Migrating to the cloud has allowed many organizations to reduce costs, innovate faster and deliver business results more effectively. However, as businesses expand their cloud investments, they must adapt their security strategies to stay one step ahead of threats that target their expanded environment. Managing, securing and having visibility across endpoints, networks and workloads is not an easy feat. It requires a unified defense-in-depth approach.
Defense-in-depth is an architectural design that originates from a military strategy requiring attackers to breach multiple lines of defense. In the context of protecting cloud workloads, defense-in-depth relies on multiple defensive mechanisms to protect valuable data, information and intellectual property.
The collaboration between CrowdStrike and Amazon Web Services (AWS) brings together a principled defense-in-depth approach to securing cloud environments that is differentiated in the market. CrowdStrike’s leading endpoint protection, workload protection and threat intelligence directly integrate with AWS services to build an effective defense-in-depth solution to stay ahead of threats.
CrowdStrike is an AWS Security Competency Partner, and to apply a defense-in-depth approach, CrowdStrike and AWS believe the following principles must be considered:
- Visibility
- Prevention
- Remediation and response
In this blog, we describe the different event-driven architectures and services that operate in tandem to provide defense-in-depth cloud security.
Visibility Drives Clarity
Visibility into all of an organization’s deployed assets and workloads allows operations and security teams to gain clarity into the current state of their environment. The tools that enable visibility need to allow teams to:
- View configurations of all components
- Aggregate and monitor system calls and network traffic entering and leaving the workload
- Audit API calls
- Provide runtime visibility by introspecting system calls made by applications in an Amazon Elastic Cloud Compute (Amazon EC2) instance or a container
Regardless of whether an organization has homegrown, cloud-native or third-party workloads, the data gathered across these parameters must be treated as a point-in-time assessment of a continuously monitored environment.
To operationalize these capabilities, it is crucial to understand and compartmentalize workloads based on the data, users and applications that use them. One of the first considerations for applying defense-in-depth to workloads focuses on visibility into, and auditing resources for, environments where applications and data reside. At this point, CrowdStrike and AWS together provide the insight into what data, applications and assets are being utilized so you are ready to face attacks. The CrowdStrike Falcon® platform leverages real-time indicators of attack (IOAs), threat intelligence, evolving adversary tradecraft and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation, elite threat hunting, and prioritized observability of vulnerabilities.
Organizations can achieve the first layer of the defense-in-depth framework by leveraging both CrowdStrike and AWS through:
- Centralized logs: AWS CloudTrail enables organizations to log every API call made to an AWS service while virtual private cloud (VPC) flow logs capture network traffic logs. Centralizing these logs from multiple AWS accounts and storing them separately with access based on least privilege enables organizations to ensure immutability of the logs for audit and forensics.
- Cloud security posture management (CSPM): CrowdStrike Falcon® Cloud Security uses a combination of API calls and event-driven architectures using Amazon EventBridge to gather inventory, configuration, user, service and network activity to provide organizations with a real-time assessment of their cloud security posture. As deployments become more complex and workloads span across AWS accounts, it becomes imperative to enable visibility from when an AWS account is created as well as understanding if there are any misconfigurations or compliance violations associated with it.
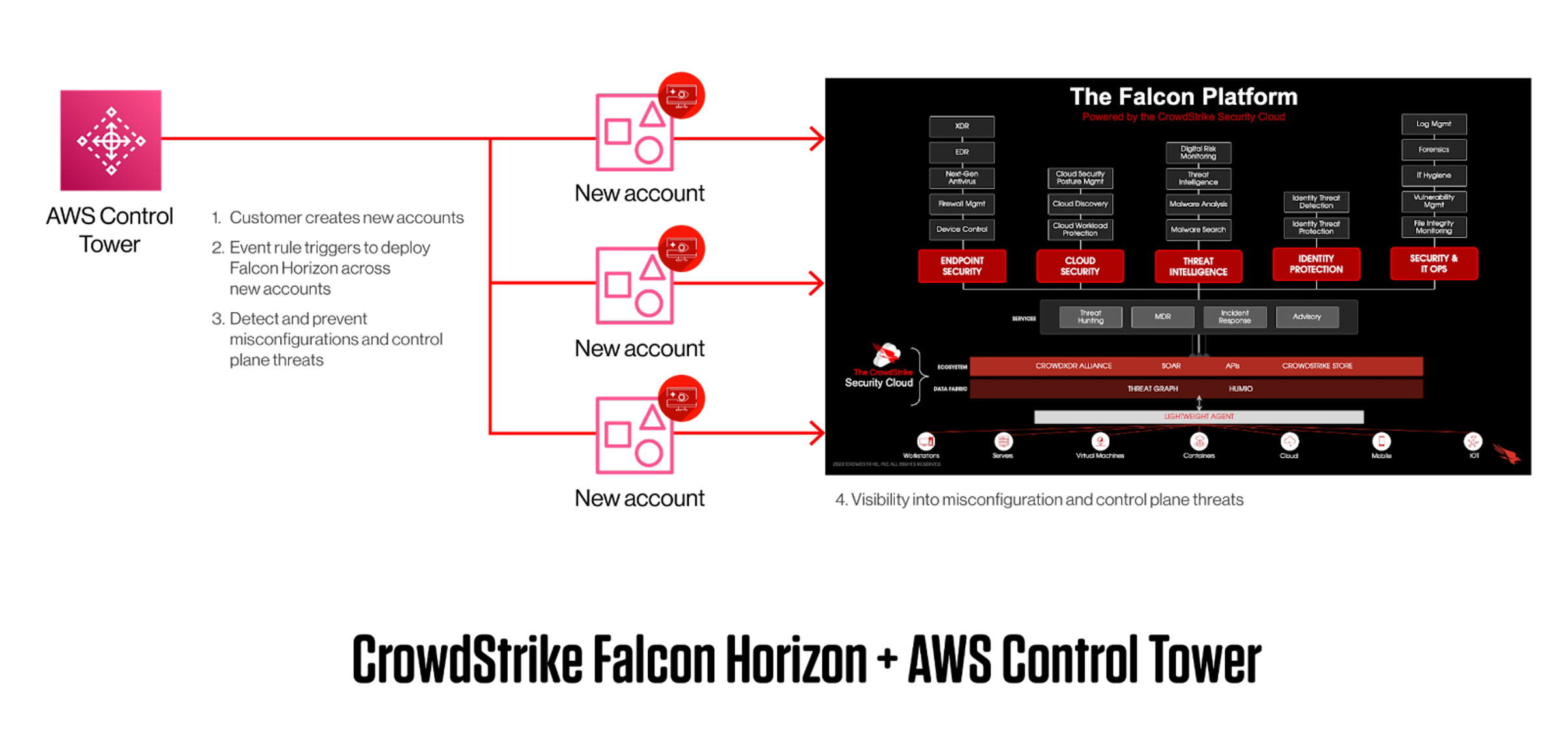
- Automatic visibility: AWS Control Tower lifecycle events allow organizations to implement asynchronous workflows as AWS accounts are spun up using the account factory. By hooking into these lifecycle events, CrowdStrike Falcon® Cloud Security simplifies visibility and continuous monitoring by building it into every AWS account that’s used.
Prevention through Aggregation and Correlation
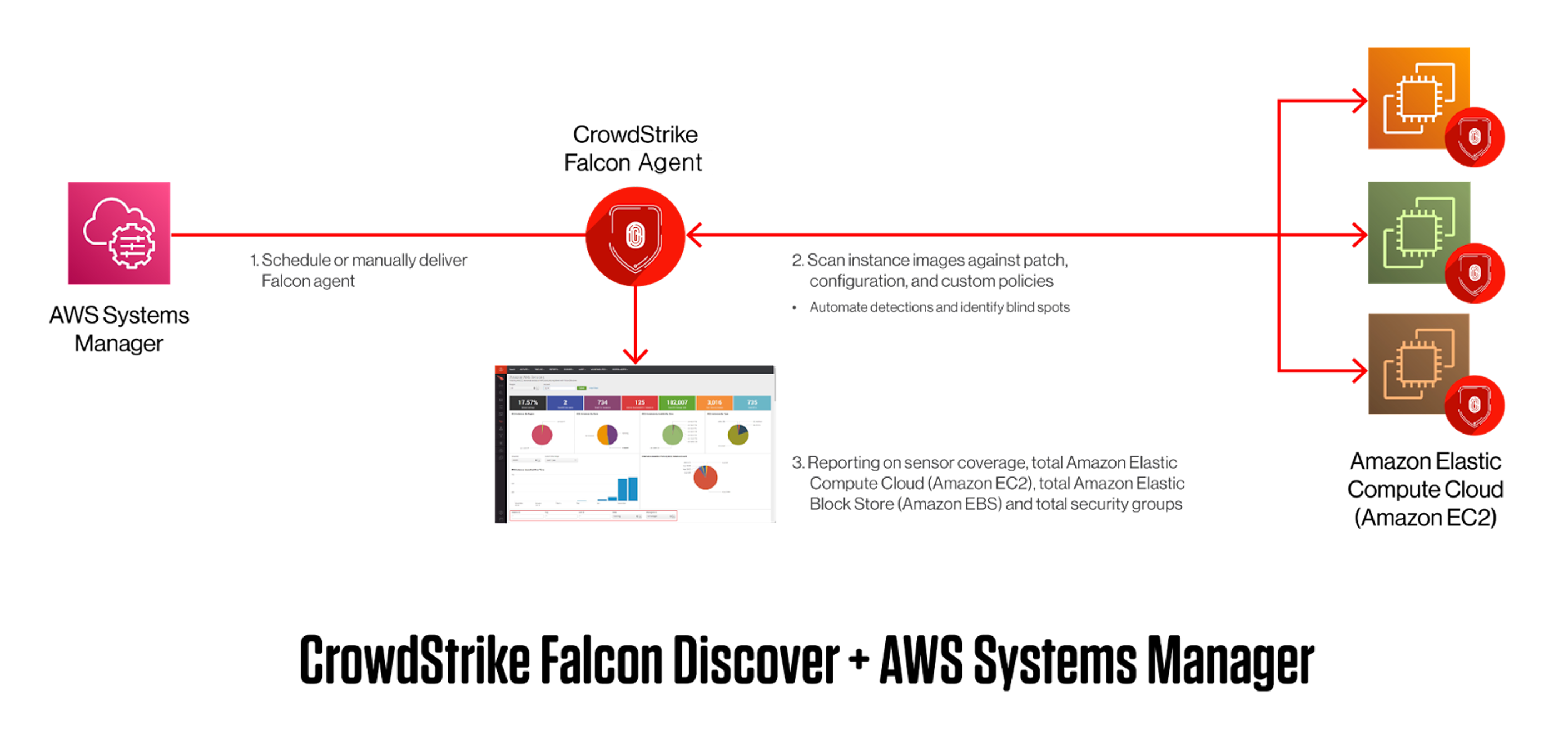
Once organizations have visibility into all of their resources, the next principle of preventative controls is to detect anomalous behavior in their workloads. This requires bringing together discovery and audit information with runtime visibility from multiple sources, such as Amazon EC2, Amazon Elastic Kubernetes Service (Amazon EKS), AWS Fargate and AWS Lambda. Organizations that need to enable runtime visibility into their Amazon EC2 instances can use CrowdStrike’s System State Manager distributor package to dynamically deploy their agents across thousands of Amazon EC2 instances.
The distributor package leverages CrowdStrike APIs to dynamically authorize every agent installation while building the package for delivery to an Amazon EC2 instance. In addition, organizations can use predefined policies and agent versions via their CrowdStrike Falcon® console. Building the package during distribution and installation enables organizations to avoid multiple versions of installation scripts (e.g., a different script for each operating system).
Finally, using a combination of AWS Systems Manager and AWS Config, organizations are able to audit compliance of their workloads for the presence of the CrowdStrike Falcon® agent and take action by sending non-compliant events to AWS Security Hub. Because AWS Security Hub natively integrates with AWS Config, it can trigger an automated System State Manager document to install the Falcon agent on the non-compliant resource.
Automated Remediation Scales Security Teams
Security teams are overwhelmed with alerts and false positives and can only respond to a fraction of the potential events detected each day. While configuration assessments, runtime visibility and correlation across those can provide effective preventative controls, organizations must be able to understand and effectively act on a security event. With multiple tools monitoring their environments, a centralized location to view events allows organizations to kick off remediation workflows while taking into context all of the associated anomalous activity.
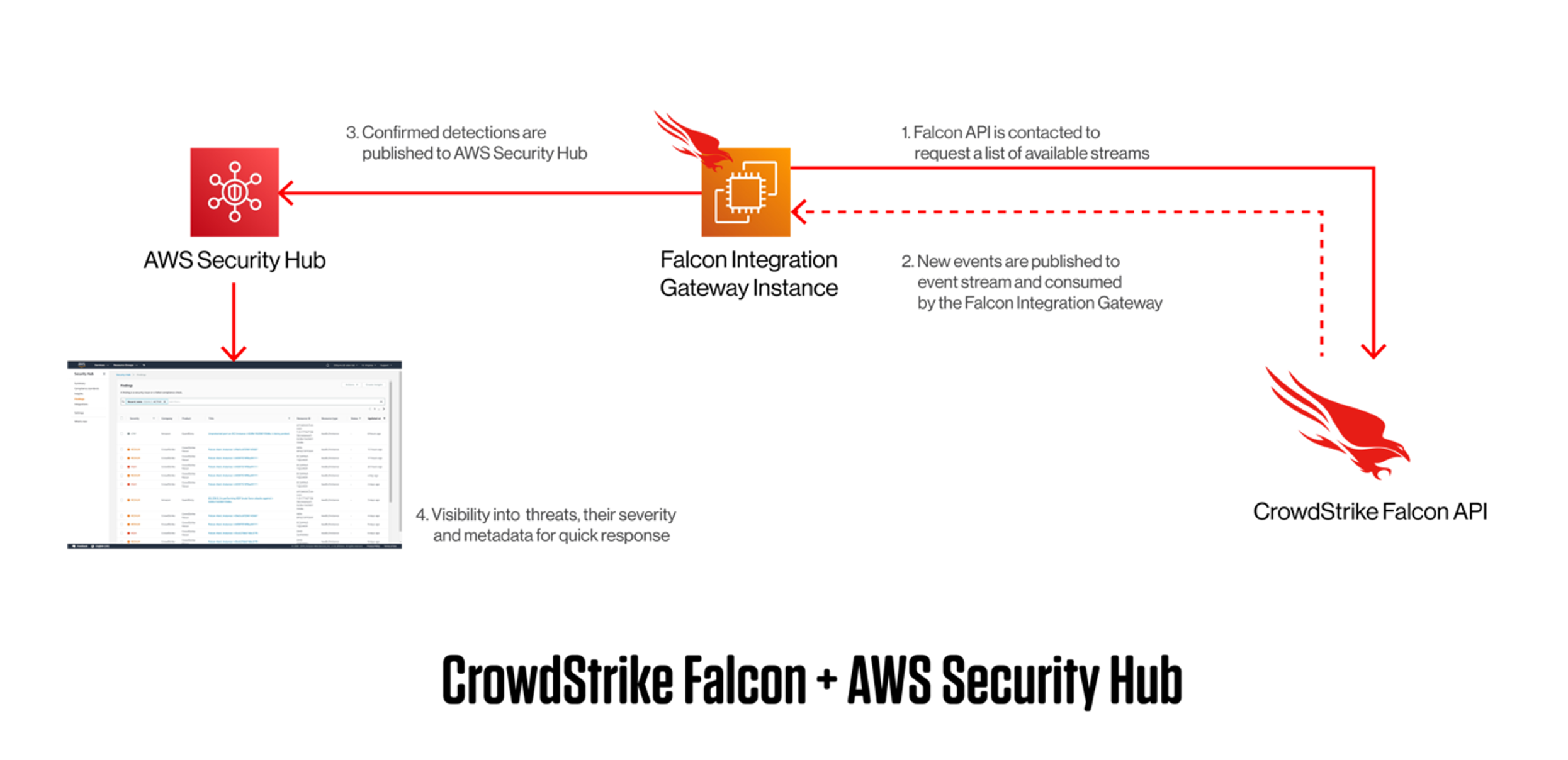
To reduce their operational burden, security teams should consider a mechanism to aggregate security events across all accounts and then deploy automated runbooks to solve for common non-compliant configurations and low-risk events. AWS Security Hub allows organizations to centralize security events across AWS and third-party tools in a common finding format called Amazon Security Finding Format (ASFF). This allows organizations to easily understand the resource, type of event, normalized severity levels and the reporting tool so they can hook in automated remediation frameworks.
To view security events detected during runtime, CrowdStrike provides the Falcon Integration Gateway — a containerized application that resides within an AWS account and polls the CrowdStrike streaming API for security events, converts them to ASFF and publishes it to AWS Security Hub.
- VPC-level automation: AWS Network Firewall protects the VPC level against network-based attacks, while a combination of stateless and stateful rules can guard against various attack vectors. One common control is limiting the domains or IP addresses a workload has access to, either inbound or outbound. However, organizations need to subscribe to the right threat intelligence feeds to block the latest set of IPs or domains that adversaries use for reconnaissance and to launch their exploits.
- Host-level automation: The CrowdStrike Falcon® agent protects at the host level where the agent can detect network activity by monitoring system calls to open new sockets. This intelligence can be extended by monitoring host-based activity and generating stateful rules for AWS Network Firewall, allowing organizations to use CrowdStrike threat intelligence across assets that may not have Falcon agents on them. The Falcon Integration Gateway enables this workflow by pushing a high-risk event into AWS Security Hub. Organizations can then trigger a remediation workflow, which is automated or manual based on Amazon EventBridge rules, allowing an AWS Lambda function to create a stateful AWS Network Firewall rule to block the specific domain or IP that is considered malicious.
Conclusion
Workload protection requires a tight integration between security solutions and services to provide end-to-end visibility and the ability to defend against threats wherever they are — from the network edge to the cloud and across endpoints and workloads. The CrowdStrike Falcon® platform operates in concert with AWS services such as AWS CloudTrail, VPC Flow Logs, Amazon EventBridge, AWS Control Tower, AWS Lambda and AWS Security Hub to apply defense-in-depth.
With an integrated security solution, organizations gain visibility and event correlation across their AWS accounts, inventory and configuration settings and runtime activity to provide actionable security events and a framework to centralize logging of security events, prevent cloud threats and automate remediation workflows for a true cloud-to-edge defense strategy.
Try It Yourself
You can access CrowdStrike to experience how the defense-in-depth principles come together to mitigate and remediate threats. Attend a CrowdStrike Dev Days session where you can set up the attack using Capture the Flag challenges to understand how it will succeed. Learn how to install CrowdStrike agents and use AWS services to address the different aspects of the attack. Learn more and register here.
Additional Resources
- Learn more about how the CrowdStrike Falcon® platform delivers end-to-end protection for workloads and containers on AWS, from the host to the cloud and everywhere in between.
- Watch this video to see how the CrowdStrike and AWS Shared Responsibility Model provides industry-leading breach protection and cloud security.
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.
- Visit CrowdStrike on the AWS Marketplace.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)