What is managed detection and response (MDR)?
Managed detection and response (MDR) is a cybersecurity service that combines technology with human expertise to rapidly identify and limit the impact of threats by performing threat hunting, monitoring, and response. The main benefit of MDR is that it quickly helps in limiting the impact of threats without the need for additional staffing, which can be costly.
MDR benefits
Organizations using an MDR solution can immediately reduce their time-to-detect (and therefore, time to respond) from the typical 277 days to as little as a few minutes — thereby dramatically reducing the impact of an event.
But reducing time-to-detect from months to mere minutes is not the only benefit. Organizations can also:
- Improve security posture and become more resilient to potential attack by optimizing security configuration and eliminating rogue systems.
- Identify and stop hidden, sophisticated threats through continuous managed threat hunting.
- Respond to threats more effectively and restore endpoints to a known good status through guided response and managed remediation.
- Redirect staff from reactive and repetitive incident response work toward more strategic projects.

MDR Buyer's Guide
The CrowdStrike MDR Buyer’s Guide has been created to walk you through the different categories of MDR services and help you confidently determine what’s best for your organization.
Download NowBusiness challenges for MDR adoption
Challenge #1: Staffing/Resources
Organizations that were already struggling to keep their security teams fully staffed are facing even greater challenges as they adopt innovative security technologies to address the evolving threat landscape.
Today, most organizations have security tools in their stack that they don’t have time to manage fluently.
The investment they’ve made in leading-edge tools can end up hurting them instead of helping them if they lack the time or resources to fully deploy and optimize their solutions against increasingly sophisticated threats.
Challenge #2: Alert Fatigue
Another challenge is managing massive numbers of alerts from all these new security technologies. This isn’t a new problem, but it’s growing by orders of magnitude as endpoints proliferate in the forms of IoT, remote workers, connected supply chain partners, and hybrid networks.
Determining how to respond to each alert requires more manpower and expertise than is typically retained in-house — and when a threat is determined to be significant, the organization needs to have the relevant skills to remediate it and return the endpoint to a secure status, and do it quickly before the intrusion can become a serious breach.
Expert Tip
Even if an organization has the resources and will to build a security team that can handle all aspects of all threats, it should expect to spend at least months, and more likely years, to build a mature detection and response program. In the interim, the business remains vulnerable.
MDRs have emerged to fill these gaps. Organizations can quickly stand up an MDR solution that remotely accesses a network to provide 24/7 coverage and access to expertise that would be extremely difficult to find and staff independently. These experts are on call around the clock, so they can rapidly respond based on their knowledge of every aspect of endpoint security, from detection to restoring the endpoint to a known good status to preventing further compromise.
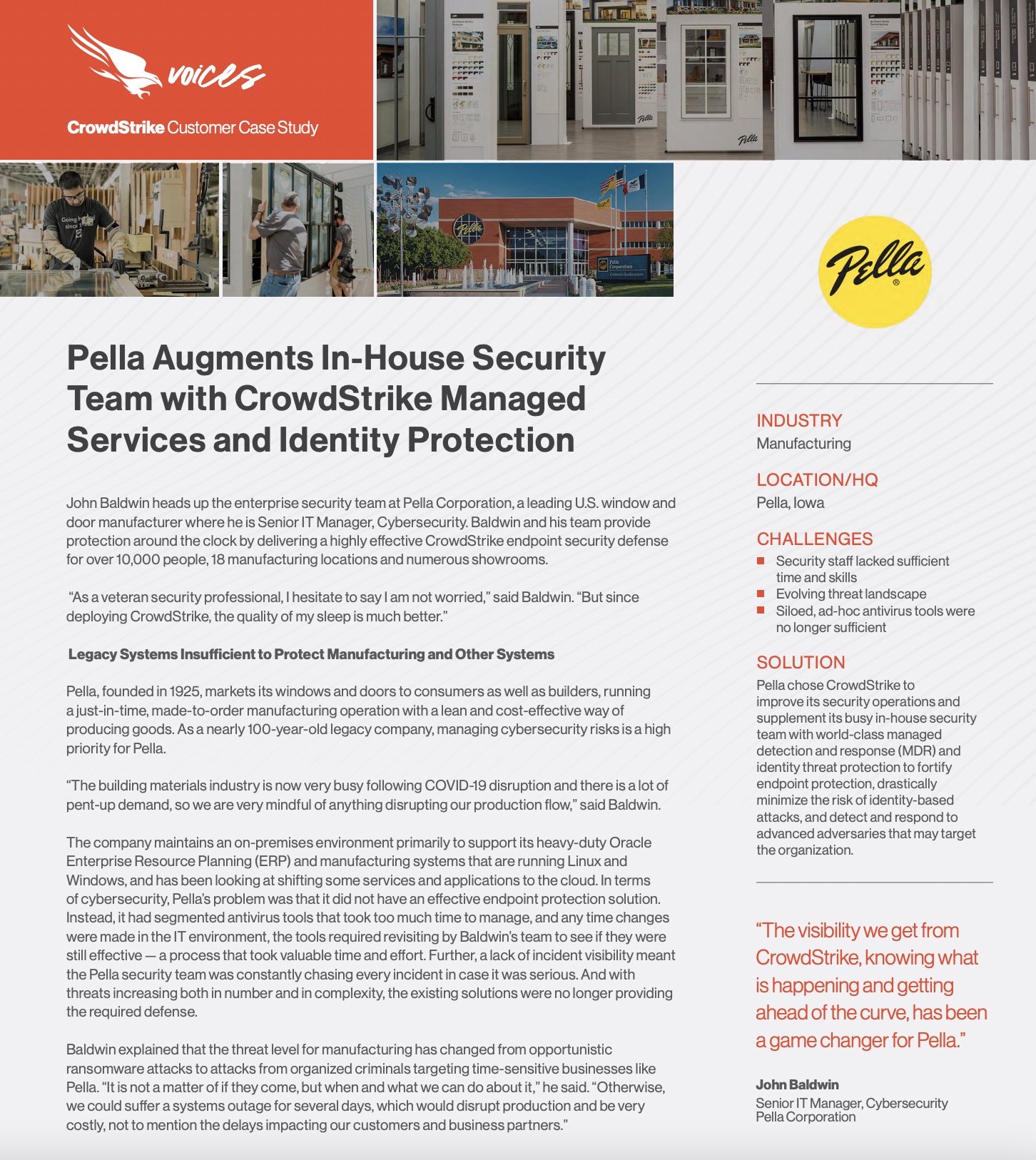
Customer Story: Pella Corporation
Pella Corporation markets its windows and doors to consumers as well as builders, running a just-in-time, made-to-order manufacturing operation. Learn why they chose CrowdStrike to improve its security operations and supplement its busy in-house security team with world-class managed detection and response (MDR).
Download NowHow MDR works
MDR remotely monitors, detects, and responds to threats detected within your organization. An endpoint detection and response (EDR) tool typically provides the necessary visibility into security events on the endpoint.
Relevant threat intelligence, advanced analytics, and forensic data are passed to human analysts, who perform triage on alerts and determine the appropriate response to reduce the impact and risk of positive incidents. Finally, through a combination of human and machine capabilities, the threat is removed and the affected endpoint is restored to its pre-infected state.
The core capabilities of an MDR are:
1. Prioritization
Managed prioritization helps organizations that struggle with the daily effort of sifting through their massive volume of alerts determine which to address first. Often referred to as “managed EDR,” managed prioritization applies automated rules and human inspection to distinguish benign events and false positives from true threats. The results are enriched with additional context, and distilled into a stream of high-quality alerts.
2. Threat Hunting
Behind every threat is a human being who’s thinking about how to avoid being caught by their targets’ countermeasures. While machines are very smart, machines are not wily: a human mind is needed to add the element that no automated detection system can provide. Human threat hunters with extensive skills and expertise identify and alert on the stealthiest and most evasive threats in order to catch what the layers of automated defenses missed.
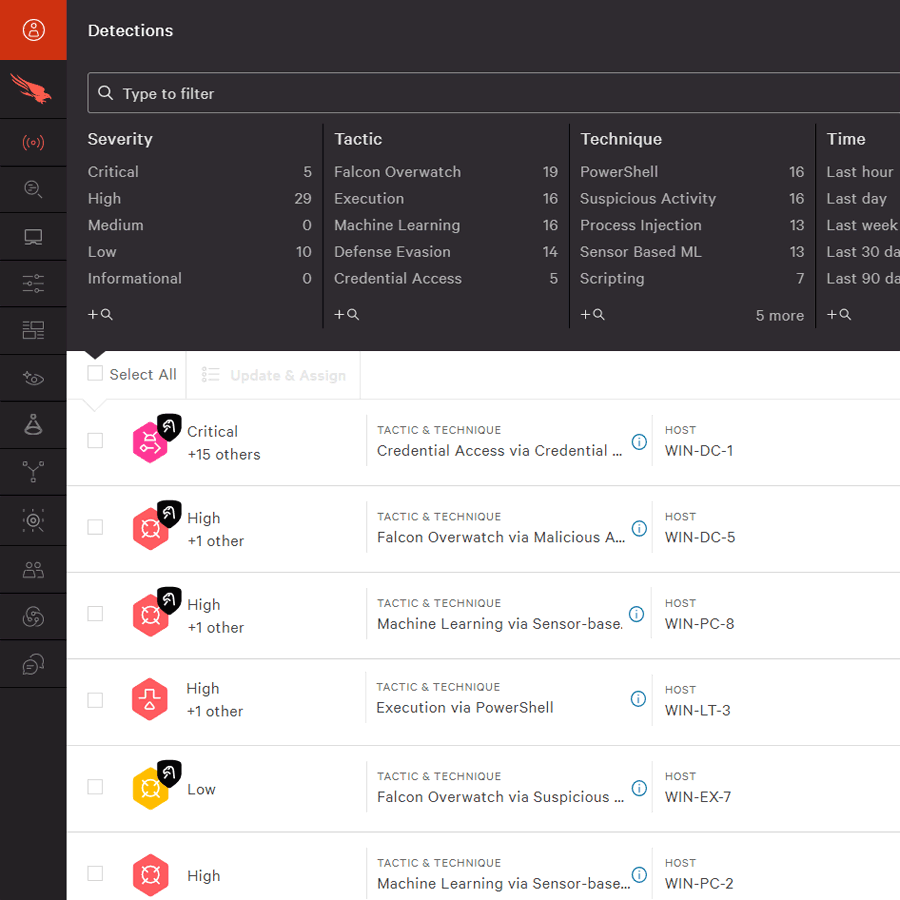
3. Investigation
Managed investigation services help organizations understand threats faster by enriching security alerts with additional context. Organizations are able to more completely understand what happened, when it happened, who was affected, and how far the attacker went. With that information, they can plan an effective response.
4. Guided Response
Guided response delivers actionable advice on the best way to contain and remediate a specific threat. Organizations are advised on activities as fundamental as whether to isolate a system from the network to the most sophisticated, such as how to eliminate a threat or recover from an attack on a step-by-step basis.
5. Remediation
The final step in any incident is recovery. If this step is not performed properly, then the organization’s entire investment in its endpoint protection program is wasted. Managed remediation restores systems to their pre-attack state by removing malware, cleaning the registry, ejecting intruders, and removing persistence mechanisms. Managed remediation ensures that the network is returned to a known good state and further compromise is prevented.
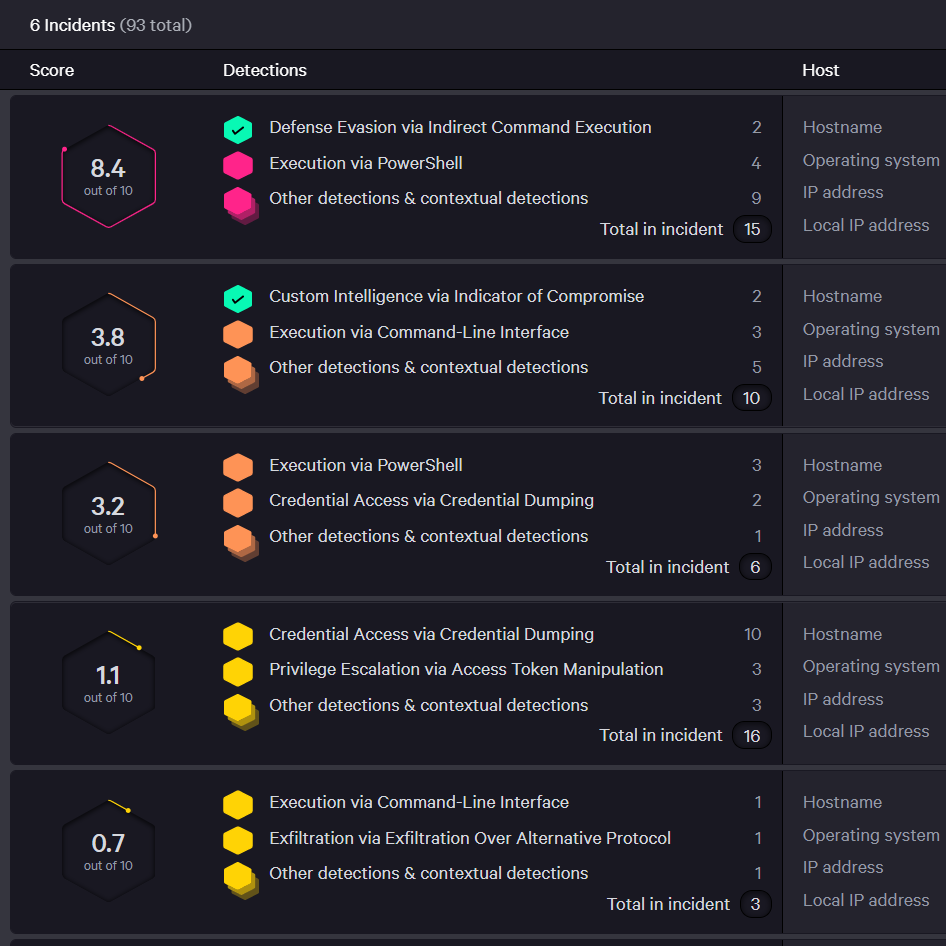
MDR vs. EDR
Endpoint detection and response (EDR) is part of the tool set used by MDR providers. EDR records and stores behaviors, and events on endpoints and feeds them into rules-based automated responses and analysis systems. When an anomaly is detected, it is sent to the security team for human investigation. EDR gives security teams the ability to use more than just indicators of compromise (IoCs) or signatures to gain a better understanding of what’s happening on their networks.
Over time EDR offerings have become more complicated, incorporating technologies such as machine learning and behavioral analysis, as well as the ability to integrate with other complex tools. Many in-house security teams lack the resources and the time to fully utilize their EDR systems, which can leave an organization less secure than it was before it purchased its EDR solution.
MDR solves that problem by introducing human expertise, mature processes, and threat intelligence. MDR is designed to help organizations acquire enterprise-grade endpoint protection without incurring the costs of an enterprise-grade security staff or security operations center (SOC).
MDR vs XDR vs MXDR
While MDR is referred to as EDR as a Service at times, Extended Detection and Response (XDR) takes it a step further by integrating data from various sources to improve visibility and reduce risk. It uses a plethora of methodologies and tools such as identity and access management and data loss prevention. By doing so, it gains visibility to more than just endpoints, but all users, networks, assets, emails, workloads, and more. XDR helps to eliminate silos and gaps that put the organization at risk.
MDR manages endpoint security and focuses on mitigating, eliminating and remediating threats with a dedicated, experienced security team. Managed Extended Detection and Response (MXDR) takes XDR to the next step because it is purchased as a service and provides all its capabilities, but is delivered by an external team that acts as a seamless extension of the internal IT and security team. At the moment, MXDR is considered the highest protection standard available in the market.

Falcon Complete XDR Data Sheet
Download this data sheet to learn how you can expand your 24/7 MDR services with the introduction of MXDR services using Falcon Complete XDR for rapid cross-domain detection of lateral movement and stealthy, advanced attacks.
Download NowMDR vs. MSSP
Managed Security Services Providers (MSSPs) are the predecessors of MDR. MSSPs typically provide broad monitoring of the network for events and send validated alerts to other tools or to the security team, along with a range of other services such as technology management, upgrades, compliance, and vulnerability management, but generally do not actively respond to threats. The customer is responsible for performing those activities, which can require specialized expertise that is not often maintained in-house. As a result, MSSP customers must also engage additional consultants or vendors to perform mitigation and remediation.
MDR services are tightly focused on detecting and responding to emerging threats quickly. In addition, MDR delivers mitigation and remediation capabilities, and can deliver immediate value with minimal investment.
MDR vs. Managed SIEM
Security information and event management (SIEM) is a broad technology category. SIEMs all start by aggregating data from many network sources and other security devices, and analyzing it to catch anomalies that may signal suspicious activity. After that, SIEM capabilities vary widely. Some are technology-only solutions while others are more like managed event processing and alerting services.
One thing all SIEMs have in common is that their customers report challenges in resolving problems exposed by their SIEM’s data because they encounter difficulties understanding the results. SIEMs can also be expensive and resource-intensive. MDRs, on the other hand, are characterized by their light network footprint and quick time-to-value.
How to Choose an MDR Service – 5 Questions
MDR solutions include a broad range of services, so be sure to know your organization’s current capabilities before beginning your search so you can select a solution that complements your existing security investment. Here are five key questions to ask MDR vendors as you begin your research:
Question #1. What kind of expertise do the analysts who staff the MDR possess?
The solution you choose should introduce new skills and maturity without requiring you to hire additional staff. Look for a vendor willing to provide knowledge transfer.
Question #2. Does your MDR service have access to the data and systems needed and in time to be effective?
The effectiveness of your MDR solution will depend greatly on its access to the breadth and depth of data necessary to do its job, and it must have that data in real-time. A cloud-native solution is most likely to have the best access to the right data.
Question #3. How does your MDR team stay current on the latest threats targeting organizations?
Security analysts pay attention to more than adversaries’ technological capabilities. They study cultural, geopolitical, and linguistic factors to build as complete an understanding as possible of the current techniques, tactics, and procedures used to target businesses. Few if any enterprises have these skills on staff, so choose an MDR vendor that does.
Question #4. How will the MDR provider communicate with your team?
At some point, the MDR team will hand-off their workflow to your team. This should be accomplished through a central communication hub, such as a single pane of glass console, in order to ensure that no new points of friction or any need to learn new systems are incurred. The hand-off should happen without slowing down your team’s response in any way.
Question #5. Is your service 24/7?
The vast majority of organizations do not staff their security operations around the clock. MDR coverage should operate around the clock, because while law-abiding citizens are sleeping, attackers are hard at work.
Learn More
Learn how Falcon Complete MDR combines the power of our cloud-native Falcon platform with the efficiency, expertise and 24/7 protection of CrowdStrike’s global team of security experts.Falcon Complete MDR