Achieve 89% faster cloud detection and response
Harness the power of real-time prevention and industry-leading cloud detection and response to speed threat mitigation.
CrowdStrike Falcon® Cloud Security
Definitive protection for everything you build and run in the cloud.
Download the Complete Guide to CNAPPs ebook
Download nowUnleash speed, savings, and seamless integration for unparalleled protection in the cloud.
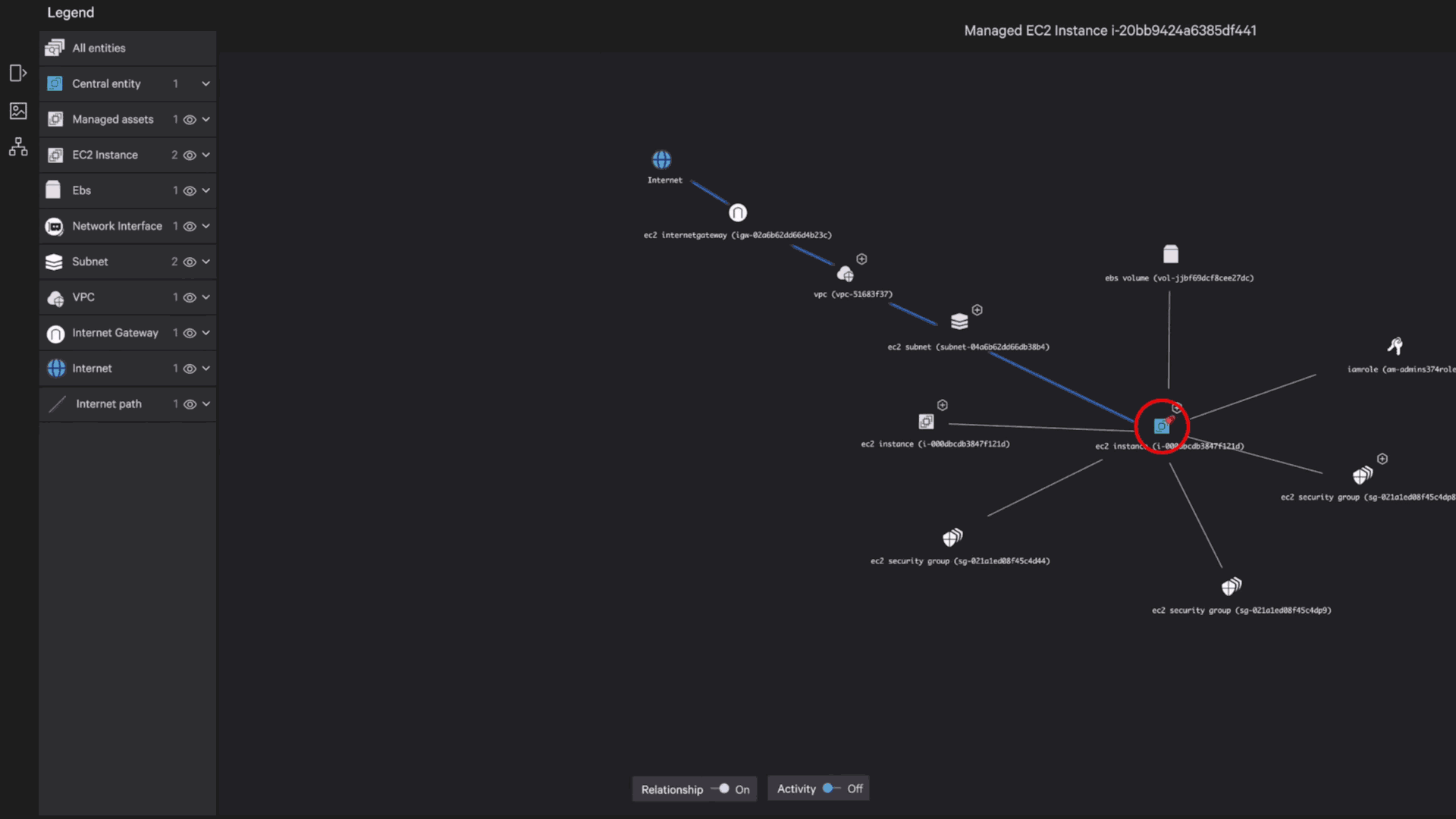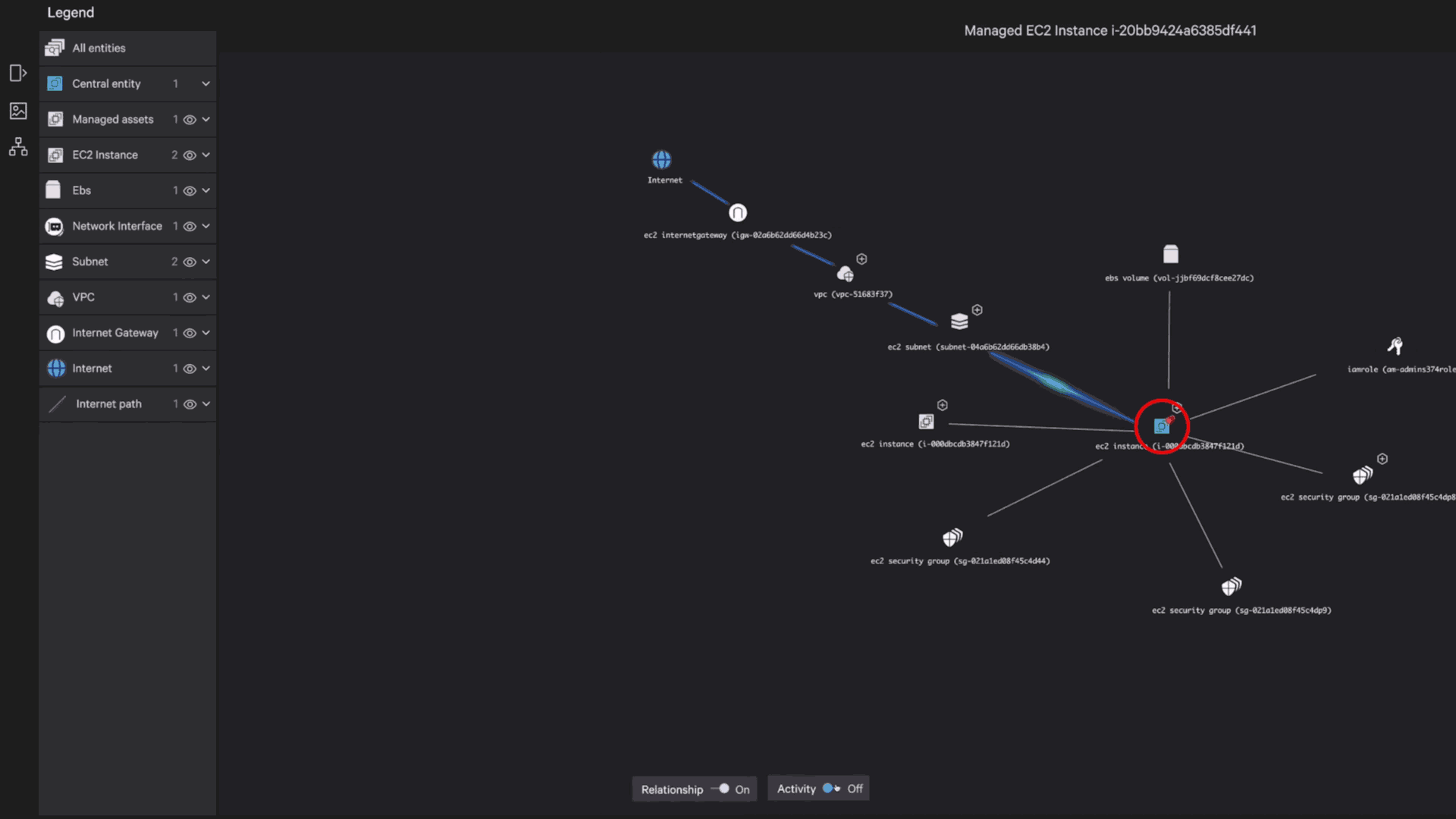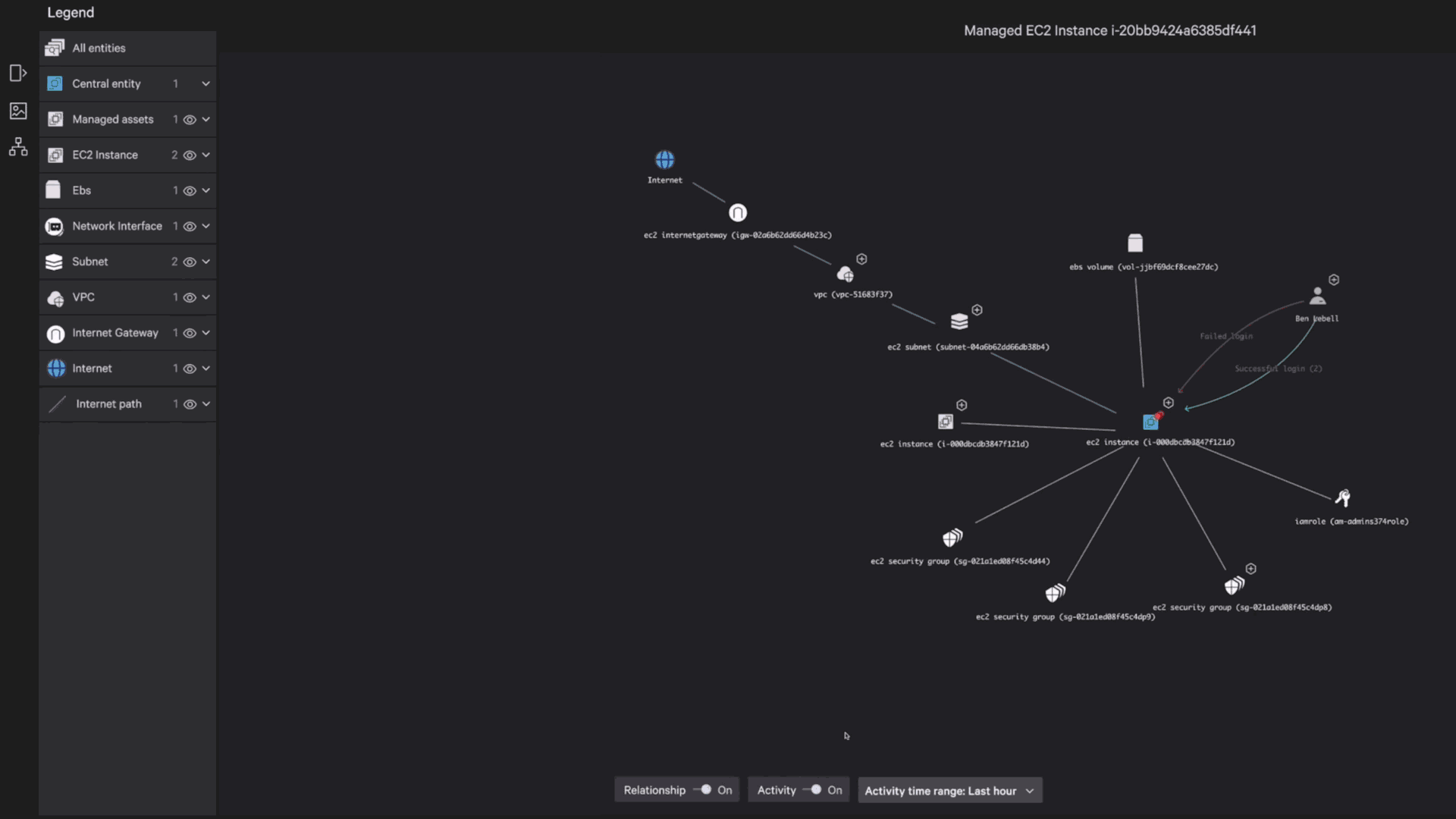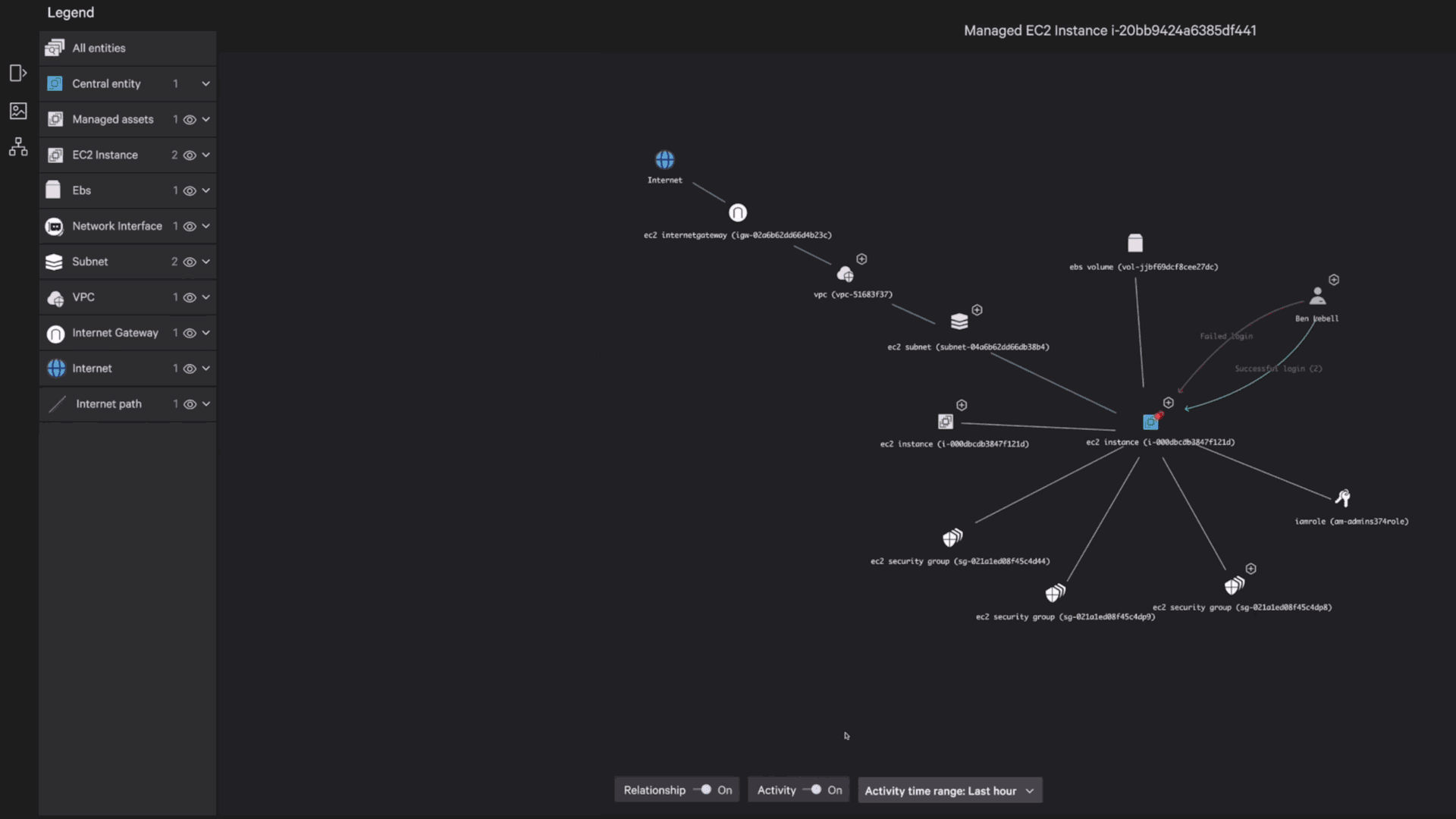
Recognized for our advanced, strategic approach to cloud security with the highest score of all vendors in Strategy.

Discover how CrowdStrike’s advanced protection can secure your cloud environment. No strings, no hassle.
Start interactive demo