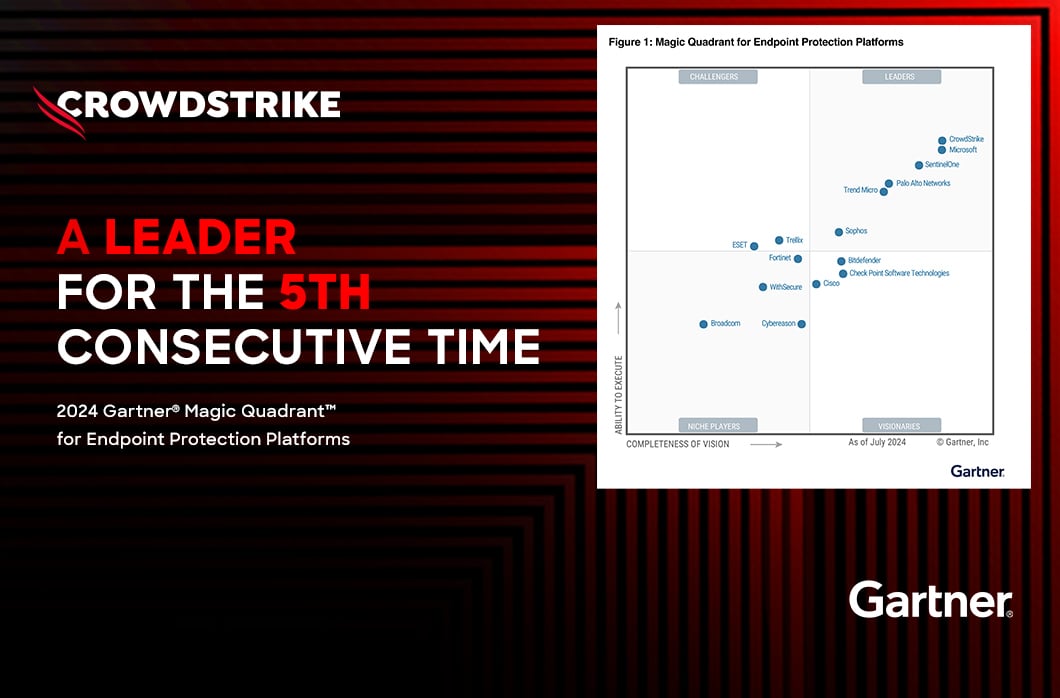
Endpoint Security – Automated Remediation

Introduction
Attacks today are sophisticated with many moving parts that can leave a wake of debris even if they are detected and stopped.
When CrowdStrike detects an attack, it’ll safely remove supporting artifacts once malicious behavior is identified through an Indicator of Attack.
Let’s take a look at how CrowdStrike’s Automated Remediation works.
Walkthrough
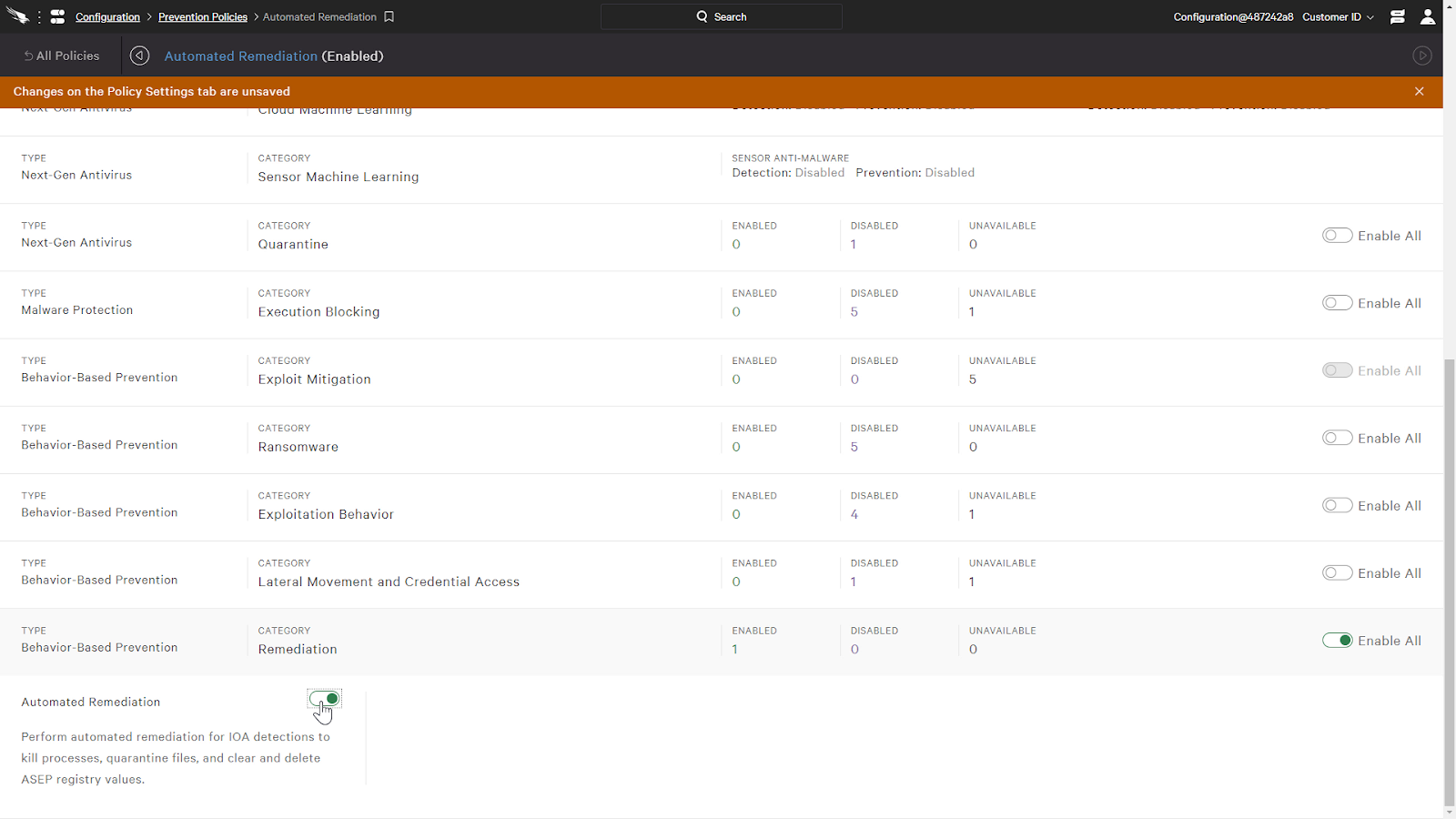
First, we’ll enable it with a policy. Under the prevention policy, we just need to toggle the Automated Remediation option. It’s as simple as that and works automatically from here on out.
Now that we have it enabled, let’s see it in action on a host.
When we execute a malicious script, CrowdStrike will analyze its behaviors. As the script is executing, we can see it drop additional files in its directory. These new artifacts have never been seen before and are only connected with the process by the fact that they were created by it.
Now we can see that CrowdStrike has convicted the process based on its behaviors and it’ll begin to remediate the system by removing files dropped by the process as we see here.
It’ll also automatically kill associated processes and reverse registry modifications.
This all happens automatically and saves the time an analyst would need to manually remove these artifacts.
When we look at the detection in the Falcon console, we can see an indicator signifying that a remediation was performed. When we click on it, it’ll bring us to a timeline that shows us all the remediation actions that it had performed.
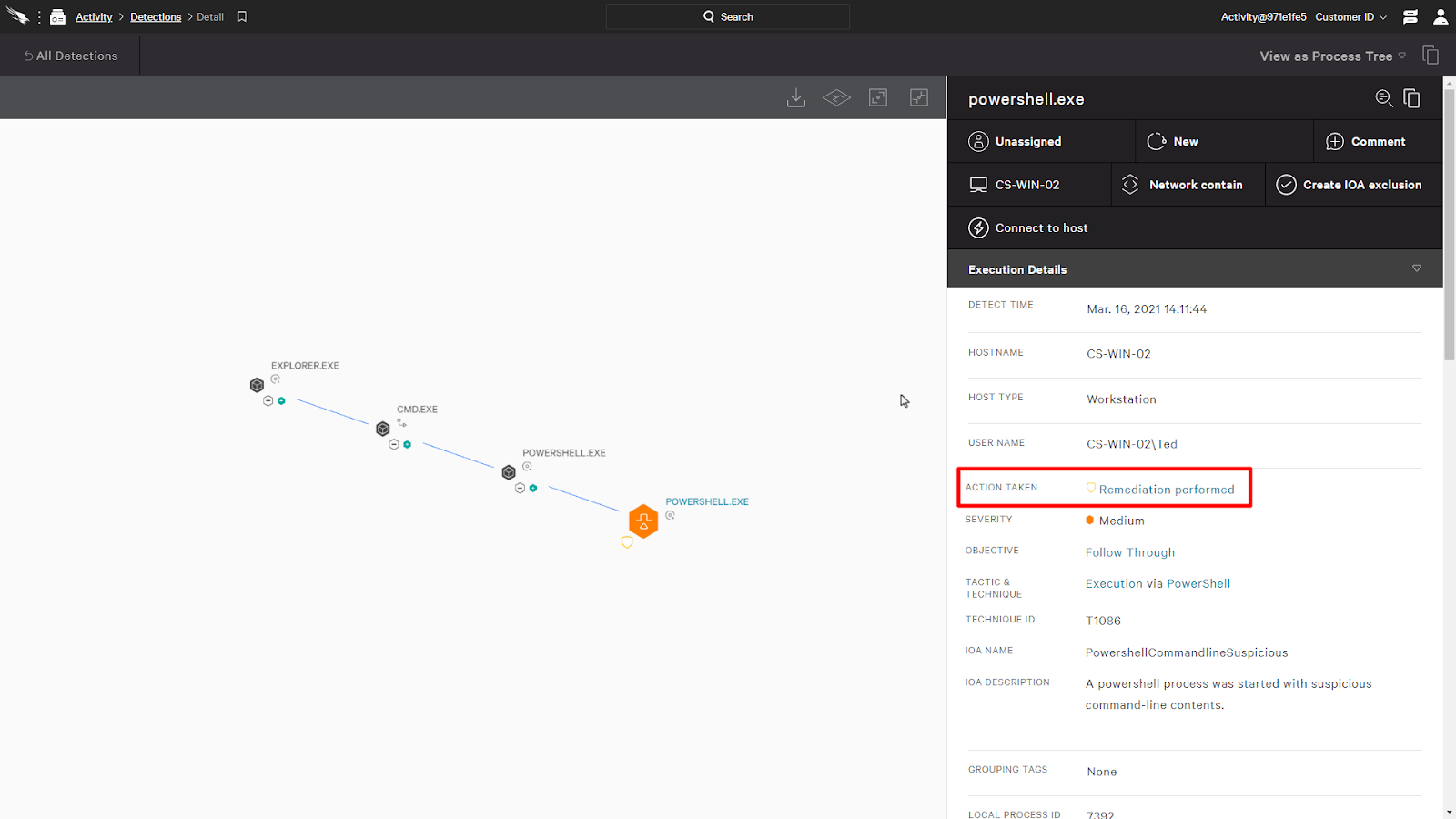
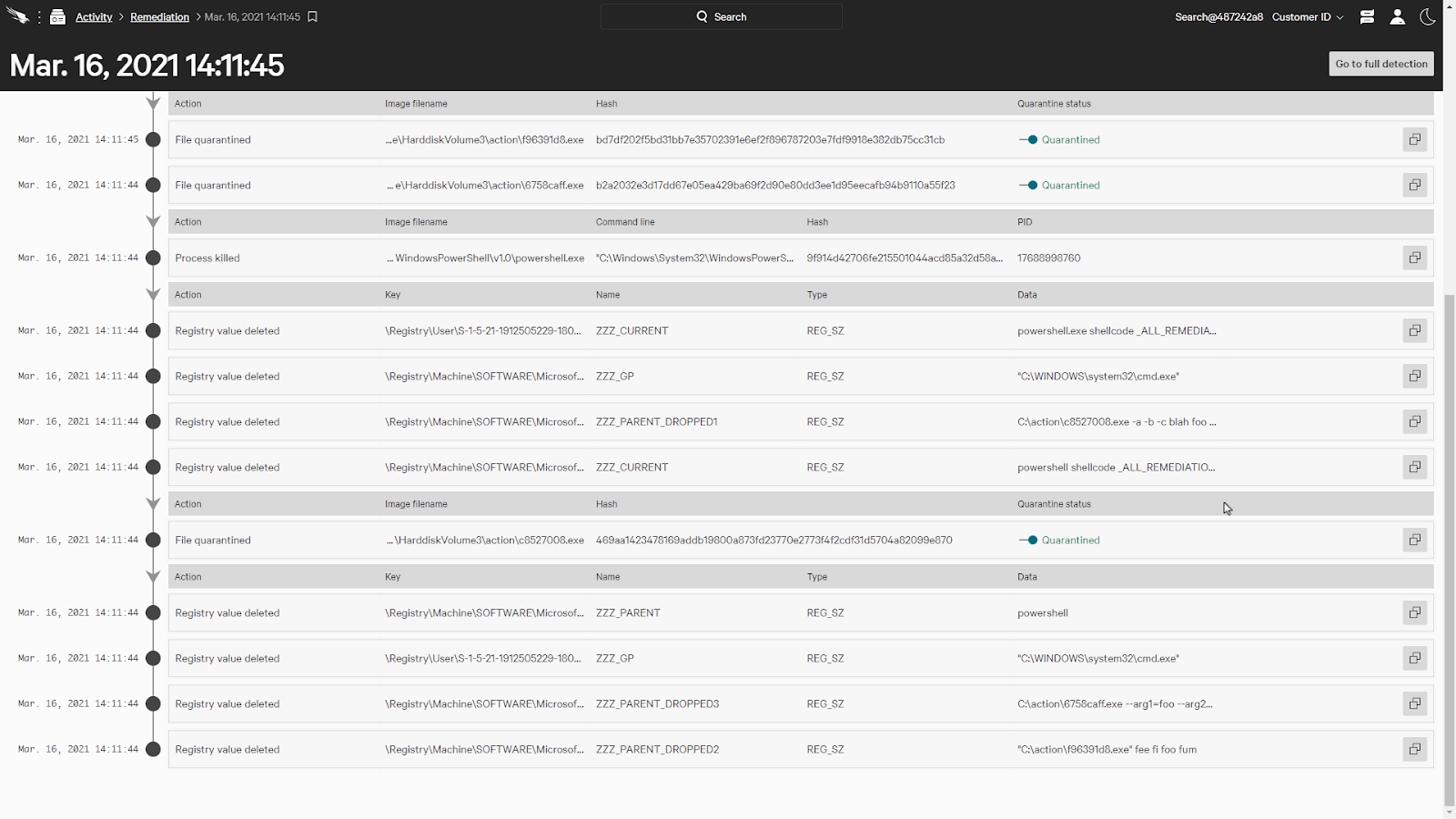
Here, we can see the details of the remediation actions, such as any files quarantined, processes killed, and registry values deleted. We can also release any quarantined files as well.
When we navigate to remediation, a list of all the remediation activities across the entire organization is available. This would better help understand what hosts are being remediated and if there are any additional steps that could be taken to prevent future breaches.
Conclusion
As we have seen, CrowdStrike’s Automated Remediation can save time and help protect the organization by automatically removing artifacts dropped by malicious actors. This simple approach can help reduce risks and allows analysts to focus on higher priority tasks.