Discovering the Critical OpenSSL Vulnerability with the CrowdStrike Falcon Platform

11/1 UPDATE
Additional details and mitigating patches are now available on OpenSSL’s website. Two CVEs have been published: CVE-2022-3602 (buffer overflow with potential for remote code execution) and CVE-2022-3786 (buffer overflow).
The original issue, CVE-2022-3602, has been downgraded to a severity of HIGH from CRITICAL. Additional details are available on OpenSSL’s blog here.
CrowdStrike Falcon Spotlight has been updated to automatically generate detections and tag CVE-2022-3602 with the appropriate classifications and attributes, with coverage for CVE-2022-3786 being added shortly.
Original Post:
Note: This post first appeared in r/CrowdStrike.
OpenSSL.org has announced that an updated version of its OpenSSL software package (version 3.0.7) will be released on November 1, 2022.
This update contains a fix for a yet-to-be-disclosed security issue with a severity rating of “critical” that affects OpenSSL versions above 3.0.0 and below the patched version of 3.0.7, as well as applications with an affected OpenSSL library embedded.
Many applications rely on OpenSSL and, as such, the vulnerability could have major implications for organizations spanning all sizes and industries. Now is the best time to identify which of your systems run impacted versions of OpenSSL and create a prioritized plan for patching when the update becomes available on Tuesday.
CrowdStrike customers can log into the customer support portal and follow the latest updates in Trending Threats & Vulnerabilities: Critical Vulnerability in OpenSSL.
A CVE number has not yet been released and the nature of the flaw — whether it enables local privilege escalation, remote code execution, etc. — is not public. OpenSSL has categorized the issue as critical, a designation it uses to indicate a vulnerability which “affects common configurations” and is likely to be exploitable. A critical issue may, in their words, lead to “significant disclosure of the contents of server memory,” potentially revealing user details; or it may be easily exploited to compromise server private keys or likely lead to RCE.
Below we describe how to determine whether you’re using a vulnerable version of the software and which applications are running it.
For organizations compiling a prioritization plan, an example would be:
- External facing systems and mission-critical infrastructure
- Servers or systems hosting shared services
- All other affected systems
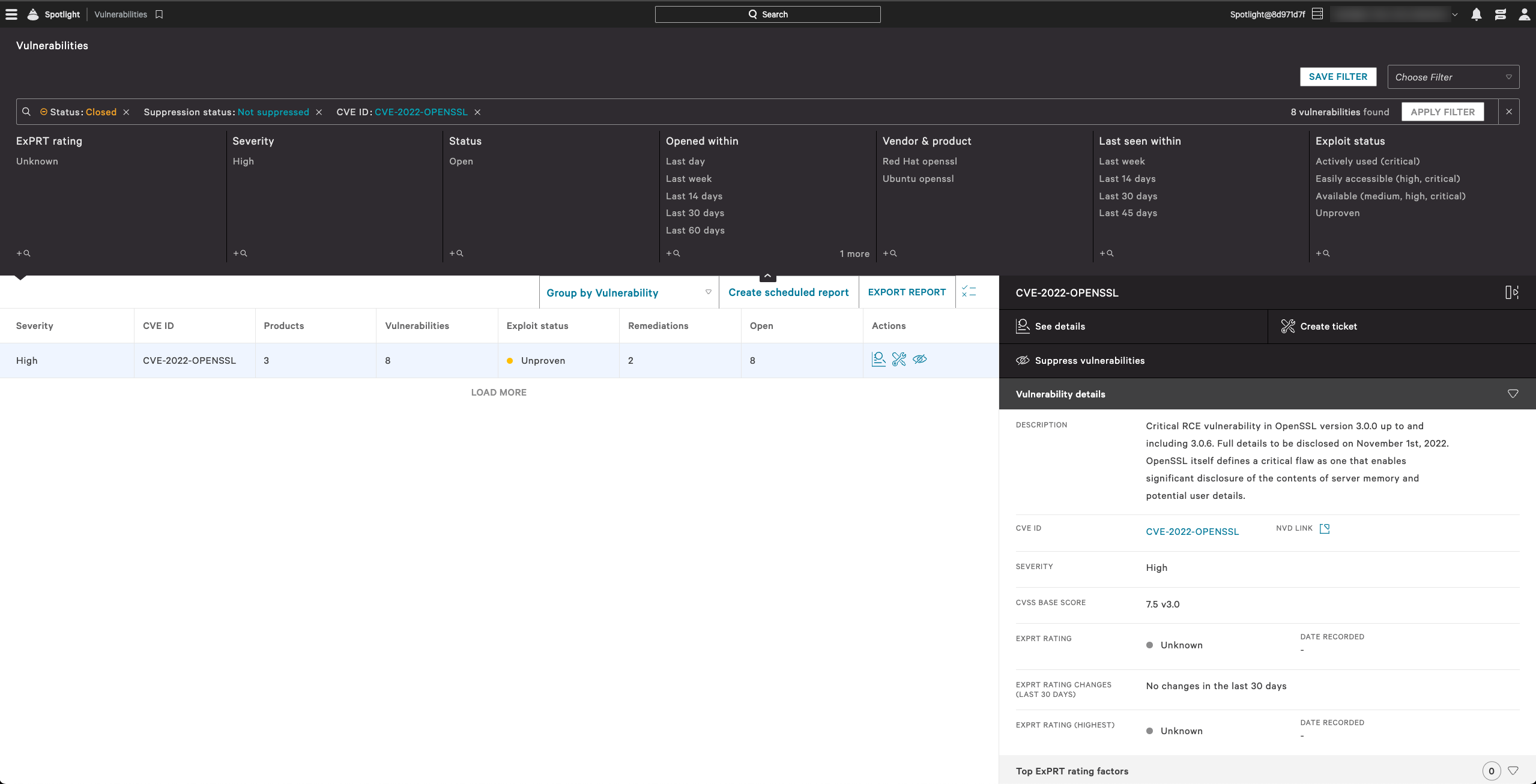
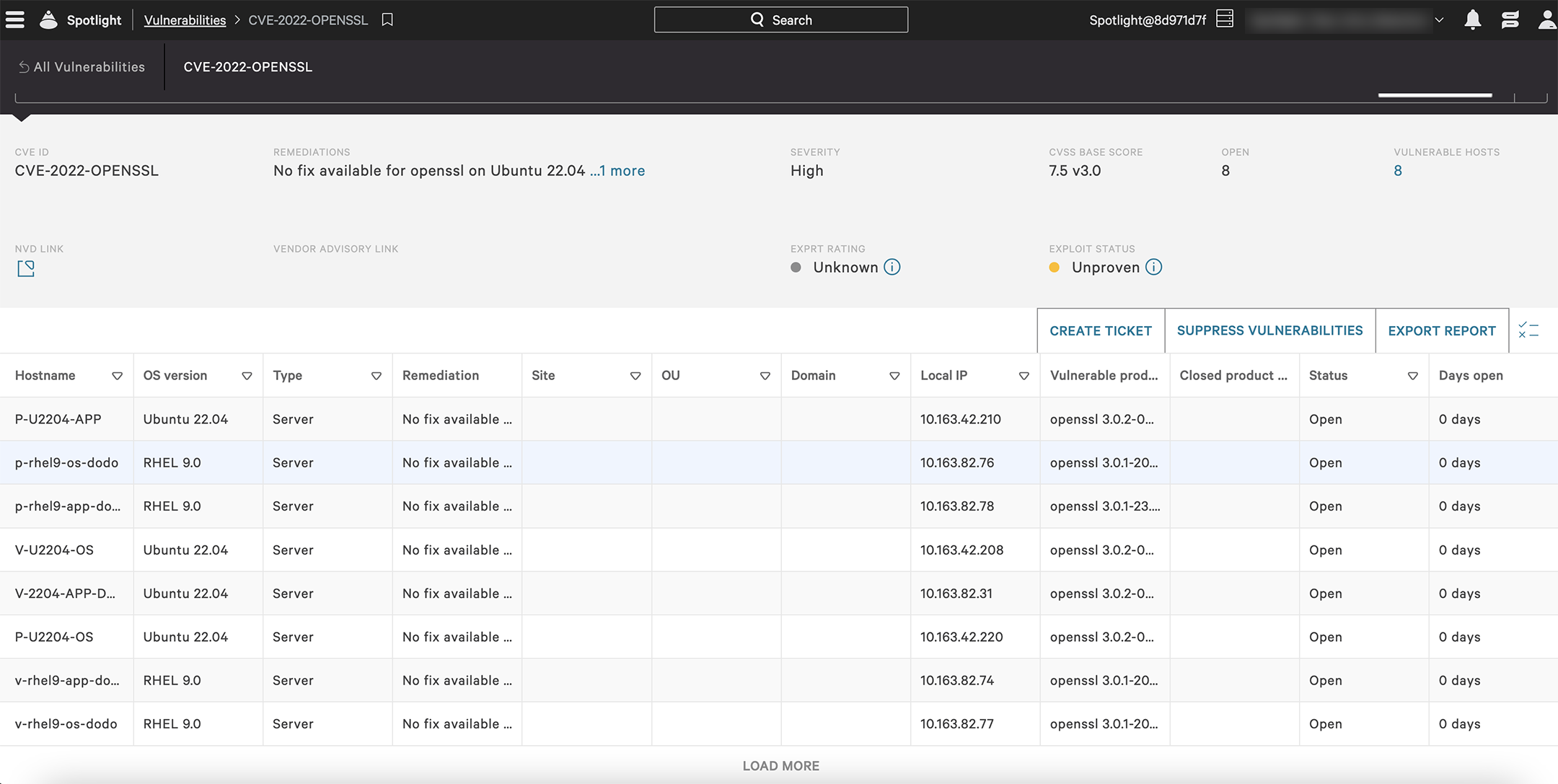
CrowdStrike Falcon Spotlight: Automatically Identify Potentially Vulnerable Versions of OpenSSL
Falcon Spotlight customers can automatically identify potentially vulnerable versions of OpenSSL. Falcon Spotlight will generate detections for CVE-2022-OPENSSL on Windows and Linux Distributions:
If you are not yet a customer, you can start a free trial of the Falcon Spotlight™ vulnerability management solution today.
Hunting Down A Critical Flaw with the Falcon Platform
CrowdStrike Falcon Insight XDR customers with Spotlight or Discover can search for the presence of OpenSSL software now using the following:
Event Search
index=main sourcetype=InstalledApplication*
event_simpleName=InstalledApplication "openssl"
| stats values(ComputerName) as computerName by AppVendor, AppSource, AppName, AppVersion
LogScale
#event_simpleName=InstalledApplication openssl
| groupBy([aid], function=stats([collect([AppVendor, AppSource, AppName, AppVersion])]), limit=max)
| match(file="fdr_aidmaster.csv", field=aid, include=ComputerName, ignoreCase=true, strict=false)
The above query has intentionally been left broad to include all OpenSSL versions; however, it can be narrowed. A per-system formatted query is below:
Event Search
index=main sourcetype=InstalledApplication*
event_simpleName=InstalledApplication "openssl"
| stats values(AppVendor) as appVendor, values(AppSource) as appSource, values(AppName) as appName, values(AppVersion) as appVersion, by aid
| lookup local=true aid_master aid OUTPUT ComputerName, Version, AgentVersion, Timezone
| table aid, ComputerName, Version, AgentVersion, Timezone, app*
| sort + ComputerName
LogScale
#event_simpleName=InstalledApplication openssl
| match(file="fdr_aidmaster.csv", field=aid, include=ComputerName, ignoreCase=true, strict=false)
| groupBy([AppVendor, AppSource, AppName, AppVersion], function=stats([collect([ComputerName])]), limit=max)
Discover Customers
Discover customers can use the following link(s) to search for the presence of OpenSSL in their environment: [ US-1 | US-2 | EU | Gov ].
Additional Resources
- Read the blog “Falcon Insight XDR and Falcon LogScale: What You Need to Know.”
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.