CrowdStrike vs. Palo Alto Networks
Fatigue doesn’t win. A single platform does. Don’t settle for a high-cost platform that’s hard to use and hard to deploy.
Fatigue can’t stop cyberattacks.
But we can.
 Palo Alto Networks Disjointed products that slow critical investigations
Palo Alto Networks Disjointed products that slow critical investigations
-
×3+ separate consoles across Cortex and Prisma Cloud, fragmenting SOC workflows
-
×Requires analysts to manage multiple, disjointed UIs during investigations
-
×"Requires a steep learning curve and may be less suitable for lean security teams and those pursuing ease of use", according to Gartner
The CrowdStrike difference
CrowdStrike A single console that powers unparalleled SOC efficiency
CrowdStrike's single console consolidates endpoint, cloud, identity, data protection, IT automation, NG-SIEM, exposure management, and more, enhancing SOC operations by automatically correlating data across CrowdStrike’s unified platform. The result? Faster detection and response.
66 %
Faster investigations1
2 x
More effective security teams1
66 %
Faster investigations1
2 x
More effective security teams1
66 %
Faster investigations1
2 x
More effective security teams1
66 %
Faster investigations1
2 x
More effective security teams1
66 %
Faster investigations1
2 x
More effective security teams1
 Palo Alto Networks Hard to deploy, hard to maintain
Palo Alto Networks Hard to deploy, hard to maintain
-
×3 separate agents required for full platform functionality
-
×Requires constant manual tuning and configuration across modules
The CrowdStrike difference
CrowdStrike Rapid deployment, streamlined operations
CrowdStrike simplifies operations with a single, lightweight agent that deploys all platform modules. It’s easy to maintain, saving customers valuable time and resources, and eliminating the need for manual configuration and tuning.
Customer assessment
100kAgents deployed in less than 24 hours2.
 Palo Alto Networks Excessive TCO
Palo Alto Networks Excessive TCO
-
×Burdensome operations significantly increase total cost of ownership (TCO)
-
×Complex point products raise training costs
-
×Prolonged professional services commitments trap customers in overlapping vendor contracts
The CrowdStrike difference
CrowdStrike Unmatched ROI
CrowdStrike’s single console, single agent architecture simplifies operations and provides an unmatched ROI, freeing up your time and resources. Our intuitive modules also cut down training expenses, and rapid deployment eases the shift from outdated systems—avoiding costly contract overlaps.
$6
Of return for every $1 invested.
 Compare
Compare
 Empty heading
Empty heading
Palo Alto Networks
Platform
 Single, unified console powers consolidation
Single, unified console powers consolidation
CrowdStrike’s single console, single agent architecture enables rapid deployment of all platform modules and accelerates investigations through a unified, easy-to-use UI.
 Multiple consoles, multiple agents
Multiple consoles, multiple agents
Palo Alto Networks’ fragmented platform is spread over three disjointed consoles. It also requires three different agents for full platform functionality, lengthening deployment time and hindering SOC effectiveness.
Endpoint Security
 Designed for modern endpoint security
Designed for modern endpoint security
CrowdStrike was named a “Leader” for the fifth consecutive time in the latest Gartner MQ for Endpoint Protection Platforms and positioned best on both axes. Our single lightweight agent streamlines deployment and operations, ensuring no performance impacts.
 Poor architecture prevents effective endpoint security
Poor architecture prevents effective endpoint security
Palo Alto Networks' flawed architecture compromises endpoint security. The Cortex agent's high RAM and disk usage also slows down endpoints.
Identity Protection
 Leading AI-powered identity threat protection
Leading AI-powered identity threat protection
CrowdStrike detects identity attacks 85% faster with an anomaly detection engine that analyzes live traffic against behavior baselines and policies. It offers real-time threat prevention, including MFA enforcement and password resets, all through a unified agent.
 Identity protection that can’t stop attacks
Identity protection that can’t stop attacks
Palo Alto Network’s Identity Threat Module is limited to detection without out-of-the-box blocking capabilities, missing essential responses such as risk-based access controls and step-up MFA for legacy apps. It also requires a complex setup involving a separate cloud identity engine and agent.
Cloud Security
 Pre-built cloud detections and automated alert correlation
Pre-built cloud detections and automated alert correlation
CrowdStrike Falcon® Cloud Security delivers pre-built runtime detections, on-sensor machine learning, and integrated threat intelligence. SOC analysts gain superior initial detections and alert context via a unified console with other CrowdStrike modules, boosting protection and speeding up investigations.
 Cloud security that struggles out of the box
Cloud security that struggles out of the box
Prisma Cloud relies on static behavioral baselines for detection, leaving customers vulnerable to breach for 24 hours after any new workload is deployed. Customers need to manually tune baselines to weed out false positives and false negatives.
SIEM
 Unmatched speed and performance at a better cost
Unmatched speed and performance at a better cost
Designed for the modern SOC, CrowdStrike Falcon® Next-Gen SIEM delivers breach prevention with real-time alerts, rapid search capabilities, and elite threat intelligence. CrowdStrike processes petabytes of data with sub-second latency, all more cost-effectively than rival SIEM solutions.
 XSIAM can’t effectively address SIEM use cases
XSIAM can’t effectively address SIEM use cases
XSIAM struggles to address traditional SIEM use cases with slow search speeds, limited data visualization, and an arduous onboarding process. Their “automation” is nothing more than standard SOAR playbooks that require extensive manual configuration or expensive professional services.
Managed Detection and Response
 Industry-leading managed detection and response
Industry-leading managed detection and response
CrowdStrike is the #1 leader in MDR by market share (Gartner). Our service delivers end-to-end response across endpoint, identity, and cloud to conclusively remediate attacks, with zero customer handoffs that waste time or increase risk. CrowdStrike provides the most comprehensive detection coverage and delivers the fastest threat detection.
 Incomplete MDR leaves you with homework
Incomplete MDR leaves you with homework
Palo Alto Networks’ MDR only offers basic remediation through standard agent actions unless licensed for costly IR hours, putting the burden on the customer to fully mitigate attacks. Any remediation beyond basic endpoint response is limited to guidance, not action. Palo Alto Networks’ MDR also can’t respond to identity-based threats.
Threat Intelligence
 Global leader in threat intelligence
Global leader in threat intelligence
Fully integrated, world-class threat intelligence enables SOC analysts to do their jobs faster and more effectively. Leverage a list of recently published IOCs, adversary attribution, and an automated malware sandbox, all within a single user interface. 257 adversaries tracked, 200,000 new IOCs published per day.
 Ineffective threat intel provides little context to analysts
Ineffective threat intel provides little context to analysts
Palo Alto Networks’ threat intel lacks adversary profiles, and fails to provide meaningful alert context to SOC analysts. Even with Autofocus, customers receive basic adversary attribution without comprehensive adversary information, hindering SOC analyst investigations and productivity.
Data Protection
 A modern approach to stop data theft
A modern approach to stop data theft
Built on CrowdStrike’s single unified agent, Falcon Data Protection reliably detects and prevents the movement of sensitive data by combining both content and context across endpoints, identities, data, and egress channels.
 Network-based data protection creates visibility gaps
Network-based data protection creates visibility gaps
Palo Alto Networks' data loss prevention technology is network-based only, with no ability to reliably detect and prevent sensitive data egress from endpoints, particularly for endpoints not connected to corporate networks.
Total Cost of Ownership (TCO)
 Cost effective
Cost effective
CrowdStrike's single-agent platform minimizes deployment and maintenance costs, dramatically reducing TCO.
 High TCO
High TCO
Palo Alto Networks' fragmented platform requires multiple disjointed consoles and agents, complicating deployment and increasing operational overhead, leading to a higher TCO.
 Validated by industry leading analysts
Validated by industry leading analysts
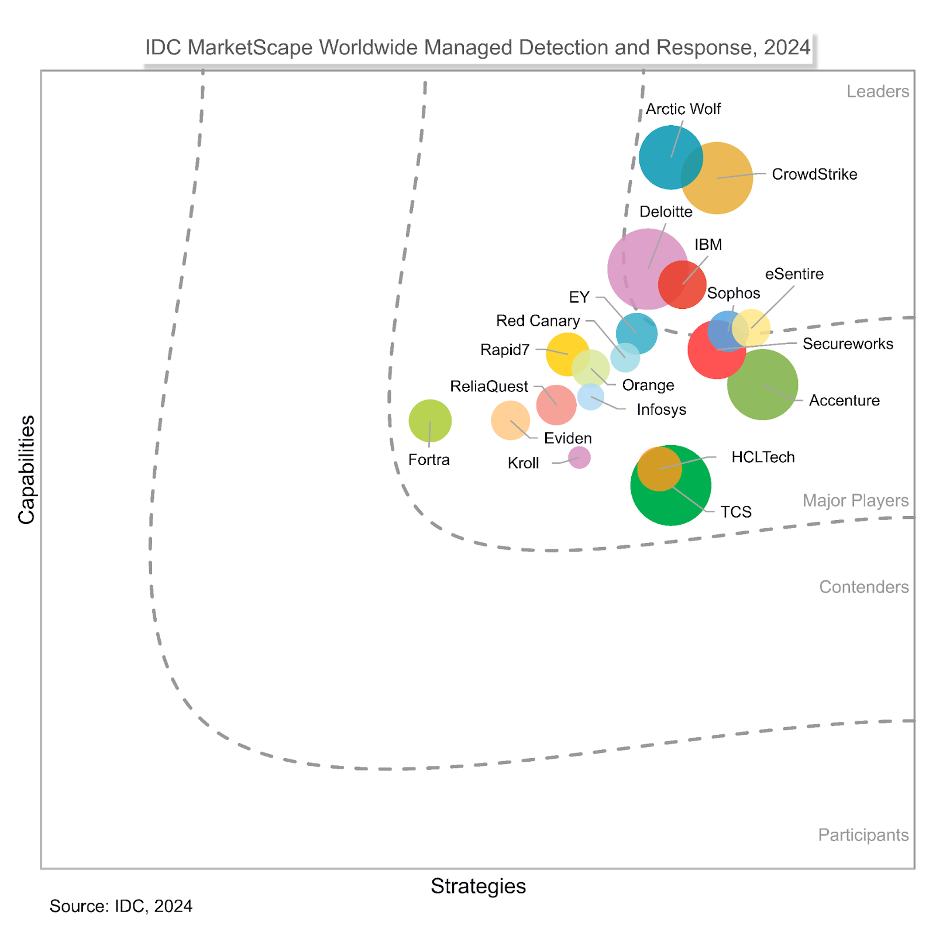
Leader in IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
CrowdStrike named one of only four “Leaders”.

Leader in Magic Quadrant for Endpoint Protection Platforms
CrowdStrike is positioned highest for ability to execute and furthest to the right for completeness of vision.
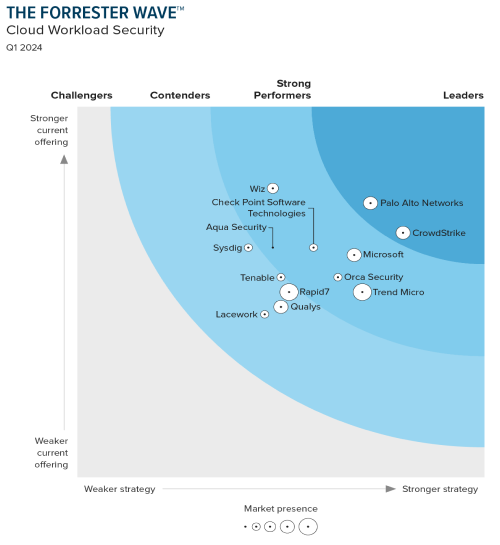
Leader in Forrester Wave: Cloud Workload Security
CrowdStrike is rated as having the strongest strategy of all vendors.
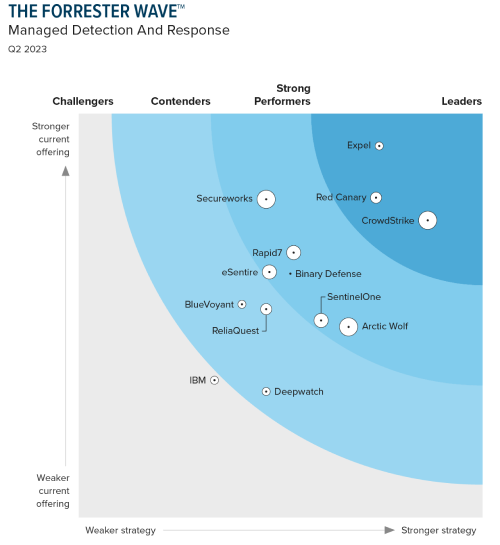
Leader in Forrester Wave: Managed Detection and Response
CrowdStrike is rated as having the strongest strategy of all vendors.
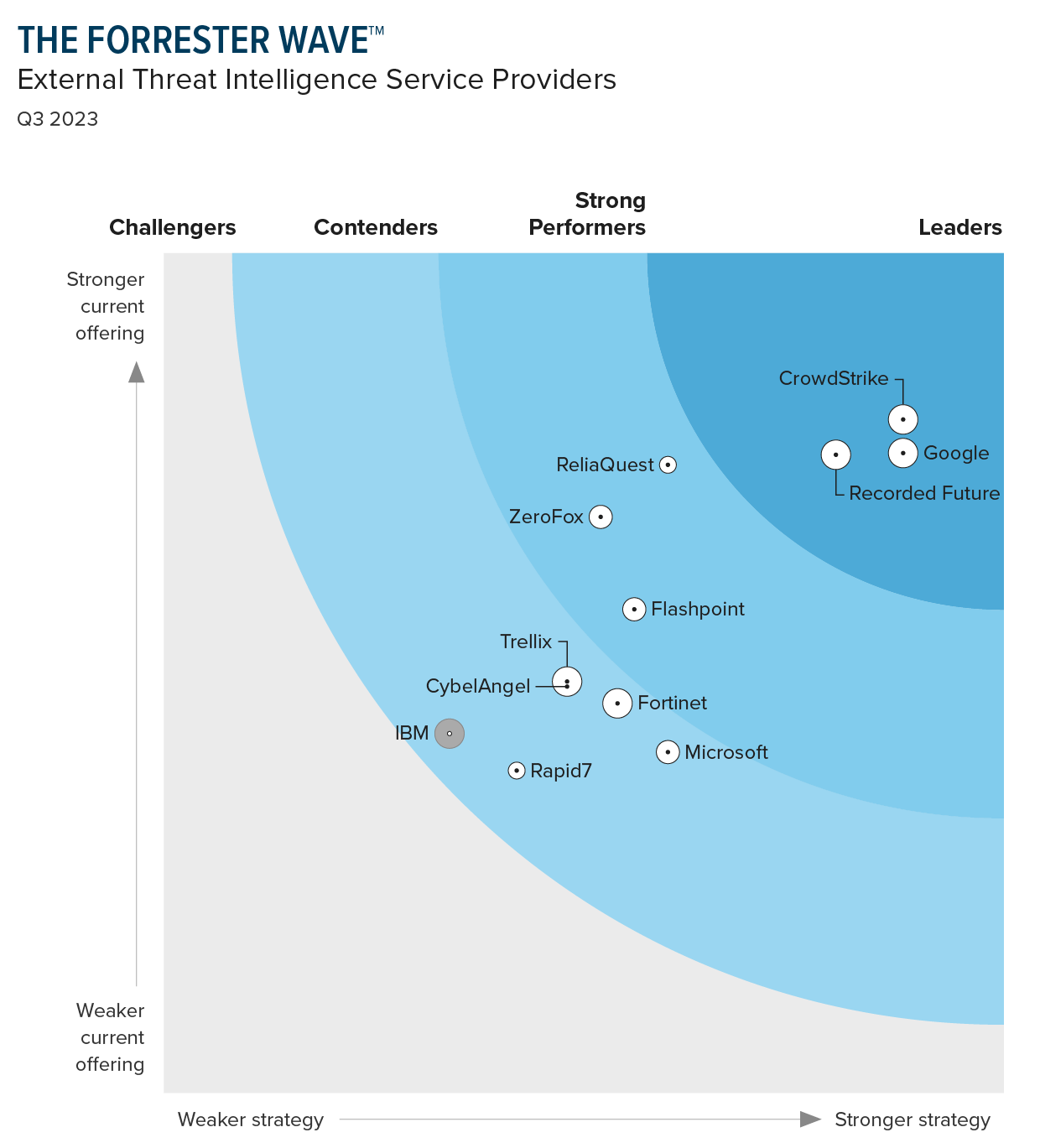
Leader in Forrester Wave: External Threat Intelligence Service Providers
CrowdStrike positioned highest for current offering and furthest for strategy.

Leader in IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
CrowdStrike named one of only four “Leaders”.

Leader in Magic Quadrant for Endpoint Protection Platforms
CrowdStrike is positioned highest for ability to execute and furthest to the right for completeness of vision.

Leader in Forrester Wave: Cloud Workload Security
CrowdStrike is rated as having the strongest strategy of all vendors.

Leader in Forrester Wave: Managed Detection and Response
CrowdStrike is rated as having the strongest strategy of all vendors.

Leader in Forrester Wave: External Threat Intelligence Service Providers
CrowdStrike positioned highest for current offering and furthest for strategy.

Leader in IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
CrowdStrike named one of only four “Leaders”.

Leader in Magic Quadrant for Endpoint Protection Platforms
CrowdStrike is positioned highest for ability to execute and furthest to the right for completeness of vision.

Leader in Forrester Wave: Cloud Workload Security
CrowdStrike is rated as having the strongest strategy of all vendors.

Leader in Forrester Wave: Managed Detection and Response
CrowdStrike is rated as having the strongest strategy of all vendors.

Leader in Forrester Wave: External Threat Intelligence Service Providers
CrowdStrike positioned highest for current offering and furthest for strategy.

Leader in IDC MarketScape: Worldwide Risk-Based Vulnerability Management Platforms 2023 Vendor Assessment
CrowdStrike named one of only four “Leaders”.

Leader in Magic Quadrant for Endpoint Protection Platforms
CrowdStrike is positioned highest for ability to execute and furthest to the right for completeness of vision.
 See what our customers think
See what our customers think
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
CrowdStrike Falcon has been amazing! Not only is the application extremely lightweight, but it also catches all anomalous activity and can immediately stop it.
The Falcon platform has allowed us to consolidate our security toolbox. It yields big savings for us, but more importantly, it allows us to focus. When an alert hits from the Falcon platform, we’re able to address it without being distracted by other tools

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon Cloud Security is an awesome tool with great capabilities, it offers easy to use interface where administrator can do monitoring and do the policy configuration.
Falcon Complete is amazing for smaller Security Teams that need enterprise class endpoint protection.
CrowdStrike has built a very powerful combination of modules that cover a broad swath of the cyber security mission, especially as it relates to endpoint. While no security tool is a silver bullet, Falcon does a great job of tackling some of the most prevalent and impactful challenges in defending endpoints.
CrowdStrike Falcon has been amazing! Not only is the application extremely lightweight, but it also catches all anomalous activity and can immediately stop it.
The Falcon platform has allowed us to consolidate our security toolbox. It yields big savings for us, but more importantly, it allows us to focus. When an alert hits from the Falcon platform, we’re able to address it without being distracted by other tools

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
CrowdStrike is the next level security for cyber protection offering the best protection and innovative software.
The best feature of CrowdStrike Falcon is that it is very easy to use and manage and works in offline mode also and the product implementation was very easy and the customer support was also helpful.
I have been in the industry for close to thirty years and this has been one of the best endpoint protection programs I have ever used. We feel confident as an organization that we are protected on the endpoints at all times. The Falcon Complete team is great for providing assistance whenever we need it.
CrowdStrike Falcon Cloud Security addresses critical cybersecurity challenges by providing real-time threat detection, rapid response capabilities, and seamless integration. This proactive approach enhances our overall security posture, safeguarding digital assets and ensuring a robust defense against evolving threats.
CrowdStrike Falcon has been amazing! Not only is the application extremely lightweight, but it also catches all anomalous activity and can immediately stop it.
The Falcon platform has allowed us to consolidate our security toolbox. It yields big savings for us, but more importantly, it allows us to focus. When an alert hits from the Falcon platform, we’re able to address it without being distracted by other tools

The value for the money that CrowdStrike offered was hard to challenge. Pella is a growing business and we saw that investing in CrowdStrike would help us improve security in an expanding and more complex environment. Also, we found that CrowdStrike managed services have a level of maturity nobody else could match.
CrowdStrike Falcon Endpoint Protection Platform provides protections for all kinds of threats, exploits, known and unknown threats, it also supports all types of cloud infrastructures along with different types of container platforms.
One of the best EDR solutions in market. I really like the interface of the platform, it is so much user friendly. False positives are very less compared to the previous endpoint security solutions we have used. A light weight agent makes it a very stable product
I would highly recommend CrowdStrike Falcon to any organization serious about bolstering its cybersecurity defenses. The platform’s effectiveness in threat detection, proactive mitigation, and scalability make it a valuable asset in today’s ever-evolving threat landscape.
1. IDC: The Business Value of the CrowdStrike Falcon XDR Platform
2. Individual results may vary. Based on a customer assessment of CrowdStrike vs traditional, legacy AV vendors





