How to Perform a Simple File Search with the CrowdStrike Falcon® Host Investigate App
Thank you for joining us today. Today we’re going to show you how Falcon Host can search on any hash file across your organization within seconds.
I’ve already logged in to my user interface. I’m going to jump from my Detections area to my Investigate area. The Investigate area allows you to easily search for computer, IP address, hash, or user, historically across your entire organization.
I’m going to choose Hash, and paste an MD5 hash that I may have received from one of my peers, or a threat intelligence service that I may be subscribed to. I want to see if it has been executed across my organization in the last seven days. I could alternatively enter a file name that goes along with that hash, or a command line or a specific computer name or a username.
I’m going to go ahead and hit Submit. The second I do, we are only searching in the Cloud. We are not going out to your endpoints in real time and asking them if they have that hash on them right now.
The importance of this is the fact that the machine may have been reimaged, destroyed, or stolen. If the machine is no longer able to come online, you must be able to search historically. And in our case, we search in the Cloud, where all your data is located.
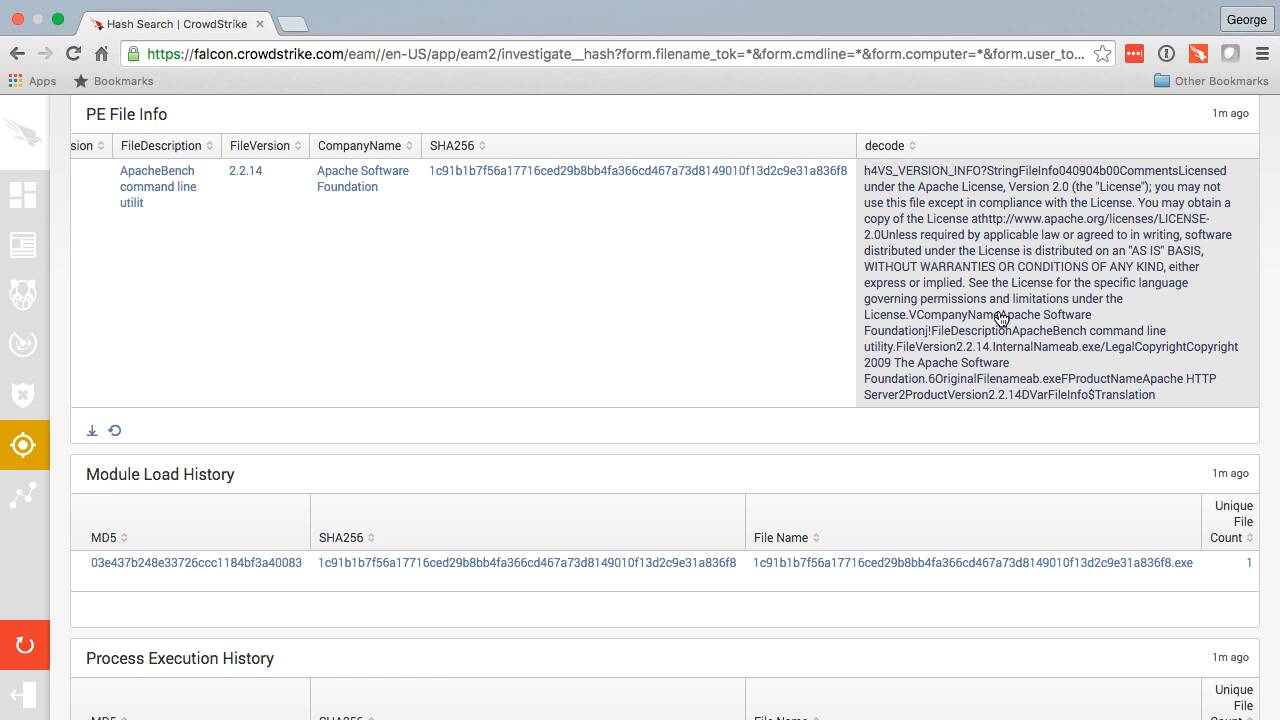
As we can see here, here is the file result. This is the name of the actual file, any certificates or file descriptions associated with that file, and the SHA250 hash that matches up with the hash that I searched for. We can also see the decoding of the actual file information, or the metadata about that file.
Here is the history of where that file ran. There’s only one file with that exact cache, and this is it right here. It only ran on one single computer loaded right here. And that’s the name of the computer. This is the first time it ran– and it also last ran on the same exact computer– and the last time it ran.
We also see the process execution history– again, number of computers, unique file count, and number of process executions. The first time it executed and the first date it executed.
We can also see that it did have detections from Falcon Host associated with that file. In this case, these detections would show up in our detection screen. And the reason why it showed up in the first place, there were 40 AV engines that felt that this file was malware.
If I scroll to the right, I can see the process ID and the exact command line that was used to launch that file, which would give me a lot more info. Here is the timeline of the process execution. Had this file been spreading across my organization, I would have seen several more blue bars– which indicate further executions of the file– across additional machines if any had executed that file. So, now we know that the execution was isolated to one single machine on one single day.
Again, here is more additional anti-virus information– all the different engines and all the different malware names that this was detected as.
Again, the importance of searching historically across your organization for file executions is imperative to a good incident response strategy.