Your Current Endpoint Security May Be Leaving You with Blind Spots

Threat actors are continuously honing their skills to find new ways to penetrate networks, disrupt business-critical systems and steal confidential data. In the early days of the internet, adversaries used file-based malware to carry out attacks, and it was relatively easy to stop them with signature-based defenses. Modern threat actors have a much wider variety of tactics, techniques and procedures (TTPs) at their disposal. CrowdStrike’s 2022 Global Threat Report reveals 62% of attacks involve non-malware, hands-on-keyboard activity that will easily evade most legacy solutions, which are simply blind to this type of malicious activity.
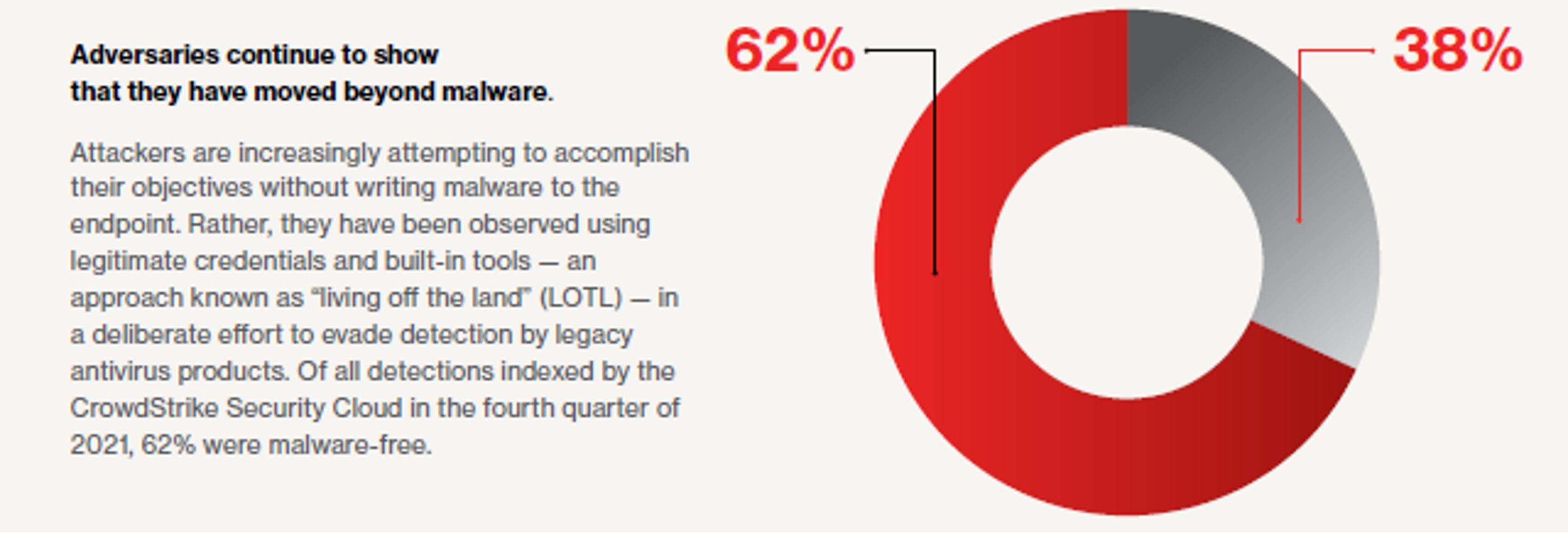
Today’s savvy threat actors exploit endpoint vulnerabilities and use stolen credentials and fileless malware to penetrate systems and move laterally across a network to wreak havoc. Once they breach a network, sophisticated attackers can fly under the radar for weeks or longer, living off the land to actively plan and execute their moves. The incredibly sophisticated SUNBURST attack, for example, went undetected for nine months, impacting over 18,000 organizations across the globe.
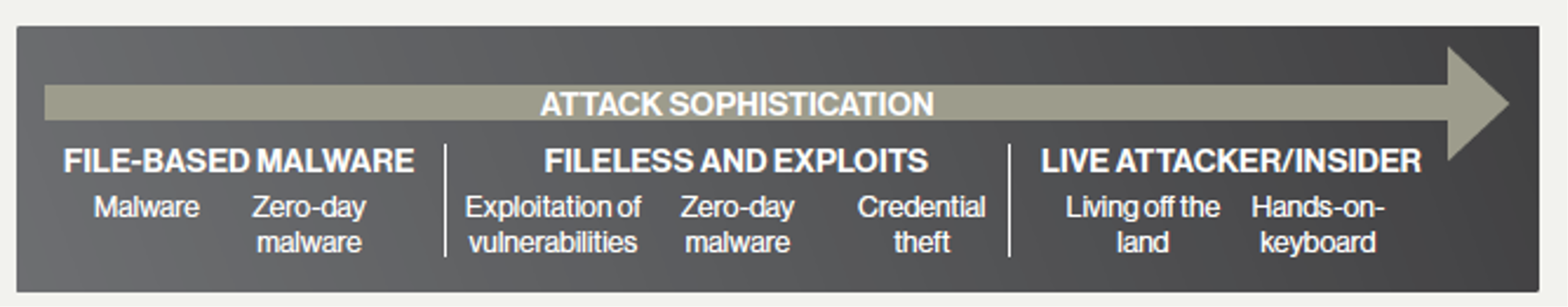
Today’s attacks are highly sophisticated
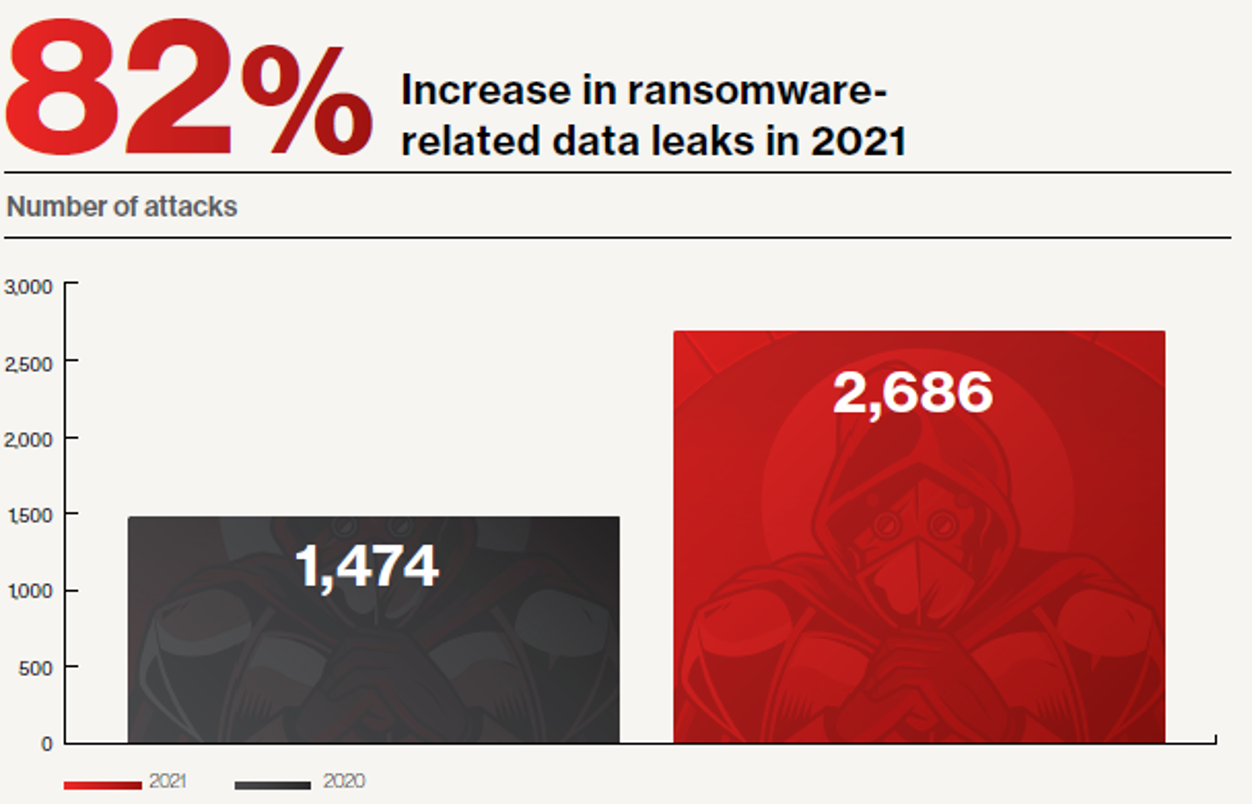
Advanced threats like ransomware can paralyze your business and tarnish your company’s reputation. The evolution of ransomware also reflects how adversaries are adapting their techniques and shifting their objectives. Many cybercriminals, no longer content to simply hold your data for ransom, now use ransomware to harvest data and reap additional awards. In fact, according to the CrowdStrike 2022 Global Threat Report, ransomware-related data leaks increased 82% in 2021.
Are You Still Fighting Yesterday’s Battles?
Legacy endpoint security products like antivirus solutions were developed years ago to protect traditional IT environments and block rudimentary file-based malware. Antivirus solutions offer limited protection in the cloud era and no real visibility or protection against sophisticated threats that don’t use malware. They are fraught with limitations, including:
- Protection gaps. Traditional antivirus clients rely on a central server deployed in a corporate data center to stay current with the latest threats. Today’s cloud-first workers are often disconnected from the corporate network for extended periods and are unable to communicate with the server, which weakens protection and opens the door for threat actors.
- Software lags and lapses. Conventional antivirus clients are notoriously difficult to update. It can take weeks to roll out a routine software upgrade across the entire business. In the meantime, the organization may be exposed.
- Performance and support barriers. Traditional “thick” antivirus clients consume CPU, RAM and disk resources. They can degrade endpoint performance, impair user experience and burden the help desk with support issues.
- Blind spots. Conventional antivirus solutions are designed to protect individual endpoints against file-based malware. They don’t gather or analyze security data holistically across endpoints to identify or block actions symptomatic of a modern attack like credential theft and lateral movement.
Learn more about what legacy endpoint security really costs.
Eliminate Blind Spots with CrowdStrike Falcon®
CrowdStrike’s cloud-native endpoint security solution is built from the ground up to eliminate blind spots and protect against today’s sophisticated attacks. CrowdStrike has redefined security with the world’s most advanced cloud-native platform that protects and enables the people, processes and technologies that drive modern enterprise. Purpose-built in the cloud with a single lightweight-agent architecture, CrowdStrike’s endpoint security provides unmatched scalability, superior protection and performance, reduced complexity and immediate time-to-value.
Powered by the CrowdStrike Security Cloud and world-class artificial intelligence (AI), the CrowdStrike Falcon® platform leverages real-time indicators of attack (IOAs), threat intelligence and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation across every customer endpoint in real time.
Designed for the digital era, CrowdStrike Falcon® is delivered as a 100% cloud-based service that requires no on-premises hardware or software. The Falcon platform enables Day One deployment and on-demand scalability, and provides a single cloud-based administrative console. Easy-to-use APIs provide interoperability with other security platforms and tools to simplify security operations.
Falcon’s cloud-delivered, universal lightweight agent runs on a wide range of endpoints and operating systems including workstations, servers, virtual machines and desktops, containers, mobile devices and Internet of Things (IoT) endpoints. Ideal for today’s cloud-centric businesses, the Falcon agent requires no corporate network or VPN connectivity, and supports physical devices like PCs and bare-metal servers as well as virtual endpoints running in private or public clouds.
Falcon can help you eliminate antivirus blind spots, strengthen your security posture and reduce risk.
Next Steps
Legacy endpoint security solutions are no match for today’s savvy threat actors. It’s time to say goodbye to your old antivirus software. Try CrowdStrike Falcon® for free today. Want more information? Join our CrowdCast, Focus on 5: Critical Capabilities for Modern Endpoint Security, to see a firsthand demo of the Falcon platform.
Additional Resources
- Learn how the powerful CrowdStrike Falcon® platform provides comprehensive protection across your organization, workers and data, wherever they are located.
- Visit our Industry Recognition and Technology Validation webpage to see what industry analysts are saying about CrowdStrike and the Falcon platform.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see for yourself how true next-gen AV performs against today’s most sophisticated threats.


