CrowdStrike Falcon® Discover
The world’s leading AI-native platform for complete asset visibility
Get deep asset visibility in minutes with zero hardware to deploy or operate.
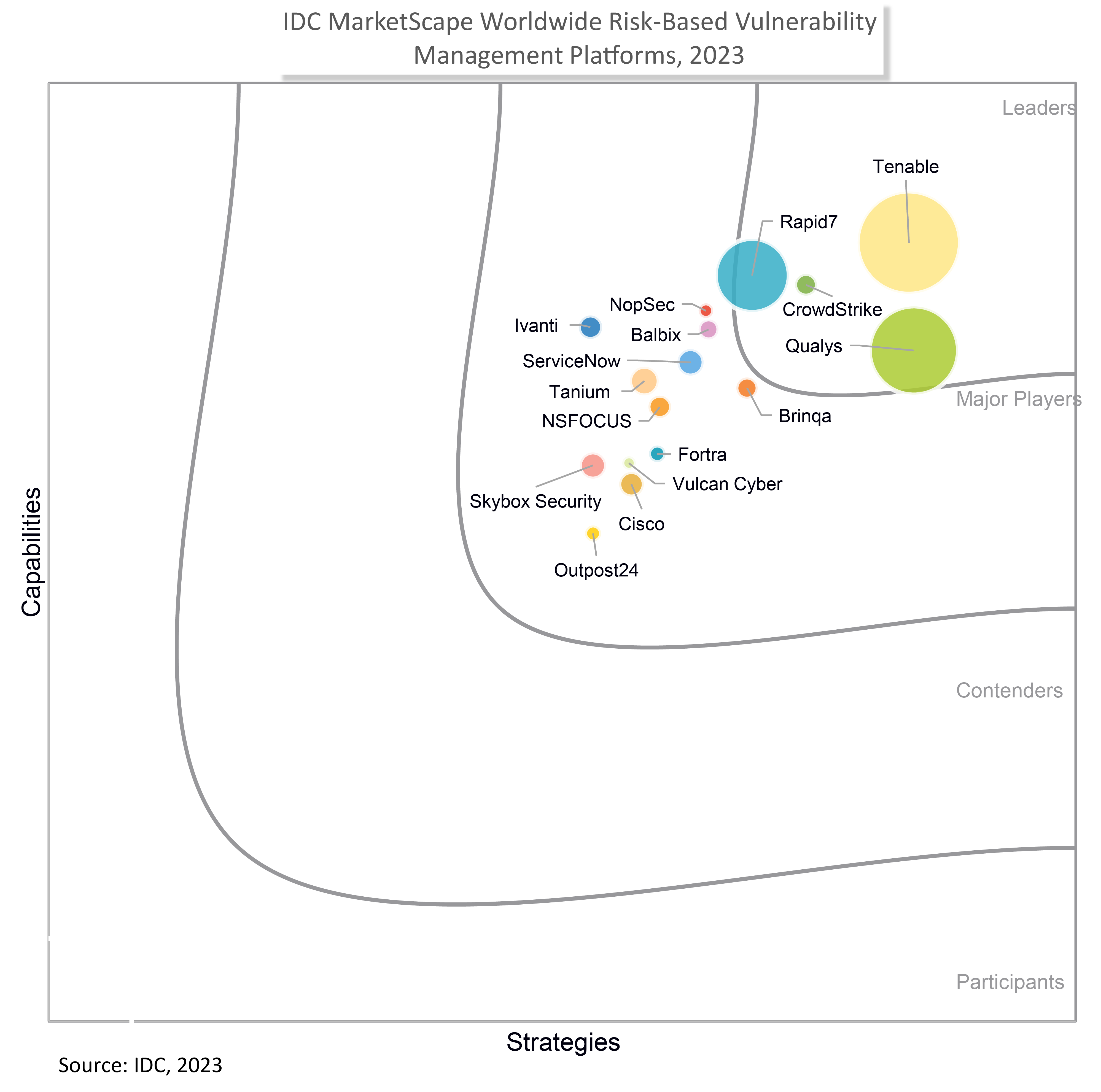
A Leader in Risk-Based Vulnerability Management Platforms
CrowdStrike named a Leader in the 2023 IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment.
You can't secure what you can't see
Lack of context
The chances of a successful breach drastically increases without deep context on the entire attack surface.
Lengthy time-to-value
Hardware-based approaches to visibility demand long deployment cycles and complex management.
Lack of insights
Legacy asset visibility tools lack the robust asset and adversary context required to effectively reduce and manage the attack surface.
Why choose Falcon Discover?
Comprehensive visibility into all assets with robust context to reduce risk, accelerate incident response, and streamline IT operations.
Visibility in minutes, not months
Visibility in minutes, not months
Get complete visibility into all managed and unmanaged assets in minutes without complex hardware deployments that can take months.

Proactively stop breaches
Proactively stop breaches
Stay ahead of adversaries with full relationship mapping and rich vulnerability insights to close security gaps before a breach occurs.

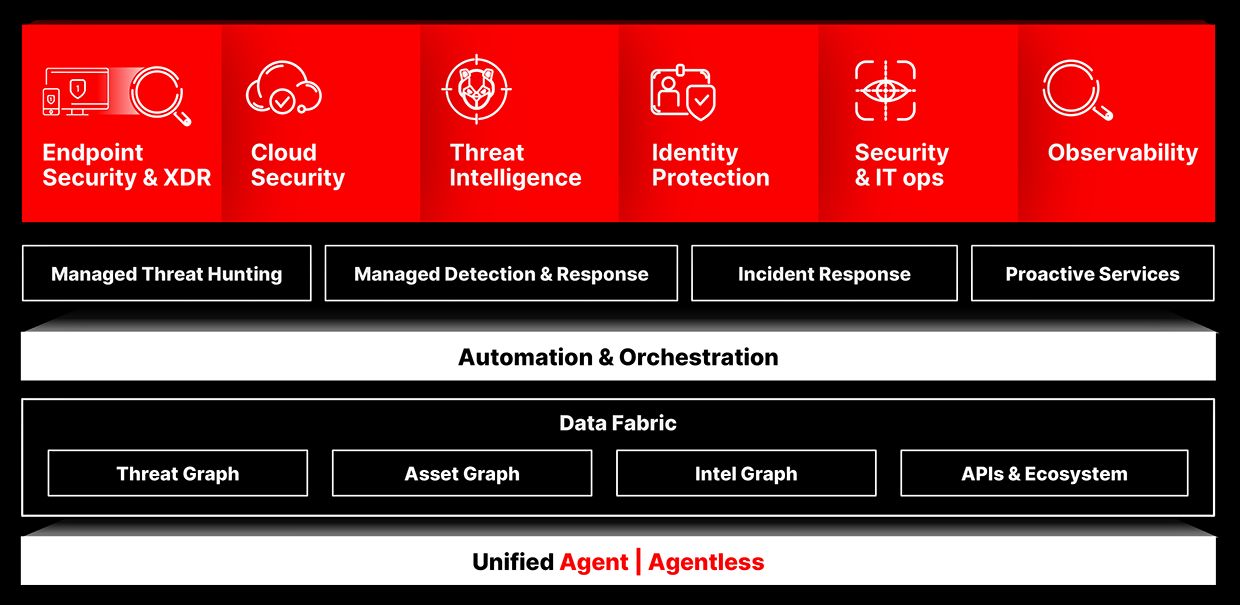
Supercharged by the CrowdStrike Falcon® platform
Supercharged by the CrowdStrike Falcon® platform
Supercharged by the CrowdStrike Falcon® platform
Deep integration with the industry’s leading EDR/XDR platform provides comprehensive visibility and protection to stop breaches.
Falcon Discover key capabilities
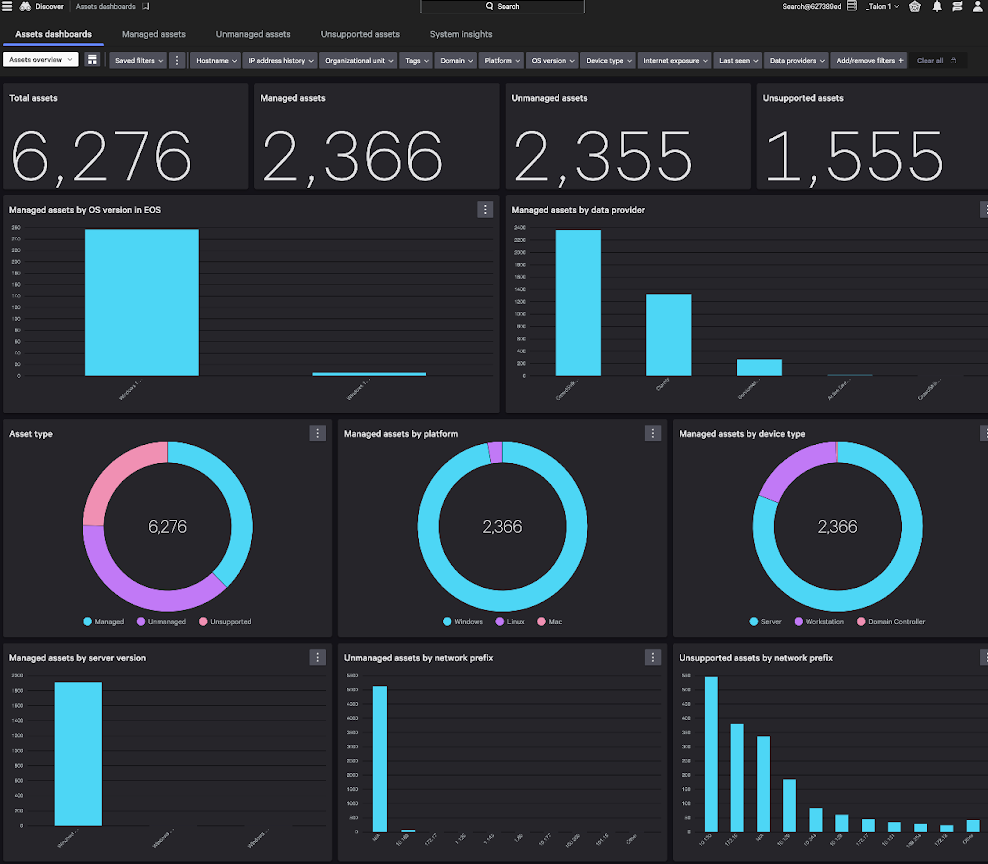
Complete visibility in minutes
- Get a comprehensive view into all assets in minutes without traffic mirroring or network monitoring appliances.
- Rich context into applications, accounts, and systems provides deep understanding of all assets.
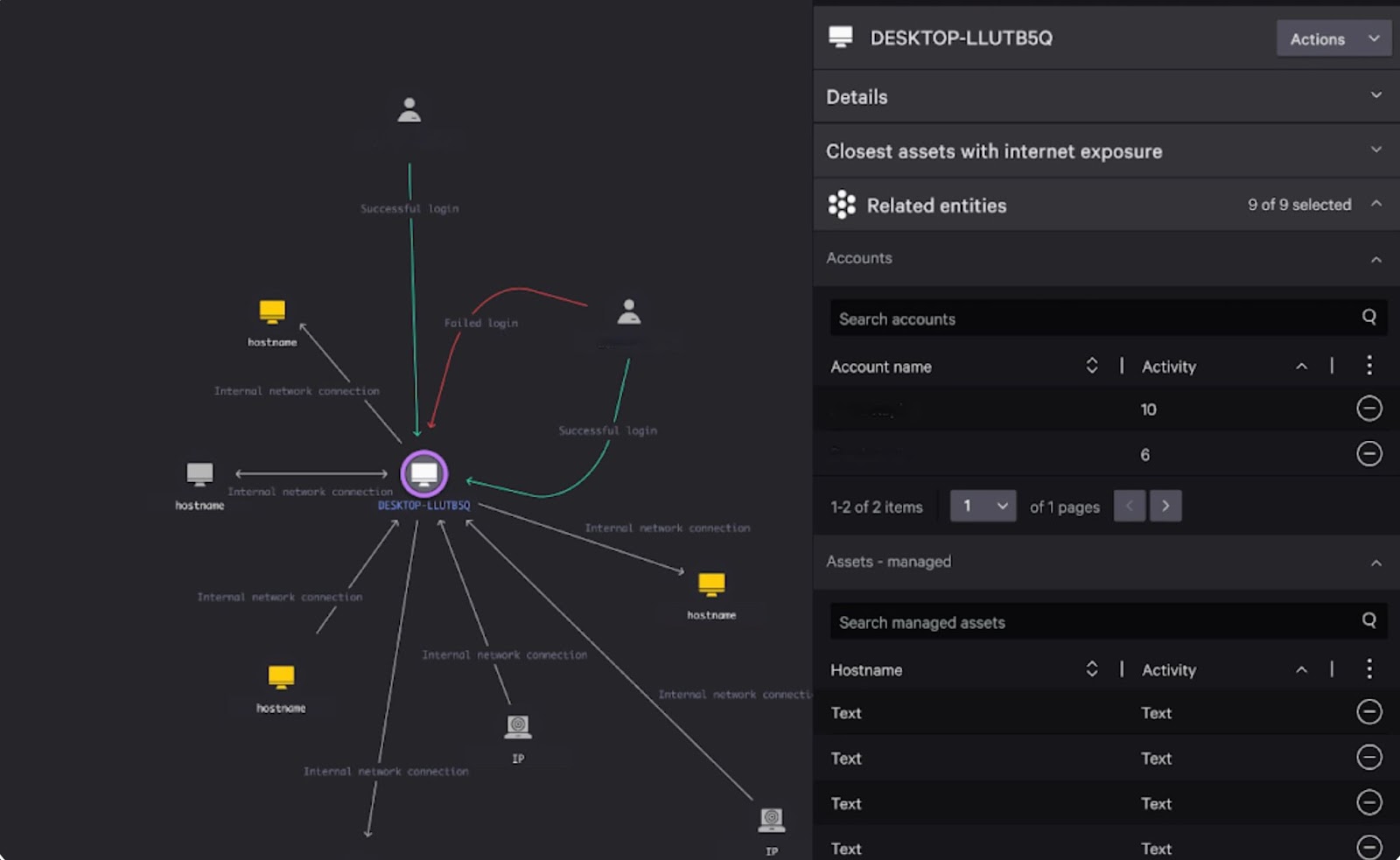
Proactively stop threats with deep context
- Reduce the attack surface with full relationship mapping to identify risky assets, users, and internet connections.
- Speed incident response with robust asset context to hone in on points of compromise and lateral movement.
- Inventory all applications in your organization to further understand the attack surface.
- Proactively prevent breaches by taking action on integrated application vulnerability and threat detection context.
Streamline IT operations
- Close security gaps by finding unmanaged assets that can be protected by the CrowdStrike Falcon® platform.
- Reduce costs with system performance insights to more effectively manage compute resources.
- Manage SaaS license spend by identifying underused applications.
- Supercharge workflows with deep integration across the CrowdStrike Falcon® platform and third-party apps, like ServiceNow.
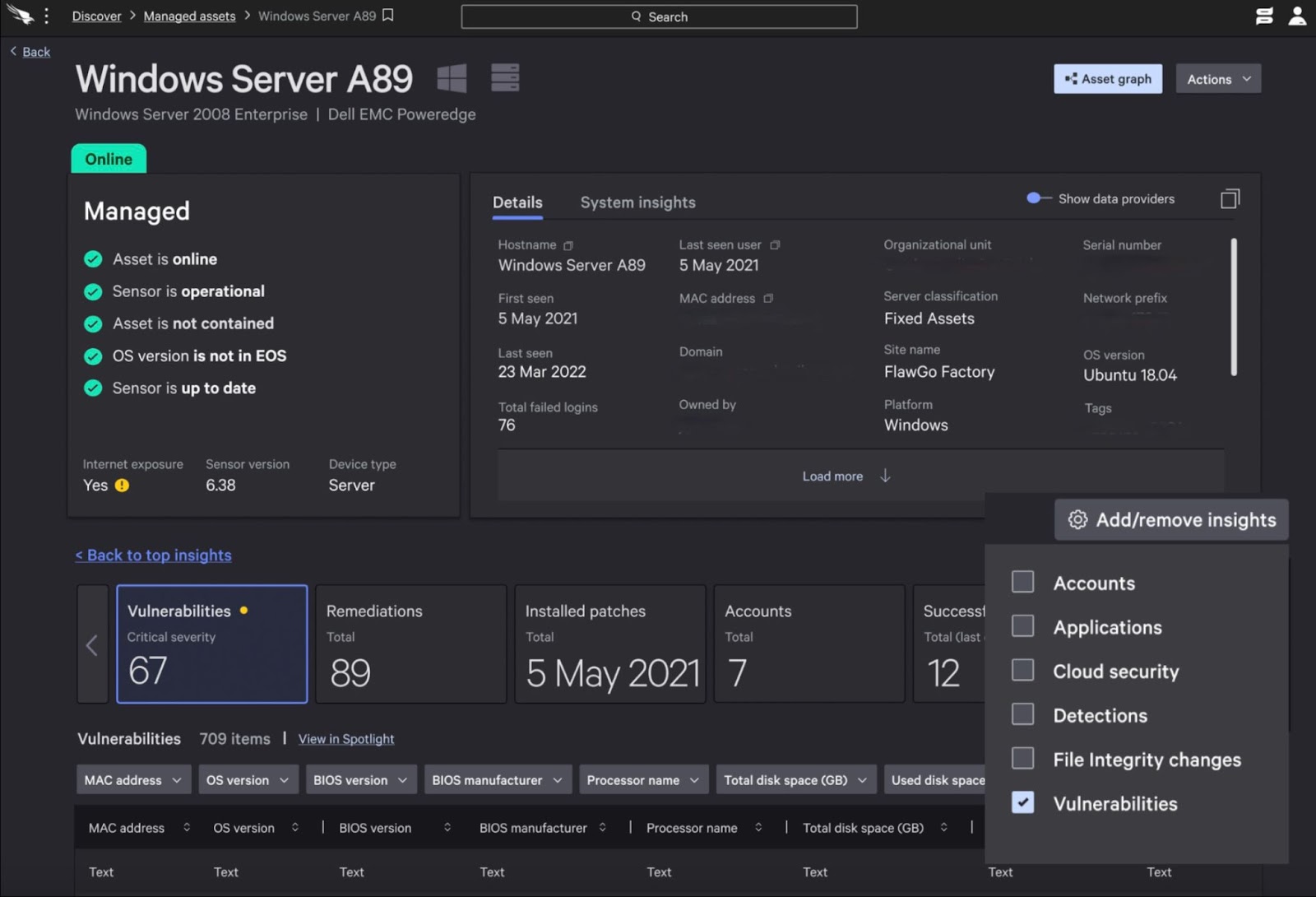
Get control of your applications
- Inventory all applications in your organization to further understand the attack surface.
- Reduce costs with system performance insights to more effectively manage compute resources.
- Proactively prevent breaches by taking action on integrated application vulnerability and threat detection context.
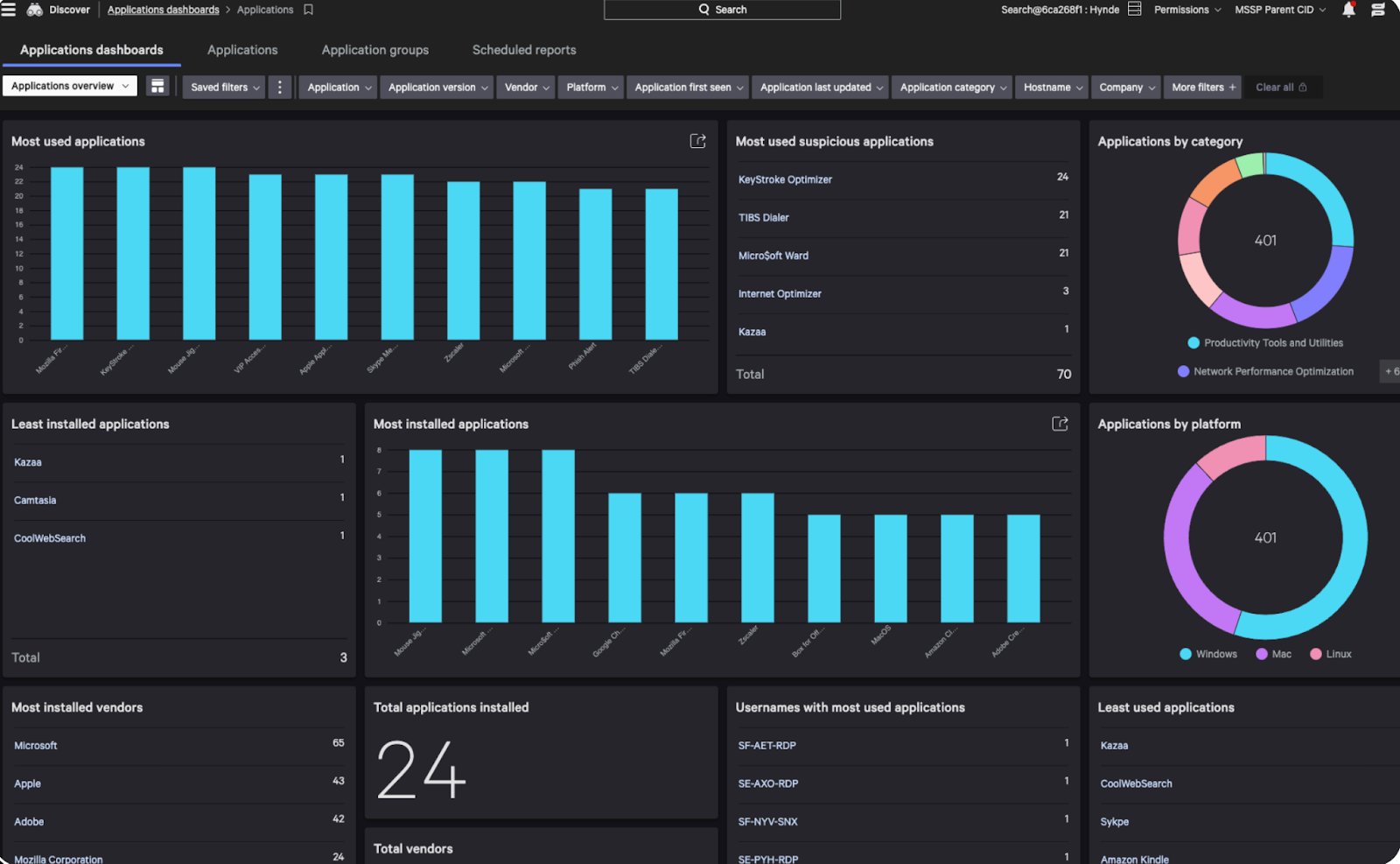
Complete XIoT visibility in 10 minutes or less
Complete XIoT visibility in 10 minutes or less
Tested and proven leader

#1 in XDR (Enterprise, Overall)
#1 in Threat Intelligence, and Enterprise Antivirus

Received Additional Top Rated Awards for -- Antivirus, Cloud Computing Security, Incident Response, Intrusion Detection, MDR, Threat Intelligence, Vulnerability Management

#1 Ranked Badge in MDR, Anti-Malware, Threat Intelligence Platforms