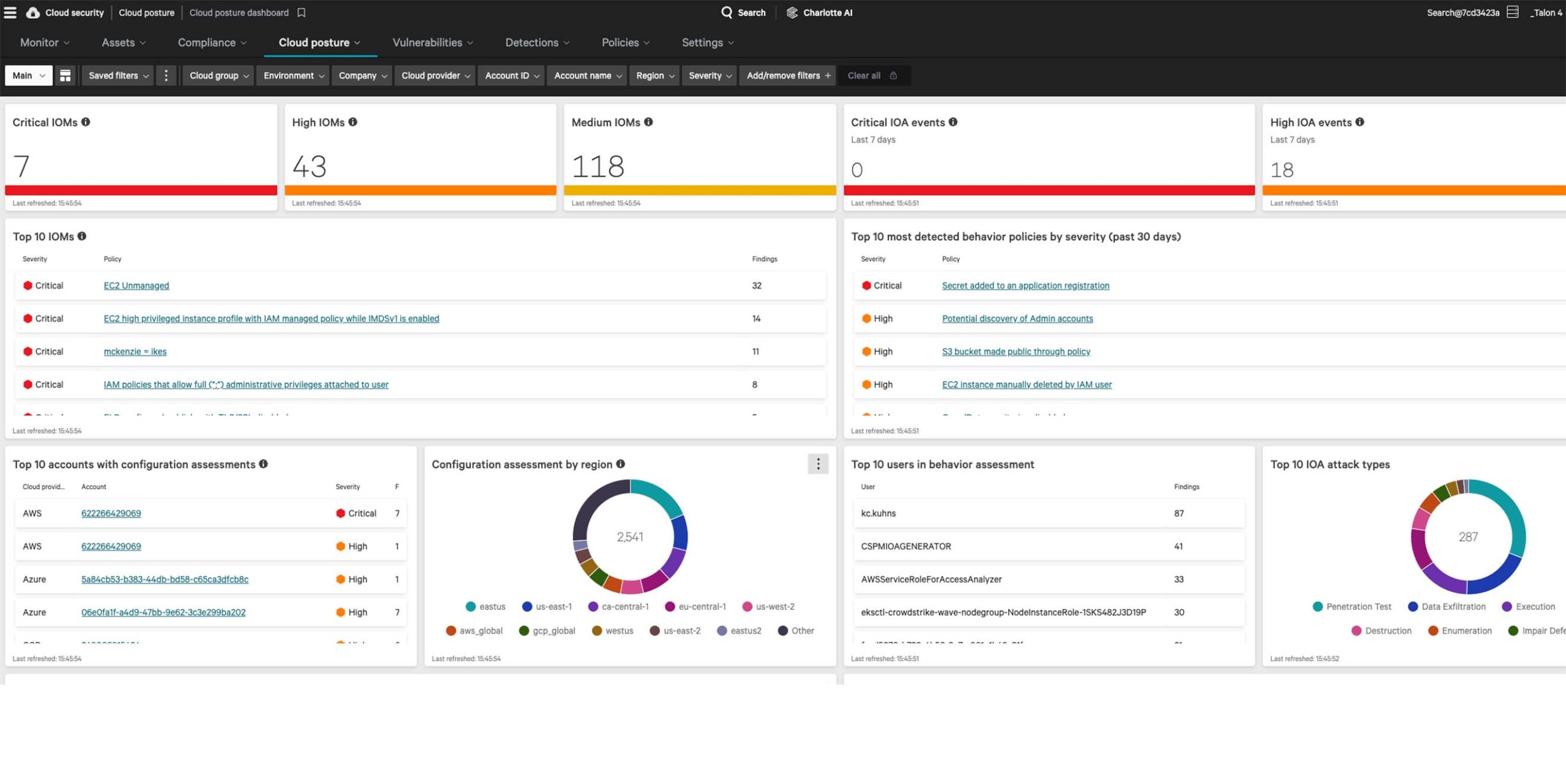
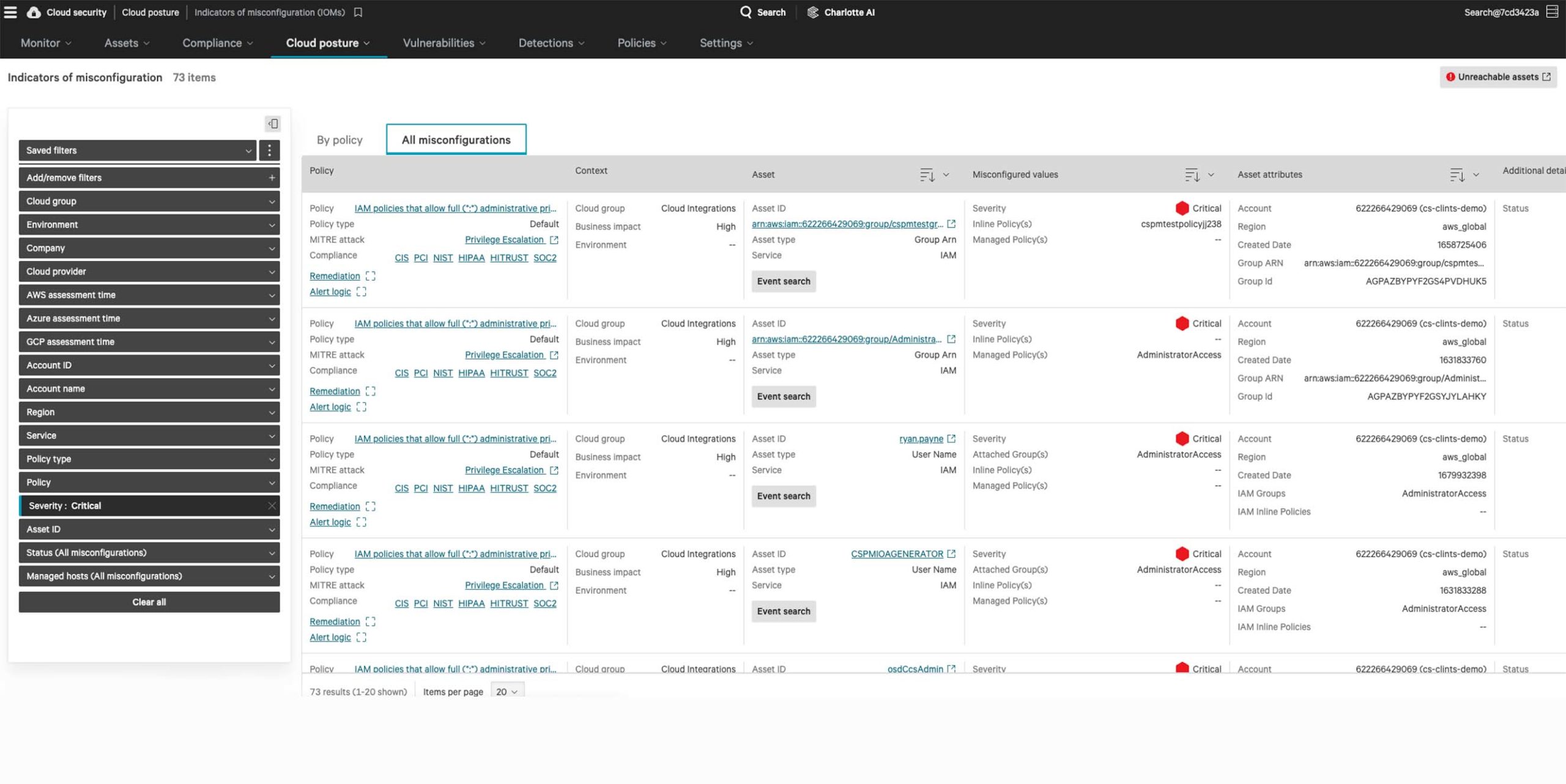
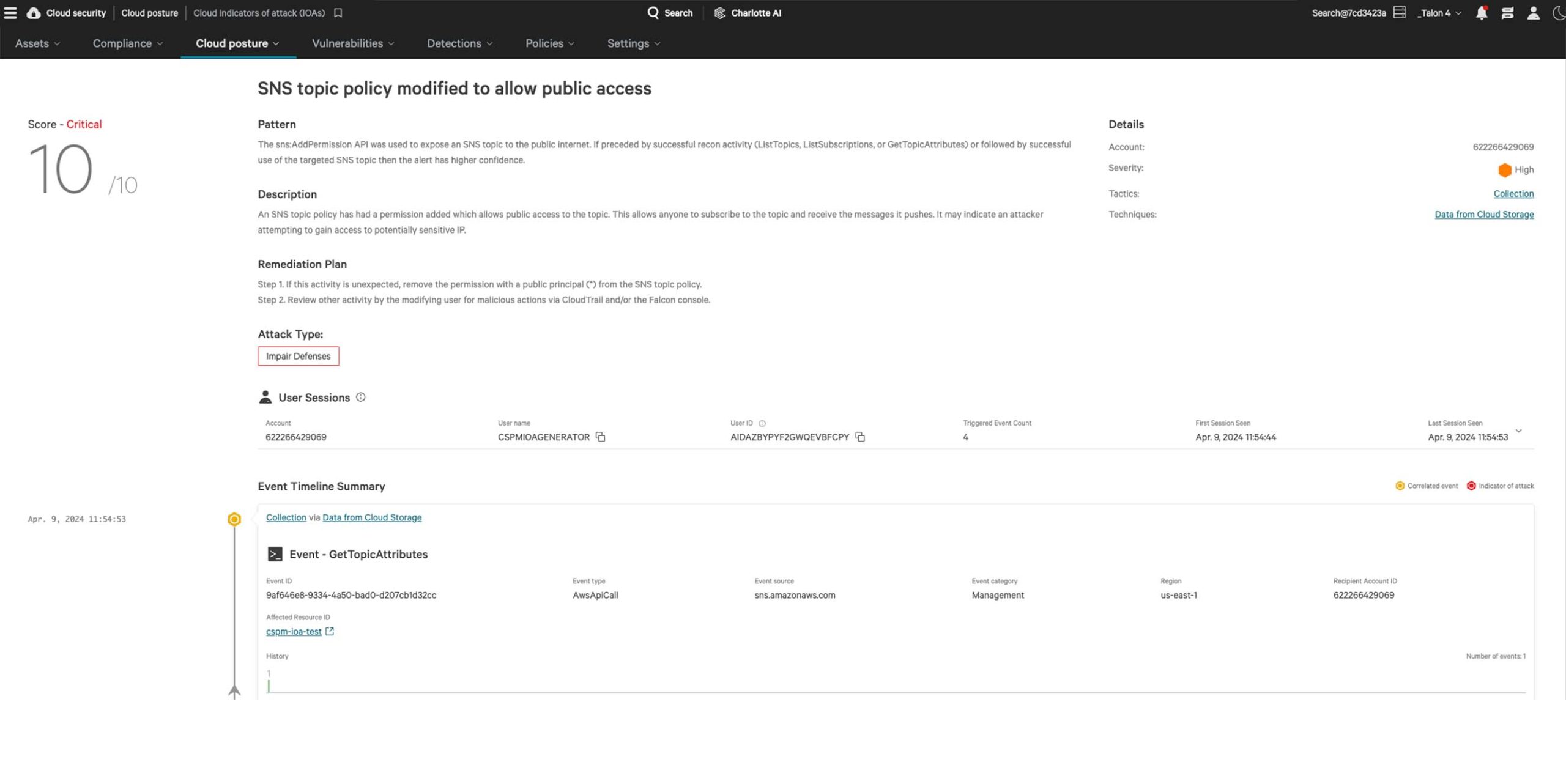
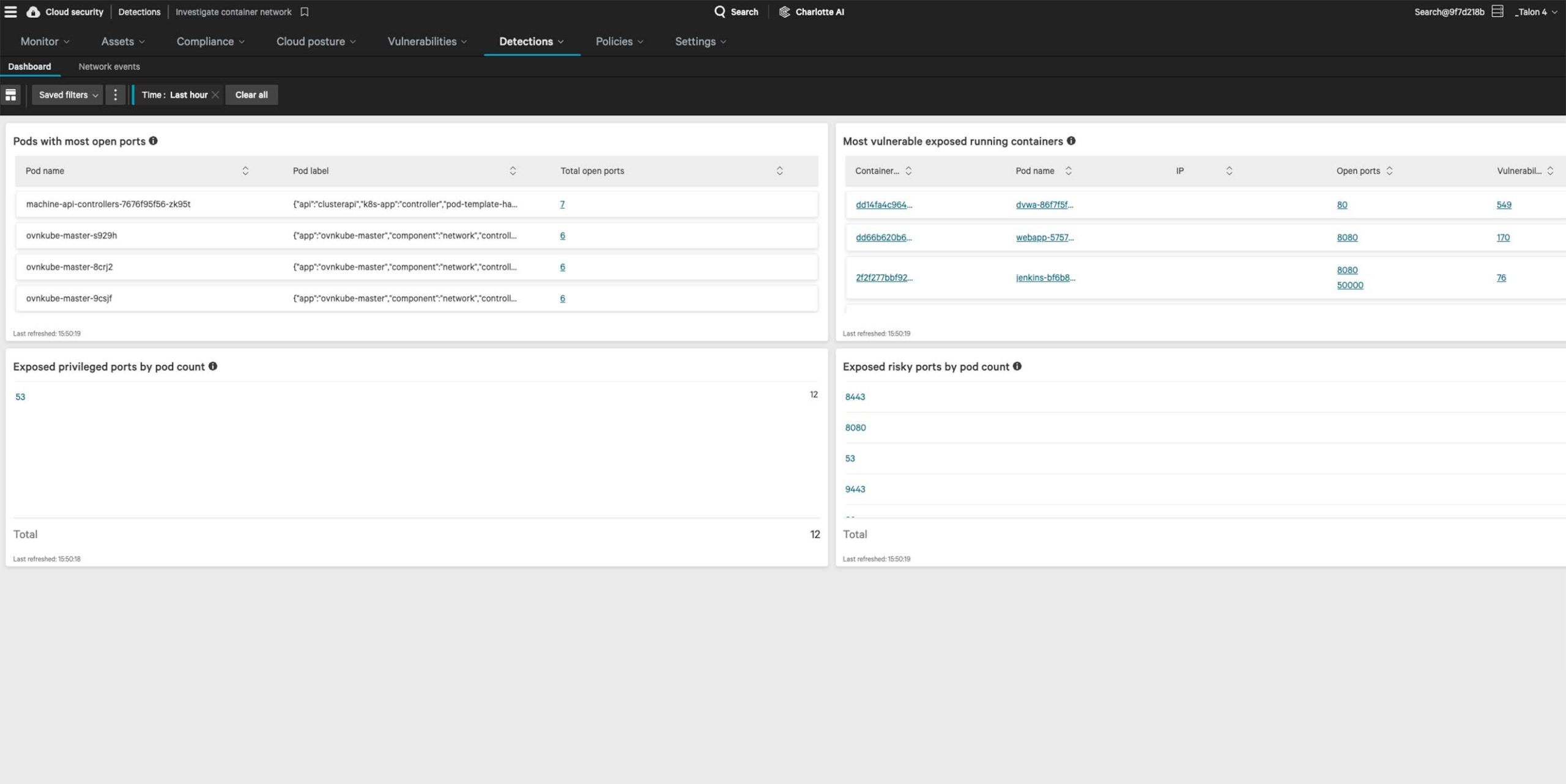
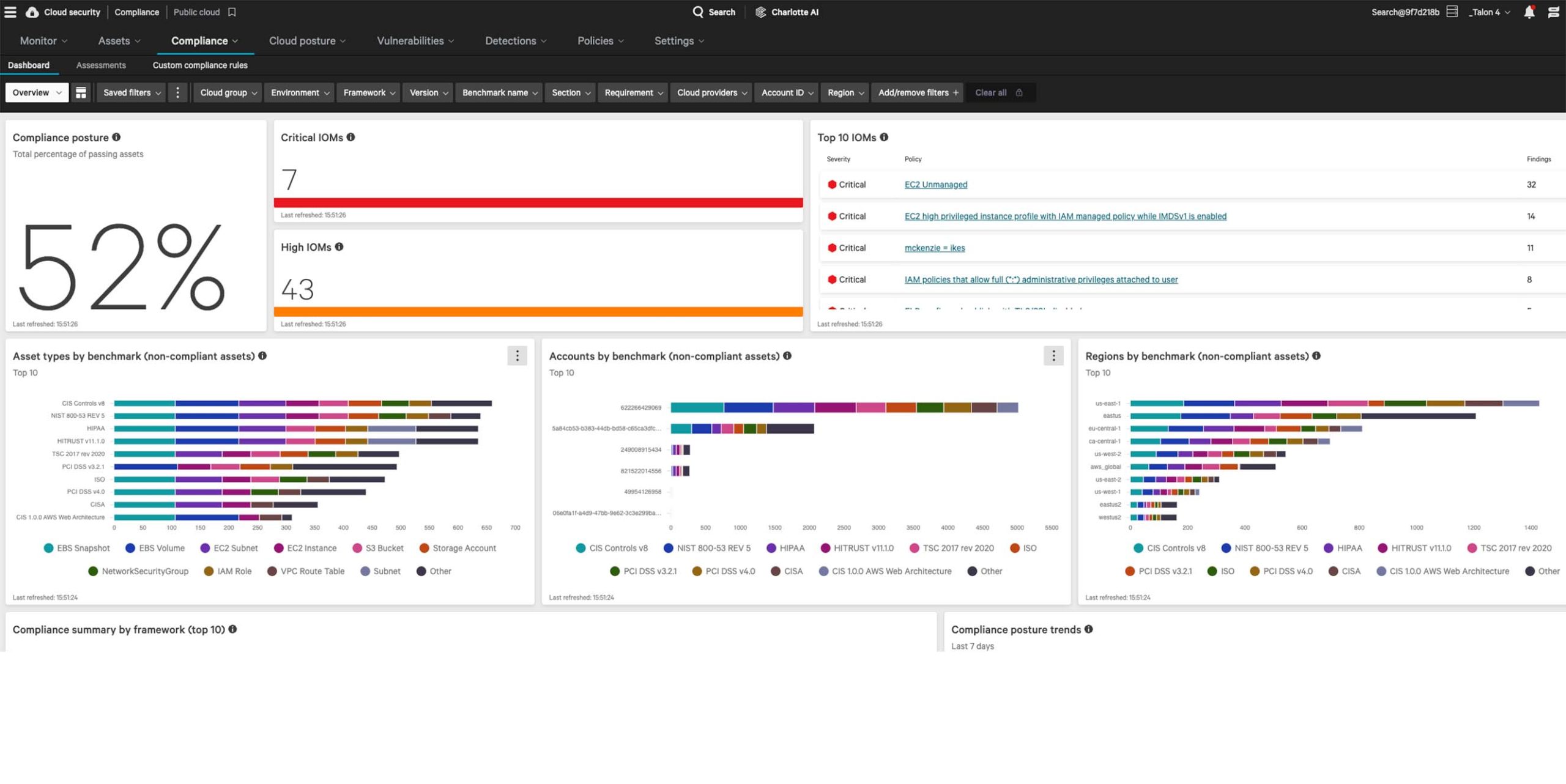
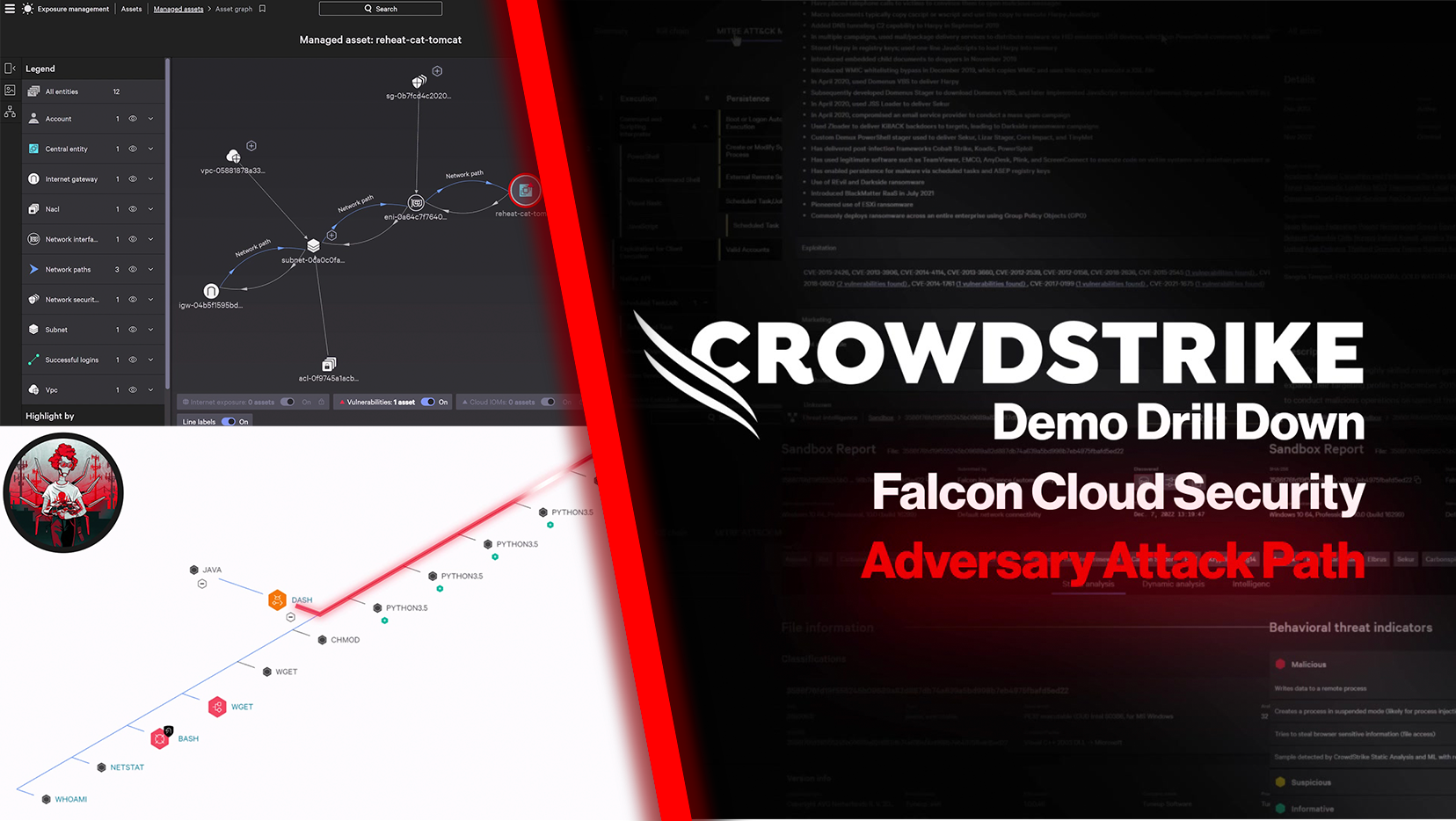
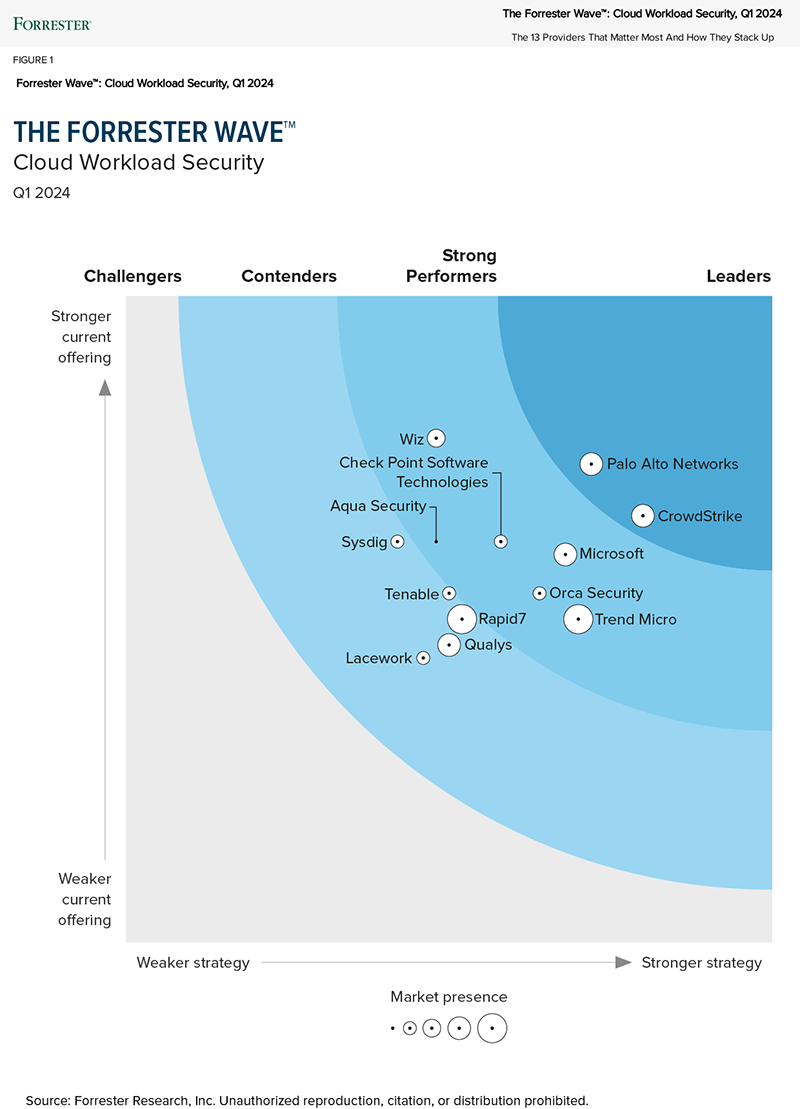
Complete visibility, everywhere
Falcon Cloud Security delivers a unified view of your cloud security posture across multi-cloud environments. Continuous agentless discovery visualizes your cloud-native assets, providing the right context for fast decisions.