Built for Security
Enable secure innovation in the cloud without friction
Strengthen the security of everything your organization builds and runs in the cloud.
CrowdStrike Falcon® Cloud Security
The industry’s most complete cloud native application protection platform (CNAPP) with unified visibility across your cloud and apps.
Discover CrowdStrike's industry-leading Cloud Detection and Response
Learn moreThe Falcon Cloud Security difference
Customer assessment
780hrs
saved per year by avoiding cloud breach response2
Customer assessment
$380k
average savings per year2
Falcon Cloud Security is the industry’s only unified agent and agentless platform for code to cloud protection, integrating pre-runtime, runtime protection, and agentless technology in a single platform.
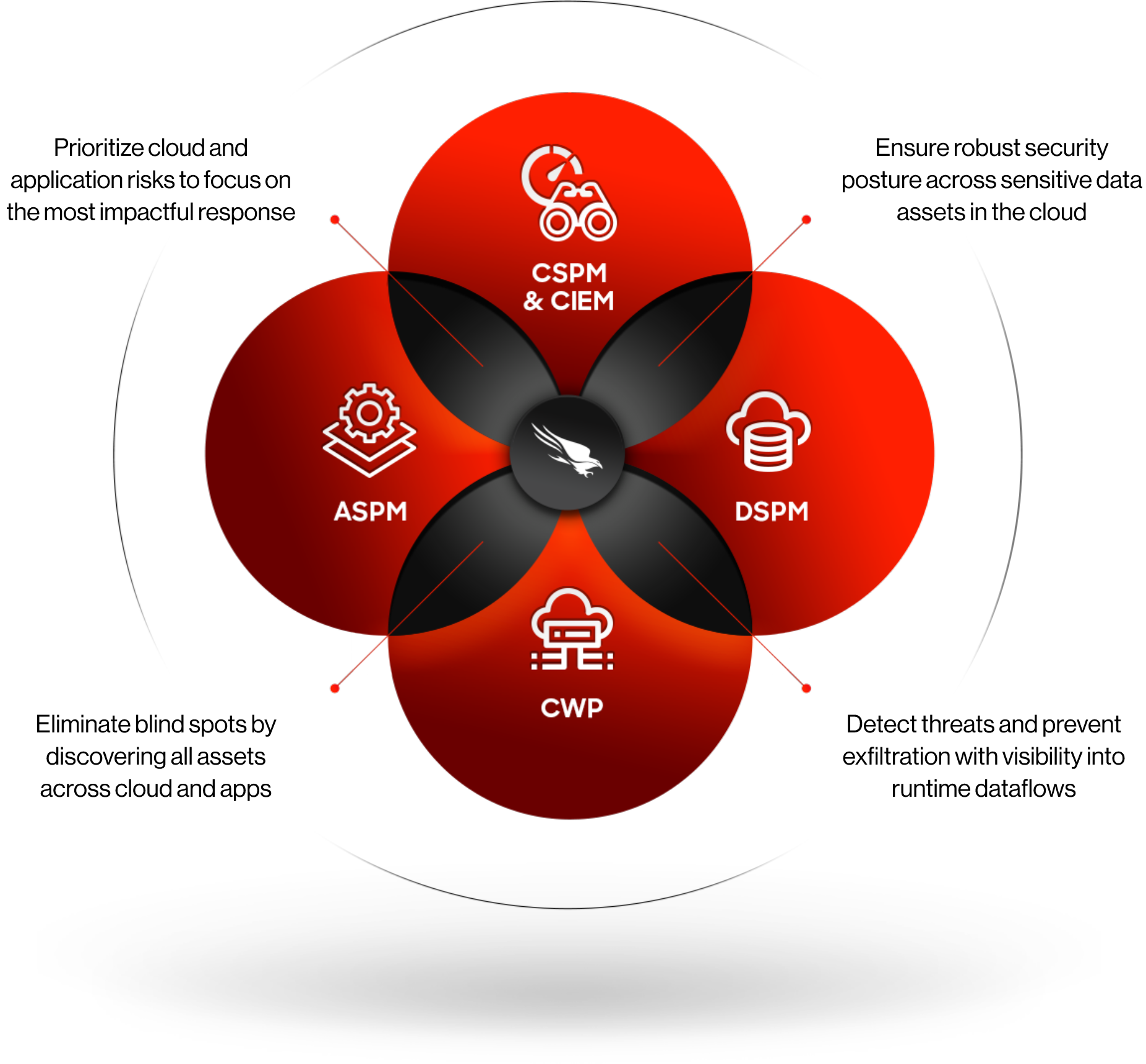
The industry’s only CNAPP that integrates cloud workload protection (CWP), cloud security posture management (CSPM), cloud identity entitlement management (CIEM), container security, and application security posture management (ASPM) in a single, unified platform.
Scan everything by discovering all assets, across cloud environments and apps, in real-time.
Stay compliant with industry regulations and security benchmarks with unified visibility and automated compliance across your cloud environment.
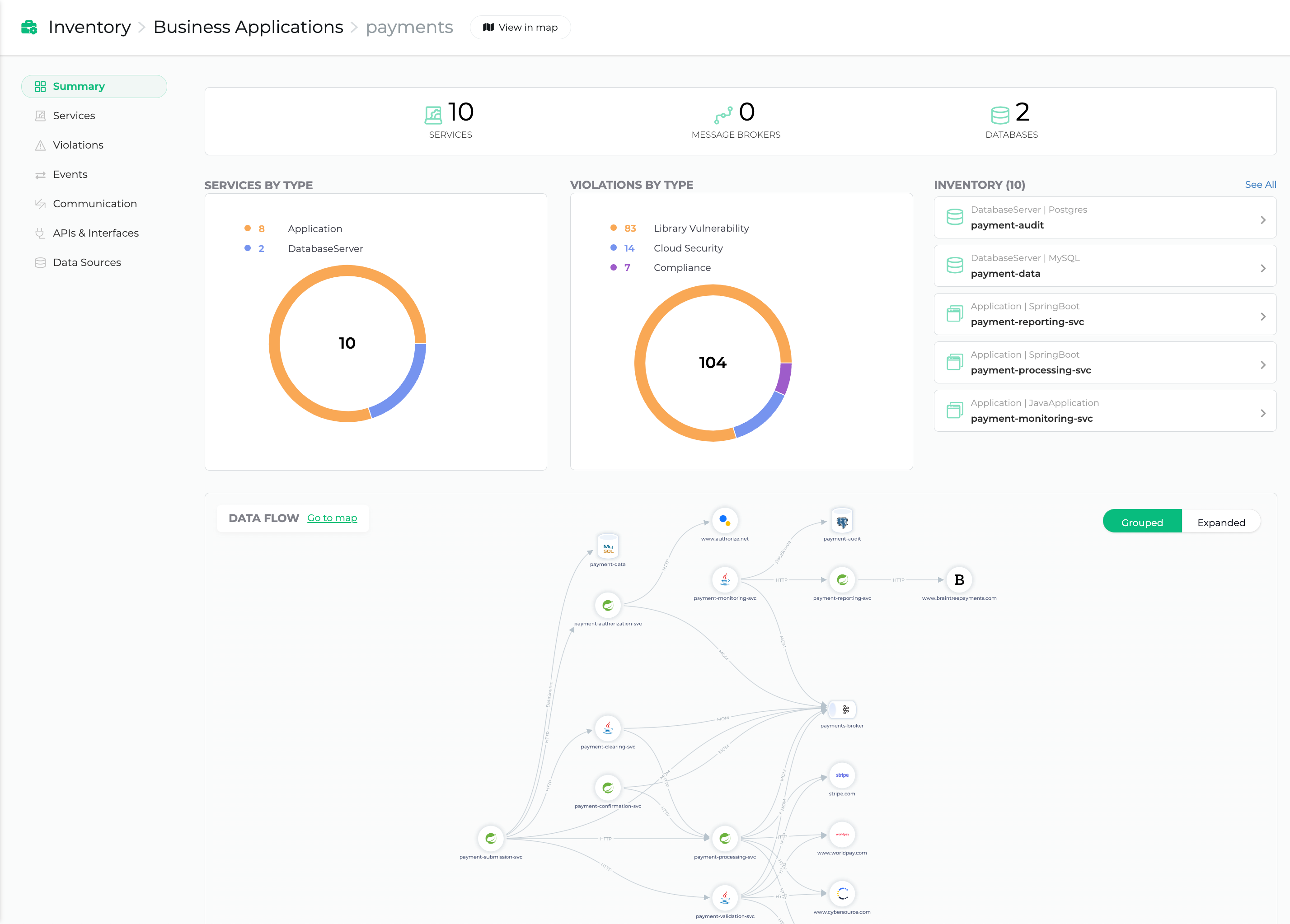
Get a code-accurate map and real-time inventory into every microservice, database, API, and dependency running in production.
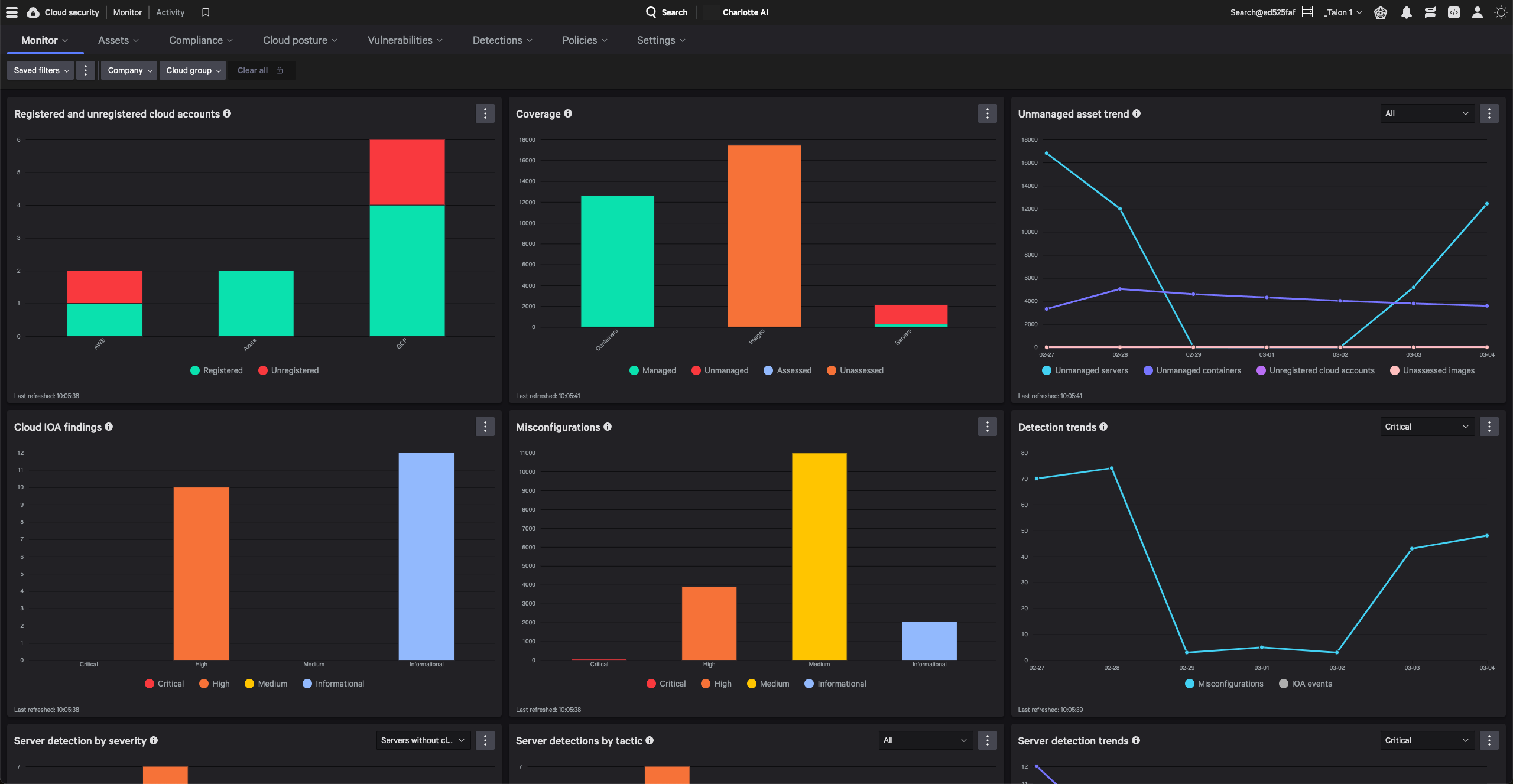
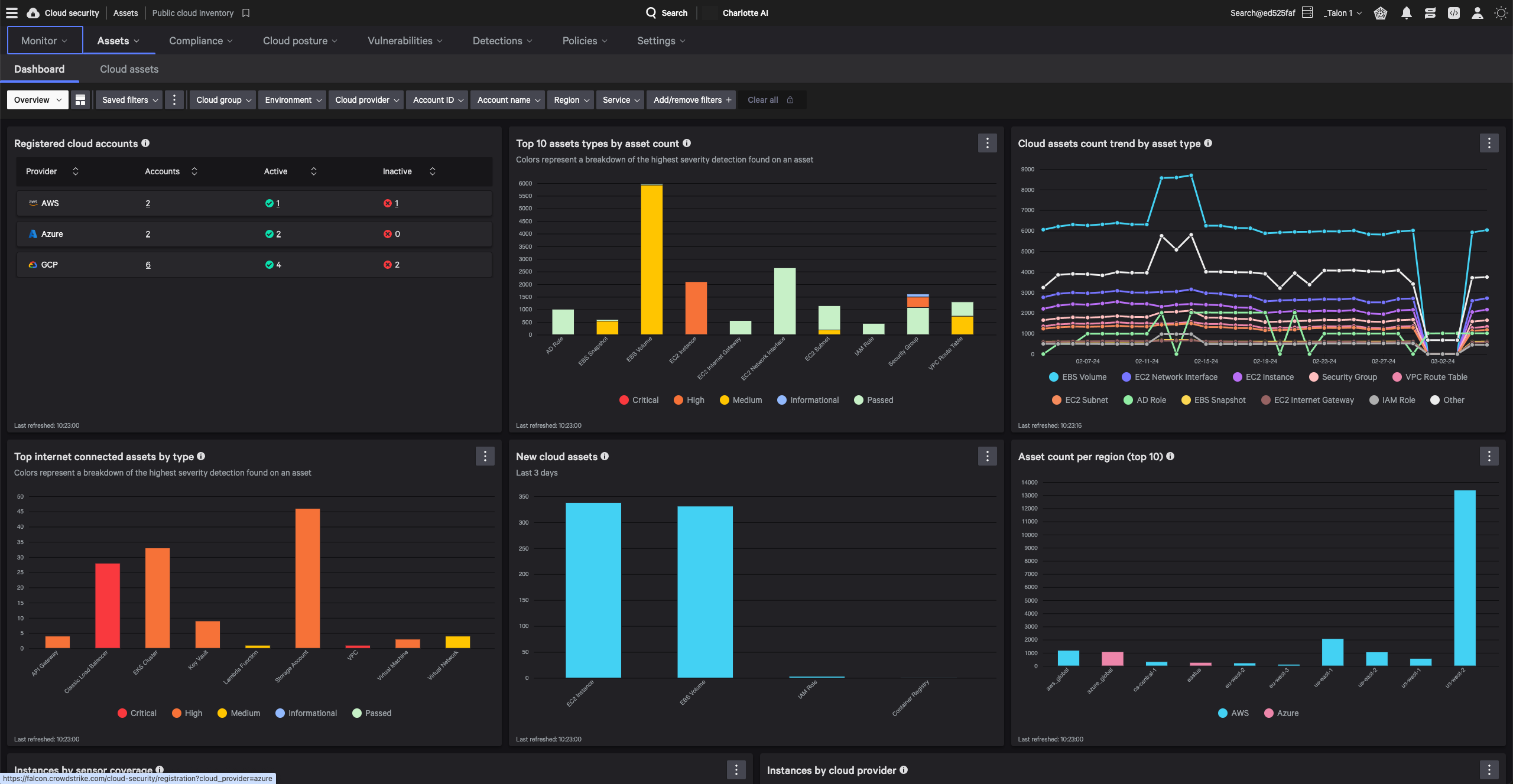
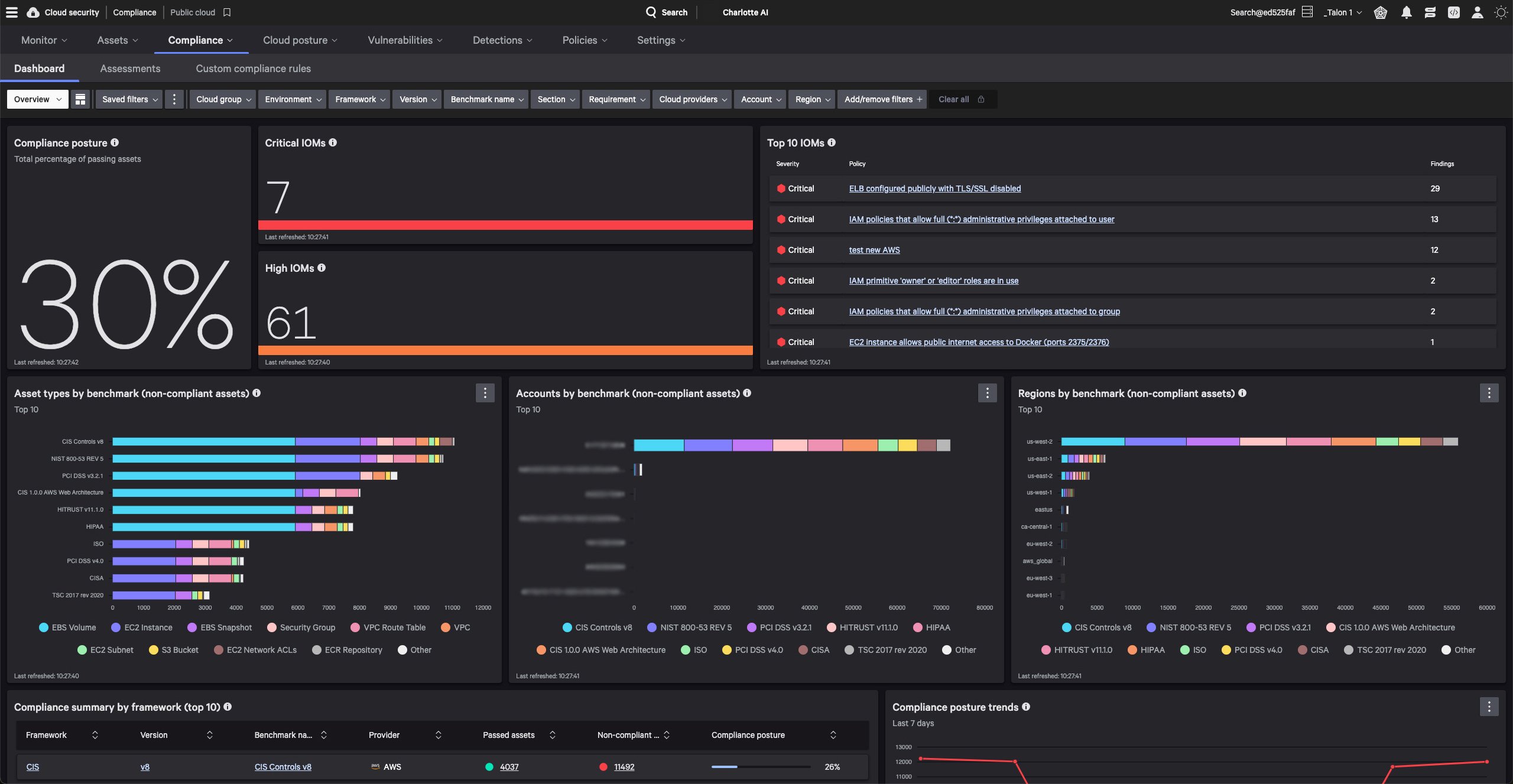
Reveals the complete attack path across cloud and runtime environments with the context needed to detect breaches, vulnerabilities, and identity based-threats.
See risk and security through a business lens by correlating cloud risks to apps and services, allowing you to focus on the threats with the highest business impact.
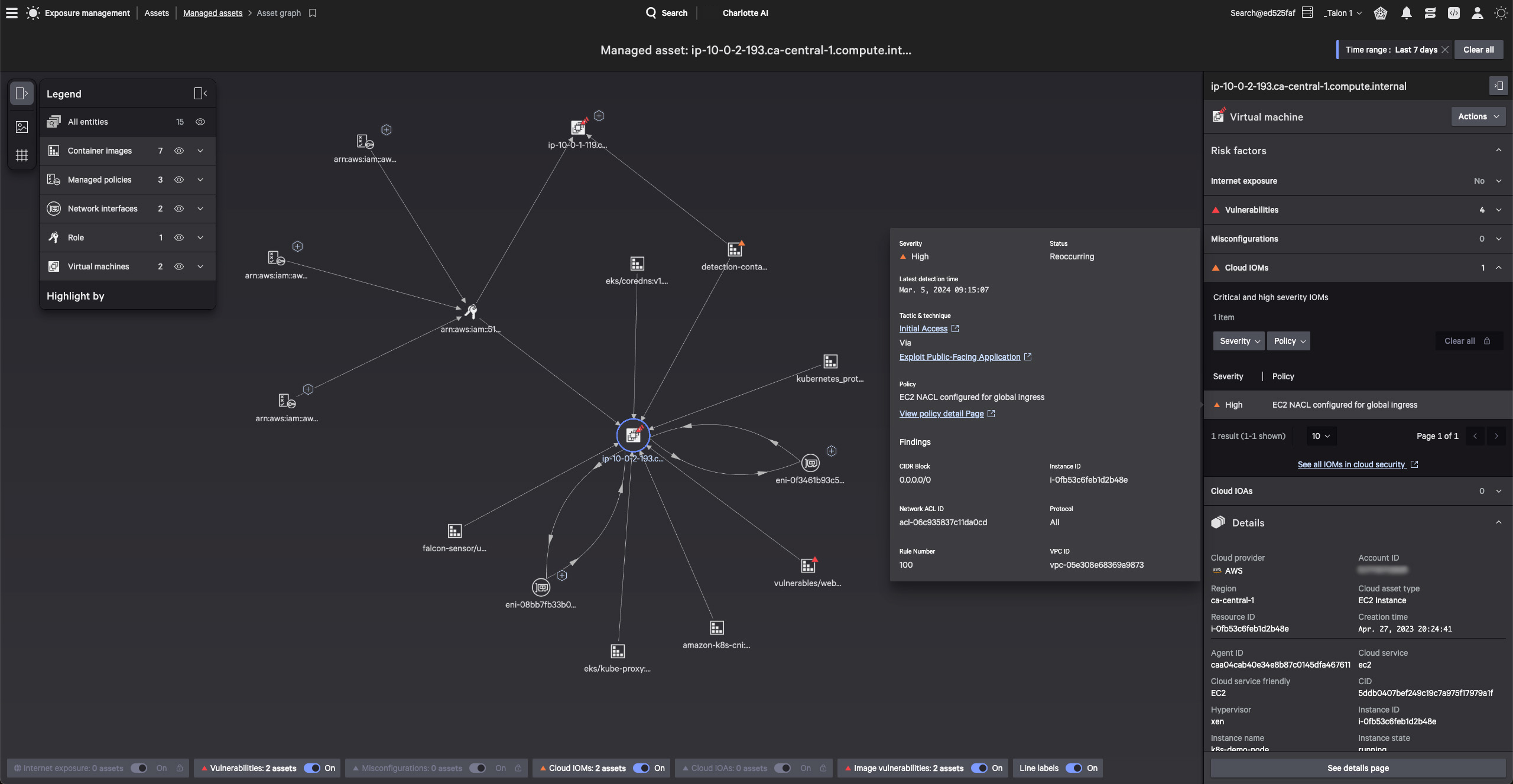
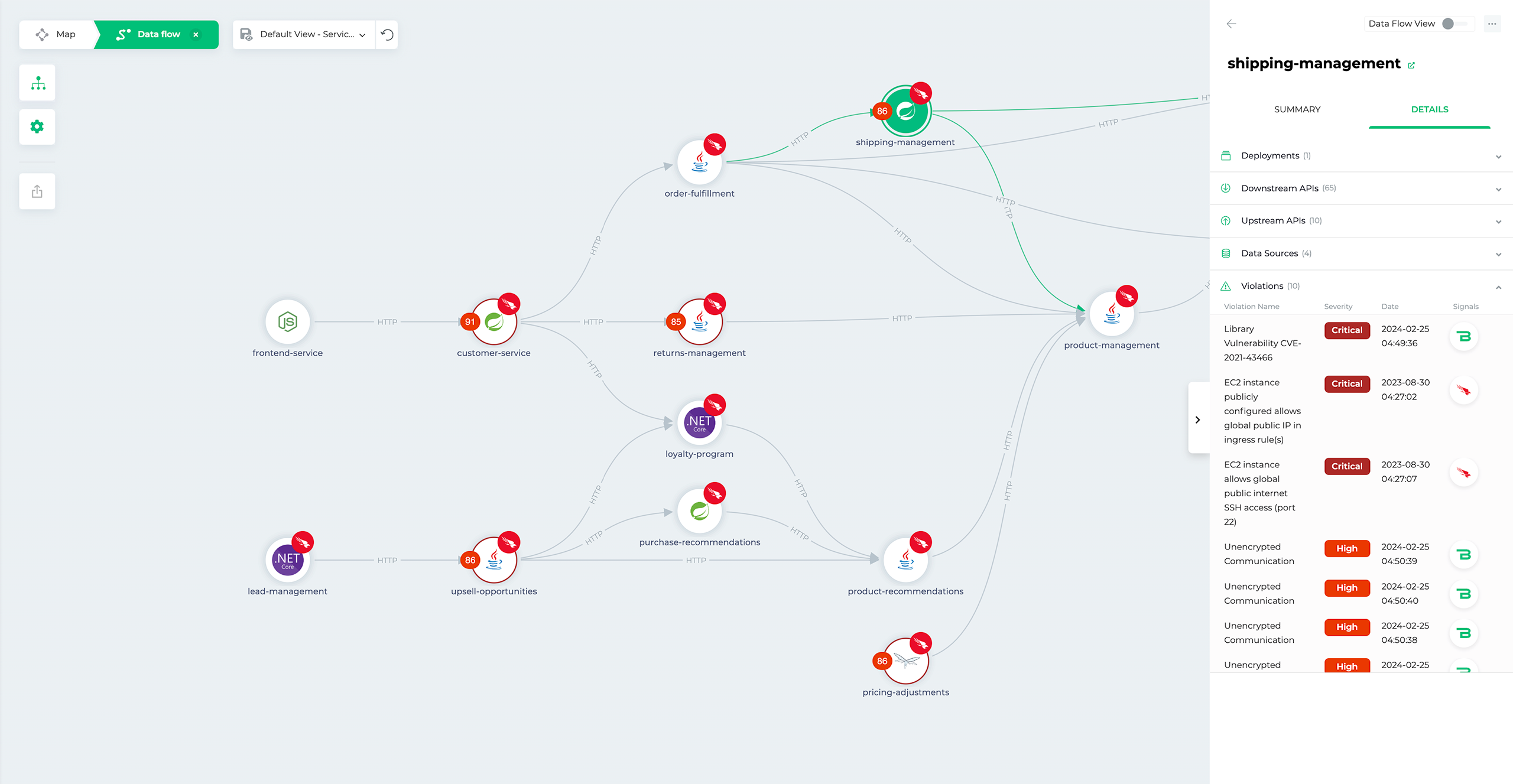
Shutdown adversaries with industry-leading cloud detection and response, backed by continuous threat intelligence, from the pioneer of EDR.
Stop breaches across endpoint and cloud runtime environments, including automated discovery and protection of all workloads with a single click.
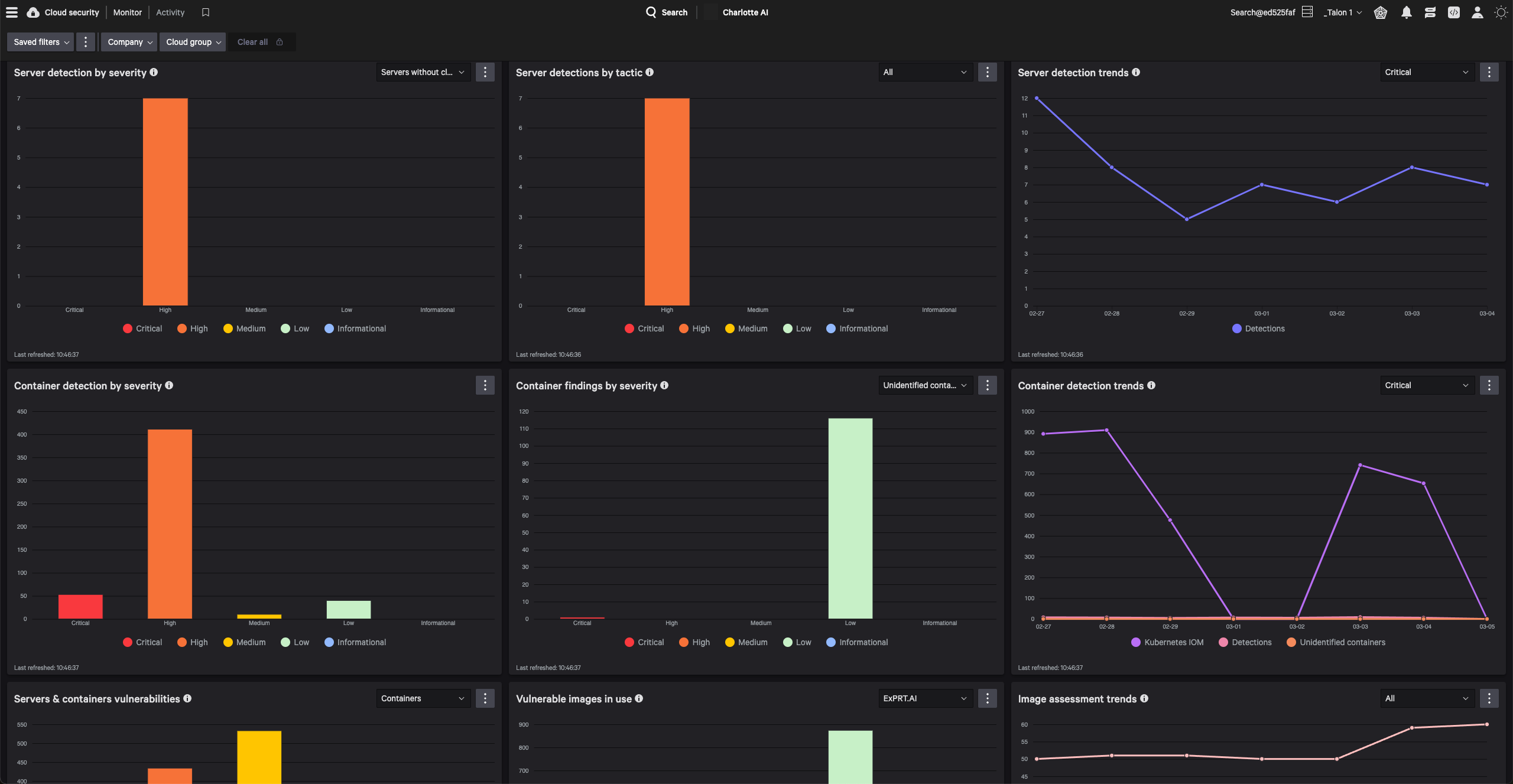
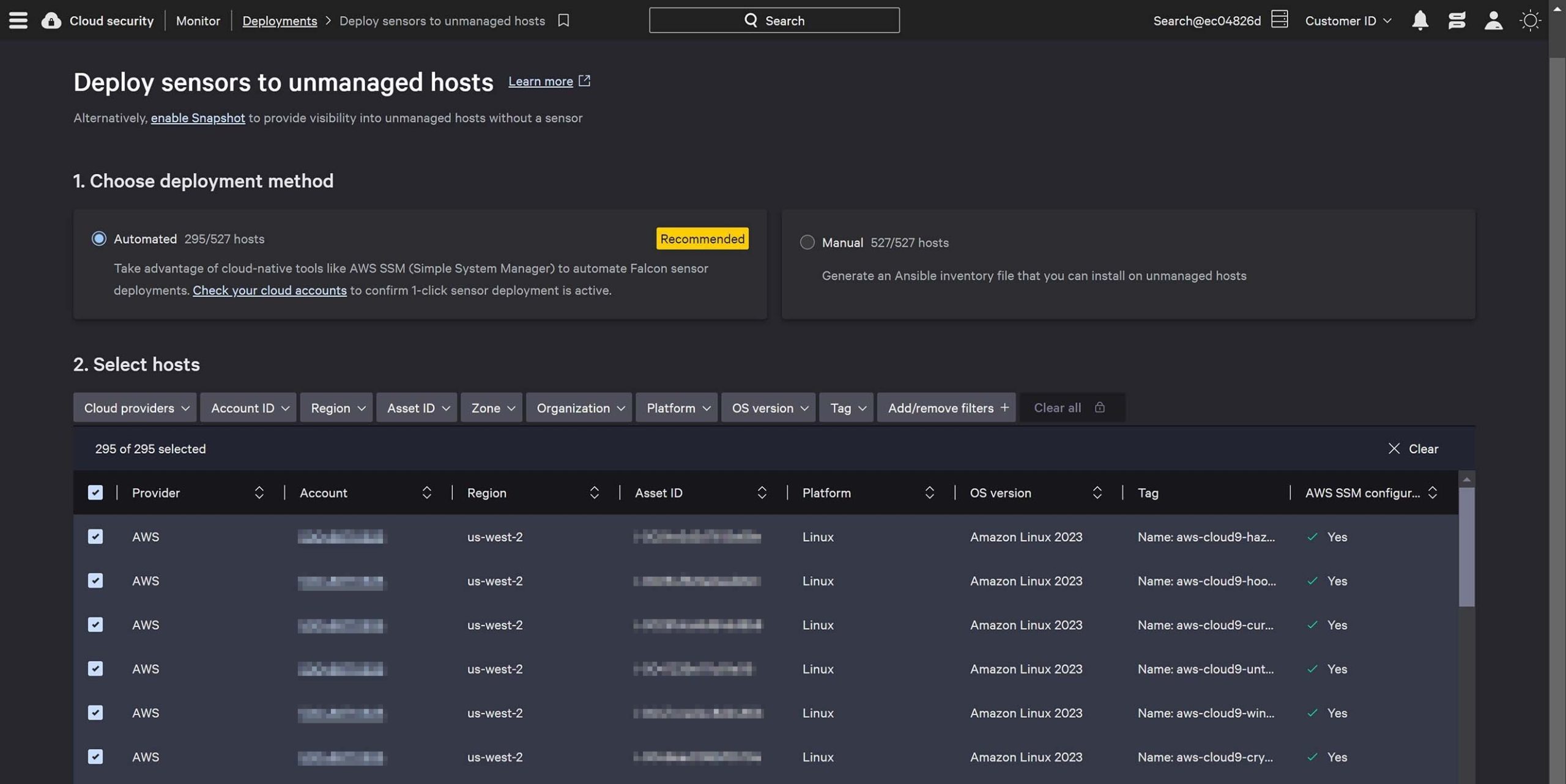
Simplify your development processes by integrating security earlier in the app development lifecycle, catching production issues before they escalate.
Improve the efficiency of developers and security teams by leveraging a single CLI tool to identify misconfigurations earlier in the application lifecycle.
Faster, more accurate and easier to use drift prevention with behavioral, AI-based real-time analysis, replacing the legacy approaches requiring allowlists, profiling creation and maintenance.
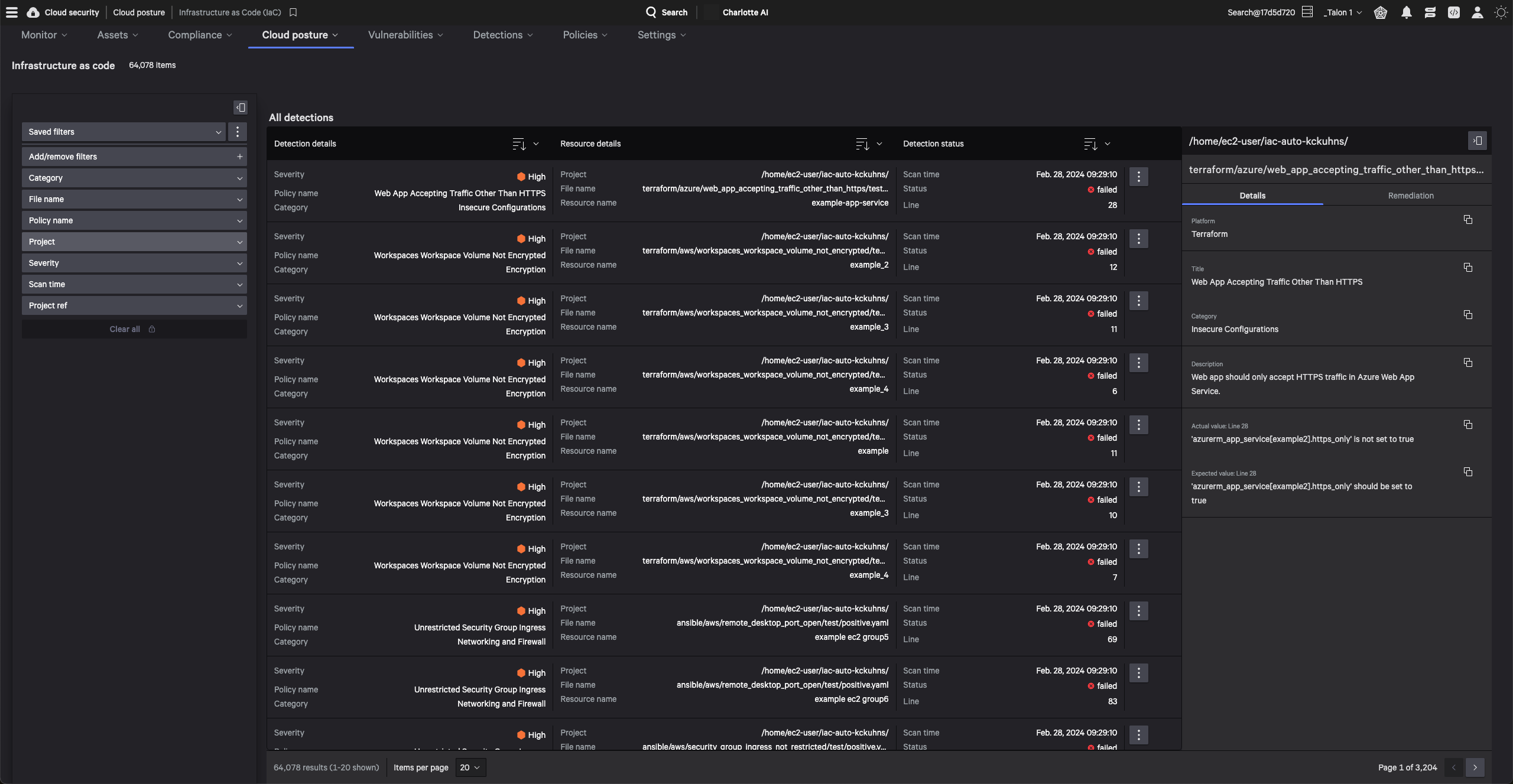
Only CrowdStrike can scan for vulnerabilities in container images and perform IaC scans in a single platform.
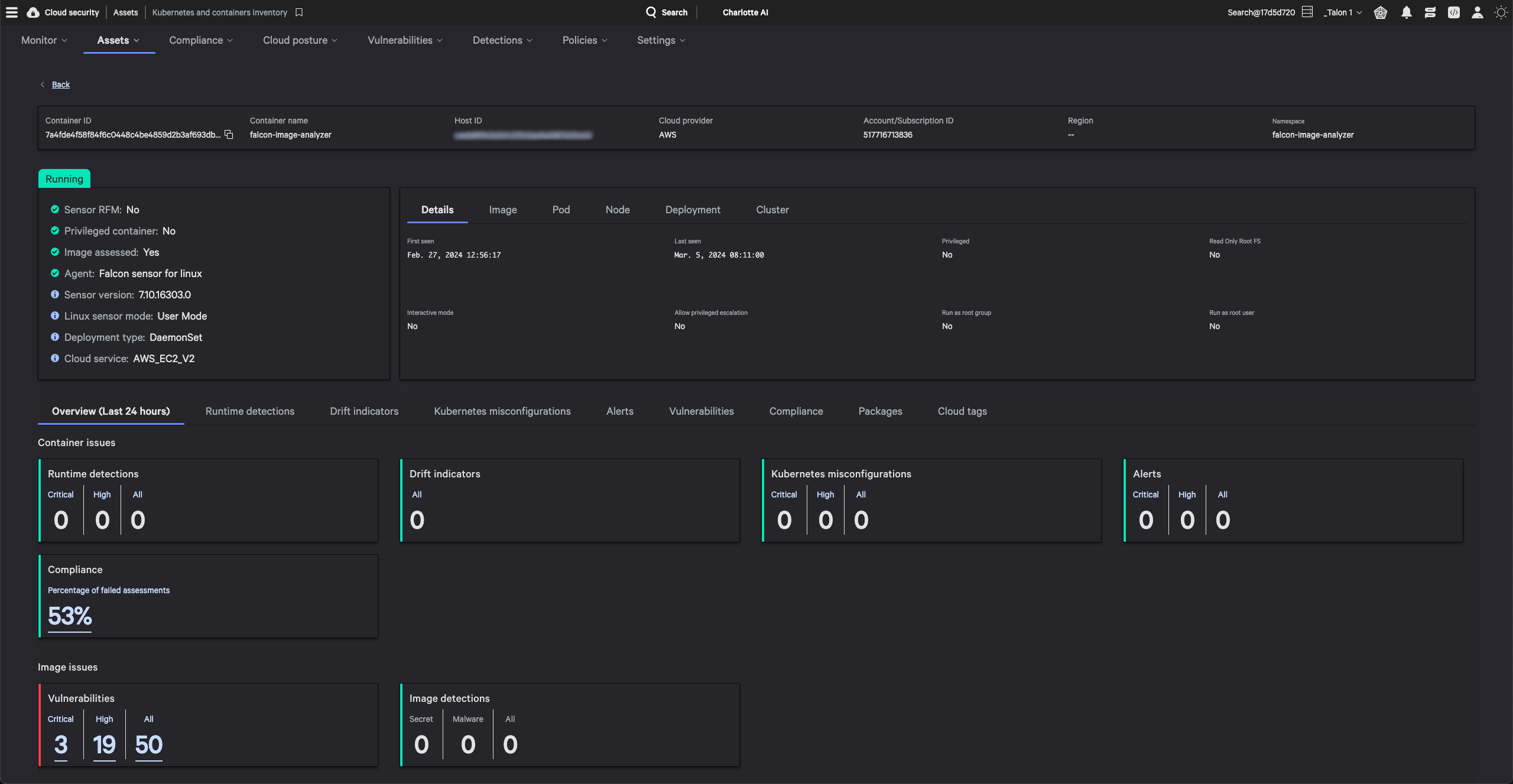
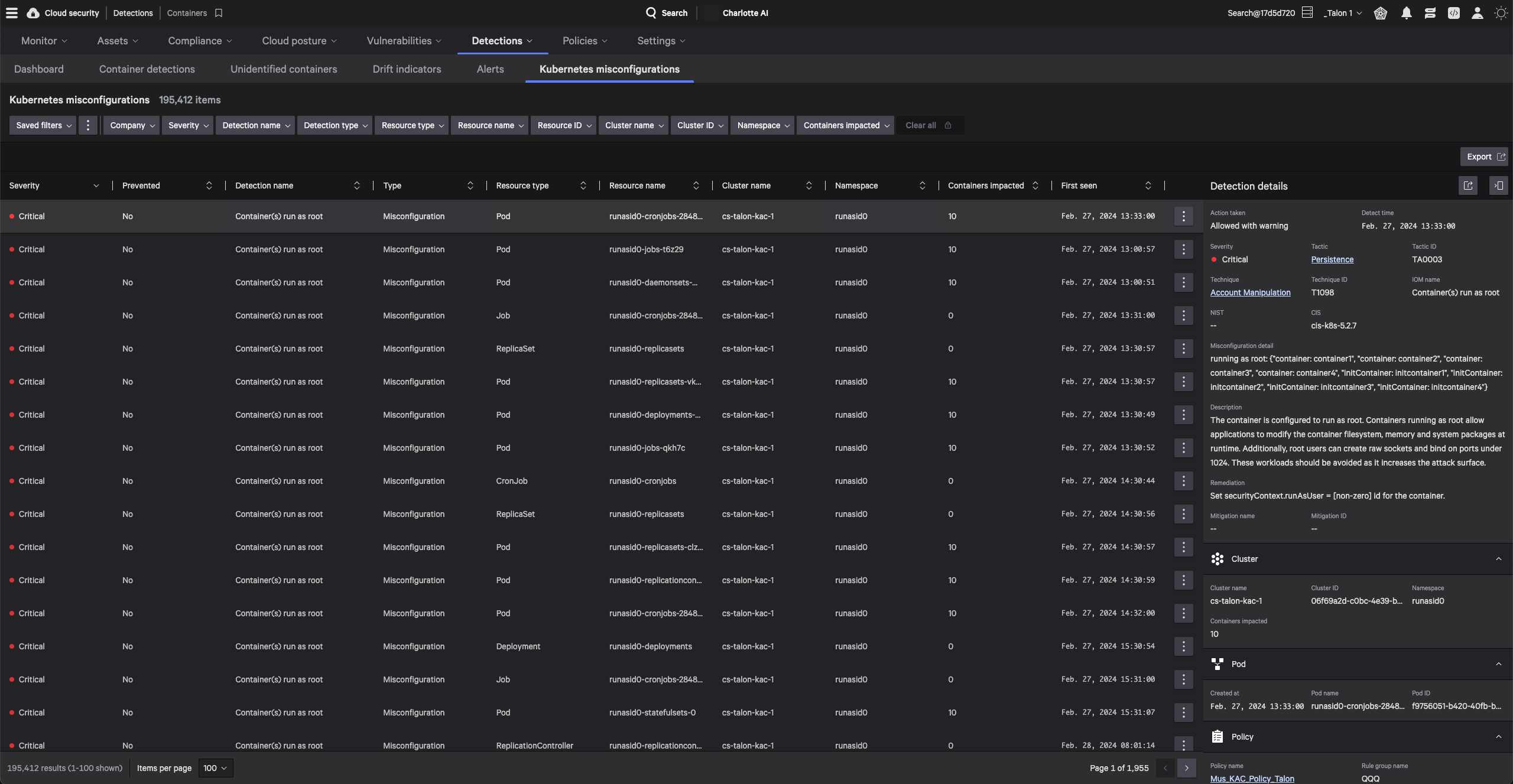
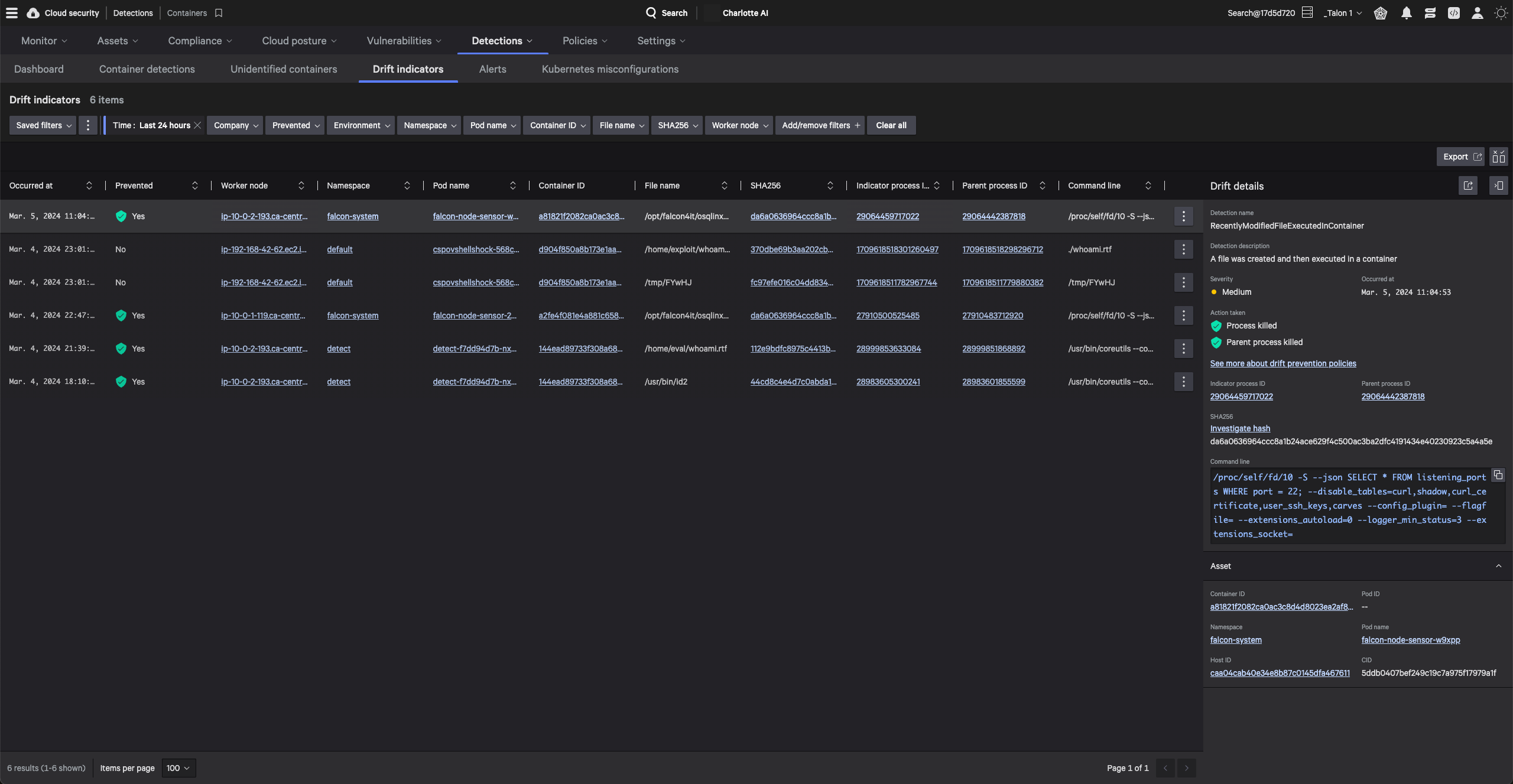
CrowdStrike receives the highest score of all vendors in the Strategy category and receives the highest scores possible in the Vision and Innovation criteria.


Get instant and complete visibility into your entire cloud estate. Deploy in minutes with agentless scanning, zero impact to your business, and no obligations attached.
Schedule free reviewBuild faster and more securely on your cloud providers with Falcon Cloud Security.
1 Results are from Mercury Financial. Individual results may vary by customer.
2 These numbers are projected estimates of average benefit based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.