CrowdStrike Falcon® Counter Adversary Operations
Know your adversary and stop breaches
The leader in cyber threat intelligence with the industry’s only unified intelligence and hunting team built to disrupt adversaries.
From reactive threat response to a confident intelligence-driven defense
Customer assessment
80%
improvement in risk posture by continuously strengthening security defenses1
Customer assessment
11k hrs
less in threat research time with insights from CrowdStrike experts1
Customer assessment
$3M
average yearly savings in security operations through end-to-end intelligence automation1
Anywhere Real Estate trusts CrowdStrike to stop breaches
The leader in threat intelligence-driven defense
The fastest attacks can happen in two minutes.2 Counter Adversary Operations is the industry’s only unified threat intelligence and hunting team that delivers 24/7 hunting, automated investigations, and expert insights to enable organizations to outpace the adversary.
Key capabilities of CrowdStrike Counter Adversary Operations
Stop the most advanced attacks
Falcon Adversary OverWatch is the industry’s only 24/7 threat hunting service that spans endpoint, identity, and cloud to proactively disrupt adversaries in real-time. Powered by industry-leading threat intelligence and advanced AI, our experts never sleep to stop the breach on your behalf.
Access world-class intelligence across CrowdStrike Falcon® platform modules to make better, faster decisions. No need for costly and fragile integrations, insights are available on day one and instantly accessible within analyst’s workflows.
Prioritize patching of vulnerabilities found within your environment. By understanding the adversaries targeting your industry and region, you can proactively patch systems before any exploit attempt.
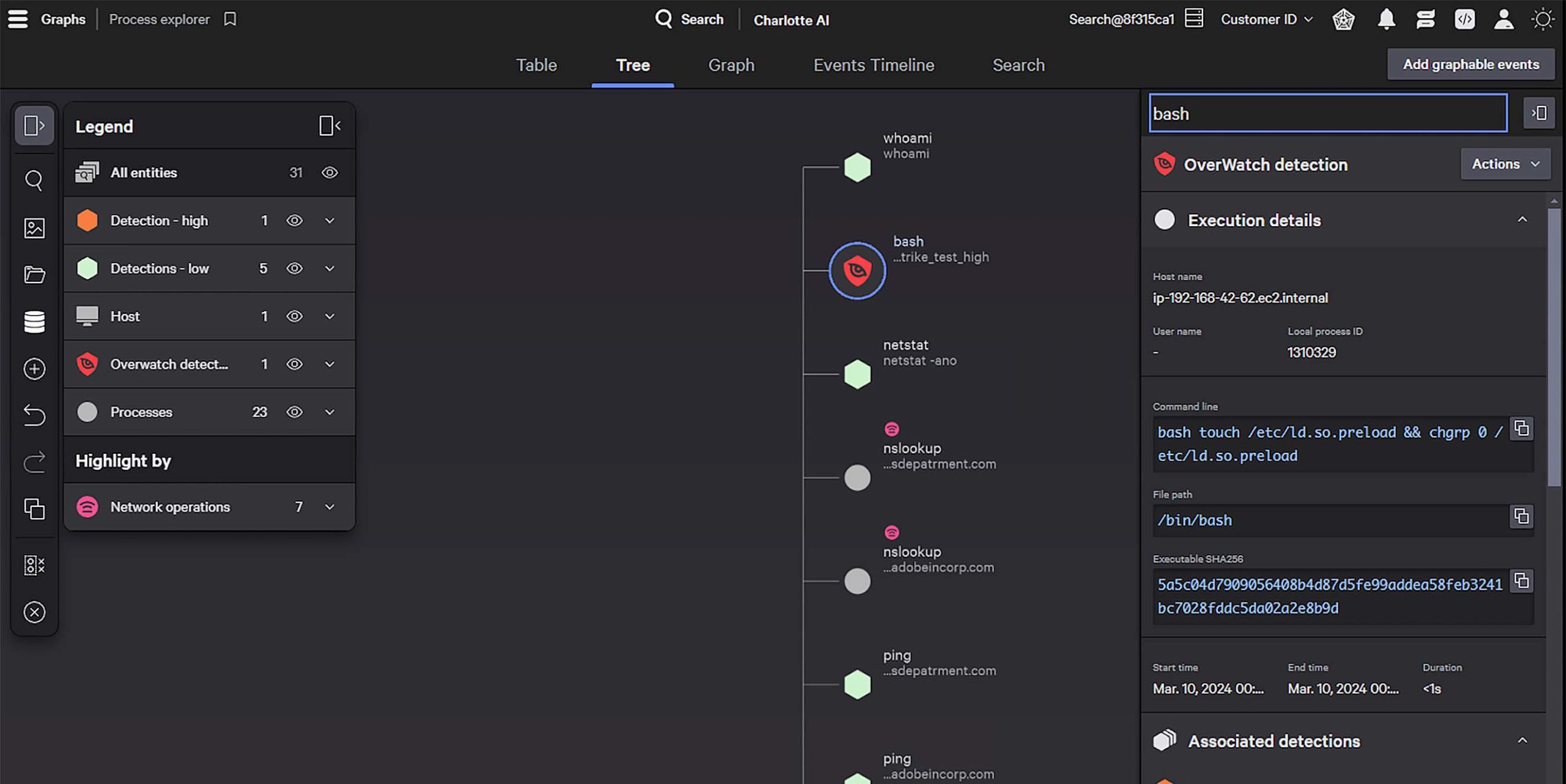
This process tree includes a Falcon Adversary OverWatch detection that identifies an attempt to execute a malicious BASH script.
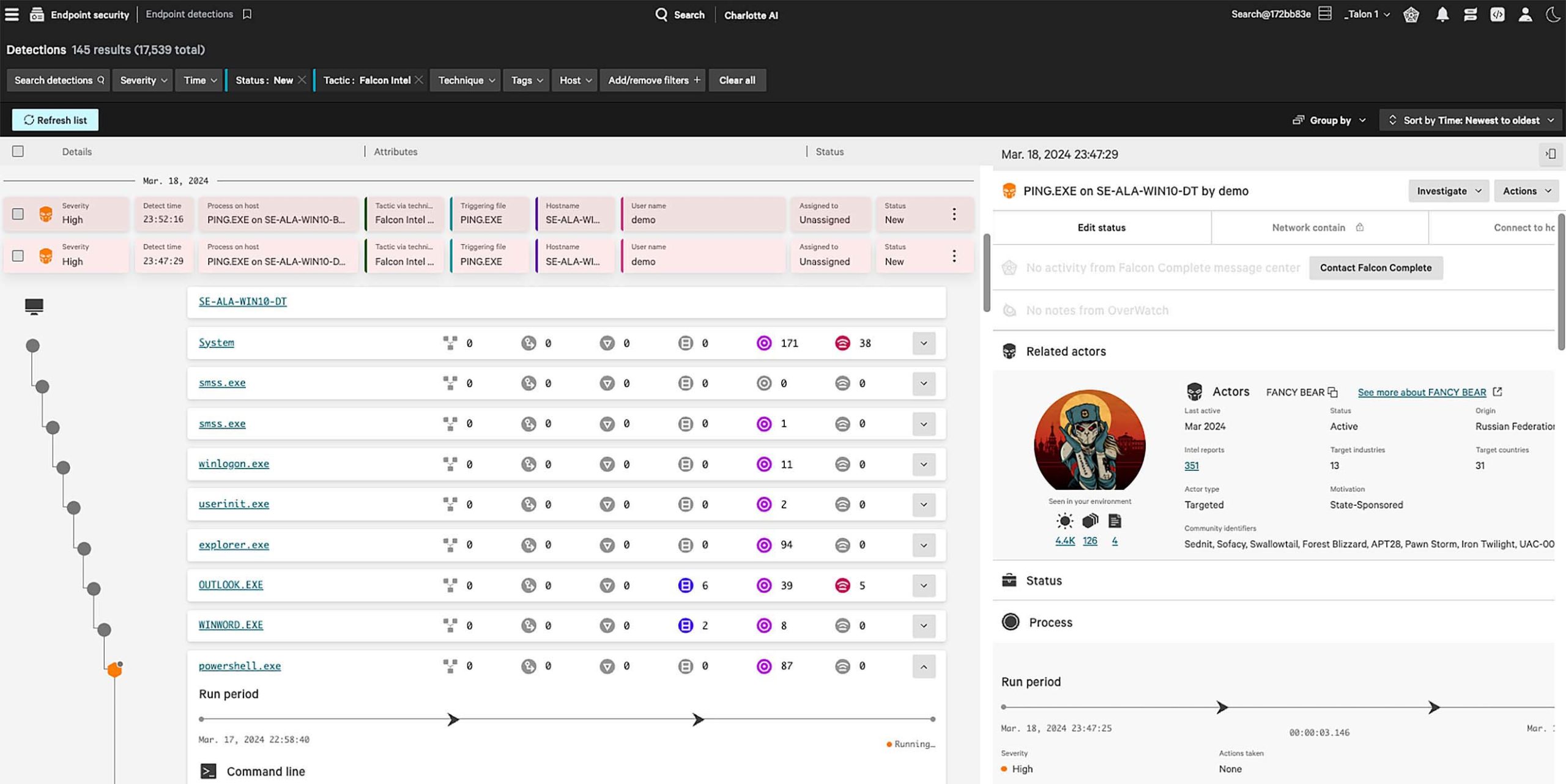
This Falcon platform endpoint detection is enriched with threat intelligence, including attribution, and provides direct links to related vulnerabilities, detections and malware sandbox reports.
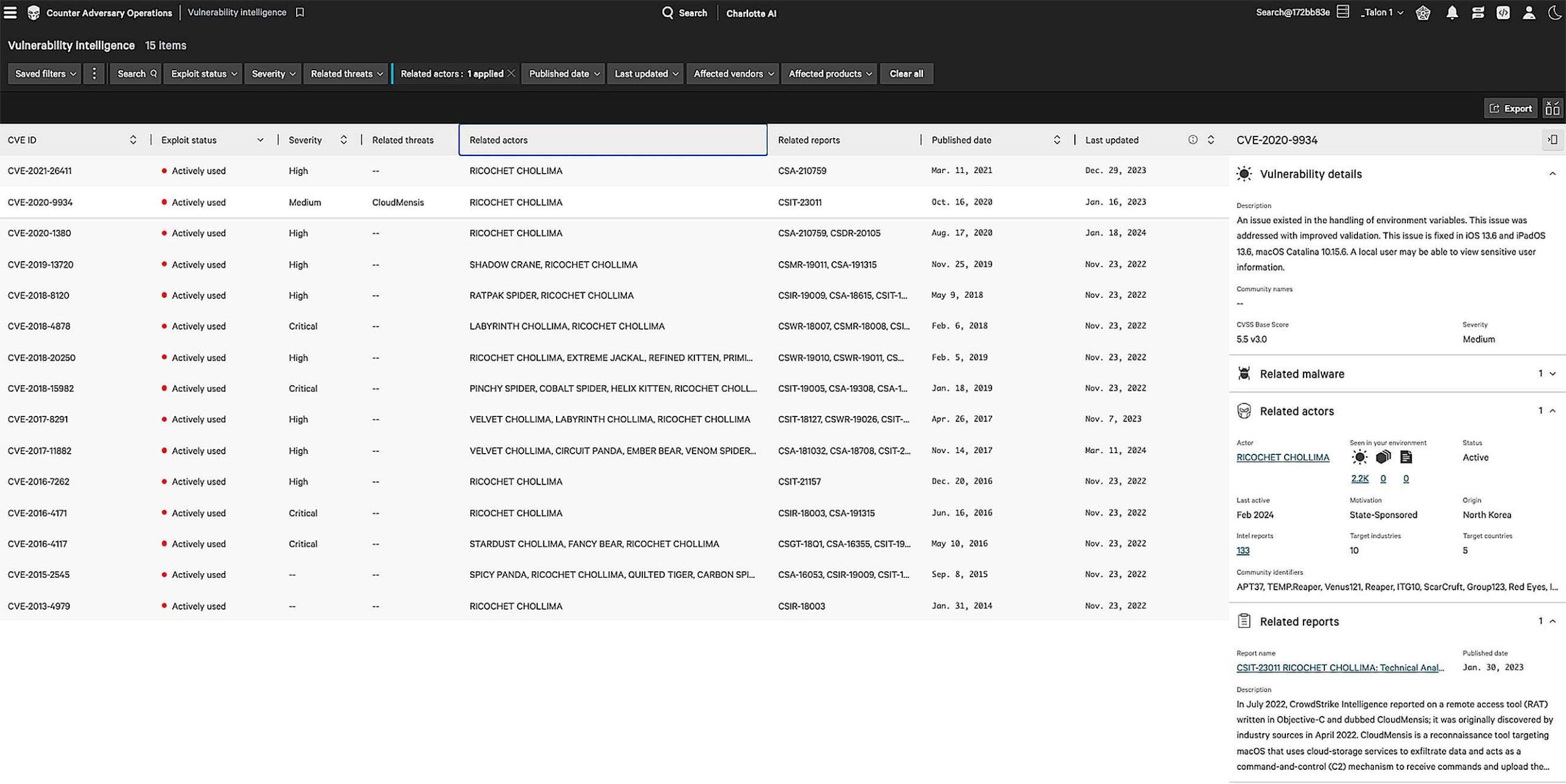
The vulnerability intelligence app is updated from the National Vulnerability Database in real-time. Access in-depth vulnerability details and pivot directly to CrowdStrike Falcon® Spotlight to immediately patch systems in your environment.
Supercharge the SOC
Falcon Adversary Intelligence provides detailed profiles of over 230 adversaries, including nation-states, eCrime groups, and hacktivists. Each profile breaks down their methods, maps their tactics to the MITRE ATT&CK framework, and reveals the vulnerabilities they exploit.
Accelerate incident triage and investigations by instantly submitting potential threats found within your environment to an advanced sandbox. Then extract indicators and instantly deploy countermeasures.
Monitor the dark web and criminal forums to detect and block threats that can compromise identities, sensitive data, and damage your organization’s brand.
Gain access to CrowdStrike’s validated, real-time indicators of compromise. Leverage pre-built integrations and easy to use APIs to get the right defenses, to the right tool, at the right time.
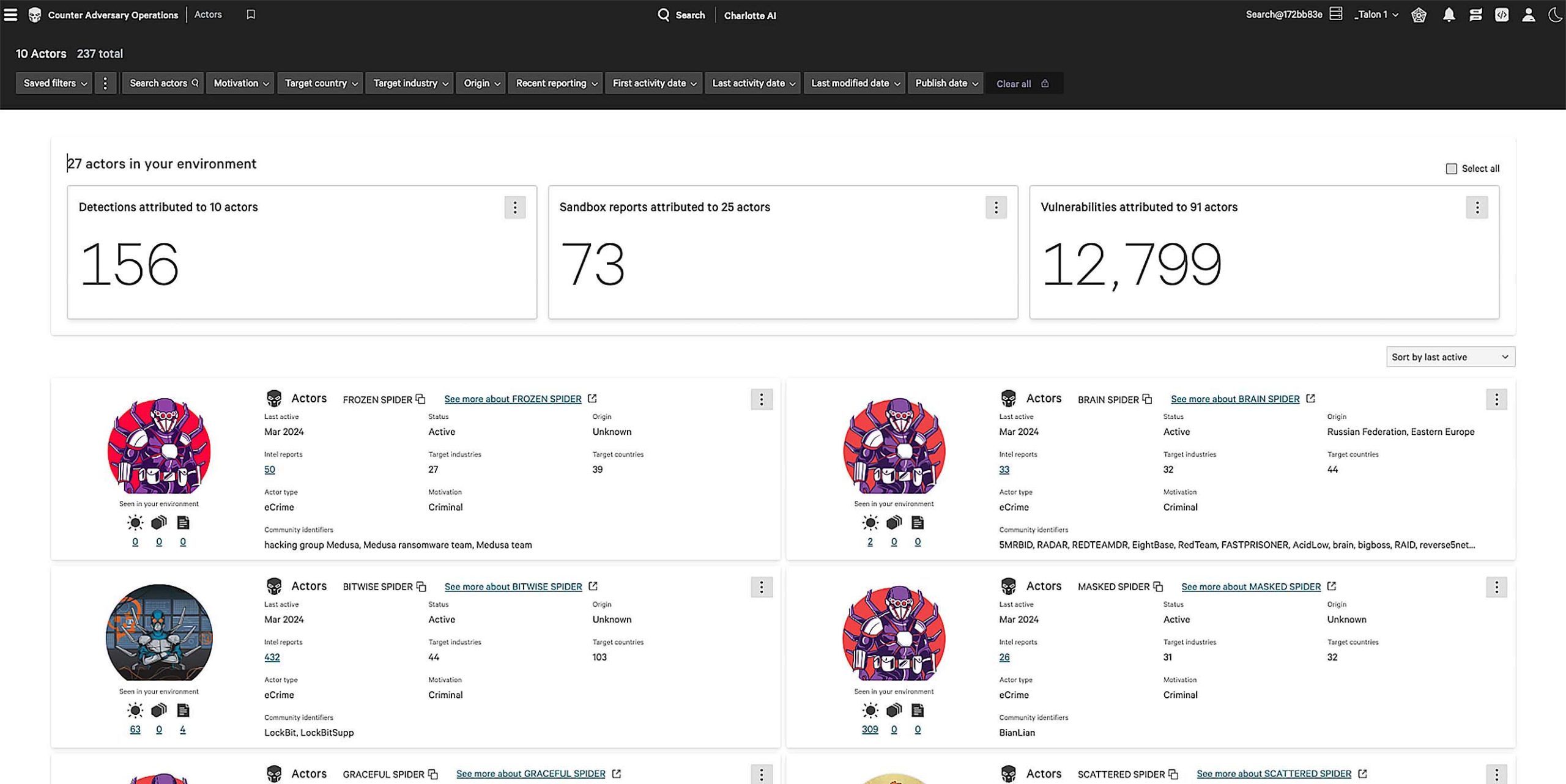
The adversary listing not only provides comprehensive profiles, but enables you to link directly to Falcon platform modules to remediate security issues in your environment.
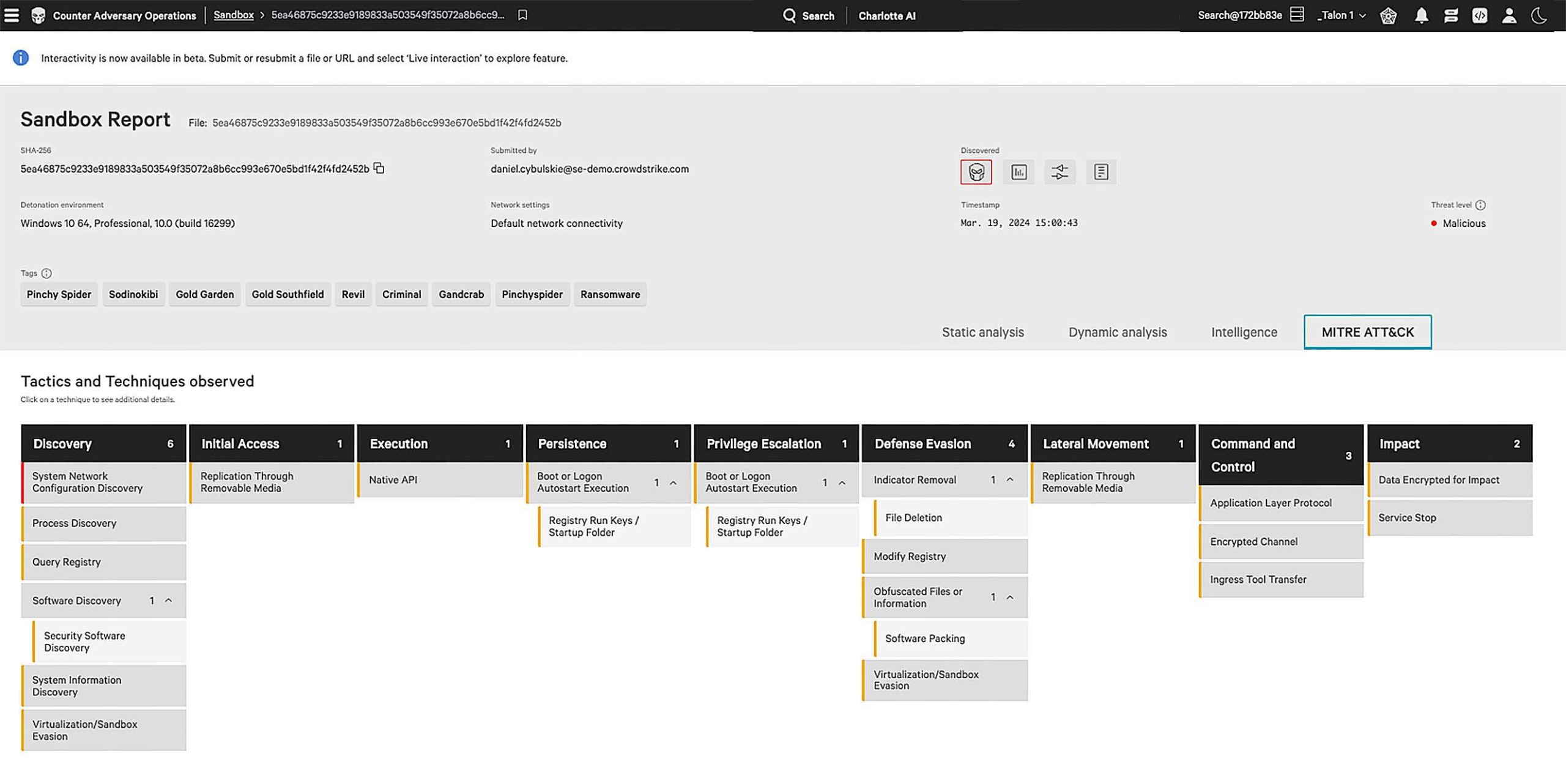
CrowdStrike Falcon® Sandbox reports provide a comprehensive overview of the behavior of suspicious files. Use the threat score to quickly triage threats, block malicious IPs, and automatically deploy related indicators of compromise.
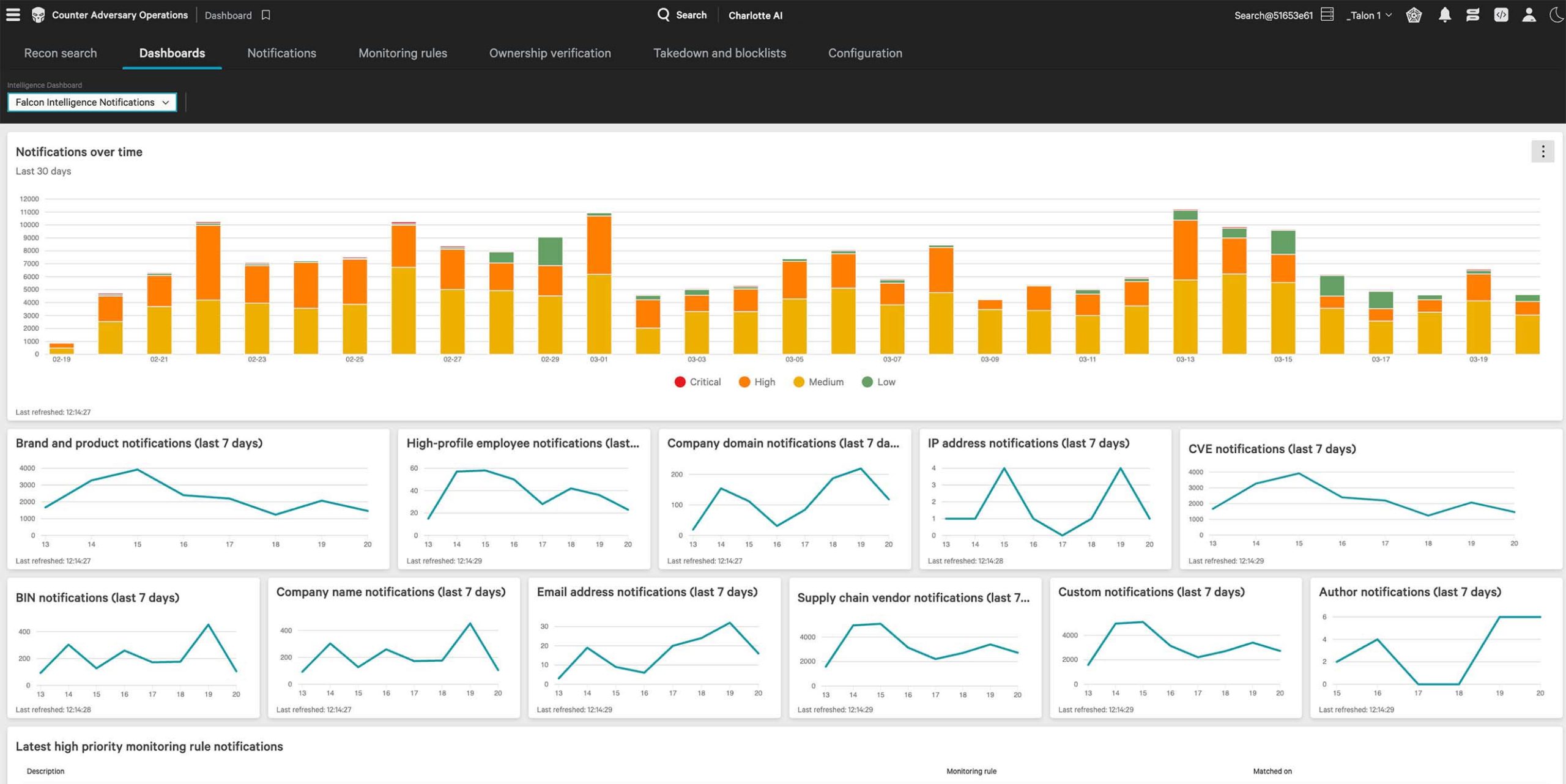
Interactive dashboards provide visibility into potential threats across the dark web. Drill down for details or set block lists and perform takedowns.
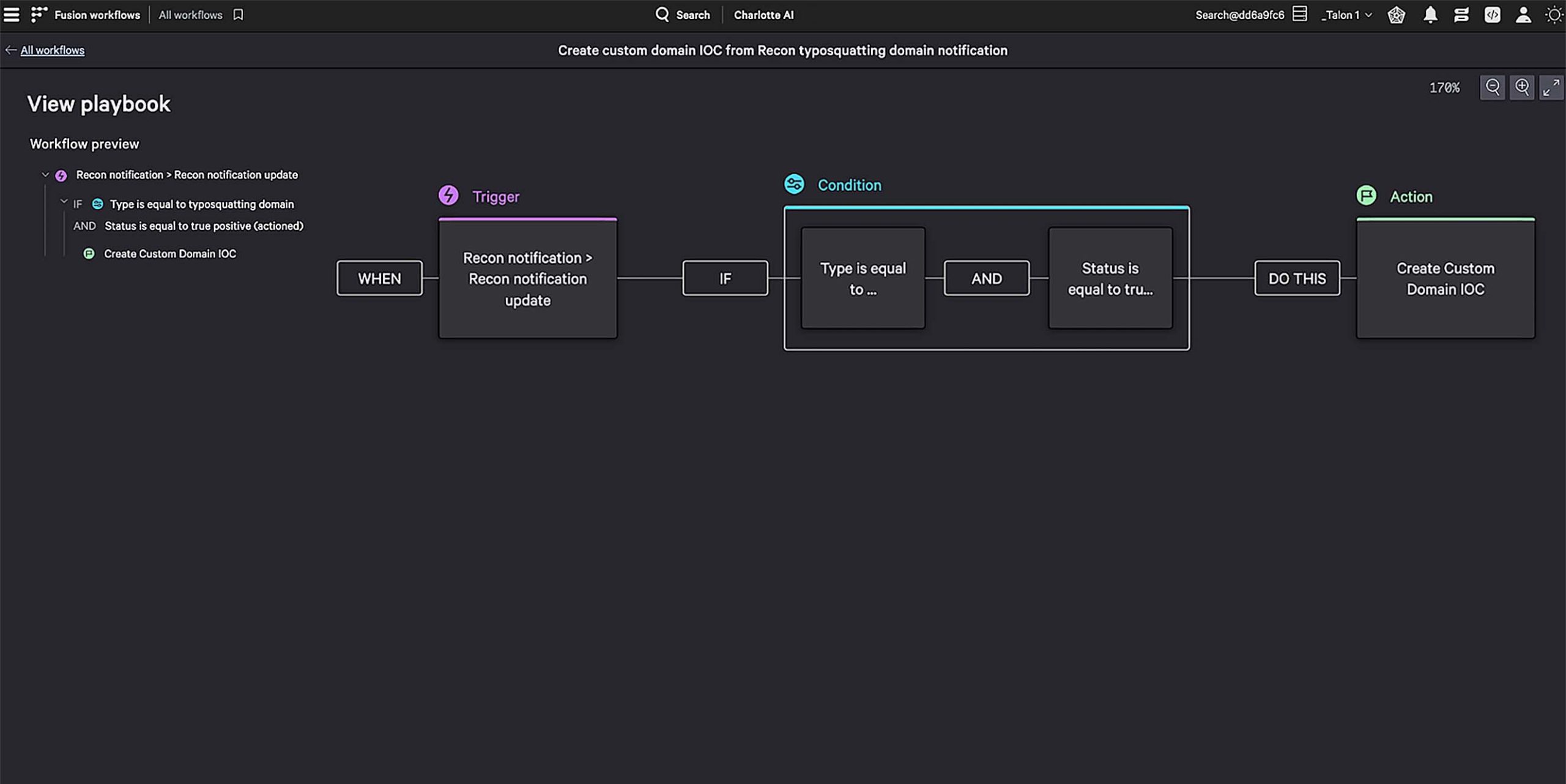
This CrowdStrike Falcon® Fusion SOAR workflow evaluates the severity of a threat discovered by CrowdStrike Adversary Intelligence on the dark web, then triggers a Falcon platform detection any time the domain is observed.
Level up your security team
Falcon Adversary Intelligence Premium delivers thousands of industry-leading intelligence reports each year and empower your team to reduce the attack surface, improve defenses, guide threat hunters and detection engineers, and update leadership on the most relevant threats to your business.
Reduce the workload of in-house security engineering teams by accessing regularly updated libraries of hunting queries and detection rules created and validated by CrowdStrike experts.
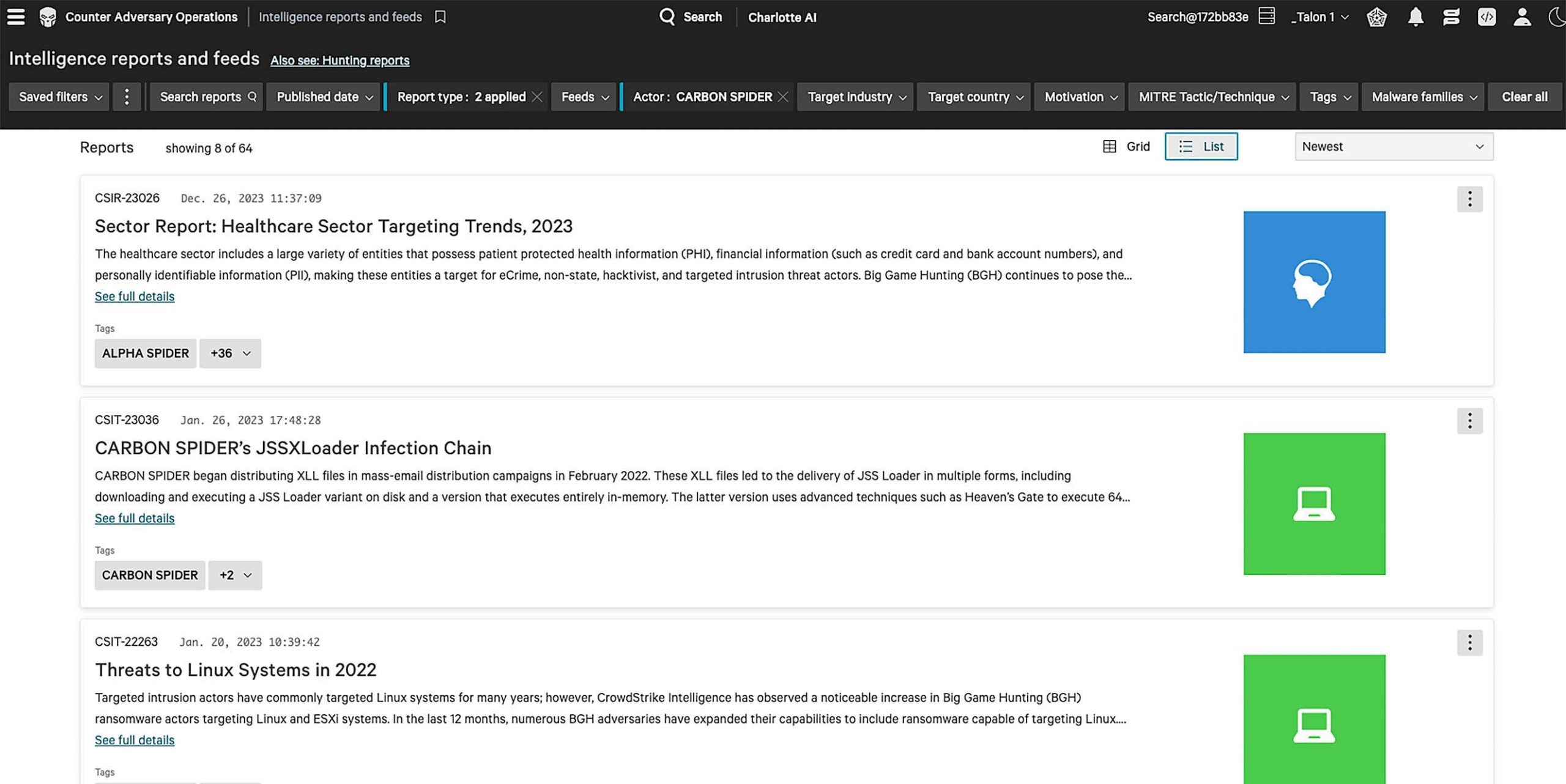
Gain access to daily alerts, technical reports, and strategic insights outlining adversary trends and recent activity. Intelligence reports are available via the AI-powered Falcon platform, via email, and through an easy to use API.
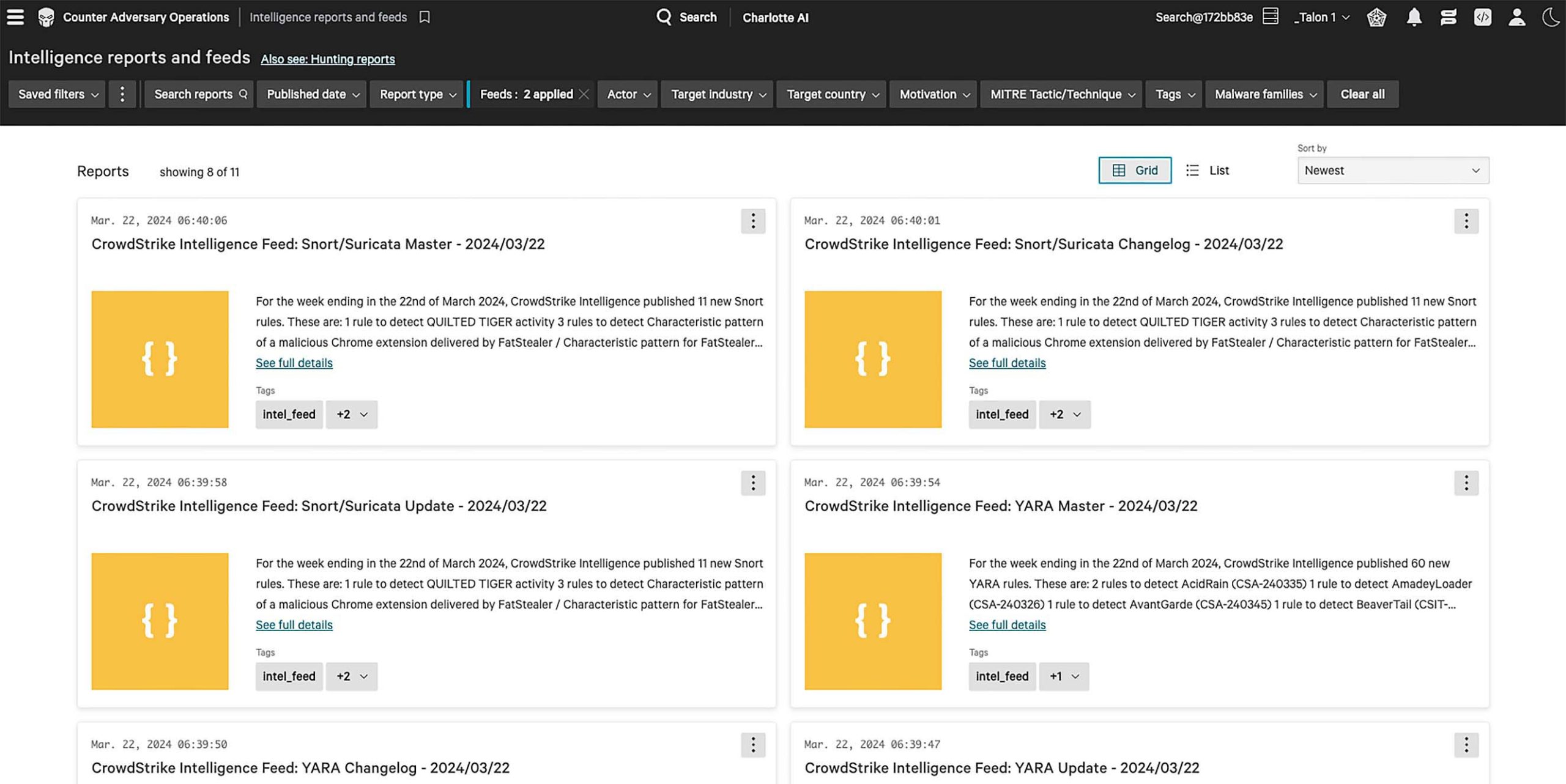
Pre-built, validated and tested detection rules are delivered in many formats and can be immediately deployed via API.
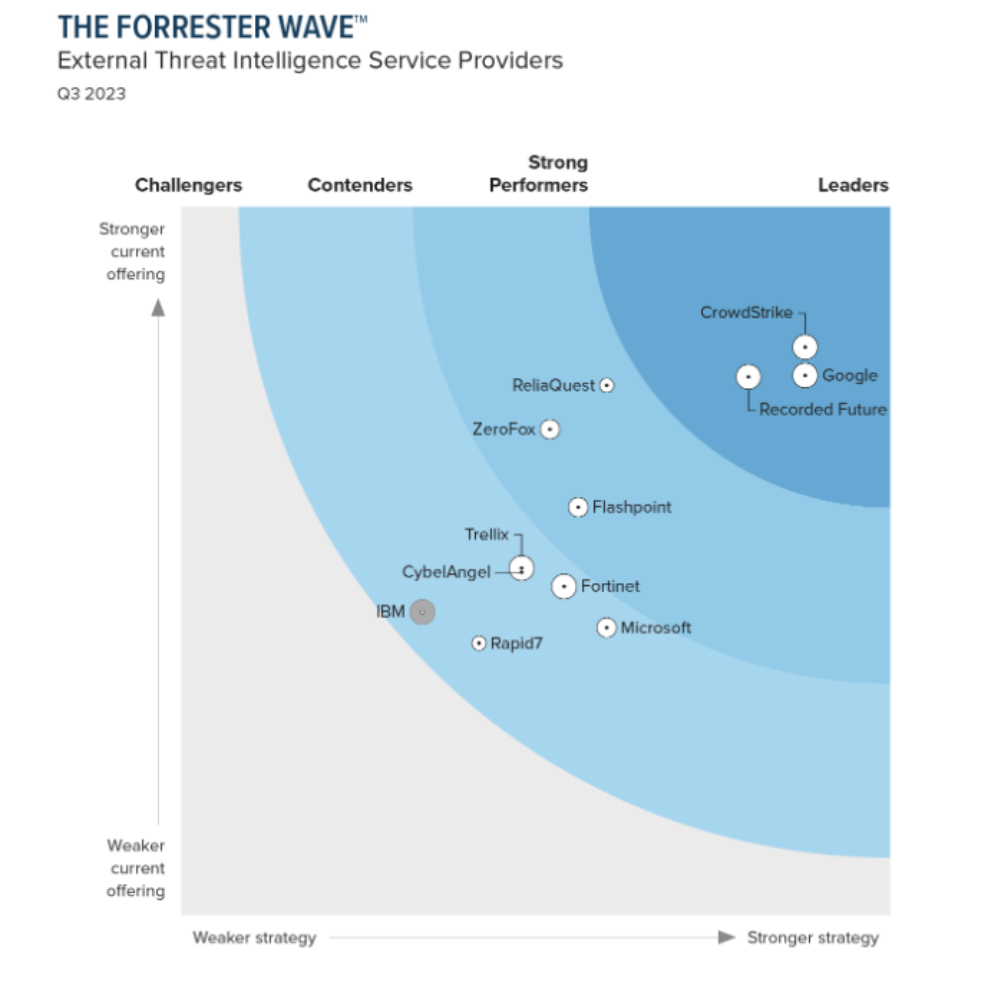
Forrester names CrowdStrike a “Leader” in The Forrester Wave™: External Threat Intelligence Service Providers, Q3 2023
CrowdStrike received the highest ranking of all vendors in the Current Offering category, with the highest score possible in 16 criteria, surpassing all other vendors evaluated in the report.
See the power of Counter Adversary Operations in three minutes
Proactively pursue adversaries to stop breaches

Know them. Find them. Stop them.
Learn how the world’s most dangerous adversaries are targeting organizations like yours.
Explore the Adversary UniverseFeatured resources
1 CrowdStrike BVA – CrowdStrike BVA numbers are projected estimates of average benefits based on recorded metrics provided by customers with 50 security team members and 6 analysts during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
2 CrowdStrike 2024 Global Threat Report