Customer Story
NetApp: Cloud is our biggest security concern
View storyReports, white papers, crowdcasts, and more.

Uncover notable themes, trends and events across the cyber threat landscape.
Get the report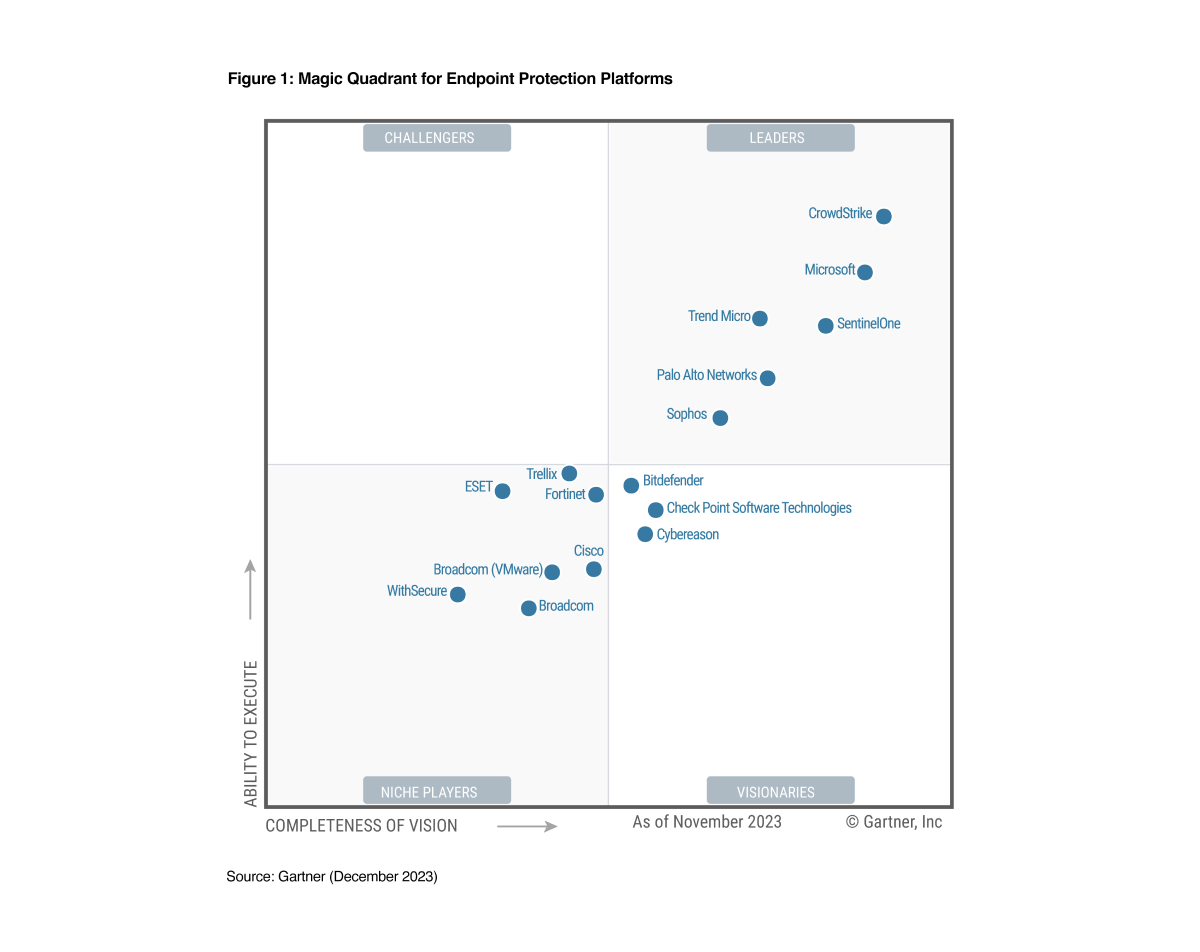
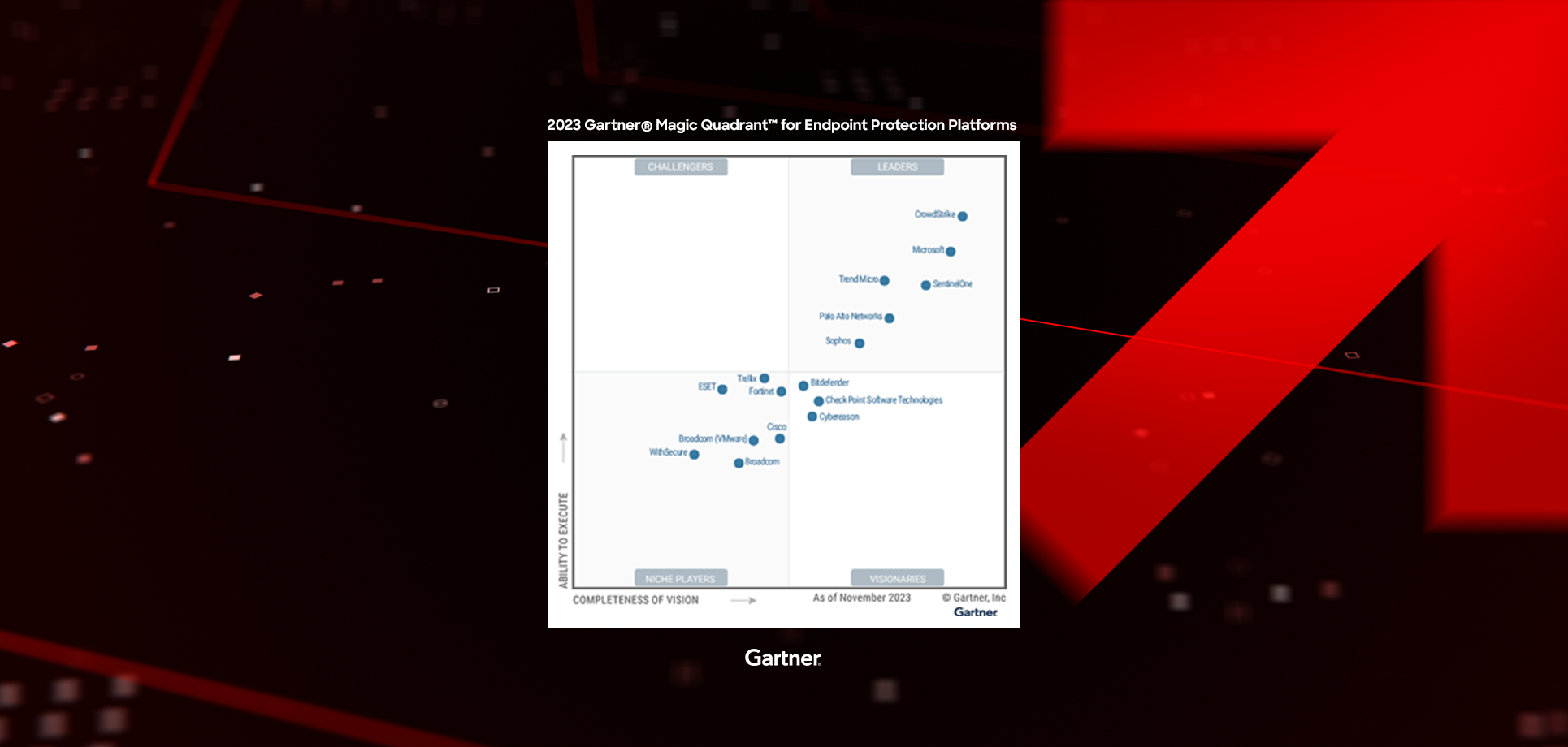
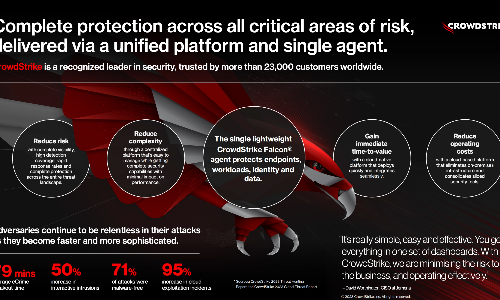
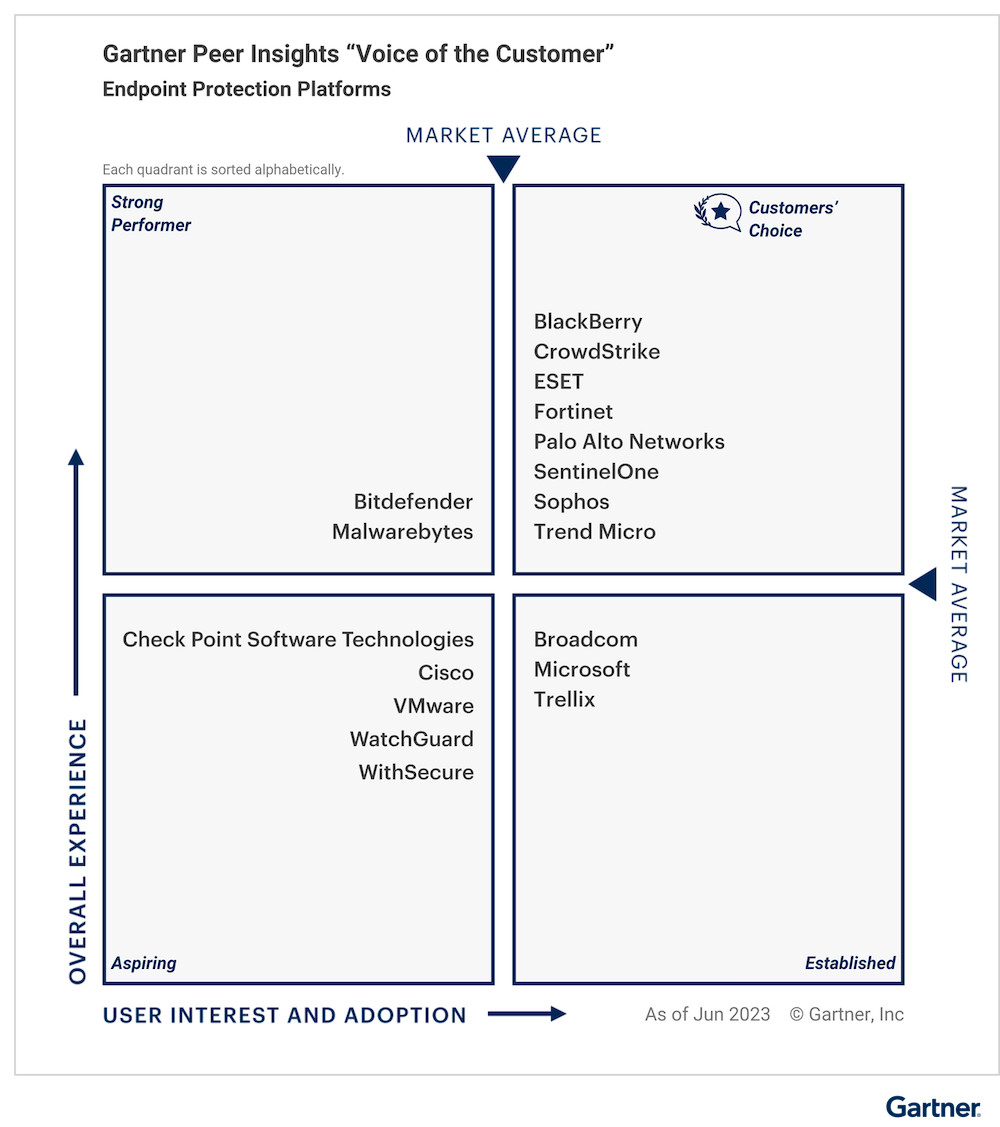
A Leader for the fourth consecutive time in the 2023 Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Get the reportAll resources
Filter by








CrowdCast
Unstoppable Innovations CrowdCast Series From Red-Hot Releases to Future Roadmap
Listen to CrowdCast








White Paper
The Power of One: lotta alla frammentazione della sicurezza informatica…
Read white paper

White Paper
Cinque driver aziendali per il consolidamento della sicurezza informatica
Read white paper




Customer Story
SA Power Networks: Securerly Delivering Reliable Energy to South Australia
View story

White Paper
Unlock Proactive Exposure Management: 5 Key Elements and Why Traditional…
Read white paper











CrowdCast
SEC Readiness: Demystifying the Four-Day Breach Disclosure Requirement
Listen to CrowdCast






Data Sheet
Falcon Cloud Security: Cloud Infrastructure Entitlement Management (CIEM) Solution Brief
View data sheet



















White Paper
Application Security Posture Management: Securing Cloud-Native Applications at Scale
Read white paper







Customer Story
Commercial Bank of California: Hardening our cloud environments against data…
View story
CrowdCast
Top 2024 Cybersecurity Trends Series – Session #2: Cybersecurity Consolidation…
Listen to CrowdCast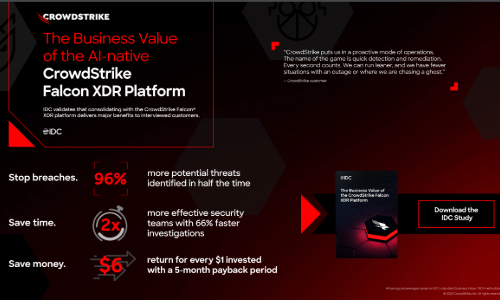












Video
Mesa Redonda Virtual: Descifrando la Ciberseguridad: Estrategias de los Protectores
Watch video










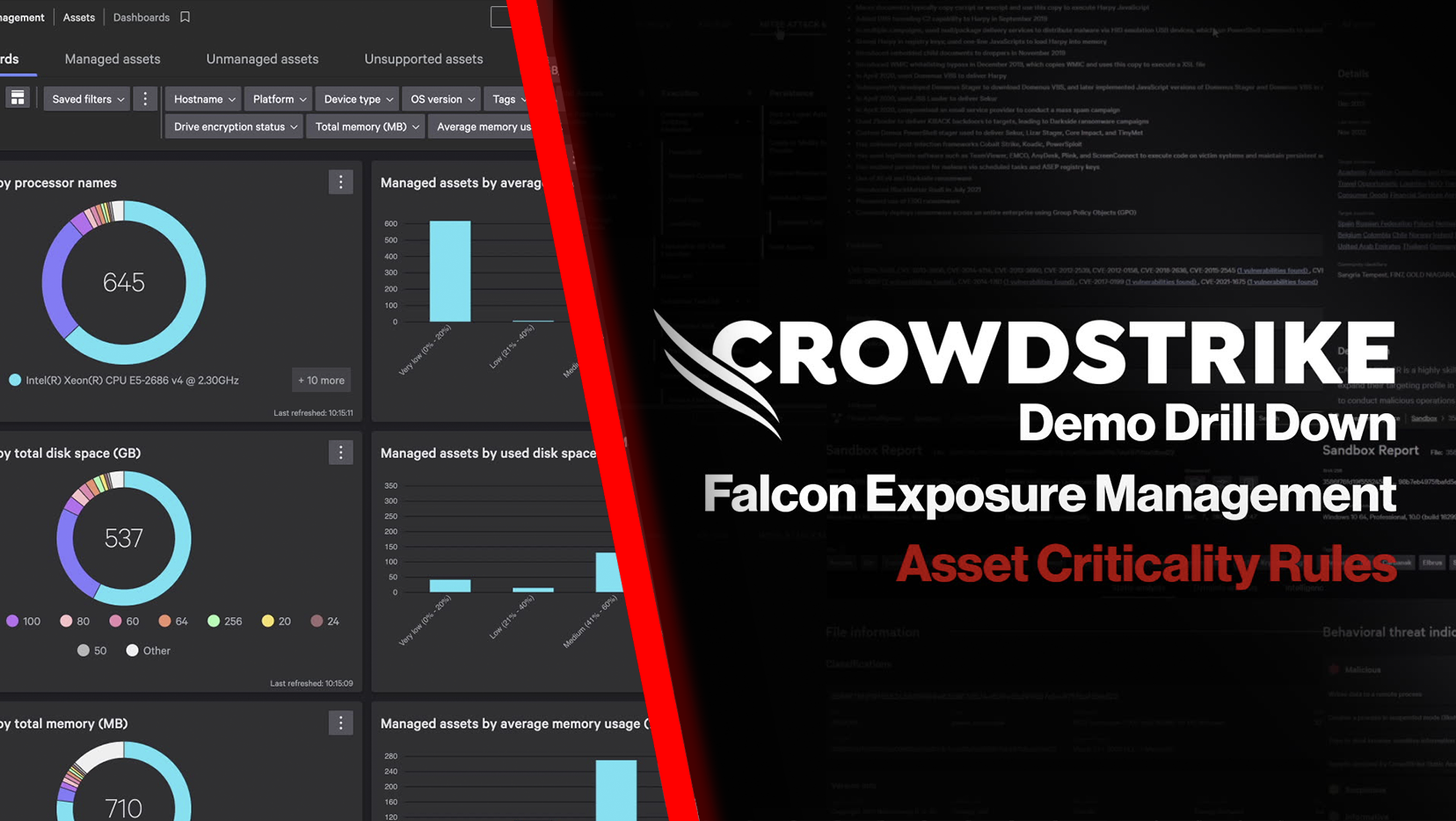
Demo
Falcon Identity Protection Unified Identity Protection for Hybrid Environments: Demo…
Watch demo



White Paper
Configuraciones inadecuadas en la nube que son fácilmente explotadas y…
Read white paper
White Paper
Safeguarding Healthcare Mergers & Acquisitions (M&A) by Integrating Cybersecurity from…
Read white paper


CrowdCast
The Convergence of AI+ Cybersecurity with CrowdStrike and Abnormal Security
Listen to CrowdCast











CrowdCast
Unstoppable Innovations CrowdCast Series - Session #4: Rise Above SCATTERED…
Listen to CrowdCast




White Paper
Crafting a Battle-Tested Team with the CrowdStrike Adversary Emulation Exercise
Read white paper






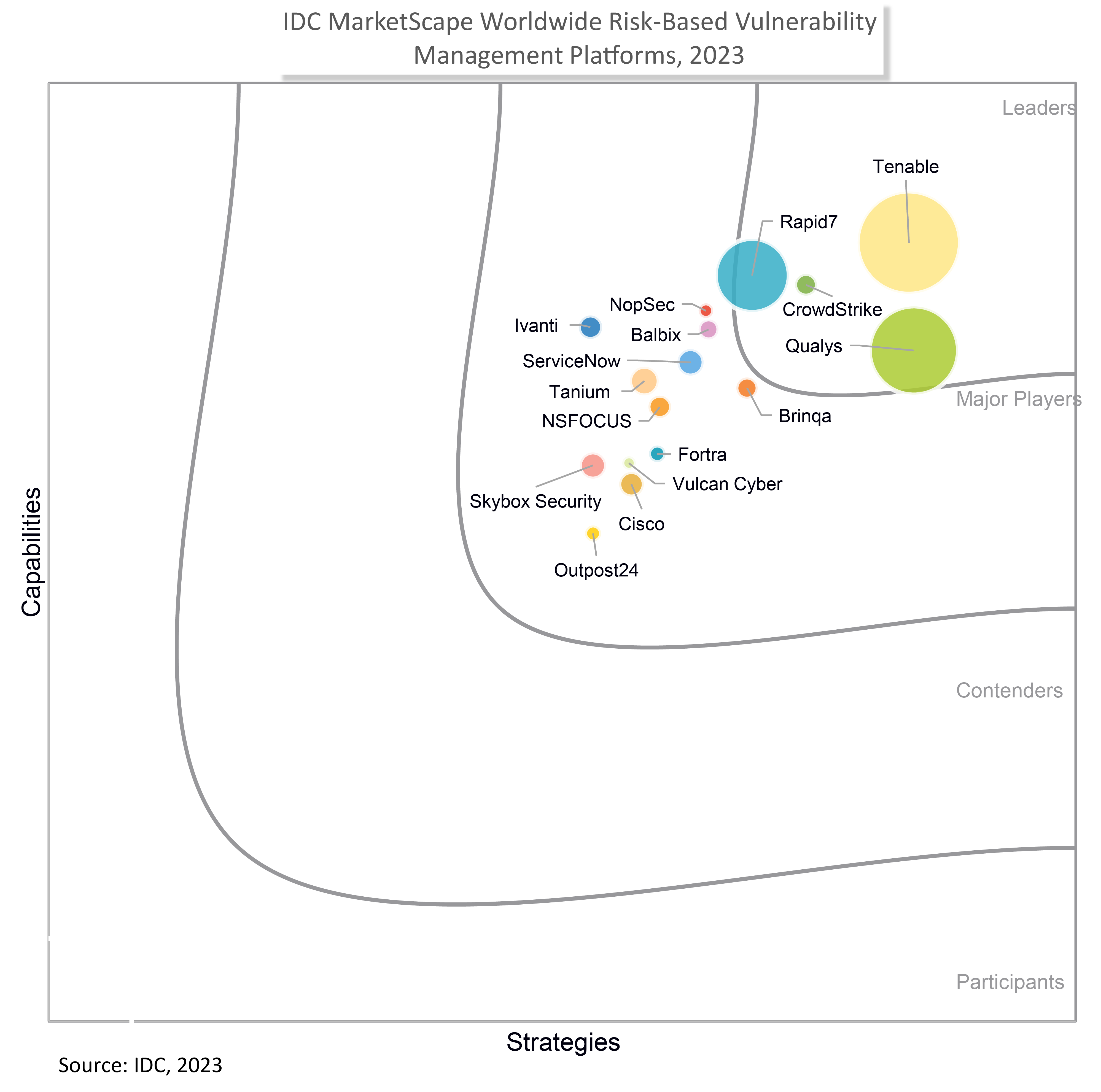
Report
IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
View report


Customer Story
Tabcorp Partners with CrowdStrike to Drive Stronger Security from Endpoint…
View story


Guide
CrowdStrike Falcon FileVantage Add-on for Splunk Installation and Configuration Guide
View guide




CrowdCast
Unstoppable Innovations CrowdCast Series - Part 2: Shut Down Adversary…
Listen to CrowdCast
CrowdCast
Unstoppable Innovations CrowdCast Series - Part 1: Defeat Cloud Adversaries…
Listen to CrowdCast





Report
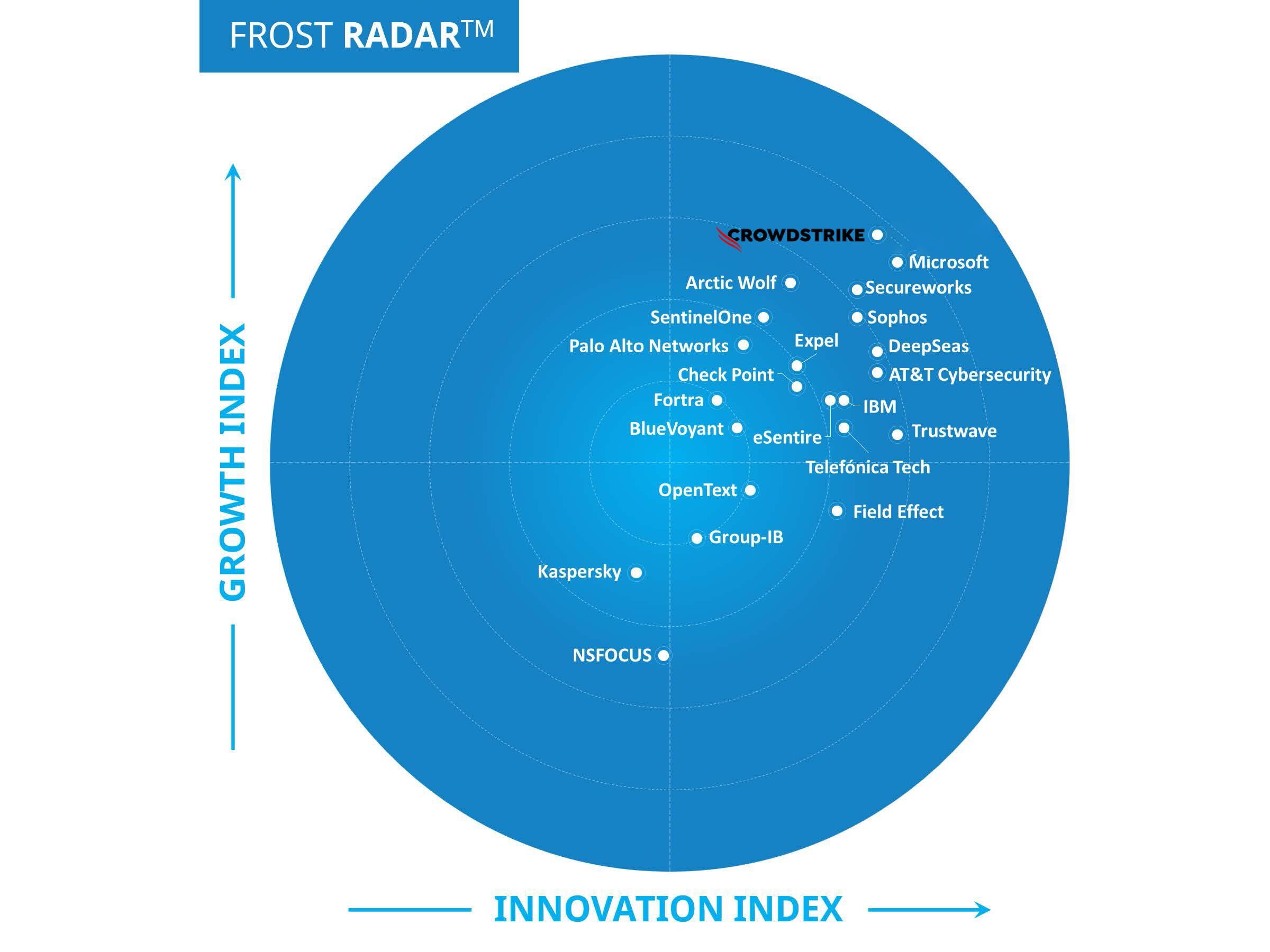
2023 Frost Radar™ Leader: CrowdStrike’s Cloud-Native Application Protection Platform (CNAPP)
View report






White Paper
I principali motivi per aggiungere subito Falcon Identity Protection al…
Read white paper


Customer Story
CrowdStrike Helps Medium-Sized Business Build Robust Corporate-Class Cybersecurity Defense
View story







White Paper
The Power of One: Combating Cybersecurity Fragmentation with a Consolidated…
Read white paper







CrowdCast
Cloud Threat SummitVirtual Event: The Rise of the Cloud-Conscious Adversary
Listen to CrowdCast











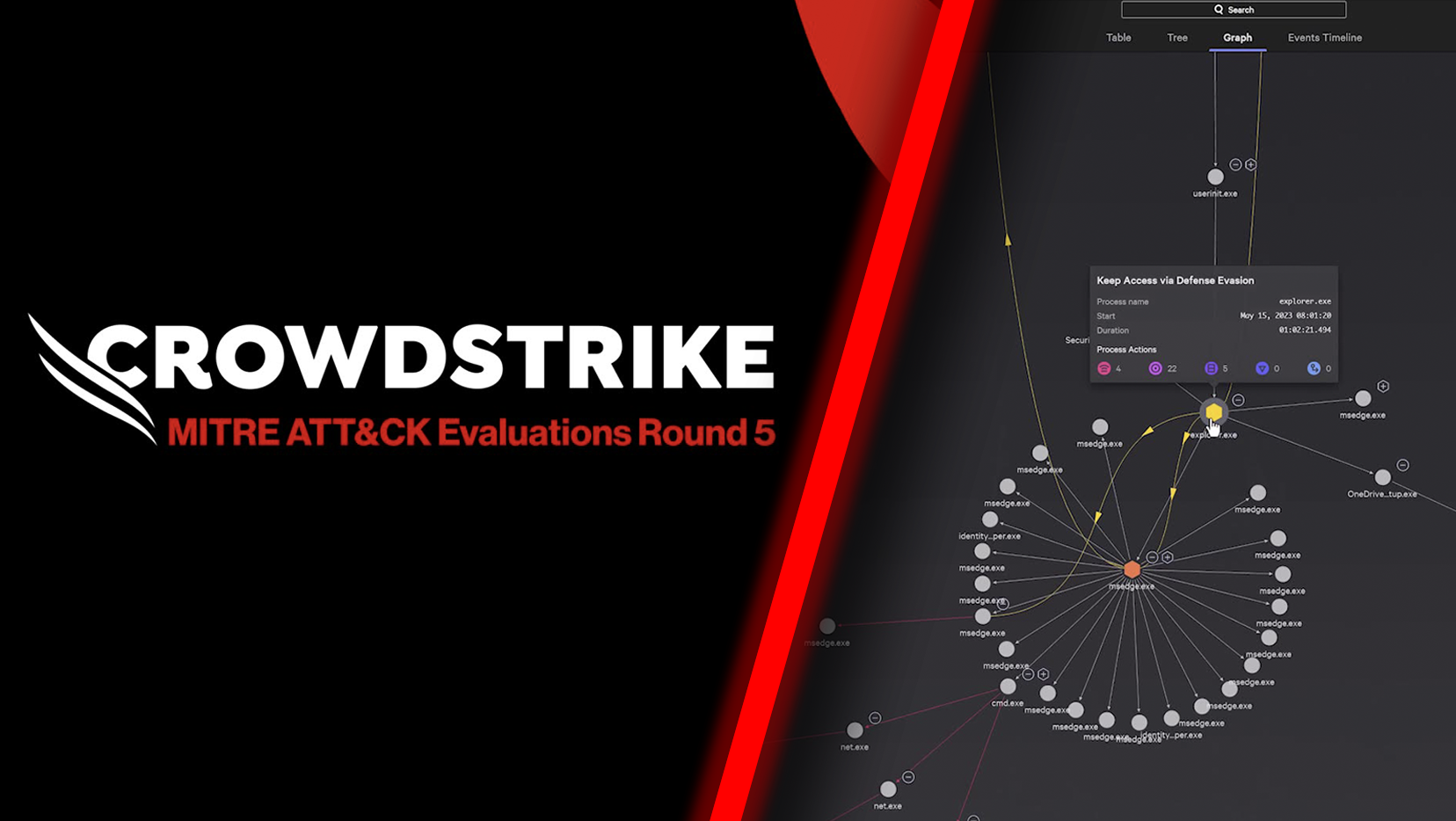
CrowdCast
MITRE Engenuity ATT&CK Evaluations: Inside the Enterprise Round 5 Results
Listen to CrowdCast


CrowdCast
Securing Kubernetes Across the Enterprise Without Killing Productivity
Listen to CrowdCast




















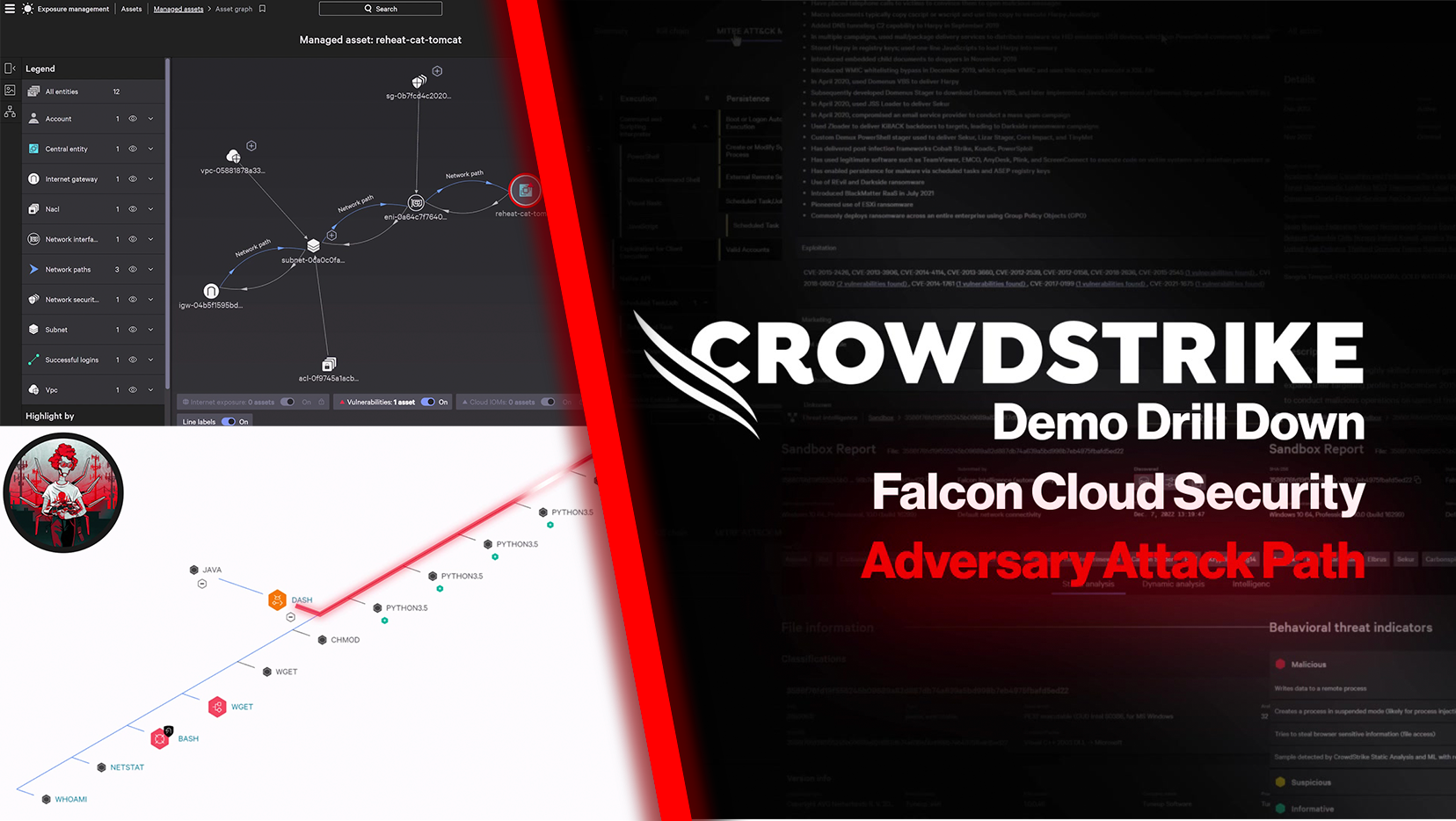




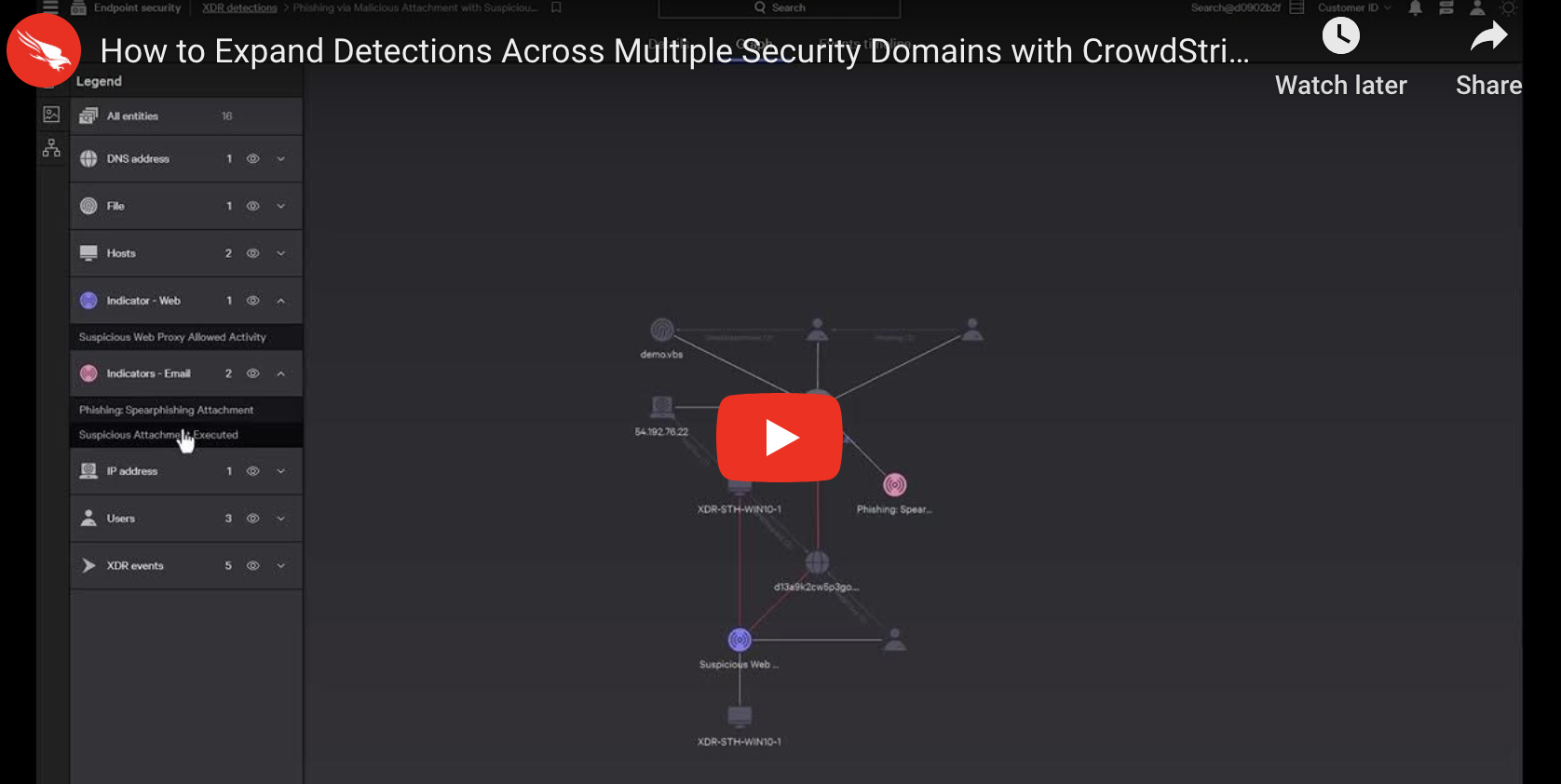

Customer Story
University Health Network: Toronto Hospital Ensures Critical Protection with CrowdStrike
View story







Video
Protegiendo la industria financiera: Identificación de amenazas, soluciones y tendencias…
Watch video













CrowdCast
Playing Defense: Lessons in Protecting Your Business Against Cyber Crime
Listen to CrowdCast










White Paper
Easily Exploited Cloud Misconfigurations and How to Minimize Their Risks
Read white paper















Customer Story
South Australian Utility Expands CrowdStrike Protections to Bolster Defence and…
View story





































CrowdCast
2023 Global Threat Report Session 1: Understanding the Threat Landscape
Listen to CrowdCast







Data Sheet
CrowdStrike and Abnormal Security Integration Discovers and Remediates Compromised Email…
View data sheet
Customer Story
From Endpoint to Cloud, CoreWeave Consolidates Security Stack With CrowdStrike
View story




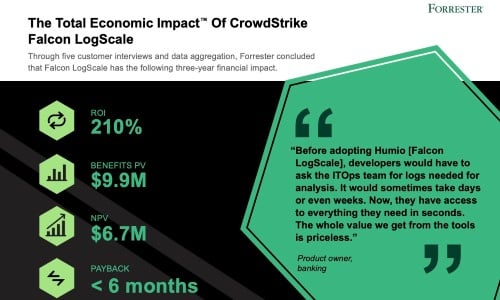


Customer Story
U.K. University Gains 24/7 Protection, Visibility and Response with CrowdStrike…
View story



White Paper
Analysis: Breaking Down the 2022 MITRE Engenuity ATT&CK Evaluations for…
Read white paper








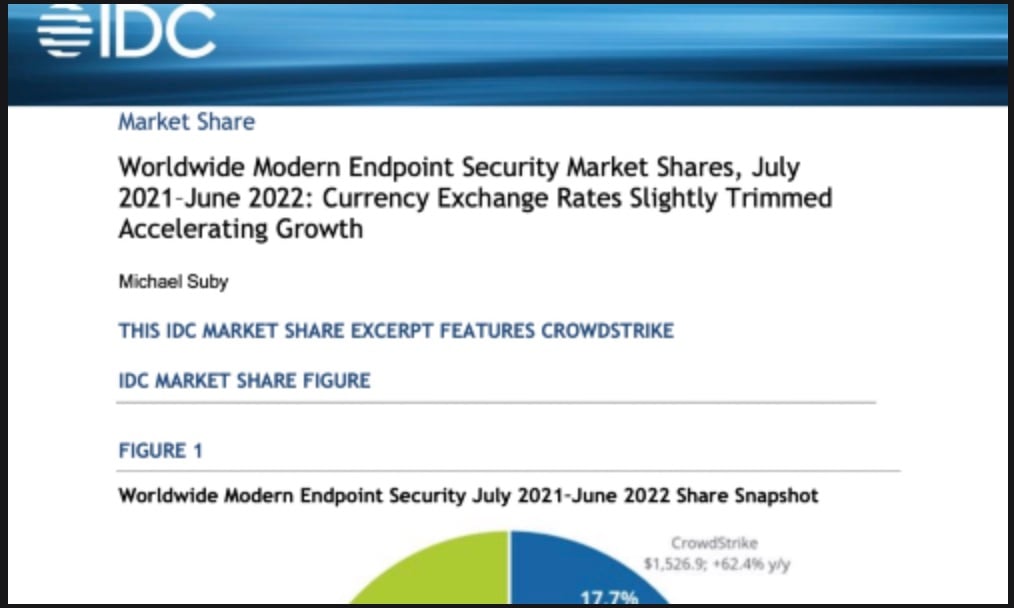

Data Sheet
Protecting your cloud workloads with defense-in-depth security from CrowdStrike and…
View data sheet






White Paper
Guía de supervivencia sobre ciberseguridad para pequeñas y medianas empresas
Read white paper
White Paper
Guida di sopravvivenza per la sicurezza informatica delle piccole imprese
Read white paper
Customer Story
International High-Tech Company Protects IT Infrastructure with Cloud-Native CrowdStrike Security
View story






Customer Story
Netlify Achieves Real-Time Observability at Scale with CrowdStrike Falcon LogScale
View story

CrowdCast
Best Practices for Protecting the Hybrid Workforce with a Comprehensive…
Listen to CrowdCast










CrowdCast
Stop Modern Active Directory Threats with CrowdStrike, Okta, Zscaler and…
Listen to CrowdCast


Customer Story
Berkshire Bank Accelerates Digital Transformation and Multi-Channel Customer Services with…
View story

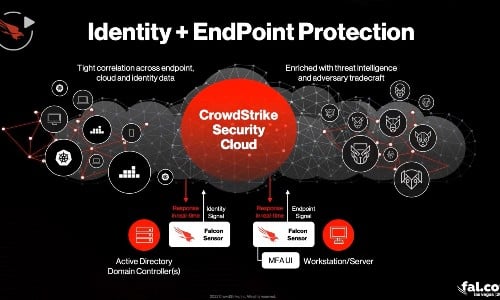



Customer Story
Australian Utility Provider, Jemena, Chooses CrowdStrike Falcon Complete to Transform…
View story
Customer Story
Leading Brazilian Automotive Business Saves Time and Increases Efficiency by…
View story














Customer Story
Pella Augments In-House Security Team with CrowdStrike Managed Services and…
View story
Report
2022 Frost Radar™ Leader: Crowdstrike’s Cloud-native Application Protection Platform (CNAPP)
View report

Customer Story
Europe Energy Protects Customer Data and Multimillion Euro Trading Transactions…
View story
Customer Story
Brazilian Fashion and Retail Business Protects 30 Million Customers' Financial…
View story
Customer Story
CrowdStrike Falcon LogScale at Remitly: Fintech Startup Transforms Raw Log…
View story





Infographic
Infografica Nessun posto dove nascondersi Report sul threat hunting di…
View infographic


















Infographic
Nowhere to Hide 2022 Falcon OverWatch Threat Hunting Report Infographic
View infographic
CrowdCast
CrowdCast: Nowhere to Hide: 2022 Falcon OverWatch Threat Hunting Report
Listen to CrowdCast
Guide
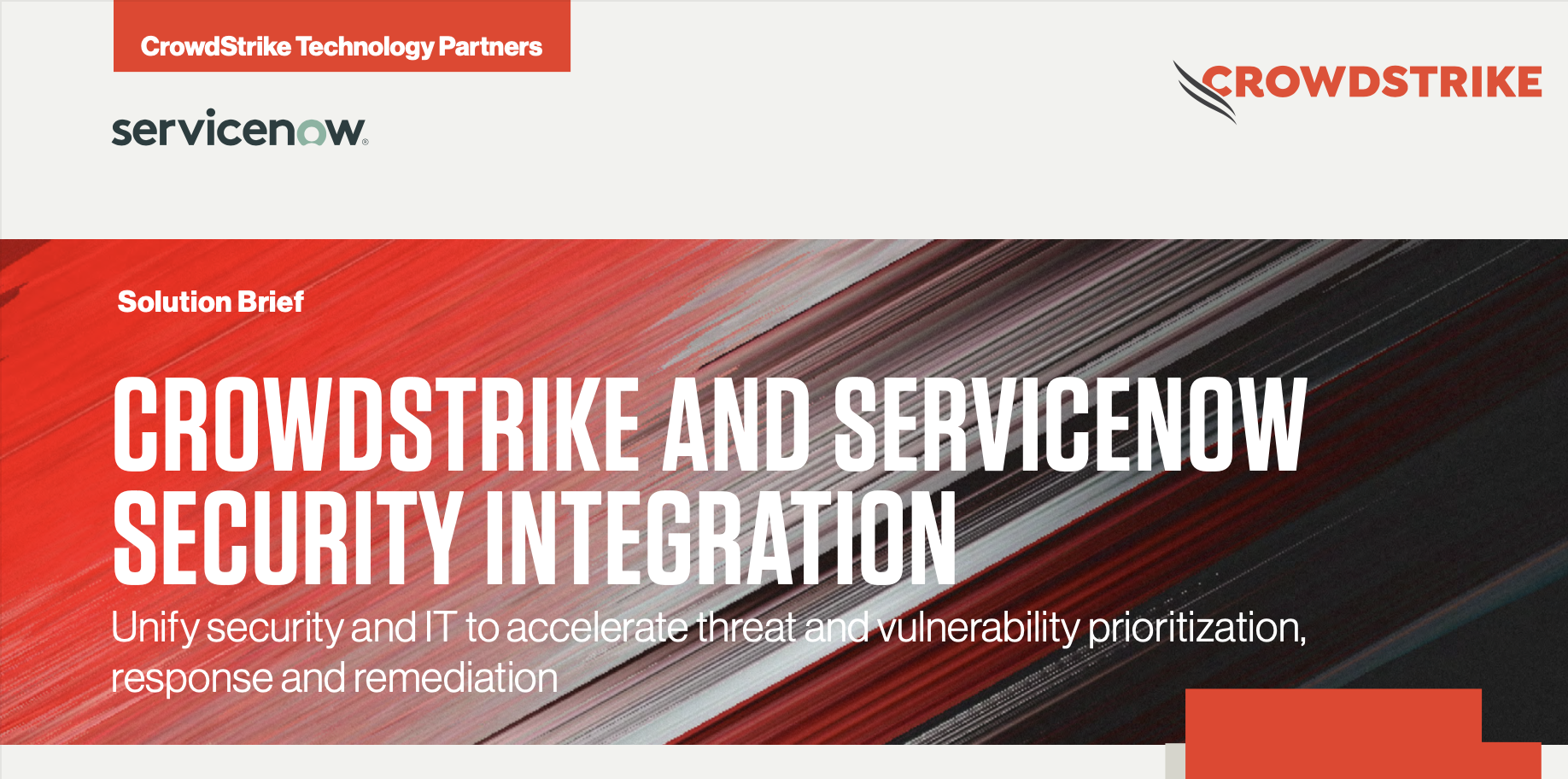
IT Practitioner Guide: Defending Against Ransomware with CrowdStrike and ServiceNow
View guide






























White Paper
Five Questions to Ask Before Choosing SentinelOne for Workforce Identity…
Read white paper














Customer Story
Global Data Analytics Company Builds Brand Reputation and “Bulletproof” Security…
View story
Customer Story
Healthcare Solutions Provider Rolls Out CrowdStrike Falcon to Secure Extensive…
View story


Customer Story
CrowdStrike Helps Engineering Consultancy Transform Protection and Reduce Time and…
View story




CrowdCast
Defeat the Adversary: Combat Advanced Supply Chain, Cloud and Identity-Based…
Listen to CrowdCast




White Paper
Falcon OverWatch Proactive Threat Hunting Unearths IceApple Post-Exploitation Framework
Read white paper











White Paper
Ransomware Preparedness: Insights from IT and Cybersecurity Professionals
Read white paper
Infographic
CrowdStrike and AWS: A defense-in-depth approach to protecting cloud workloads
View infographic








Customer Story
CrowdStrike Helps Leading Digital Recruitment Business Protect Personal Content for…
View story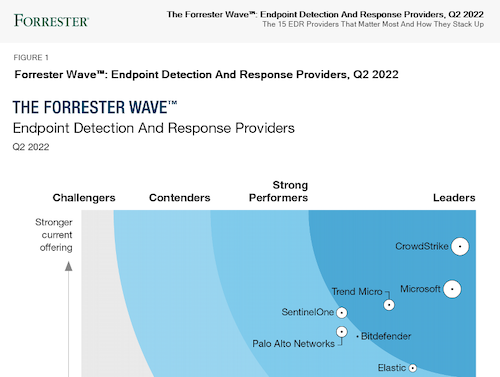







Infographic
Seis Puntos Fundamentales Para Proteger Aplicaciones Nativas De La Nube…
View infographic








White Paper
Cinco capacidades fundamentales para protegerse del riesgo de los endpoints
Read white paper












White Paper
Accelerate Your Cyber Insurance Initiatives with Falcon Identity Protection
Read white paper


Customer Story
Australian Utility Provider Partners With CrowdStrike to Transform Cybersecurity Defense…
View story






CrowdCast
Shared Responsibility Best Practices for Securing Public Cloud Platforms with…
Listen to CrowdCast

Customer Story
Banco Latinoamericano de Comercio Exterior, S.A. Finances LATAM Trade While…
View story











Customer Story
Innovative HR Solutions Provider BIPO Strengthens Security Posture and Bolsters…
View story

White Paper
Cosa è necessario sapere per selezionare una piattaforma di protezione…
Read white paper


Customer Story
Mercedes-AMG PETRONAS Formula One Team Accelerates Security Program with CrowdStrike
View story










Customer Story
Cushman & Wakefield Extends Visibility Into Globally Distributed Endpoints
View story

Customer Story
CrowdStrike Helps Inductive Automation Ensure Business Continuity for Critical Industry…
View story


Customer Story
CrowdStrike Enables Bionexo to Deliver Essential Medical Supplies to Thousands…
View story





Customer Story
Coventry University Achieves First-Class Results with Enhanced Endpoint Security Strategy
View story



Customer Story
Navitas Centralizes Cybersecurity to Protect the Data of Students, Staff,…
View story





Customer Story
European Construction Supplier Repels Ransomware, Rebuilds Security Defenses
View story
CrowdCast
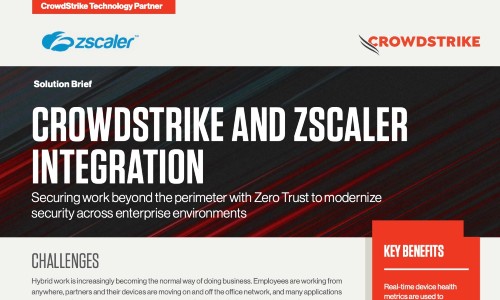
Accelerating the Journey Towards Zero Trust with CrowdStrike and Zscaler
Listen to CrowdCast
CrowdCast
How Effective Are Your Cybersecurity Solutions Against Today’s Threats?
Listen to CrowdCast








Customer Story
BOB Financial Digitally Transformed Security to Support Growth Leveraging Cloud…
View story









Customer Story
CTOS Protects Customer Data, Meets Strict Compliance and Expands Globally…
View story










Customer Story
Greenhill Advises Global Finance Clients While Protecting Data With Leading…
View story











White Paper
CrowdStrike 2022 Falcon Cloud Security, Cloud Workload Protection Buyers Guide
Read white paper
Customer Story
Leading Eurasian Raw Materials, Building Materials and Ceramic Tile Producer…
View story








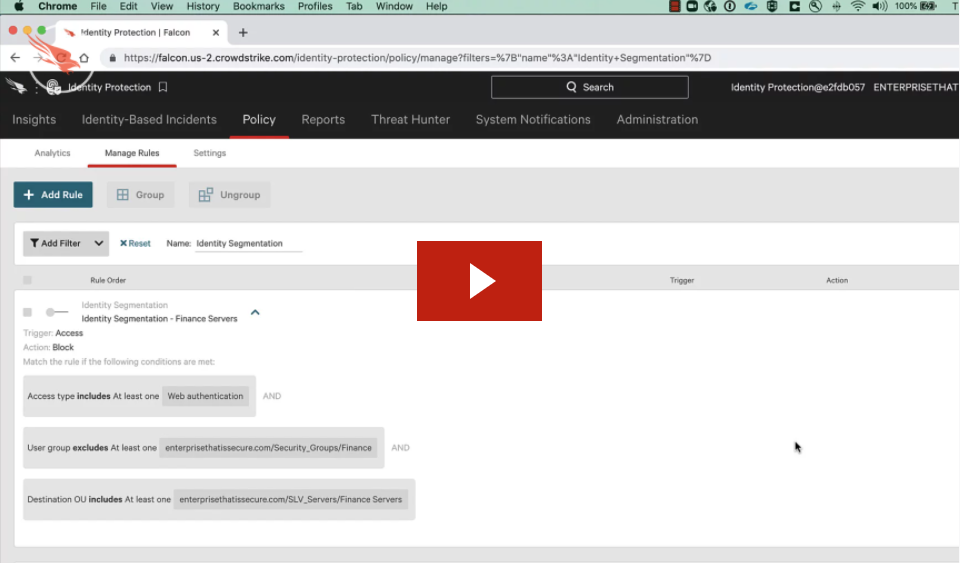






White Paper
Reducing the Attack Surface: Network Segmentation vs. Identity Segmentation
Read white paper












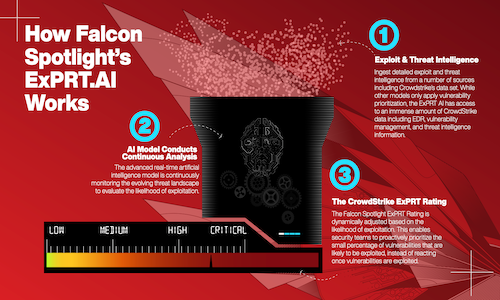
















































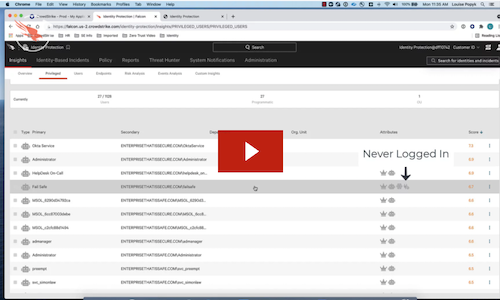
White Paper
ESG Technical Validation: Reduce Risk with CrowdStrike Falcon® Identity Protection
Read white paper














Infographic
Panoramica sulla Guida all'acquisto di una soluzione di protezione degli…
View infographic













































White Paper
Falcon Complete: Detección Y Respuesta Gestionada, Profesional Y Comprobada
Read white paper









CrowdCast
The Maturation of Cloud-native Security: Securing Modern Apps and Infrastructure
Listen to CrowdCast
















































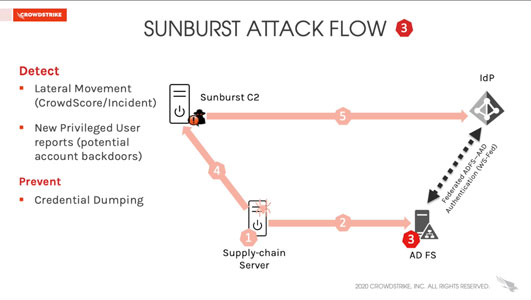

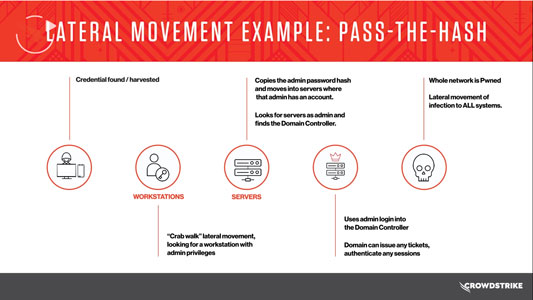











CrowdCast
Extending Security Controls to OT Networks with Claroty and CrowdStrike
Listen to CrowdCast
CrowdCast
Obsidian + CrowdStrike: Detection and Response Across Cloud and Endpoints
Listen to CrowdCast
















































White Paper
GUÍA PARA COMPRADORES DE SERVICIOS GESTIONADOS DE DETECCIÓN Y RESPUESTA…
Read white paper






White Paper
Falcon Complete: Detección y Respuesta Gestionada, Demostrada y Profesional
Read white paper



















CrowdCast
Reconciling Cybersecurity Risks With Industrial Digital Transformation
Listen to CrowdCast





















Report
CrowdStrike Intelligence Report: A Technical Analysis of the NetWalker Ransomware
View report






White Paper
L'evoluzione del ransomware: come proteggere le aziende dai nuovi trend…
Read white paper













CrowdCast
Beyond COVID-19: Protecting People and Preventing Breaches in the “New…
Listen to CrowdCast































CrowdCast
Every Second Counts: Speed & Cybersecurity with Mercedes-AMG Petronas F1…
Listen to CrowdCast









































CrowdCast
The 1/10/60 Minute Challenge: A Framework for Stopping Breaches Faster
Listen to CrowdCast




















































For technical information on installation, policy configuration and more, please visit the CrowdStrike Tech Center.
Visit the Tech Hub