Nowhere to Hide: Detecting a Vishing Intrusion at a Retail Company

The CrowdStrike Falcon OverWatch™ 2021 Threat Hunting Report details the interactive intrusion activity observed by hunters from July 2020 to June 2021. While the report brings to light some of the new and innovative ways threat actors are gaining access into victim organization’s networks, social engineering remains a tried and true method of gaining access to victim environments. The following case study from the report examines an intrusion at a North America-based retail company in which an employee unwittingly gave an eCrime adversary remote access to all hosts at the store.
Vishing Reels in Another Catch
After receiving a call from an individual claiming to be a technical support provider for the retailer’s point-of-sale (POS) vendor, a North America-based retail employee did what many employees would do: followed the instructions from the caller to download a legitimate remote access tool to all hosts at the store. Unfortunately, the person on the other end of the call was not technical support but a motivated eCrime adversary intent on financial gain.
Spear-phishing via service (learn more) is distinct from regular phishing, as it is delivered outside of enterprise email channels. In this particular intrusion, the adversary employed vishing (or voice phishing) to seek the victim’s cooperation over the phone. Vishing requires adversaries to research their targets in advance and learn how the target organization communicates with outside parties. Adversaries use this research to create personally tailored messages that can deceive employees and convince them to act in the adversary’s interests.
Because of the ubiquity of security solutions focused on the email phishing threat, delivering a successful phishing email is becoming more challenging. By researching their targeted victims in advance and circumventing email by opting for phone calls, adversaries increase their ability to bypass security controls, while simultaneously increasing their chances of successful compromise through the manipulation of unsuspecting employees.
Augmenting Technology with Human Ingenuity
The adversary in this intrusion used a legitimate remote access tool in a likely attempt to blend in with normal activity. While the activity was initiated from a valid account and leveraged legitimate remote access software, OverWatch’s continuous threat hunting caught the first sign of potentially malicious post-exploitation behavior and alerted the victim organization.
The first clue OverWatch threat hunters found was when the adversary wrote both low-prevalence and known suspicious tools to the host after gaining access. By using the CrowdStrike Threat Graph® database to correlate the same indicators from the same account across multiple hosts, a picture of potential lateral movement began to emerge.
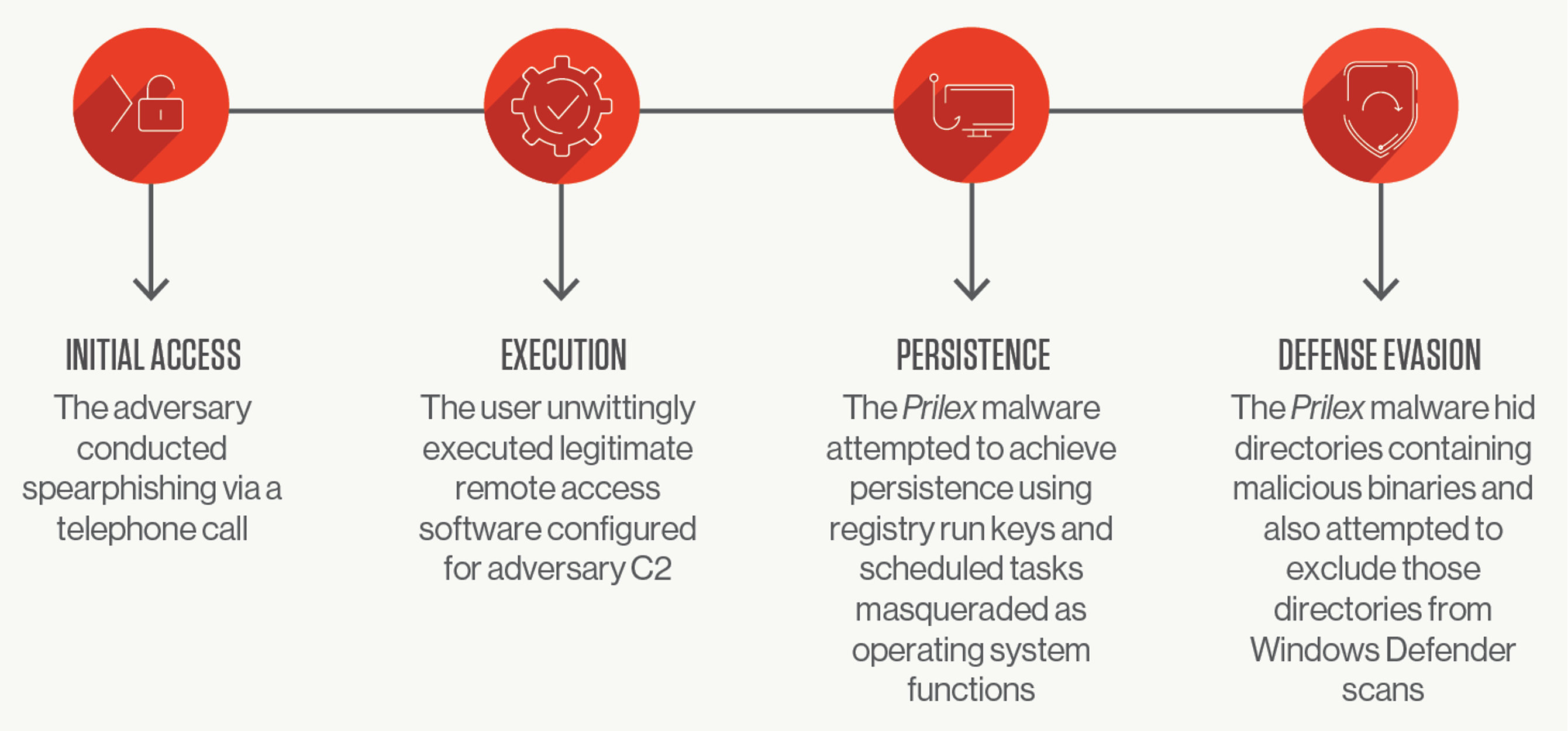
The OverWatch hunters’ suspicions were confirmed when the adversary attempted to establish persistence for their tools by scheduling individual tasks to execute each binary at system startup. The OverWatch team derived further context from the adversary’s attempts to avoid detection by naming each task to masquerade as a legitimate Microsoft update service.
The adversary also attempted to exclude Prilex malware directories from Windows Defender scans using PowerShell’s Set-MpPreference cmdlet. This suggests an intent for long-term collection operations without interruption. If not for the actions taken by the OverWatch team, the victim organization could have had an undetected eCrime actor embedded in its environment for an extended period.
Conclusions and Recommendations
User-enabled intrusions allow an adversary to bypass some tactics in the MITRE ATT&CK® matrix. This can pose a challenge to autonomous technology-based defenses. However, diligent threat hunters equipped with extensive telemetry and knowledge of adversary tactics, techniques and procedures (TTPs) can readily identify evidence of adversaries’ presence, even as they try to evade defenses.
To prevent intrusions such as this one in your environment, organizations should limit and audit the use of remote access tools. The use of legitimate, non-native remote access tools appeared in about 5% of eCrime intrusion attempts observed by OverWatch from July 2020 to June 2021. System administrators can restrict and audit the use of such tools in their environment, even for authorized use cases.
Additional Resources
- Read the 2021 Threat Hunting Report blog or download the report now.
- Learn more about Falcon OverWatch’s proactive managed threat hunting.
- Discover the power of tailored threat hunting OverWatch Elite provides customers in this blog post.
- Watch how Falcon OverWatch proactively hunts for threats in your environment.
- Read more about how part-time threat hunting is simply not enough in this blog post.
- Learn more about the CrowdStrike Falcon®® platform.

