXE and PDF) and automatically send them to be analyzed for additional malware indicators.


