How Falcon Protects Off-line Hosts From New Threats
In this demo, we’ll show the value added by having machine learning on the localhost. I’ve downloaded a sample from VirusTotal, and run it from the command prompt in my test environment.
A block of the malware is identified by the ‘access is denied’ message. Now, if we look at this event and Falcon Host, we can see the familiar process tree, and that the sample was initiated from cmd.exe and then, underneath that, a reason for the block. On the right hand side, we can get additional information about this event, including information from VirusTotal. Here we see the sample has been identified as malicious by 36 other VT vendors.
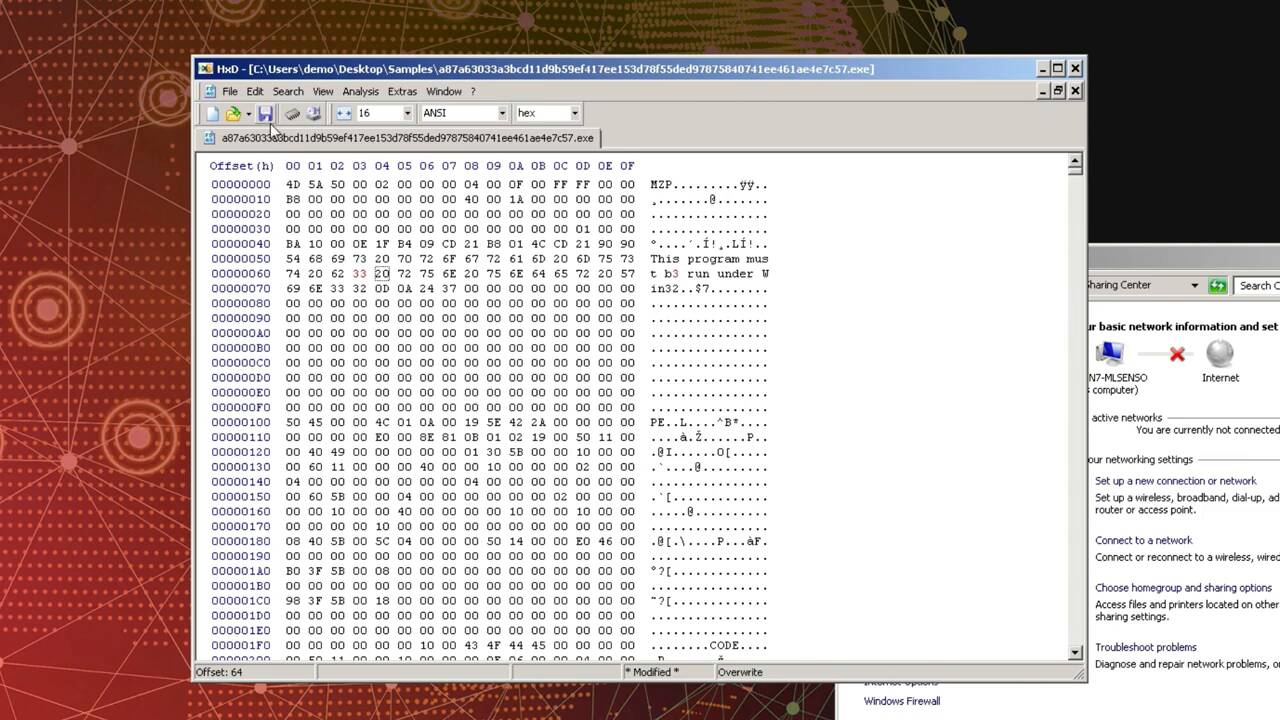
Now, let’s run that sample again only this time we’ll illustrate the benefit of having ml on sensor by disconnecting our host from the internet. And then, just so we know the sensors aren’t relying on a hash lookout for reputation, we’ll use a hex editor to slightly modify the files as to change the hash but not the behavior. To change the process tree I’ll also run the file two different ways: the first by double-clicking it, and then the second from the command prompt similar to the first time. Notice on the double-click I receive a permission error, and then on the command prompt another ‘access is denied’ message.
Now, I’m going to enable my network adapter and wait a few seconds so events can be reported from the test environment back to Falcon Host. Back in Falcon Host, we can see a new alert. Deeper inspection shows us both the attempts- one from the explorer.exe process and the other from command.exe process. We can also see that the altered file doesn’t match any other submissions in the VirusTotal on the right hand side here, where previously we saw 36 detections.
With Falcon ML sensor, customers can now benefit from world-class protection, even when offline.