How to Ingest IOCs and Integrate with SIEM Solutions with CrowdStrike Falcon®
In this demo, we’ll see how Falcon can automatically ingest IOCs via the Falcon API. We will also see any hits against this IOC being fed into a SIEM.
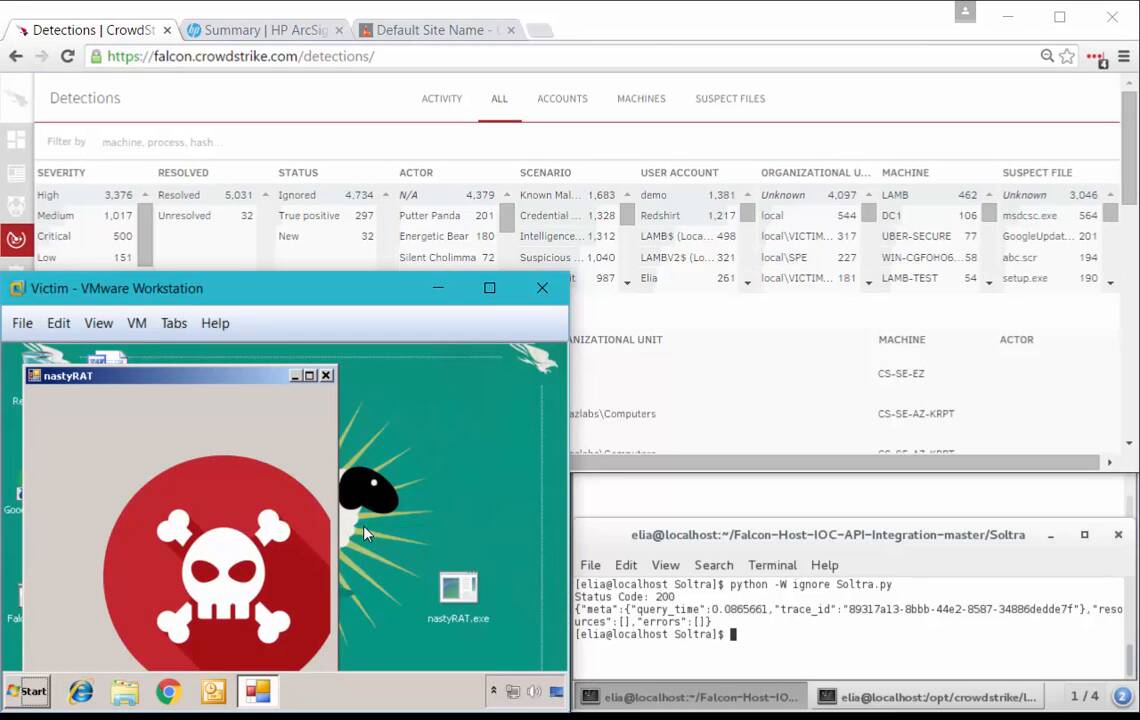
First, let’s start by creating an IOC. We do this by discovering a new piece of malware. In this case, we’ll call it Nasty Rat. If we generate an MD5 hash for this file, we now have an indicator that we can use to make our IOC. To do this, we switch over to Soltra.
Here we can start by choosing to create an indicator. Then we can give it a name and populate all the details that we have about the Nasty Rat malware. Once we publish the IOC, it is now ready to be sent to Falcon. This is done via our API.
So here we see a very simple Python script that consumes the IOC and sends it to Falcon. To prove that the IOC is now in Falcon, we will execute the Nasty Rat virus on our test system. You can see it run. And now, we switch to the Falcon management console to verify that this was detected.
You can see a new detection with the scenario “Intel.” This indicates that the event was caused by the IOC that we imported. Now that we have this event in Falcon, the next step is to publish this into a SIEM. In this case, we are using HP ArcSight. Again, we use the API to send the event from Falcon to the SIEM.
You can see that the script successfully ran. So now let’s verify in the ArcSight UI that the event has been logged. And here you can see the Nasty Rat event in the SIEM. And with that, you’ve seen the full life cycle of a custom detection. We started with a new piece of intelligence, turned it into an IOC, saw Falcon detection against that IOC, and then sent the event to the SIEM.