How to Prevent Malware with Custom Blocking in CrowdStrike Falcon®

How to Prevent Malware with Custom Blocking
This document covers malware prevention via the custom blocking feature of Falcon. Falcon uses multiple methods to prevent and detect malware. Those methods include machine learning, exploit blocking, blacklisting and indicators of attack. This unified combination of methods protects you against known malware, unknown malware, script-based attacks, file-less malware and others. This document covers blacklisting and whitelisting steps.
Video
Preventing malware with custom blocking
There are cases when you might want to block applications because you are certain that you never want them to run in your environment.
Falcon allows you to upload hashes from your own black or white lists. To enabled this navigate to the Configuration App, Prevention hashes window, and click on “Upload Hashes” in the upper right-hand corner. Note that you can also automate the task of importing hashes with the CrowdStrike Falcon® API.
Configuration App
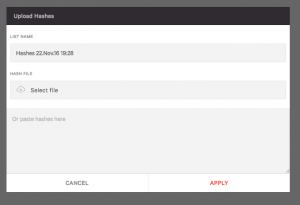
Then we can either brows to a file or paste a list directly into the windows. The list can be a text file with one MD5 or SHA256 hash per line. All valid MD5 and SHA256 hashes will be uploaded. Rows with non-MD5/SHA256 hash format will be ignored.
The list of hashes must meet the following criteria:
- Formatted as a plain text (.txt) file
- Contains up to 3,000 MD5 and SHA256 hashes (per file)
- Contains one MD5 or SHA256 hash per line
- Hash being added is for an executable file only
All valid MD5 and SHA256 hashes will be uploaded, even if a hash was already uploaded as part of a different list. Rows with non-MD5/SHA256 hash format will be ignored.
Apply changes
After clicking “apply” you’ll have the opportunity to select an action you’d like Falcon to take when a matching hash is detected. Select your choice and click “apply” again.

A confirmation window will appear, select “apply” if everything looks correct. If not make changes until the settings are as desired.
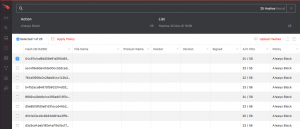
You can see that the hash has been uploaded. If you want to upload more hashes later, click on the “Upload Hashes” icon on the top right corner of the window.
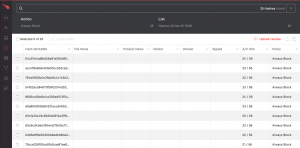
Editing Lists
A list of the hashes along with the selected policy, in this case “always block” is visible from the “Configuration -> Prevention Hashes” dashboard. If individual hashes need to be edited select the box next to the chosen hash and hit the “apply policy” button at the top.
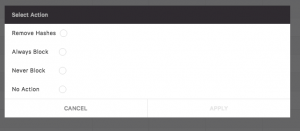
A “Select Action” dialogue window opens that will change the settings for all the selected hashes.
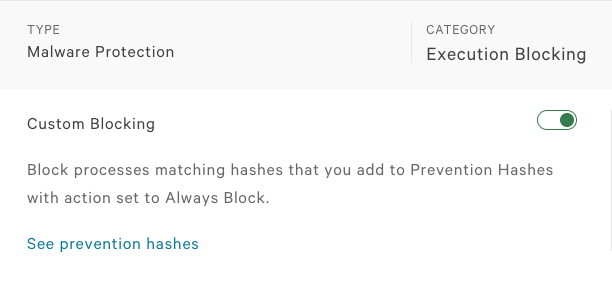
Enable Blocking
Now we also need to make sure that custom blocking is enabled in the “Malware Protection” section of the specific policy. For that, let’s go back to the “Configuration app -> Prevention Policy” page and check. If it’s not enabled for the desired policy, you can toggle the “custom blocking” button to enable it. Don’t forget to save the changes to your policy.
Validation
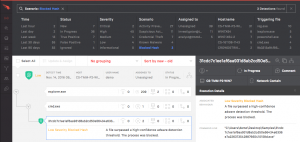
This is how this prevention shows up in the Falcon User Interface. It will show as being blocked per your organization policy.
Conclusion
Falcon uses an array of methods to protects against known malware, unknown malware and file-less malware. Those methods include:
- Machine Learning
- Exploit Blocking
- Indicators of attack
- Blacklisting and whitelisting
Falcon uniquely combines these powerful methods into an integrated approach that protects endpoints more effectively against both malware and breaches.