Standard Hero
Example of standard hero with Centered Text
The Year of Adaptability and Perseverance
The 2021 threat landscape became more crowded as new adversaries emerged.
Notable adversary updates include:
21
Newly named adversaries
45%
Increase in interactive intrusion campaigns
62%
of recent detections were malware-free
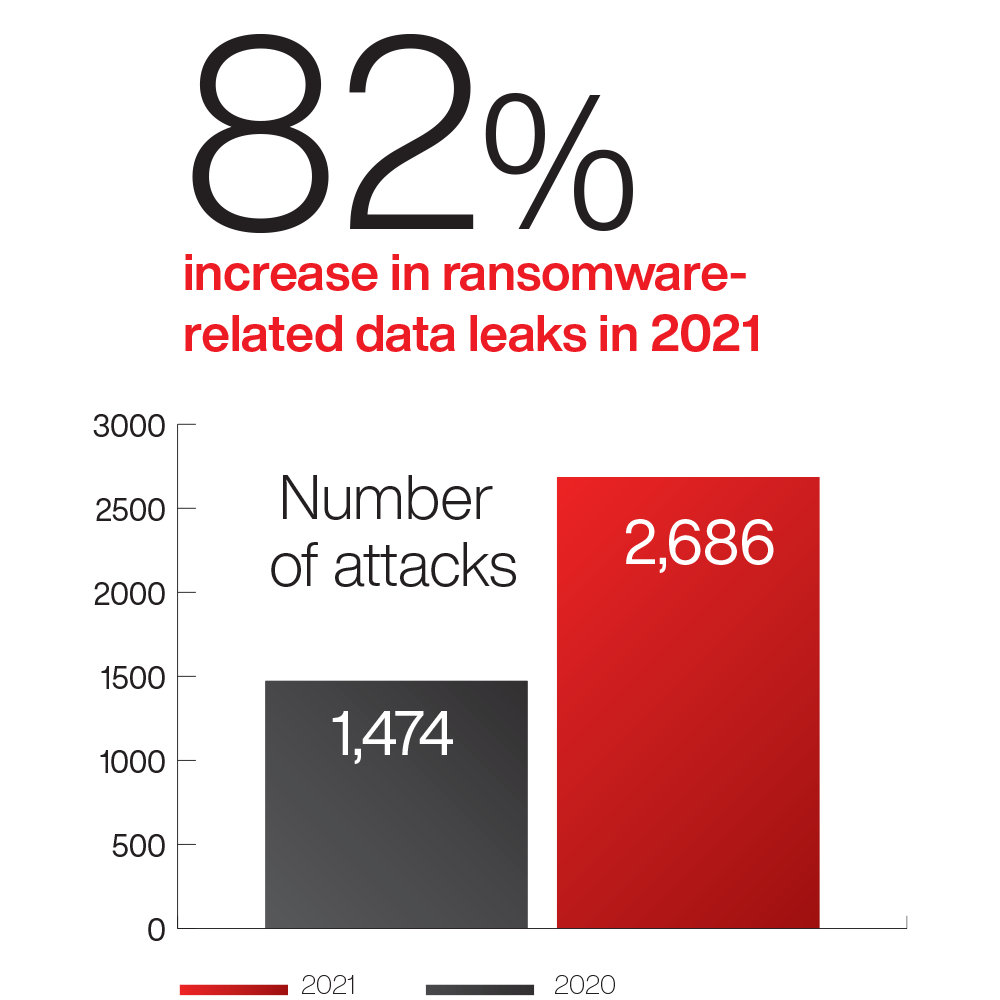
82%
Increase in ransomware-related data leaks
1 hour 38
Minutes average eCrime breakout time
170+
Total adversaries tracked
Tracking Adversaries in 2021
Meet some global enemies and the global threats they posed in 2021.
First Hero
This is some test content for display
Key Insights from the 2022 Global Threat Report
Ransomware and the Ever-adaptable Adversary
The growth and impact of big game hunting in 2021 was a palpable force felt across all sectors and in nearly every region of the world. In the eCrime landscape, ransomware is big business — CrowdStrike Intelligence observed an 82% increase in ransomware-related data leaks from 2020 to 2021. This increase, coupled with other data leaks, highlights how valuable victim data is to adversaries.
Iran and the New Face of Disruptive Operations
Since late 2020, multiple Iran-nexus adversaries and activity clusters have adopted the use of “lock-and-leak” attacks — disruptive information operations using ransomware to encrypt target networks and subsequently leak victim information via actor-controlled personas or entities. The use of high-profile lock-and-leak operations, as well as traditional ransomware activity, provides Iran with an effective capability to disrupt their targets.
China Emerges as Leader in Vulnerability Exploitation
China-nexus actors deployed exploits for new vulnerabilities at a significantly elevated rate in 2021. Since 2020, CrowdStrike Intelligence confirmed a sixfold increase in vulnerability exploitation and linked 10 named adversaries or activity clusters to these attacks.

Log4Shell Sets the Internet on Fire
The most high-profile vulnerability in 2021 was Log4Shell, which exploited Apache’s Log4j2, a ubiquitous logging library used by many web applications. First reported in November 2021, Log4Shell can be exploited by remote attackers to inject arbitrary Java code into affected services, which could result in access to the system, delivery of malware or acquisition of sensitive data.

Increasing Threats to Cloud Environments
Cloud-based services now form crucial elements of many business processes, easing file sharing and workforce collaboration. However, these same services are increasingly abused by malicious actors, a trend that is likely to continue in the foreseeable future as more businesses seek hybrid work environments.