CrowdStrike Falcon® Cloud Security for AWS
Innovate with AWS.
Secure with CrowdStrike.
Complete visibility and protection for AWS workloads
Secure as you deploy
Deploy Falcon Cloud Security to your landing zone and keep all of your AWS resources automatically protected as you migrate, build, and scale.
Protect AWS resources
Protect at every stage of cloud adoption — from instances to containers to managed services.
Complete cloud visibility
CrowdStrike automatically discovers AWS resources as they’re deployed and pinpoints misconfigurations, vulnerabilities, and elevated privileges to improve your security posture.
Why Falcon Cloud Security for AWS?
Secure and optimize cloud migration and operations
- Secure your cloud migration: Ensure a secure, cost-effective cloud migration, boosting agility and innovation while protecting against threats.
- Integrate security automatically: Deploy Falcon Cloud Security with every new AWS resource, ensuring instant, automatic, and comprehensive coverage.
- Multi-account support: Get centralized security and visibility across segmented environments through seamless integration.
Unified cloud security
- Integrated protection: Get unified protection across AWS services, combining deep runtime security with pre-runtime scanning for vulnerabilities and misconfigurations.
- Consolidate and save: Consolidate security tools into a unified CNAPP platform, enhancing breach protection and reducing costs with streamlined operations.
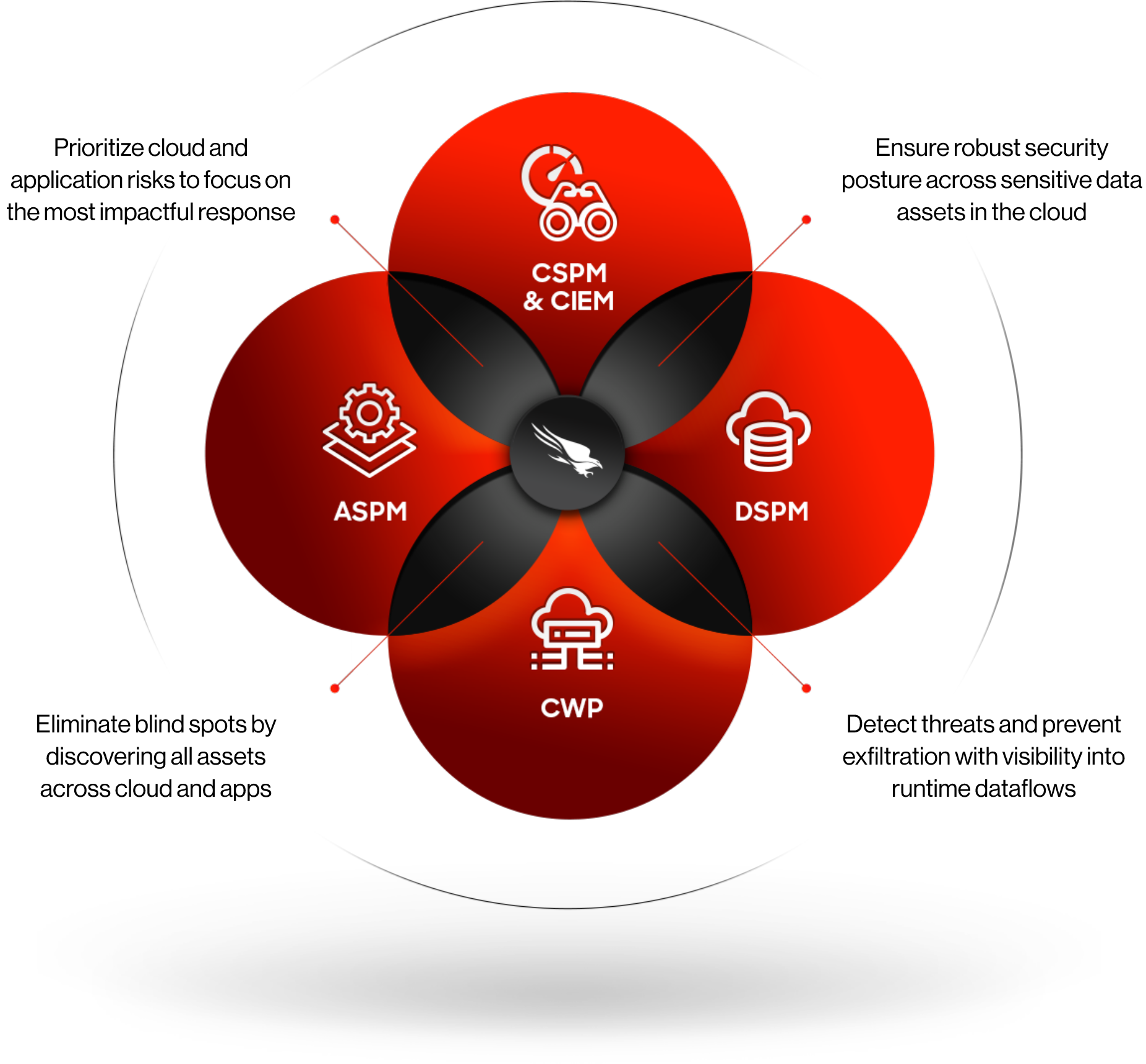
Complete cloud visibility
- See all assets: Falcon Cloud Security dynamically discovers and displays assets, then identifies vulnerabilities, misconfigurations, and instances of excessive permissions or unauthorized access.
- Secure applications: Protect microservice environments and see security risk at the application layer,ensuring security goes beyond infrastructure to protect applications running on AWS.
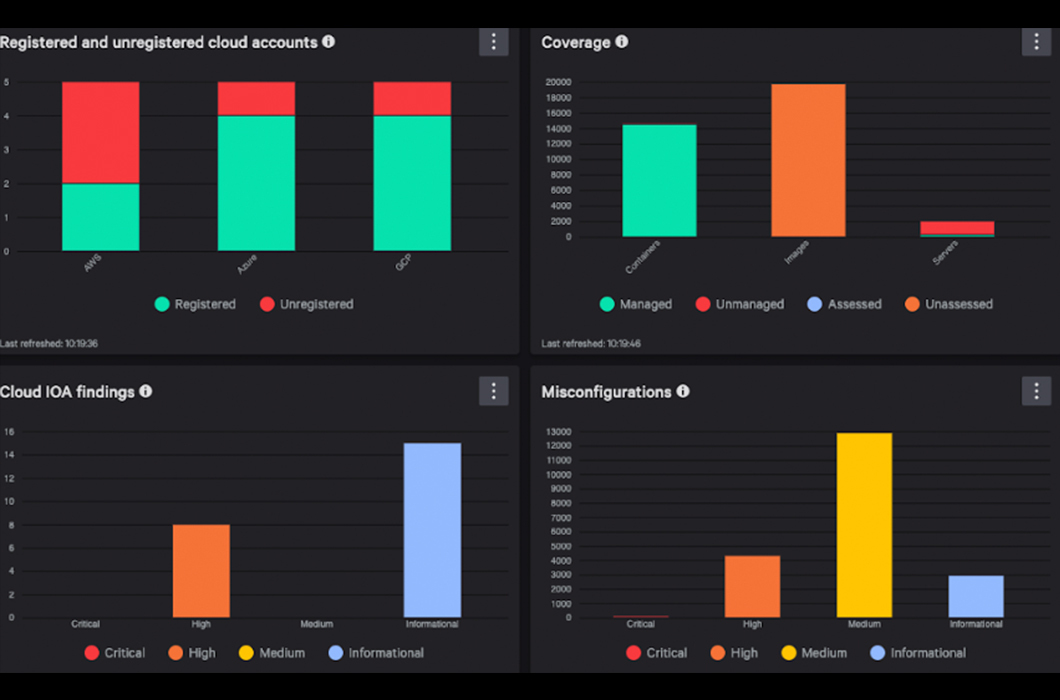
The definitive cybersecurity platform for the cloud era
Trillions
of security events monitored weekly
140M+
IOA protections every minute
Billions
of containers protected
Where CrowdStrike and AWS work together
Support for AWS cloud computing and container management services
- Amazon EC2 (including AWS Graviton)
- Amazon ECS
- Amazon EKS
- AWS Fargate
- ROSA
- AWS Outposts
- VMware on AWS
- Amazon Workspaces
- Amazon Elastic Container Registry
- AWS Lambda
- AWS PrivateLink

Integrate CrowdStrike with AWS management and automation services
- AWS Organizations
- AWS Control Tower
- AWS Systems Manager
- AWS CodePipeline
- Amazon EventBridge
- AWS Lambda
- AWS Built-in + CloudFormation

Visibility into AWS assets
- AWS CloudTrail
- Amazon EventBridge
- AWS IAM
- AWS Security Hub
- Amazon Security Lake
- Amazon GuardDuty

Tested and proven leader


Customers trust CrowdStrike for cloud security
“Cloud is a big part of our future. CrowdStrike has given us the security baseline patterns we need to have to make sure that as we move into the cloud, the infrastructure that we are setting up is secure from the outset.”
Mick McHugh
CISO, Tabcorp
“CrowdStrike Falcon Cloud Security helps us swiftly assess our environment, address gaps, and respond in real-time.”
Anthony Cunha
Deputy CISO, Mercury Financial
