How to Block Zero Day and Fileless Exploits with CrowdStrike Falcon®
In this demo, we’ll use an example for Metasploit and a common spear-phishing attempt. Once the exploit has been started on the attacker server, we’ll set our bait in an email that appears to be from someone we trust. In this case, it would appear our Gmail account has been hacked and our password needs to be reset.
As is the case with many of the account reset e-mails, this one isn’t legit. And clicking any link in the email opens a communication channel back to the attacker’s shell and migrates the suspicious process into Notepad, an application that is almost always trusted and seldom noticed. From the victim’s perspective, it just looks like another IE crash.
At this point, the attacker thinks he gone unnoticed and begins the task of reconnaissance through common tasks such as whoami, IP config, and netstat. He’ll also use a built-in Metasploit tool for privilege escalation. Once the Get System command is run, the attacker is now NT authority system. And with those privileges, steals credentials to begin the next step of his attack, which is lateral movement and persistence.
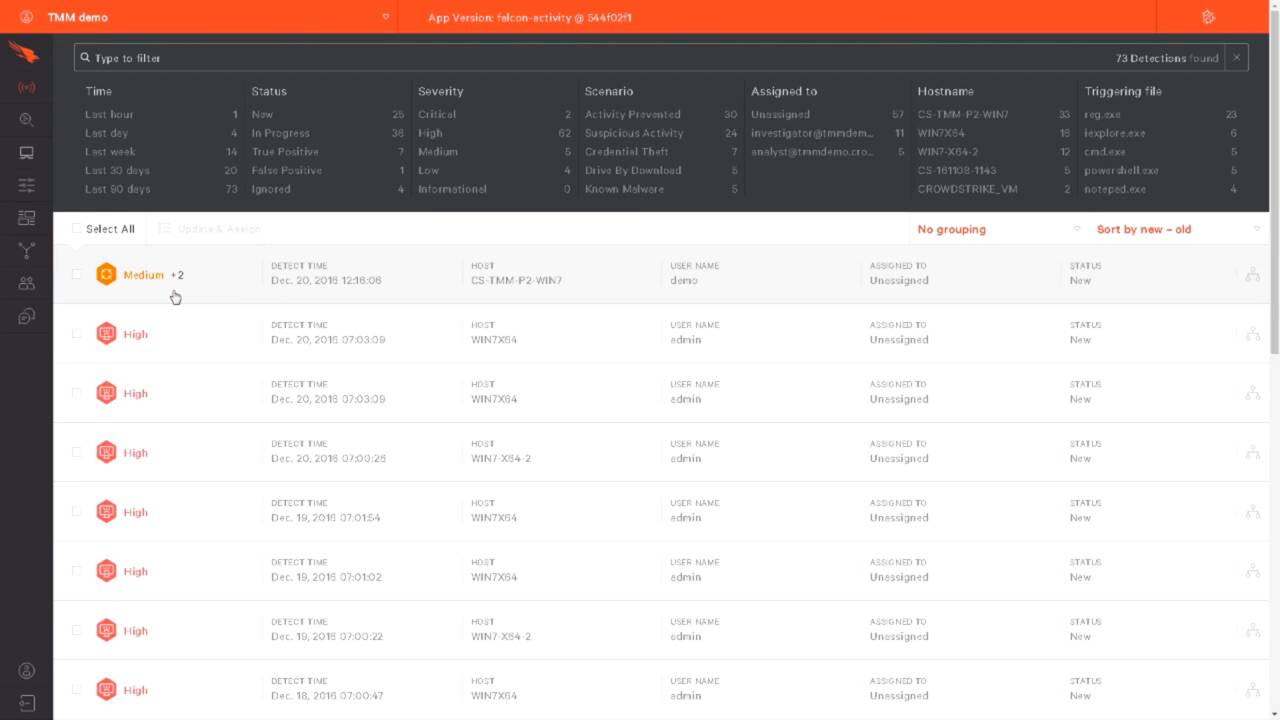
Since this is a kernel level sensor, it captures all of the events and sends them to the cloud. There, they are analyzed in the CrowdStrike threat graph. Because the data is stored in the cloud, it can be analyzed later, even when the compromise system is offline. In the Falcon UI, these events will appear in the activity app as a new and unassigned event.
Clicking on the alert expands the details of the event in a process tree. And then, on the right hand side, additional details about the event are given. You can open an interactive, visual representation of the event by clicking the full detection details icon. It’s here in the upper right hand corner.
In the future, if we’d like to just prevent these types of attacks, that can be done from the configuration app. And then on the Settings tab, navigate to the Exploit Mitigation section and enable Prevention. Then save any changes that you made.
Now when we go back and try to run the attack again, we can go to the email. Click any of the links. Then from the attacker system, we can see that there are no longer any active sessions. And in the Falcon UI, we see a new alert and this time we see a block associated with this attack.