Why customers choose CrowdStrike over Microsoft
 Microsoft Poor coverage = susceptible to breaches
Microsoft Poor coverage = susceptible to breaches
-
×Built on a foundation of obsolete, signature-based AV that is ineffective against modern adversaries
-
×Security capabilities vary drastically across different OS editions and versions, creating inconsistent protections
-
×Gartner customer research suggests "the technical support and account management support they receive from Microsoft is variable"
The CrowdStrike difference
CrowdStrike Advanced breach prevention
CrowdStrike offers advanced, consistent, signature-free security across all OS editions and versions. Leveraging AI-powered Indicators of Attack (IOAs) and integrated threat intelligence, CrowdStrike delivers world-class breach prevention, independently proven in MITRE Engenuity ATT&CK® Evaluations: Enterprise, round 5 with 100% protection, 100% visibility, and 100% analytic detection coverage.
Report
CrowdStrike named a Leader by Gartner
Furthest Right in Vision. Highest in Ability to Execute. Only CrowdStrike.
Learn more
 Microsoft Complex to operate, complex to maintain
Microsoft Complex to operate, complex to maintain
-
×Needs frequent OS-level upgrades increasing cost and operational burden
-
×Heavy operational workload often requires additional staff
-
×Security functionality is strewn across multiple disjointed consoles, fragmenting SOC workflows
The CrowdStrike difference
CrowdStrike Easy to use, easy to operate
CrowdStrike’s single, lightweight agent streamlines installation and management. All modules are housed in a unified, user-friendly interface, enhancing SOC workflows and streamlining platform consolidation.
CrowdStrike hands down gave us the most visibility."
Jason Strohbehn, Deputy CISO, State of Wyoming
 Microsoft generates High Total Cost of Ownership (TCO)
Microsoft generates High Total Cost of Ownership (TCO)
-
×Essential features like server protection aren’t included in standard bundles, leading to unexpected license costs
-
×Frequent maintenance requires more dedicated staff
-
×Inconsistent feature availability across Windows versions drive the necessity for multiple configs with associated increased workload
The CrowdStrike difference
CrowdStrike deliversUnmatched ROI
CrowdStrike offers unparalleled ROI, freeing up valuable resources and employee bandwidth. Our intuitive interface reduces training costs, and rapid deployment helps you transition from outdated systems, avoiding costly contract overlaps or extensions. CrowdStrike’s transparent licensing means no surprise fees.
8 out of 10 times
when an enterprise customer does a proof-of-value technology test, they choose CrowdStrike over Microsoft.
Learn more Compare
Compare
Understand the key differences between CrowdStrike and Microsoft
Microsoft
Deployment
Rapid deployment, instant protection
Deploy instantly with a single, lightweight agent — no OS prerequisites, complex configuration, or fine tuning required.
Complicated deployment hinders security
All endpoints require the premium edition of the latest version of Windows, requiring upfront OS and hardware upgrades for full security functionality.
Detection coverage
Advanced threat detection
High-fidelity detection engine leverages advanced AI, behavioral IOAs, and industry-leading threat intelligence to detect the most advanced threats — including zero-days, unknown malware, and hands-on-keyboard activity.
Ineffective threat detection
Adversaries are easily bypassing Microsoft security products, exploiting its outdated, signature-based AV, making them ineffective against modern attacks.
Total cost of ownership
Simplified operations and licensing cuts TCO
No hidden costs. Transparent licensing is easy to budget, and simplified security management frees up staff and reduces training costs.
Unexpected costs skyrocket TCO
Microsoft’s security solutions incur unexpected high costs from burdensome platform maintenance, and complex licensing, often requiring additional dedicated staff.
Ease of use
Optimized analyst experience
A single, unified console and customizable workflow automations offer complete attack visibility, real-time threat context, and accelerated investigation across endpoints, cloud, identity and more.
Disjointed user experience
Microsoft’s complex platform frustrates analysts with its multiple consoles, creating security risks and slowing response times.
Managed Detection and Response
World-class expertise
CrowdStrike is the #1 leader in MDR by market share (Gartner). Our service delivers end-to-end response across endpoint, identity, and cloud to conclusively remediate attacks, with zero customer handoffs that waste time or increase risk. CrowdStrike provides the most comprehensive detection coverage and delivers the fastest threat detection.
Incomplete managed detection and response
Lacks proactive threat hunting provided by security experts. Instead, Microsoft’s MDR relies on inadequate, generalized threat intelligence and AI. Microsoft was missing entirely from the recent Forrester Wave: Managed Detection and Response, Q2 2023.
 Validated by industry leading analysts
Validated by industry leading analysts

Report
Leader in Magic Quadrant for Endpoint Protection Platforms
CrowdStrike is positioned highest for ability to execute and furthest to the right for completeness of vision.
Report
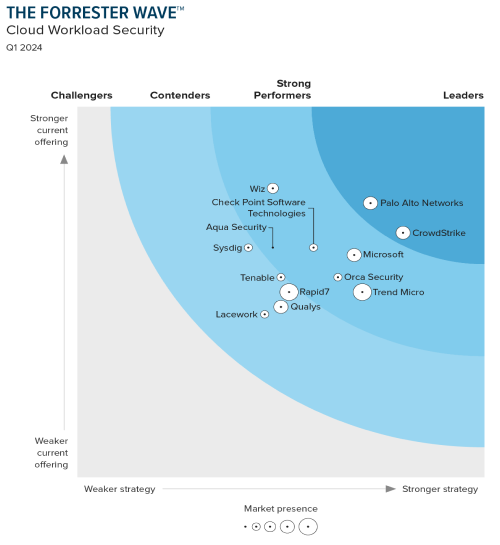
Leader in Forrester Wave: Cloud Workload Security
CrowdStrike is rated as having the strongest strategy of all vendors.
Report
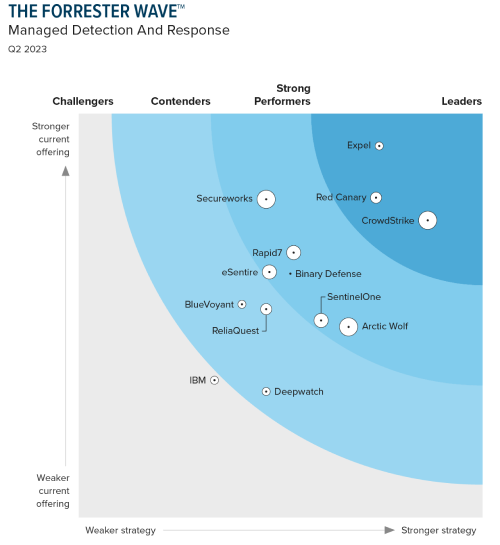
Leader in Forrester Wave: Managed Detection and Response
CrowdStrike is rated as having the strongest strategy of all vendors.
Report
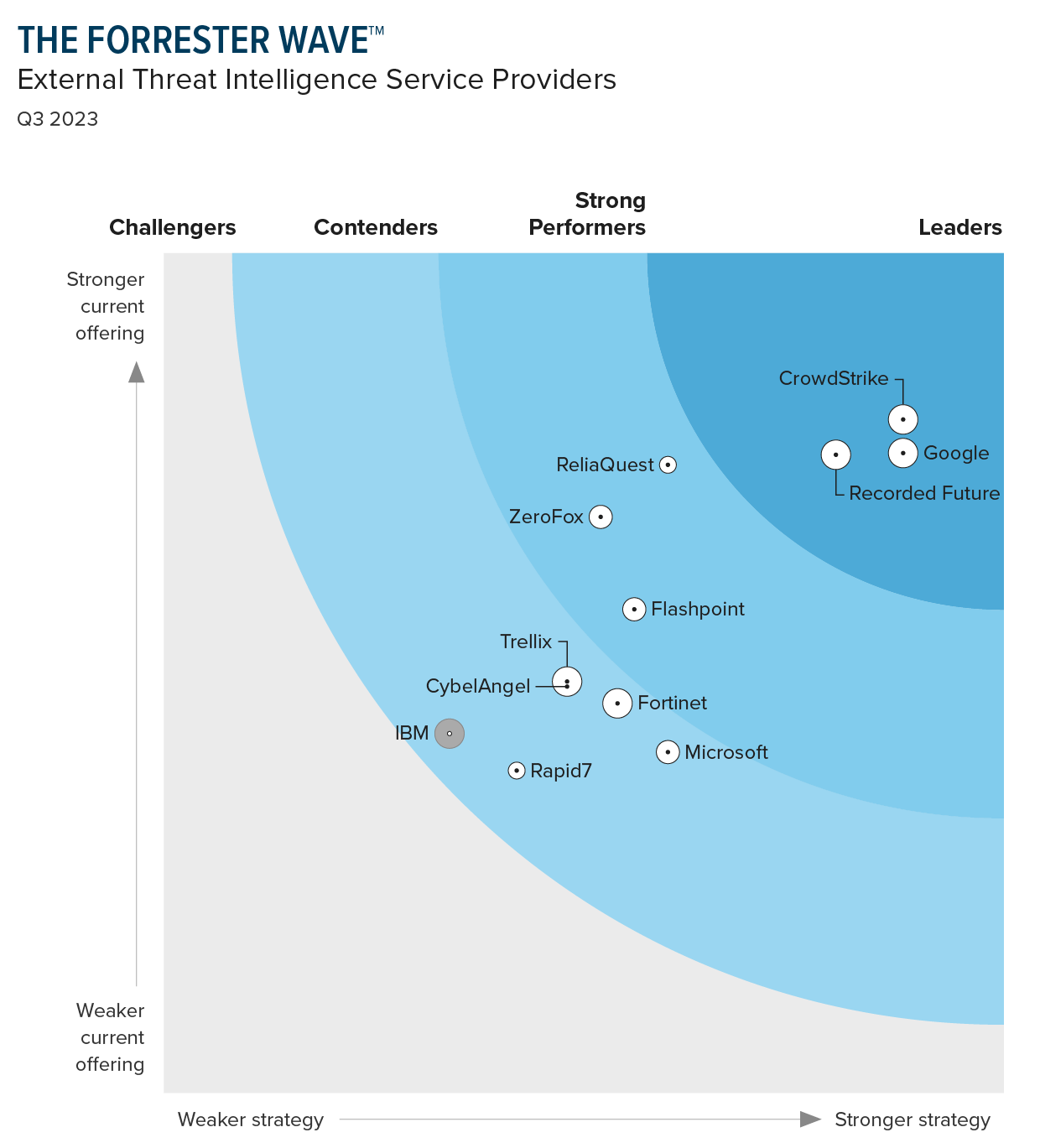
Leader in Forrester Wave: External Threat Intelligence Service Providers
CrowdStrike positioned highest for current offering and furthest for strategy.
Report
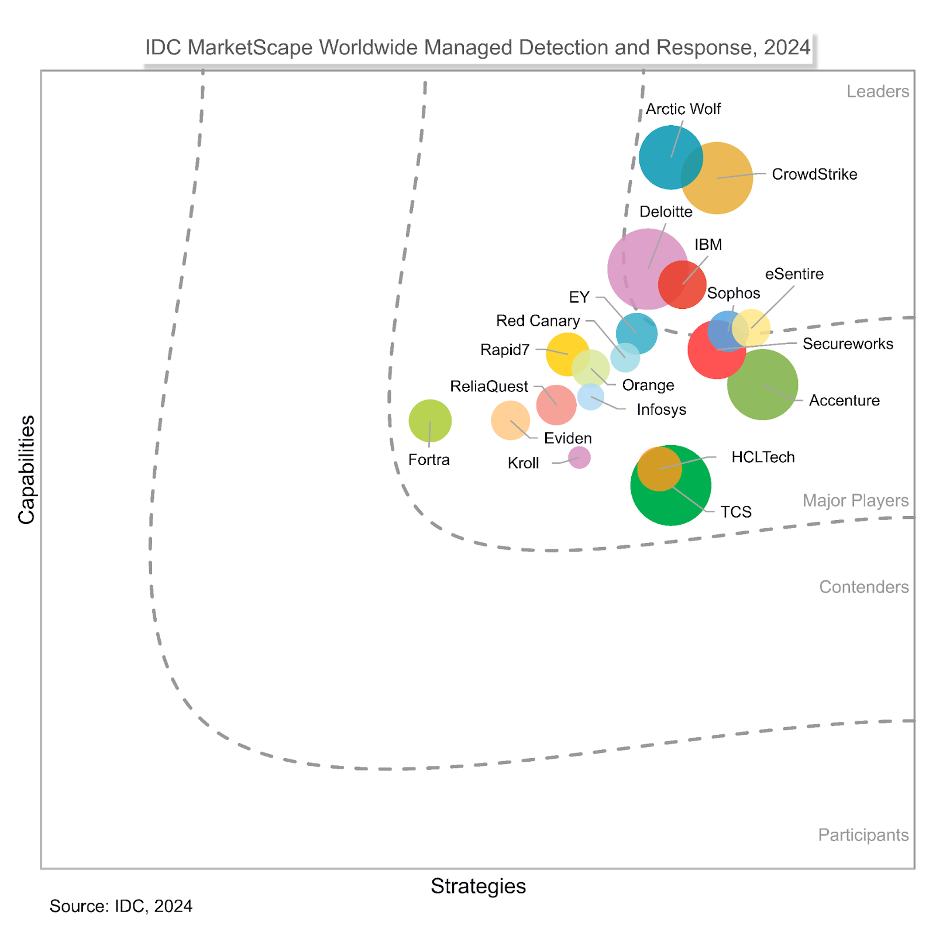
Leader in IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
CrowdStrike named one of only four “Leaders”.
 See what our customers think
See what our customers think
CrowdStrike’s advanced detection and prevention capabilities offer a superior level of protection against potential threats. Its unique feature of automated rules is designed to effectively confine threats at the device level. This automatic confinement of high alerts ensures that the device is secured immediately, buying crucial time for the dedicated response team to identify and neutralize the threat.
David L
PeerSpot
It has helped tremendously to strengthen our security posture by securing our endpoints. It has helped to free up our IT department from having to constantly worry about malware and malicious software infecting our endpoints.
Chris S
G2
Threat Graph gives a detailed explanation and helps to identify the root process from which the attack is being carried out. Overwatch and hybrid analysis in threat graph is the best features which makes us to respond to the attack in a short span of time.
Ganesan K
G2
Very easy to deploy with the amazing help of Crowdstrike staff. It has a very small footprint on resources, and the Falcon Dashboard is very intuitive. The reports are of a standard that can be shared with the Exec team and is fully understood.
Andrew M
G2
It offers ample features for all platforms- windows,linux and max. The user interface is easy to use. Crowdstrike query helps in investigating the alerts more deeply. With right access containment and real time connection proves to be great when working critical alerts. Its machine learning and custom intelligence capabilities makes sure that no incident is overlooked. It also provides great customer support. Implementing tuning for white listing is also simple
Verified User
G2
We receive meaningful events on the platform for investigation. The events are detailed and well-structured. The remote connection option allows us to investigate events in realtime.
Christiaan R
G2
The agent is extremely lightweight and it never takes huge resources on the system. Management is extremely easy with easy dashboard. The alerts are extremely well detailed
Abhishek R
G2
Since we deployed CrowdStrike, the network has become much calmer, and we now understand the sources of infections, which helps us prevent them from spreading.
Security Officer
PeerSpot
Look, all I can say, is this I have a vast experience in every one of the major ADRXDR platforms, and by far would continue to use crowd strike, just due to capability
With CrowdStrike everything is integrated into a single platform, and this is a huge advantage.
Europe Energy

You place a sensor on your computers that requires a very small amount of memory. It’s not like other programs that slow down the computer. CrowdStrike is constantly scanning your computer from the cloud and responds in a millisecond when it detects anything. It couldn’t be less painful, and it couldn’t be more reassuring.
Robert B
PeerSpot
Crowdstrike allows us to completely outsource our endpoint device security – we gain access to highly qualified cyber agents that help address any cyber related instances on our equipment. If a cyber issue occurs, they are there assisting in quickly blocking and resolving the issue. In my experience, the response time has been better than they advertise. Easy to roll out, easy to manage and work with their staff to setup and apply a playbook for issues. All in all a great solution.
Aaron J
G2
The 10 hours a week that we are freeing up from having to manage and monitor our AV solution has really allowed us to focus on other areas of the business. This has been a huge return on investment
Jim M
PeerSpot
Great real-time visibility and reaction to all the endpoints.Offers a lightweight agent. Network isolation and sandboxing features help a lot in conducting an investigation.
Arathi S
G2
CrowdStrike’s advanced detection and prevention capabilities offer a superior level of protection against potential threats. Its unique feature of automated rules is designed to effectively confine threats at the device level. This automatic confinement of high alerts ensures that the device is secured immediately, buying crucial time for the dedicated response team to identify and neutralize the threat.
David L
PeerSpot
It has helped tremendously to strengthen our security posture by securing our endpoints. It has helped to free up our IT department from having to constantly worry about malware and malicious software infecting our endpoints.
Chris S
G2
Threat Graph gives a detailed explanation and helps to identify the root process from which the attack is being carried out. Overwatch and hybrid analysis in threat graph is the best features which makes us to respond to the attack in a short span of time.
Ganesan K
G2
Very easy to deploy with the amazing help of Crowdstrike staff. It has a very small footprint on resources, and the Falcon Dashboard is very intuitive. The reports are of a standard that can be shared with the Exec team and is fully understood.
Andrew M
G2
It offers ample features for all platforms- windows,linux and max. The user interface is easy to use. Crowdstrike query helps in investigating the alerts more deeply. With right access containment and real time connection proves to be great when working critical alerts. Its machine learning and custom intelligence capabilities makes sure that no incident is overlooked. It also provides great customer support. Implementing tuning for white listing is also simple
Verified User
G2
We receive meaningful events on the platform for investigation. The events are detailed and well-structured. The remote connection option allows us to investigate events in realtime.
Christiaan R
G2
The agent is extremely lightweight and it never takes huge resources on the system. Management is extremely easy with easy dashboard. The alerts are extremely well detailed
Abhishek R
G2
Since we deployed CrowdStrike, the network has become much calmer, and we now understand the sources of infections, which helps us prevent them from spreading.
Security Officer
PeerSpot
Look, all I can say, is this I have a vast experience in every one of the major ADRXDR platforms, and by far would continue to use crowd strike, just due to capability
With CrowdStrike everything is integrated into a single platform, and this is a huge advantage.
Europe Energy

You place a sensor on your computers that requires a very small amount of memory. It’s not like other programs that slow down the computer. CrowdStrike is constantly scanning your computer from the cloud and responds in a millisecond when it detects anything. It couldn’t be less painful, and it couldn’t be more reassuring.
Robert B
PeerSpot
Crowdstrike allows us to completely outsource our endpoint device security – we gain access to highly qualified cyber agents that help address any cyber related instances on our equipment. If a cyber issue occurs, they are there assisting in quickly blocking and resolving the issue. In my experience, the response time has been better than they advertise. Easy to roll out, easy to manage and work with their staff to setup and apply a playbook for issues. All in all a great solution.
Aaron J
G2
The 10 hours a week that we are freeing up from having to manage and monitor our AV solution has really allowed us to focus on other areas of the business. This has been a huge return on investment
Jim M
PeerSpot
Great real-time visibility and reaction to all the endpoints.Offers a lightweight agent. Network isolation and sandboxing features help a lot in conducting an investigation.
Arathi S
G2
CrowdStrike’s advanced detection and prevention capabilities offer a superior level of protection against potential threats. Its unique feature of automated rules is designed to effectively confine threats at the device level. This automatic confinement of high alerts ensures that the device is secured immediately, buying crucial time for the dedicated response team to identify and neutralize the threat.
David L
PeerSpot
It has helped tremendously to strengthen our security posture by securing our endpoints. It has helped to free up our IT department from having to constantly worry about malware and malicious software infecting our endpoints.
Chris S
G2
Threat Graph gives a detailed explanation and helps to identify the root process from which the attack is being carried out. Overwatch and hybrid analysis in threat graph is the best features which makes us to respond to the attack in a short span of time.
Ganesan K
G2
Very easy to deploy with the amazing help of Crowdstrike staff. It has a very small footprint on resources, and the Falcon Dashboard is very intuitive. The reports are of a standard that can be shared with the Exec team and is fully understood.
Andrew M
G2
It offers ample features for all platforms- windows,linux and max. The user interface is easy to use. Crowdstrike query helps in investigating the alerts more deeply. With right access containment and real time connection proves to be great when working critical alerts. Its machine learning and custom intelligence capabilities makes sure that no incident is overlooked. It also provides great customer support. Implementing tuning for white listing is also simple
Verified User
G2
We receive meaningful events on the platform for investigation. The events are detailed and well-structured. The remote connection option allows us to investigate events in realtime.
Christiaan R
G2




