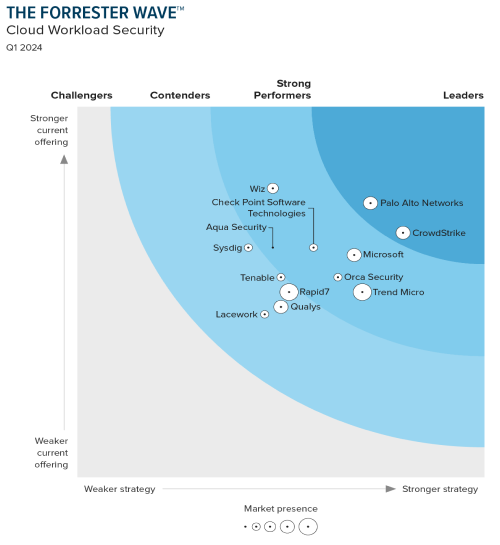
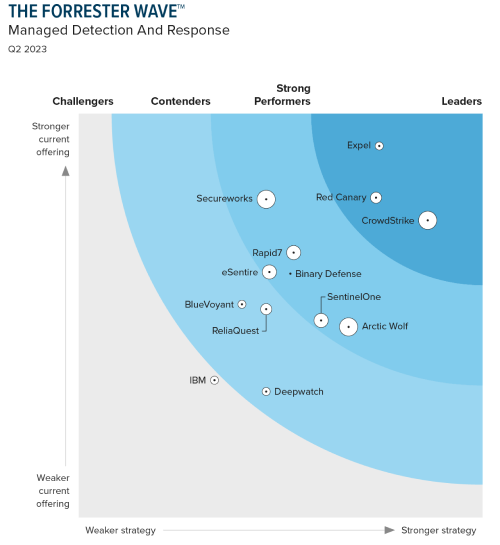
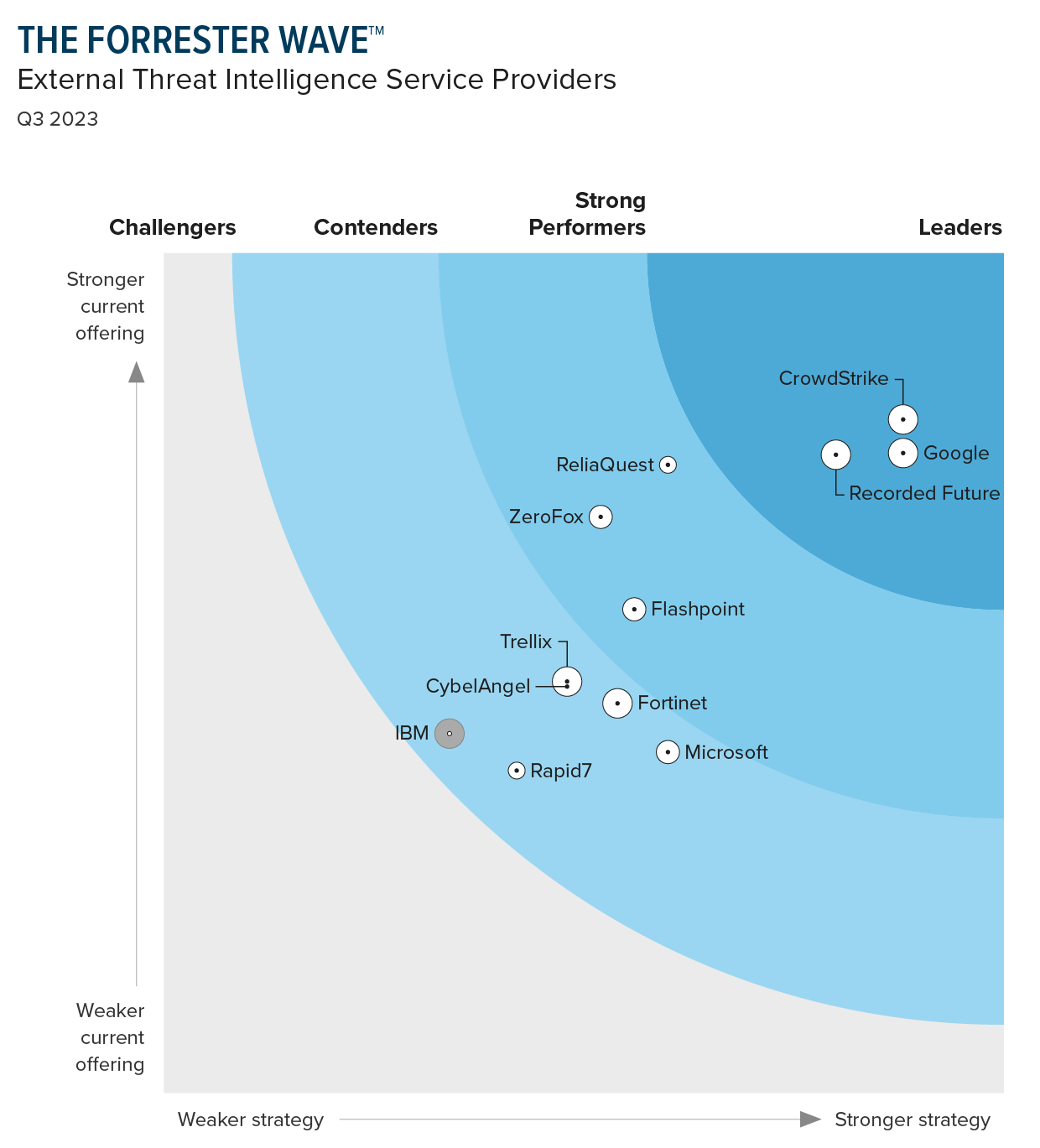
CrowdStrike vs. Microsoft
Why customers choose CrowdStrike over Microsoft
 Microsoft Poor coverage = susceptible to breaches
Microsoft Poor coverage = susceptible to breaches
- ×Built on a foundation of obsolete, signature-based AV that is ineffective against modern adversaries
- ×Security capabilities vary drastically across different OS editions and versions, creating inconsistent protections
- ×Gartner cautions Microsoft “is challenged by limited support for older OSs and generally uneven support across non-Windows OSs”
The CrowdStrike difference
CrowdStrike Advanced breach prevention
CrowdStrike offers advanced, consistent, signature-free security across all OS editions and versions. Leveraging AI-powered Indicators of Attack (IOAs) and integrated threat intelligence, CrowdStrike delivers world-class breach prevention, independently proven in MITRE Engenuity ATT&CK® Evaluations: Enterprise, round 5 with 100% protection, 100% visibility, and 100% analytic detection coverage.
 Microsoft Complex to operate, complex to maintain
Microsoft Complex to operate, complex to maintain
- ×Needs frequent OS-level upgrades increasing cost and operational burden
- ×Heavy operational workload often requires additional staff
- ×Security functionality is strewn across multiple disjointed consoles, fragmenting SOC workflows
The CrowdStrike difference
CrowdStrike Easy to use, easy to operate
CrowdStrike’s single, lightweight agent streamlines installation and management. All modules are housed in a unified, user-friendly interface, enhancing SOC workflows and streamlining platform consolidation.
 Microsoft generates High Total Cost of Ownership (TCO)
Microsoft generates High Total Cost of Ownership (TCO)
- ×Essential features like threat analytics and server protection aren’t included in standard bundles, leading to unexpected license costs
- ×Frequent maintenance requires more dedicated staff
- ×Gartner warns that Microsoft’s security bundles “often [create] shelfware and redundant spending”
The CrowdStrike difference
CrowdStrike deliversUnmatched ROI
CrowdStrike offers unparalleled ROI, freeing up valuable resources and employee bandwidth. Our intuitive interface reduces training costs, and rapid deployment helps you transition from outdated systems, avoiding costly contract overlaps or extensions. CrowdStrike’s transparent licensing means no surprise fees.
 Compare
Compare
Understand the key differences between CrowdStrike and Microsoft
Microsoft
Deployment
 Rapid deployment, instant protection
Rapid deployment, instant protection
Deploy instantly with a single, lightweight agent — no OS prerequisites, complex configuration, or fine tuning required.
 Complicated deployment hinders security
Complicated deployment hinders security
All endpoints require the premium edition of the latest version of Windows, requiring upfront OS and hardware upgrades for full security functionality.
Detection coverage
 Advanced threat detection
Advanced threat detection
High-fidelity detection engine leverages advanced AI, behavioral IOAs, and industry-leading threat intelligence to detect the most advanced threats — including zero-days, unknown malware, and hands-on-keyboard activity.
 Ineffective threat detection
Ineffective threat detection
Adversaries are easily bypassing Microsoft security products, exploiting its outdated, signature-based AV, making them ineffective against modern attacks.
Total cost of ownership
 Simplified operations and licensing cuts TCO
Simplified operations and licensing cuts TCO
No hidden costs. Transparent licensing is easy to budget, and simplified security management frees up staff and reduces training costs.
 Unexpected costs skyrocket TCO
Unexpected costs skyrocket TCO
Microsoft’s security solutions incur unexpected high costs from burdensome platform maintenance, and complex licensing, often requiring additional dedicated staff.
Ease of use
 Optimized analyst experience
Optimized analyst experience
A single, unified console and customizable workflow automations offer complete attack visibility, real-time threat context, and accelerated investigation across endpoints, cloud, identity and more.
 Disjointed user experience
Disjointed user experience
Microsoft’s complex platform, criticized by Gartner for its “below-average ease of use,” frustrates analysts with its multiple consoles, creating security risks and slowing response times.
Managed Detection and Response
 World-class expertise
World-class expertise
CrowdStrike is the #1 leader in MDR by market share (Gartner). Our service delivers end-to-end response across endpoint, identity, and cloud to conclusively remediate attacks, with zero customer handoffs that waste time or increase risk. CrowdStrike provides the most comprehensive detection coverage and delivers the fastest threat detection.
 Incomplete managed detection and response
Incomplete managed detection and response
Lacks proactive threat hunting provided by security experts. Instead, Microsoft’s MDR relies on inadequate, generalized threat intelligence and AI. Microsoft was missing entirely from the recent Forrester Wave: Managed Detection and Response, Q2 2023.