Endpoint Security & XDR
CrowdStrike Falcon Wins AV-Comparatives Awards for EDR Detection and Mac Security
AV-Comparatives, an independent cybersecurity software testing organization, has released the results of two key evaluations of enterprise security solutions. The CrowdStrike Falcon® cybersecurity pla[…]
CrowdStrike Researchers Investigate the Threat of Patchless AMSI Bypass Attacks
Adversaries have employed various tactics to bypass Windows’ AMSI security feature, but such attacks are noisy, meaning they can be detected by monitoring security products A CrowdStrike Red Team Engi[…]
CrowdStrike Elevates XIoT Security with AI-Powered Insights
As organizations increasingly rely on connected devices to drive efficiency and innovation, the Extended Internet of Things (XIoT) — covering industrial control systems (ICS), operational technology ([…]
CrowdStrike Named a Customers’ Choice in 2025 Gartner® Voice of the Customer for Endpoint Protection Platforms Report
A unified endpoint protection platform (EPP) is the essential foundation to a strong cybersecurity strategy. The industry standard for delivering AI-powered cybersecurity is the CrowdStrike Falcon® pl[…]
CrowdStrike Falcon for Mobile Gains Android Enterprise and Zero Trust Integrations
As organizations support an increasingly mobile workforce, the challenge of securing access to corporate resources from personal and company-owned devices, across various locations, networks, and use […]
Falcon Next-Gen SIEM Integrates with Microsoft Edge for Business to Improve Enterprise Browser Security
CrowdStrike is a strategic launch partner for the new Microsoft Edge for Business security connector framework, a new initiative that brings critical browser security data direction into CrowdStrike F[…]
CrowdStrike Falcon for IT Adds Endpoint Automation to Advance SOC Transformation
Today, CrowdStrike is releasing automated baseline enforcement and remediation in CrowdStrike Falcon® for IT to secure misconfigured devices and consistently address vulnerabilities across endpoints. […]
Securing XIoT in the Era of Convergence and Zero Trust
The rise of connected devices has fundamentally reshaped industries, enabling unprecedented levels of automation, efficiency, and innovation. These devices fall under the Extended Internet of Things ([…]
Intelligence-Led Threat Hunting: The Key to Fighting Cross-Domain Attacks
Cross-domain attacks have become a defining challenge in modern cybersecurity, with adversaries exploiting gaps across endpoints, identity systems, and cloud environments to achieve their objectives. […]
CrowdStrike Named a Leader in The Forrester Wave™: Managed Detection and Response Services Q1 2025
CrowdStrike has been named a Leader in The Forrester Wave™: Managed Detection and Response (MDR) Services, Q1 2025. Forrester researched, analyzed, and scored the ten most significant vendors in the M[…]
CrowdStrike and Intel Partner with MITRE Center for Threat-Informed Defense in PC Hardware-Enabled Defense Project
CrowdStrike and Intel Corp. were key research sponsors and participants in the latest project from the MITRE Center for Threat-Informed Defense The PC Security Stack Mappings — Hardware-Enabled Defens[…]
University of Sunderland Goes from Ransomware Recovery to Proactive Defense with CrowdStrike
In 2021, the University of Sunderland experienced a devastating ransomware attack that disrupted its services and highlighted vulnerabilities in its security posture. With over 28,000 students relying[…]
CrowdStrike Falcon Platform Achieves Perfect Score in SE Labs’ Most Comprehensive Ransomware Evaluation
In the 2024 SE Labs ® Enterprise Advanced Security (EDR) Ransomware Test, the CrowdStrike Falcon® platform scored 100% detection, 100% protection, and 100% accuracy, earning the AAA Award for Advanced[…]
CrowdStrike Falcon for Legacy Systems: Modern Security for Legacy Environments
Many organizations across critical industries such as healthcare, manufacturing and energy rely on legacy Windows operating systems to run essential equipment. These systems, while operationally vital[…]
CrowdStrike Earns AAA Award, 100% Total Accuracy Score in SE Labs Q3 Enterprise Advanced Security Test
The CrowdStrike Falcon® platform earns the AAA award in SE Labs Q3 2024 Enterprise Advanced Security Test The Falcon platform outperformed all other vendors in accurately detecting the real-world cros[…]
CrowdStrike Named a Leader in GigaOm Radar for Ransomware Prevention
Ransomware continues to be one of the most pervasive and costly cyber threats facing organizations worldwide. More than 40% of organizations surveyed by ESG research experienced a successful ransomwar[…]
BLG Sees an 80% Reduction in False Positives with CrowdStrike
Borden Ladner Gervais LLP is Canada’s largest law firm with 850 lawyers and 2,300 employees working in five offices spread across the country. The firm is 200 years old and fully bilingual across its […]
The Rise of Cross-Domain Attacks Demands a Unified Defense
Modern adversaries are quiet. No longer reliant on clunky malware to breach their targets, they have adopted more subtle and effective methods to infiltrate businesses, move laterally and access criti[…]
CrowdStrike Falcon Prevents Multiple Vulnerable Driver Attacks in Real-World Intrusion
Over the last 18 months, bring your own vulnerable driver (BYOVD) attacks have escalated significantly as adversaries attempt to bypass endpoint detection and response (EDR) products including the Cro[…]
Aflac Drives Consolidation with the Falcon Platform, Eliminating 15 Point Security Tools in Three Years
Aflac, one of the world’s largest supplemental insurance providers, is built on a promise: to support its customers in times of need. Whether it’s an accident, critical illness or mounting medical bil[…]
Solar Group Eliminates Complexity and Speeds Response Time with the CrowdStrike Falcon Platform
Solar Group is a leading European sourcing and services company whose core business centers on product sourcing, value-adding services and optimizing their customers’ businesses. Headquartered in Denm[…]
Gulf Bank Swaps Four Security Products for the CrowdStrike Falcon Platform
The Middle East’s financial sector, particularly in Kuwait, faced a surge of sophisticated cyberattacks starting in 2018. For Gulf Bank, a leading financial institution in Kuwait, this wave of attacks[…]
CrowdStrike Receives High Scores in 2024 Gartner® Critical Capabilities for Endpoint Protection Platforms Report
This week, Gartner released its 2024 Gartner® Critical Capabilities Report for Endpoint Protection Platforms (EPP) as a companion to last month’s 2024 Gartner® Magic Quadrant™ for Endpoint Protection […]
CrowdStrike + Fortinet: Unifying AI-Native Endpoint and Next-Gen Firewall Protection
In today’s fast-evolving cybersecurity landscape, organizations face an increasing barrage of sophisticated threats targeting endpoints, networks and every layer in between. CrowdStrike and Fortinet h[…]
Enhancing Detection Fidelity: Fight Alert Fatigue with Accurate and Reliable Detections
In today's rapidly evolving cybersecurity landscape, the importance of detection fidelity cannot be overstated. Security operations center (SOC) teams are overwhelmed by the sheer volume and complexit[…]
TDK Electronics Goes from Complexity to Confidence with CrowdStrike
TDK Electronics is a German manufacturer of electronic components, modules and systems. With more than 23,000 employees spread across 20 development and production sites worldwide, TDK serves a range […]
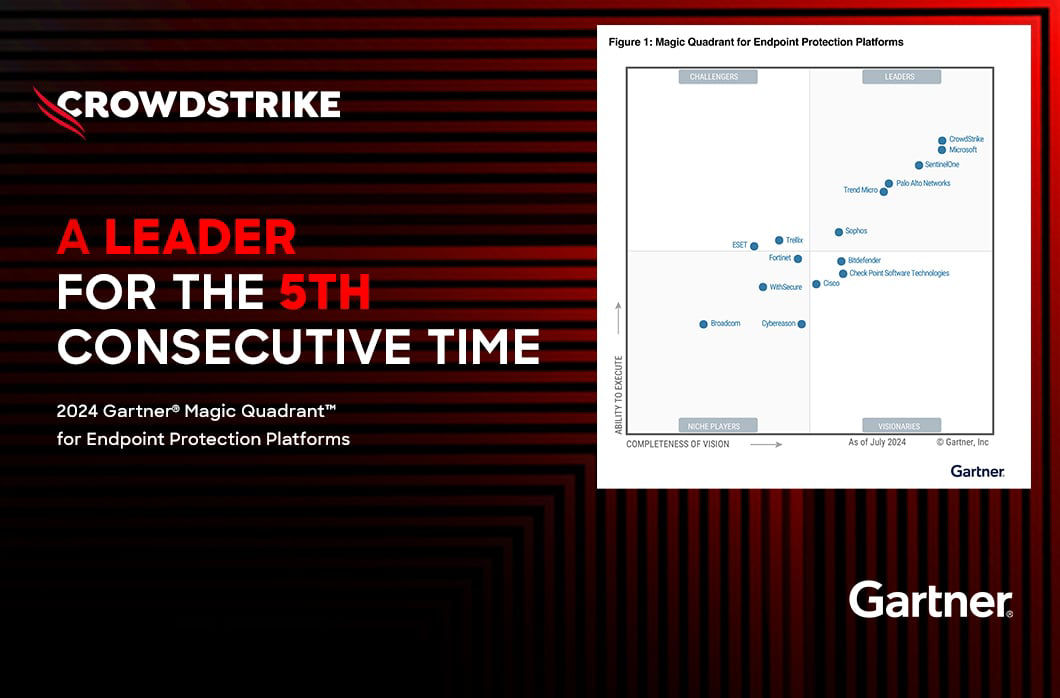
CrowdStrike Named a Leader in 2024 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
CrowdStrike is proud to be named a Leader in the 2024 Gartner® Magic Quadrant™ for Endpoint Protection Platforms. We believe this recognition clearly demonstrates the power of the CrowdStrike Falcon® […]
Take Your Endpoint Security to New Heights at Fal.Con 2024
This blog is part of a five-part series previewing Fal.Con 2024 content. Read previews for cloud, AI, next-gen SIEM and identity. Endpoint security remains the foundation of modern cyber defense. It’s[…]
CrowdStrike Named a Customers’ Choice in 2024 Gartner® Voice of the Customer for Endpoint Protection Platform Report
The endpoint combines both opportunity and risk for most organizations. While an essential hub for modern business operations and the tools employees use, it also is the primary attack surface for tod[…]
Retailer Compares Microsoft with CrowdStrike for Security. The Verdict? “It’s Not Even Close”
The CISO of an American retailer recently shared their experience comparing CrowdStrike with Microsoft for endpoint and identity security. This person, who has nearly a decade of experience in cyberse[…]
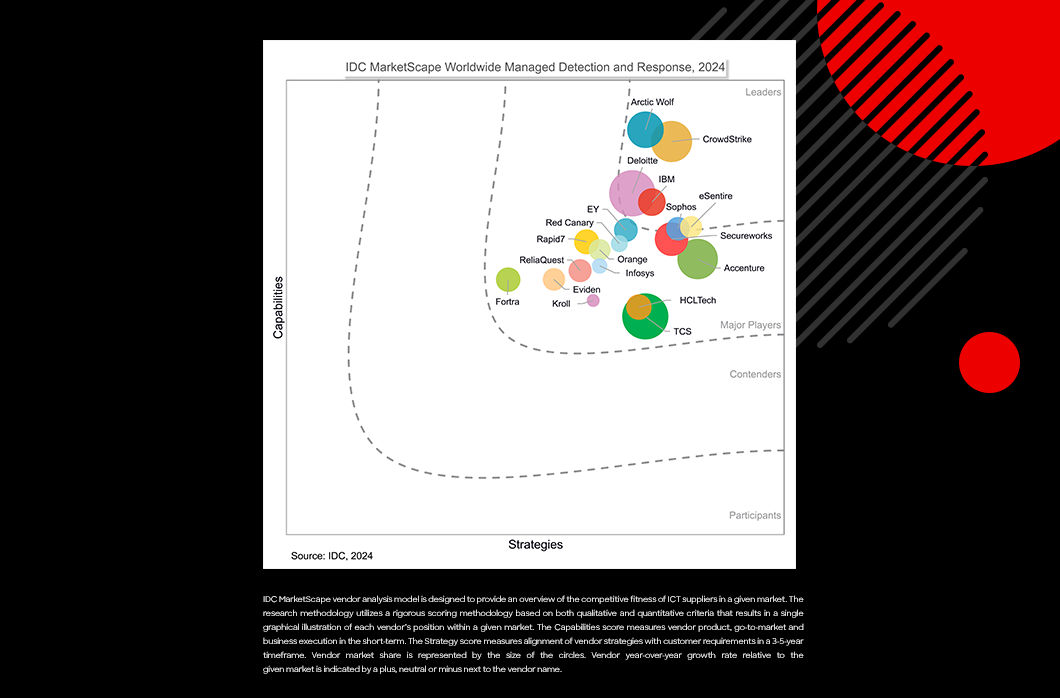
CrowdStrike Named a Leader in IDC MarketScape for Worldwide MDR
The #1 global managed detection and response (MDR) provider and pioneer continues to dominate. Today, CrowdStrike was named a Leader in the 2024 IDC MarketScape: Worldwide Managed Detection and Respon[…]
Falcon Fund in Focus: Nagomi Helps Customers Maximize Their Cybersecurity Investments
Preventable breaches are a common problem. According to research by Nagomi, a leader in the nascent field of automated security control assessment, 80% of breached organizations already had a tool in […]
CrowdStrike Falcon Wins Best EDR Annual Security Award in SE Labs Evaluations
CrowdStrike wins third consecutive Best Endpoint Detection and Response 2024 Award from SE Labs The award recognizes that the CrowdStrike Falcon® platform demonstrates consistent results in detecting […]
CrowdStrike, Intel and Dell: Clustering and Similarity Assessment for AI-driven Endpoint Security with Intel NPU Acceleration
CrowdStrike’s mission is to stop breaches. We continuously research and develop technologies to outpace new and sophisticated threats and stop adversaries from pursuing attacks. We also recognize that[…]
CrowdStrike a Research Participant in Two Latest Center for Threat-Informed Defense Projects
As a global cybersecurity industry leader and a Research Partner for the MITRE Engenuity Center for Threat-Informed Defense, CrowdStrike provided expertise and thought leadership to two of the Center […]
Does Your MDR Deliver Outcomes — or Homework?
At CrowdStrike, we’re on a very simple mission: We stop breaches. It’s easy for us to make this claim but challenging to put into practice and maintain day in and day out. Still, we know with absolute[…]
CrowdStrike and Intel Research Collaborate to Advance Endpoint Security Through AI and NPU Acceleration
At CrowdStrike, we are relentlessly researching and developing new technologies to outpace new and sophisticated threats, track adversaries’ behavior and stop breaches. As today’s adversaries continue[…]
CrowdStrike Customers Share Benefits of Cybersecurity Consolidation and Technology Integrations
I recently had the opportunity to speak with three CrowdStrike customers who shared their stories on why they consolidated on the CrowdStrike Falcon® XDR platform and the benefits of CrowdStrike’s tec[…]
Seeing into the Shadows: Tackling ChromeOS Blind Spots with Dell and CrowdStrike
According to a 2023 Forbes article, 12.7% of U.S. workers work remotely and 28.2% have adopted a hybrid work schedule. As device and usage trends continue to shift, organizations must find ways to sec[…]
HijackLoader Expands Techniques to Improve Defense Evasion
HijackLoader continues to become increasingly popular among adversaries for deploying additional payloads and tooling A recent HijackLoader variant employs sophisticated techniques to enhance its comp[…]
4 Reasons Why Nonprofits Are a Target — and What You Need to Know About Cybersecurity
Small and medium-sized businesses (SMBs) are a more frequent target of cybercrime than large companies, a trend largely driven by their lack of security resources and expertise. Some SMBs are at great[…]
CrowdStrike Native XDR Now Brings Faster, More Comprehensive Detections to EDR Customers at No Additional Cost
Today’s adversaries are moving faster than ever. With the quickest attacks happening in just 7 minutes, adversaries are compromising endpoints and moving laterally before security teams can respond.1 […]
Furthest Right in Vision. Highest in Ability to Execute. Only CrowdStrike.
If a picture is worth a thousand words, the 2023 Gartner® Magic Quadrant™ for Endpoint Protection Platforms says it all. Today, I’m incredibly honored and proud to announce CrowdStrike has been named […]
CrowdStrike Falcon Platform Delivers $6 Return for Every $1 Invested
A new IDC white paper, “The Business Value of The CrowdStrike Falcon XDR Platform,” sponsored by CrowdStrike, highlights the substantial operational benefits, cost savings and ROI that organizations a[…]
CrowdStrike Participates in Center for Threat-Informed Defense OceanLotus Project, the First Public Adversary Emulation Plan Combining macOS and Linux
The MITRE Engenuity Center for Threat-Informed Defense created a public adversary emulation library in 2020 as adversary emulation plans comprising MITRE ATT&CK® tactics and techniques are essential t[…]
Five Steps to a Bulletproof Business Case for MDR
For many cybersecurity leaders, the most intimidating threat they encounter isn’t an adversary — it’s the daunting prospect of trying to win over key business stakeholders and obtain vital budget. Esp[…]
CrowdStrike Achieves 100% Ransomware Protection Accuracy and 100% EDR Rating in SE Labs Test
In the 2023 SE Labs Enterprise Advanced Security (EDR) Ransomware test, the AI-native CrowdStrike Falcon® platform achieved a 100% ransomware protection rating and scored a 100% EDR rating. Testing wa[…]
Small Screens, Big Risks: Falcon for Mobile Releases New Innovations to Accelerate Detection and Response for Mobile Threats
Mobile devices have become critical endpoints for accessing enterprise applications, systems and data. Adversaries know this all too well, as evidenced by the growing numbers of attacks that target mo[…]
CrowdStrike Recognized by Forrester as a Leader in Endpoint Security with the Highest Score in the Current Offering Category
CrowdStrike has been named a Leader in The Forrester Wave™: Endpoint Security, Q4 2023, the latest recognition in a string of accolades for our market-leading cybersecurity solutions delivered from th[…]
CrowdStrike Partners with Box to Add Automated Protections Against Security Breaches and Data Loss
The risk of cyberattacks continues to grow for small to medium-sized businesses (SMBs). Today, a staggering 70% of cyberattacks target SMBs, a scourge that cost organizations with fewer than 500 emplo[…]
CrowdStrike vs. Microsoft Defender for Endpoint: A Cybersecurity Leader Compares EDR Tools
CrowdStrike customers tend to stay with CrowdStrike, typically starting with endpoint detection and response (EDR), then expanding to other attack surfaces as they consolidate their cybersecurity with[…]
Three Recommendations for a Next-Generation Cybersecurity Framework
Cyberattacks evolve daily, and defenders are forced to adapt at the same rate. Cybersecurity best practices, however, are updated and codified much less frequently. There is broad experimentation in t[…]
It’s Time to Do Better as an Industry with MITRE Evaluations
We couldn’t be prouder that CrowdStrike achieved the highest coverage across the last two consecutive MITRE Engenuity ATT&CK® Evaluations. We achieved 100% protection, 100% visibility and 100% analyti[…]
CrowdStrike Redefines Cybersecurity with New Falcon Platform Innovations to Deliver True Platform Consolidation
Cybersecurity is about speed. The faster you can detect an attack, the faster you can respond and stop adversaries in their tracks — and they are steadily growing quicker and more sophisticated, with […]
CrowdStrike and Intel Corporation: Addressing the Threat Landscape Today, Tomorrow and Beyond
At CrowdStrike, our mission is to stop breaches. We’re constantly researching and developing new technologies to stay ahead of sophisticated threats and stop adversaries from advancing their attacks. […]
Unveiling the CrowdStrike Marketplace: A Powerful Ecosystem to Meet Unique Cybersecurity Needs
Organizations must find ways to unify disjointed tools and mitigate their cybersecurity risk as threats become more sophisticated and siloes impede visibility. Today’s adversaries are getting faster —[…]
CrowdStrike Joins the MITRE Engenuity Center for Threat-Informed Defense’s “Summiting the Pyramid” Research Project to Make Analytics More Robust
CrowdStrike is a Research Partner with the MITRE Engenuity Center for Threat-Informed Defense and actively participates in the Center’s research into proactive cybersecurity defense As a global leader[…]
Why Legacy AV Is an Easy Target for Attackers
If you still rely on legacy antivirus software to stop modern cyberattacks, this post is for you. Today’s adversaries are relentless. While many threat actors have adopted newer techniques such as dat[…]
Falcon Complete for Service Providers: New Program Expands Access to Market-Leading MDR Service
CrowdStrike is expanding access to its market-leading managed detection and response (MDR) service, CrowdStrike Falcon® Complete. With the announcement of Falcon Complete for Service Providers, CrowdS[…]
Earn Your Wings in the New CrowdStrike Community
It’s never been easier to get your CrowdStrike questions answered. The new and improved CrowdStrike Community is now generally available to all CrowdStrike customers and partners, offering a trusted u[…]
CrowdStrike Teams with the MITRE Engenuity Center for Threat-Informed Defense in Development of TRAM II
As a Research Partner for the MITRE Engenuity Center for Threat-Informed Defense, CrowdStrike was involved in the development of a new version of the Threat Report ATT&CK Mapper (TRAM) CrowdStrike pro[…]
Healthcare Is Experiencing a Cybersecurity Emergency
Hospitals are seeking creative ways to fund technology and cybersecurity protection measures amid a perfect storm of operational challenges that affect quality of care. These include: Rising Costs: Ho[…]
CrowdStrike Scores 100% in SE Labs Q2 2023 Enterprise Advanced Security Detection Test, Wins AAA Award
The CrowdStrike Falcon® platform achieved 100% attack detection with zero false positives in the Q2 2023 SE Labs Enterprise Advanced Security (EAS) test, earning the AAA award for its perfect performa[…]
Meet the Protectors: New Video Series Spotlights Cybersecurity Leaders Powered by CrowdStrike
You don’t have a malware problem — you have an adversary problem. CrowdStrike has relentlessly focused on finding and stopping the humans behind cyberattacks. Today, we’re launching a new series that […]
Welcome to the Adversary Universe Podcast: Unmasking the Threat Actors Targeting Your Organization
The modern adversary is relentless. Today’s threat actors target global organizations with increasingly sophisticated attacks. As we’ve said since the founding of CrowdStrike: “You don’t have a malwar[…]
CrowdStrike Expands XDR Ecosystem to Give Customers a Data Advantage
Cybersecurity is fundamentally a data problem. As adversary techniques continue to mature, organizations still struggle to collect the right data from all their security and IT point products to detec[…]
Why Customers Are Consolidating Cybersecurity with CrowdStrike
As adversaries continue to evolve their tactics and techniques, organizations are scrambling to shore up their security posture. Security teams have historically turned to point products to fill gaps […]
Falcon Insight for ChromeOS: The Industry’s First Native XDR Offering for ChromeOS
In recent years, ChromeOS device usage among businesses has seen a significant uptick, particularly in its adoption across verticals, from schools to large enterprises. According to recent IDC researc[…]
CrowdStrike Falcon Pro for Mac Achieves 100% Mac Malware Protection, Awarded 2023 AV-Comparatives Approved Mac Security Product
CrowdStrike Falcon® Pro for Mac achieved 100% Mac malware protection in the May 2023 AV-Comparatives Mac Security Test This 2023 win marks the sixth consecutive year that CrowdStrike Falcon Pro for Ma[…]
CrowdStrike Researchers Automate Zero-Day Malware Classification for More Effective Threat Mitigation
CrowdStrike researchers use machine intelligence to categorize zero-day malware by using behavioral data, pre-defined Threat Type groups, and supervised and unsupervised clustering and similarity asse[…]
CrowdStrike Invests in and Partners with Prelude Security to Drive Continuous Security Testing and Validation for Our Customers
Managing security posture at scale is a significant challenge for global organizations of all sizes. With a rapidly expanding security estate and a global worker gap of 3.4 million, according to (ICS)[…]
The Security Compromise that Comes with Windows 10 End of Support
On April 27, 2023, Microsoft announced the end of support for Windows 10, making 1022H2 the final version of the operating system. In the announcement, Microsoft outlined that Windows 10 will continue[…]
CrowdStrike Falcon Platform Achieves Certification in AV-Comparatives' First Anti-Tampering Test
After completing extensive tests designed to evaluate the tampering resistance of enterprise security solutions, the CrowdStrike Falcon® platform has achieved certification in the AV-Comparatives Anti[…]
How to Establish Cross-Border Transfer Systems that Help Protect Privacy
Cybersecurity, privacy and data flows will be key topics at this year’s G7 in Japan. Against this backdrop, it has been a year since last year’s amendments to the Act on Protection of Personal Informa[…]
CrowdStrike Expands Falcon Data Replicator Capabilities to Boost SOC Performance
Are you getting the most from your data? Collecting data from across your environment can provide security teams with the visibility needed to detect and respond to threats, but large volumes of data […]
Accelerate Your Security Transformation with Google Workspace and CrowdStrike
Each day, enterprise and public sector IT teams face new challenges when managing hybrid work for networks of hundreds, or even thousands, of users. A more distributed workforce means an increased rel[…]
New CrowdStrike Falcon Fusion Features Refine Workflow Automation for CrowdStrike Customers
CrowdStrike Falcon® Fusion is a cloud-scale, extensible security orchestration, automation and response (SOAR) framework that’s natively integrated with the CrowdStrike Falcon® platform and available […]
CrowdStrike Delivers Cyber Resilience for the Airline Industry to Meet New TSA Requirements
The U.S. Transportation Security Administration (TSA) is taking proactive measures to protect the nation’s transportation system by issuing new cybersecurity requirements for airports and aircraft ope[…]
Introducing CrowdStrike Falcon Complete XDR: Solving the Cybersecurity Skills Gap with Managed XDR
CrowdStrike today introduced CrowdStrike Falcon® Complete XDR, a new managed extended detection and response (MXDR) service that builds on the industry-leading CrowdStrike Falcon® Complete managed det[…]
Mitigating USB Data Exfiltration with New Capabilities in Falcon Device Control
New features in CrowdStrike Falcon® Device Control deliver enhanced data identification and enable investigation into data loss and exfiltration activities through USB devices. New file metadata capab[…]
CrowdStrike Brings Extended Detection and Response to New z16 and LinuxONE 4 Single Frame and Rack Mount Models
We are excited to collaborate with IBM, which today unveils its new IBM z16 and LinuxONE Rockhopper 4 single frame and rack mount models, available globally on May 17, 2023. Powered by IBM’s Telum pro[…]
4 Examples of Third-Party Testing and Customer Reviews that Highlight CrowdStrike’s Cybersecurity Leadership
CrowdStrike researchers work tirelessly to stay a step ahead of even the most sophisticated adversaries, with an elevated profile that includes becoming a Research Partner in the MITRE Engenuity Cente[…]
CrowdStrike Falcon Named the Winner of the 2022 AV-TEST Award for Best MacOS Security Product
After extensive testing and analysis, the AV-TEST Institute has named CrowdStrike Falcon® Pro for Mac the Best MacOS Security Product for Business for 2022. AV-TEST completed its evaluation of macOS s[…]
CrowdStrike Uncovers I2Pminer MacOS Mineware Variant
CrowdStrike analyzed an I2Pminer variant that targets macOS The mineware utilizes I2P to hide XMRig network traffic The CrowdStrike Falcon® platform provides continuous protection against mineware thr[…]
CrowdStrike Ranked #1 in the IDC Worldwide Endpoint Security Market Shares Report for Third Time in a Row
CrowdStrike maintains endpoint security market leadership with a #1 ranking in IDC’s 2021-2022 report, and has been awarded Best Endpoint Detection and Response and Best Product Development by SE Labs[…]
DLL Side-Loading: How to Combat Threat Actor Evasion Techniques
Threat actors constantly evolve their tactics and techniques to circumvent security solutions. Working at the cutting-edge of detection engineering, CrowdStrike rapidly tracks and observes these evolu[…]
3 Easy Steps for End-to-End XDR with CrowdStrike and Zscaler
Hybrid working models have increasingly become the normal way of doing business. Employees are working from anywhere, users and their devices are moving on and off the office network, and many applica[…]
Malware Analysis: GuLoader Dissection Reveals New Anti-Analysis Techniques and Code Injection Redundancy
GuLoader is an advanced malware downloader that uses a polymorphic shellcode loader to dodge traditional security solutions CrowdStrike researchers expose complete GuLoader behavior by mapping all emb[…]
Our Customers Have Spoken: CrowdStrike Delivers the Best in EDR, EPP and XDR
Time and again, analyst reports, independent tests and numerous other awards and acknowledgements affirm CrowdStrike is a leader in cybersecurity. Why is this important? Because when CrowdStrike is #1[…]
Inside the MITRE ATT&CK Evaluation: How CrowdStrike’s Elite Managed Services Operate in the Real World
Following CrowdStrike’s strong performance in the first-ever MITRE ATT&CK® Evaluations for Security Managed Services Providers with 99% detection coverage, we take a deep dive into the testing process[…]
CrowdStrike Falcon Platform Achieves 100% Detection and Protection Against MacOS Malware with Zero False Positives in Latest MacOS AV-TEST
As organizations increasingly face malware attacks that target macOS, detecting and preventing attacks without disruption caused by false positives and false warning messages is increasingly important[…]
CrowdStrike Powers MXDR by Deloitte, Offering Customers Risk Mitigation with Powerful Customized and Managed Security Services
Deloitte (U.S/Global), a leader in managed security services, recently announced the global availability of MXDR by Deloitte — a managed extended detection and response suite of offerings (U.S./Global[…]
CrowdStrike Teams with the MITRE Engenuity Center for Threat-Informed Defense to Develop ATT&CK Defense for IaaS
CrowdStrike is a Research Partner in the MITRE Engenuity Center for Threat-Informed Defense and also a Research Participant in the Center’s Defending IaaS with ATT&CK® research project This project’s […]
CrowdStrike Falcon Platform Achieves 100% Ransomware Prevention with Zero False Positives, Wins AAA Enterprise Advanced Security Award from SE Labs
The CrowdStrike Falcon® platform achieved 100% protection accuracy and 100% legitimacy accuracy with zero false positives, winning SE Labs’ first-ever endpoint detection and response (EDR) ransomware […]
CrowdStrike Advances to Research Partner with MITRE Engenuity Center for Threat-Informed Defense to Help Lead the Future of Cyber Defense
CrowdStrike is deepening its commitment to advancing the security ecosystem leading the future of protection by becoming a top-tier partner in the MITRE Center for Threat-Informed Defense research pro[…]
CrowdStrike Introduces Sandbox Scryer: A Free Threat-Hunting Tool for Generating MITRE ATT&CK and Navigator Data
Sandbox Scryer is an open-source tool for producing threat hunting and intelligence data from public sandbox detonation output The tool leverages the MITRE ATT&CK Framework to organize and prioritize […]
Why XDR Should Be on Your Roadmap for SOC Success
Fighting modern adversaries requires having a modern security operations center (SOC), especially as organizations move to the cloud. To protect their estates against tomorrow’s threats, security prof[…]
CrowdStrike Wins Technology Innovation Leadership Award, Continues Dominance in Endpoint Security Market
CrowdStrike is proud to receive Frost & Sullivan’s 2022 Global Technology Innovation Leadership Award in the endpoint security sector. This recognition reflects CrowdStrike’s continued investment to d[…]
CrowdStrike and Industry Partners Release Open Cybersecurity Schema Framework
CrowdStrike is excited to announce the release of the Open Cybersecurity Schema Framework (OCSF) project, a collaborative open-source effort among cybersecurity and technology leaders to break down si[…]
Securing Our Nation: How the Infrastructure Investment and Jobs Act Delivers on Cyber Resiliency
Attacks and intrusions on our nation’s vital infrastructure — our electrical grid, water systems, ports and oil supply — are on the rise. For example, as reported by the Pew Charitable Trust in March […]
Address the Cybersecurity Skills Shortage by Building Your Security Stack with the CrowdStrike Store
The increase in attack sophistication coupled with the decline of skilled security staff continues to put pressure on organizations and their teams by minimizing their ability to effectively see and c[…]
CrowdStrike Falcon® Pro for Mac Achieves 100% Mac Malware Protection, Wins Fifth AV-Comparatives Approved Mac Security Product Award
CrowdStrike Falcon® Pro for Mac achieved 100% Mac malware protection in the May 2022 AV-Comparatives Mac Security Test and Review CrowdStrike Falcon® Pro for Mac has now won five consecutive Approved […]
CrowdStrike Tops IDC Worldwide Corporate Endpoint Security Market Shares, 2021
CrowdStrike is proud to be ranked No. 1 in the IDC Worldwide Corporate Endpoint Security Market Shares, 2021 report (doc #US48580022, May 2022). We are grateful to our customers and partners for helpi[…]
CrowdStrike Uncovers New MacOS Browser Hijacking Campaign
CrowdStrike analyzed a new browser hijacking campaign that targets MacOS The purpose of the campaign is to inject ads into the user’s Chrome or Safari browser The CrowdStrike Falcon® platform provides[…]
CrowdStrike Falcon Protects Customers from Follina (CVE-2022-30190)
On May 27, 2022, a remote code execution vulnerability was reported affecting the Microsoft Windows Support Diagnostic Tool (MSDT) The vulnerability, which is classified as a zero-day, can be invoked […]
CrowdStrike Named an Overall Leader in 2022 KuppingerCole Leadership Compass for EPDR Market
CrowdStrike is proud to announce its recognition as an Overall Leader with the highest rating in the 2022 KuppingerCole Leadership Compass for vendors in the Endpoint Protection, Detection & Response […]
CrowdStrike Falcon Pro for Mac Achieves Highest Score in AV-TEST MacOS Evaluation for Business Users (March 2022)
CrowdStrike Falcon®® achieves the maximum score of 18 points in the first 2022 AV-TEST MacOS evaluation for business users AV-TEST is an independent research institute for IT security that performs qu[…]
CrowdStrike Partners with Center for Threat-Informed Defense to Reveal Top Attack Techniques Defenders Should Prioritize
CrowdStrike is a Research Sponsor and contributor for the new Top ATT&CK Techniques project — an initiative of the Center for Threat-Informed Defense, a non-profit, privately funded research and devel[…]
How Falcon OverWatch Spots Destructive Threats in MITRE Adversary Emulation
In the recent MITRE Engenuity ATT&CK Enterprise Evaluation, CrowdStrike demonstrated the power of its unified platform approach to stopping breaches. Facing attack emulations from the highly sophistic[…]
Falcon Fusion Accelerates Orchestrated and Automated Response Time
CrowdStrike Falcon® Fusion automates and accelerates incident response by orchestrating sandbox detonations to automatically analyze related malware samples and enrich the results with industry-leadin[…]
Security Doesn’t Stop at the First Alert: CrowdStrike Falcon Intelligence Offers New Context in MITRE ATT&CK Evaluation
The CrowdStrike Falcon® platform delivers 100% prevention across all nine steps in the MITRE Engenuity ATT&CK® Enterprise Evaluation CrowdStrike extends endpoint and workload protection by fully integ[…]
XDR: A New Vision for InfoSec’s Ongoing Problems
Let's face it. The information security industry loves a new acronym. For industry long-timers, a new acronym might be just the latest reason for an eye roll. For folks new to the field, it can be ver[…]
Falcon Platform Identity Protection Shuts Down MITRE ATT&CK Adversaries
“We were asked to disable identity protection capabilities to let the testing proceed — and still achieved 100% prevention.” The weeks following the release of the MITRE Engenuity ATT&CK Evaluation ca[…]
CrowdStrike “Dominates” in Endpoint Detection and Response
“CrowdStrike dominates in EDR while building its future in XDR and Zero Trust.” — The Forrester Wave™: Endpoint Detection and Response Providers, Q2 2022 We are excited that Forrester has named CrowdS[…]
BERT Embeddings: A Modern Machine-learning Approach for Detecting Malware from Command Lines (Part 2 of 2)
A novel methodology, BERT embedding, enables large-scale machine learning model training for detecting malware It reduces dependency on human threat analyst involvement in training machine learning mo[…]
CrowdStrike Achieves 100% Prevention in Recent MITRE Engenuity ATT&CK Evaluation Emulating Russia-based Threat Groups
“We were asked to disable identity protection capabilities to let the testing proceed — and still achieved 100% prevention.” The CrowdStrike Falcon®® platform delivers 100% prevention across all nine […]
Your Current Endpoint Security May Be Leaving You with Blind Spots
Threat actors are continuously honing their skills to find new ways to penetrate networks, disrupt business-critical systems and steal confidential data. In the early days of the internet, adversaries[…]
CrowdStrike and Cloudflare Expand Zero Trust from Devices and Identities to Applications
Threat actors continue to exploit users, devices and applications, especially as more of them exist outside of the traditional corporate perimeter. With employees consistently working remotely, advers[…]
Empower Your SOC with New Applications in the CrowdStrike Store
With chaos seemingly surrounding us in security, it can be hard to cut through the noise. How do you detect and prioritize evolving threats and what tools should you use to address them? With new atta[…]
Five Steps to Kick-start Your Move to XDR
Alert overload is practically a given for security teams today. Analysts are inundated with new detections and events to triage, all spread across a growing set of disparate, disconnected security too[…]
The Easy Solution for Stopping Modern Attacks
Modern cyberattacks are multifaceted, leveraging different tools and techniques and targeting multiple entry points. As noted in the CrowdStrike 2022 Global Threat Report, 62% of modern attacks do not[…]
CrowdStrike Falcon® Protects from New Wiper Malware Used in Ukraine Cyberattacks
On Feb. 23, 2022, a new wiper malware was reported targeting Ukraine systems The wiper destroys files on infected Windows devices by corrupting specific elements of connected hard drives CrowdStrike I[…]
Modernize Your Security Stack with the Falcon Platform
The job for CIOs, CISOs and their security and IT teams may be more complex than ever in 2022. Ongoing support for hybrid workforces, coupled with the continued shift to the cloud, has expanded the th[…]
Why the Most Effective XDR Is Rooted in Endpoint Detection and Response
Extended detection and response (XDR) solutions deliver powerful capabilities to help security teams fight adversaries by increasing visibility, simplifying operations and accelerating identification […]
CrowdStrike Research Investigates Exploit Behavior to Strengthen Customer Protection
CrowdStrike continuously observes and researches exploit behavior to strengthen protection for customers Code execution techniques constantly target Windows, Linux and macOS operating systems Successf[…]
CrowdStrike Partners with MITRE CTID, Reveals Real-world Insider Threat Techniques
Remote working has exposed companies to greater levels of insider risk, which can result in data exfiltration, fraud and confidential information leakage CrowdStrike is a founding sponsor and lead con[…]
Defend Against Ransomware and Malware with Falcon Fusion and Falcon Real Time Response
Adversaries are moving beyond malware and becoming more sophisticated in their attacks by using legitimate credentials and built-in tools to evade detection by traditional antivirus products. Accordin[…]
CROWDSTRIKE FALCON XDR: Delivered at the Speed and Scale of the CrowdStrike Security Cloud
We are thrilled to announce the general availability of CrowdStrike's newest innovation: CROWDSTRIKE FALCON® XDR. Founded on our pioneering endpoint detection and response (EDR) technology and the pow[…]
CrowdStrike Falcon® Proactively Protects Against Wiper Malware as CISA Warns U.S. Companies of Potential Attacks
The Cybersecurity and Infrastructure Security Agency (CISA) warns of potential critical threats similar to recent cyberthreats targeting Ukraine U.S. companies are advised to implement cybersecurity m[…]
BERT Embeddings: A Modern Machine-learning Approach for Detecting Malware from Command Lines (Part 1 of 2)
Suspicious command lines differ from common ones in how the executable path looks and the unusual arguments passed to them Bidirectional Encoder Representations from Transformers (BERT) embeddings can[…]
Linux-Targeted Malware Increases by 35% in 2021: XorDDoS, Mirai and Mozi Most Prevalent
Malware targeting Linux systems increased by 35% in 2021 compared to 2020 XorDDoS, Mirai and Mozi malware families accounted for over 22% of Linux-targeted threats observed by CrowdStrike in 2021 Ten […]
Zero Trust Integrations Are Expanding in the CrowdStrike Partner Ecosystem
Organizations need to stay ahead of the ever-evolving security landscape. It’s no secret that Zero Trust security is crucial for successful endpoint protection. Due to the rapid transition to a remote[…]
TellYouThePass Ransomware Analysis Reveals a Modern Reinterpretation Using Golang
TellYouThePass ransomware, discovered in 2019, recently re-emerged compiled using Golang Golang’s popularity among malware developers makes cross-platform development more accessible TellYouThePass ra[…]
CrowdStrike Strengthens Exploit Protection Using Intel CPU Telemetry
December 28, 2021
Timo Kreuzer - Yarden Shafir - Satoshi Tanda - Blair Foster Endpoint Security & XDRFalcon adds a new feature that uses Intel hardware capabilities to detect complex attack techniques that are notoriously hard to detect. CrowdStrike’s new Hardware Enhanced Exploit Detection feature d[…]
CrowdXDR Alliance Expands to Help Security Teams Identify and Hunt Threats Faster
CrowdStrike is proud to announce that Armis, Cloudflare and ThreatWarrior have joined the open CrowdXDR Alliance. The addition of these industry leaders enhances XDR with telemetry from cloud, network[…]
How CrowdStrike Protects Customers from Threats Delivered via Log4Shell
Log4Shell, the latest critical vulnerability, found in the Log4j2 Apache Logging Services library, poses a serious threat to organizations Active attempts to exploit the vulnerability were identified […]
How to Set Yourself Up for Real XDR Success
Extended detection and response (XDR) is all the rage these days. It seems like almost every security vendor now claims to offer XDR functionality. But are those claims based in reality? The fact is t[…]
CrowdStrike Falcon® Awarded AV-Comparatives Approved Business Security Product for the Second Time in 2021
CrowdStrike Falcon® receives second half-year award for Approved Business Security Product from AV-Comparatives in 2021 This marks the tenth consecutive Approved Business Security Product award from A[…]
CrowdStrike Falcon® Detects 100% of Attacks in New SE Labs EDR Test, Winning Highest Rating
The CrowdStrike Falcon® platform achieves 100% attacks detected in new Advanced Security Test (EDR) from SE Labs This SE Labs test demonstrated that CrowdStrike’s Zero Trust module, Falcon Identity Th[…]
CrowdStrike Falcon®'s Autonomous Detection and Prevention Wins Best EDR Award and Earns Another AAA Rating in SE Labs Evaluations
CrowdStrike wins the prestigious SE Labs “Best Endpoint Detection and Response” 2021 award. This marks CrowdStrike’s second consecutive year winning Best EDR from SE Labs, the highly regarded independ[…]
Ransomware (R)evolution Plagues Organizations, But CrowdStrike Protection Never Wavers
ECrime activities dominate the threat landscape, with ransomware as the main driver Ransomware operators constantly refine their code and the efficacy of their operations CrowdStrike uses improved beh[…]
The ICS/OT Landscape: How CrowdStrike Supports Through Partnerships With Rockwell and Others
CrowdStrike and Rockwell Automation have announced a partnership to help joint customers secure the expanded threat surface of the industrial control systems (ICS) and operational technology (OT) cont[…]
Golang Malware Is More than a Fad: Financial Motivation Drives Adoption
Golang malware popularity snowballs, increasing by 80% from June to August 2021 eCrime turns to Golang because of its versatility, enabling cross-compiling for other operating systems Cryptocurrency m[…]
Why the Detection Funnel Hits Diminishing Returns
Noisy alerts caused by an increased number of rules for detecting malicious behavior overburden security analysts. Alert fatigue happens when an overwhelming number of alerts desensitize the security […]
CrowdStrike Positioned as a Leader in Inaugural IDC MarketScape: Worldwide Modern Endpoint Security for Enterprise 2021 Vendor Assessment
“CrowdStrike's cloud platform, Falcon, and lightweight agent have rated well with enterprises that are under attack and must deploy rapidly across a large and diverse endpoint footprint.”1 According t[…]
CrowdStrike Falcon® Demonstrates Continued Excellence in Recent AV-Comparatives Evaluations
CrowdStrike Falcon® receives new recognition from AV-Comparatives, a prestigious independent third-party testing institution In AV-Comparatives Real-World Protection Test, Falcon achieved 99.7%, and z[…]
Compromised NPM Package Used in Supply Chain Attack: CrowdStrike Falcon® Customers Protected
Popular NPM package with over 7 million weekly downloads was compromised and used to distribute cryptocurrency miners and password stealers NPM library is used by developers to publish and download no[…]
How to Test Endpoint Security Efficacy and What to Expect
What is efficacy, and why are independent tests necessary? What is the difference between MITRE ATT&CK® TTPs and the cyber kill chain? How can I distinguish between benign and malicious techniques? Ho[…]
CrowdStrike Named A “Strong Performer” in the Forrester New Wave for XDR Providers
We are thrilled to announce that Forrester named CrowdStrike a “Strong Performer” in The Forrester New Wave™: Extended Detection And Response (XDR) Providers, Q4 2021, its New Wave market evaluation o[…]
Fal.Con 2021: Introducing CROWDSTRIKE FALCON XDR and CrowdXDR Alliance
This announcement is part of the Fal.Con 2021 CrowdStrike Cybersecurity Conference, Oct. 12-14. Register now for free to learn all about our other exciting new products and partnerships! Our mission a[…]
Modernize Your SOC with Falcon Fusion, CrowdStrike’s Integrated SOAR Framework
This announcement is part of the Fal.Con 2021 CrowdStrike Cybersecurity Conference, Oct. 12-14. Register now for free to learn all about our other exciting new products and partnerships! Security pros[…]
Falcon FileVantage: New CrowdStrike File Integrity Monitoring Solution Creates Total Efficiency for SecOps
This announcement is part of the Fal.Con 2021 CrowdStrike Cybersecurity Conference, Oct. 12-14. Register now for free to learn all about our other exciting new products and partnerships! When it comes[…]
Protect Your Robot Workforce: Extending Endpoint Protection to Robotic Process Automation (RPA) in a First-of-its-Kind Integration
Automation is on the rise, with more organizations using digital workers — or software “robots” — to take on mundane repetitive tasks, to automate business processes and to streamline operations. As a[…]
CrowdStrike and Verizon Form Partnership to Provide Integrated Solutions and Services to Customers
CrowdStrike is excited to announce a newly formed global partnership with Verizon to bring to market integrated cybersecurity, managed services and risk management capabilities that empower customers […]
Threat Protection from Cloud to Ground: Unified Power of EDR with SaaS and Application Security
There’s no stopping when it comes to scaling your business, so why should your security remain stagnant? With your organization constantly expanding and your IT and security stack increasing in tools,[…]
Teaching an Old Dog New Tricks: 2017 Magniber Ransomware Uses PrintNightmare Vulnerability to Infect Victims in South Korea
2017 Magniber ransomware makes a comeback using the same methods: exploiting unpatched vulnerabilities on South Korean victims In July 2021, CrowdStrike identified Magniber ransomware attempting to us[…]
Spectra Alliance’s Strategic Approach to Zero Trust Adoption
The concept of Zero Trust has recently gained popularity, as the global pandemic has fundamentally changed many aspects of work and business, including cybersecurity. Organizations of all sizes are be[…]
Black Hat 2021: Join Us Virtually or In Person
We’re proud to be a Titanium Sponsor for Black Hat USA 2021, Aug. 2-5, and we have lots in store, both in person and virtually. If you’ll be onsite in Las Vegas, stop by Booth #1836 for a chance to ge[…]
What the New AV-Comparatives’ Approved Business Security Product Award Means for CrowdStrike Falcon®
The new award demonstrates the ability of the CrowdStrike Falcon® platform to protect against real-world threats using the power of machine learning and behavioral detection CrowdStrike is committed t[…]
CrowdStrike Falcon® Pro for Mac Wins Fourth AV-Comparatives Approved Security Product Award
CrowdStrike Falcon® Pro™ for Mac recently won a fourth consecutive Approved Security Product award from leading independent testing organization AV-Comparatives, achieving 99.8% Mac malware protection[…]
How CrowdStrike Falcon Stops REvil Ransomware Used in the Kaseya Attack
Kaseya, makers of popular IT software used by managed service providers (MSPs), was recently affected by a REvil ransomware attack CrowdStrike associates REvil ransomware to the PINCHY SPIDER threat a[…]
CrowdStrike Services Releases AutoMacTC 1.2.0
The CrowdStrike Services team is excited to announce the release of AutoMacTC 1.2.0 to the community. AutoMacTC was originally released in March 2019 to help incident responders investigate intrusions[…]
The Power of Winning Together: Partners Help CrowdStrike Win Recognition Awards and Races
Right from Day One, CrowdStrike has embraced a partner-first and community driven approach to protect customers against modern cyberattacks. It’s no secret that CrowdStrike has built a strong, diverse[…]
The Importance of Integrated Endpoint and Workload Protection for IT and Security Operations
Countless headlines report what we already know all too well: No matter how advanced cybersecurity prevention tools are, with enough motivation, time and resources, adversaries will eventually devise […]
UAL Thank Us Later: Leveraging User Access Logging for Forensic Investigations
CrowdStrike analysts recently began researching and leveraging User Access Logging (UAL), a newer forensic artifact on Windows Server operating system that offers a wealth of data to support forensic […]
CrowdStrike Falcon® Scores 100% Protection in AV-Comparatives Real-World Protection Test (March-April 2021)
Recent high-visibility ransomware attacks — such as the disruption of a major U.S. East Coast fuel pipeline caused by DarkSide ransomware — underscore how critical it is for companies to protect thems[…]
New Message Center Improves Response Time by Reducing Friction in MDR Collaboration
CrowdStrike has long emphasized the importance of identifying, triaging and remediating threats in line with our 1-10-60 framework. This framework is designed to provide a benchmark for security teams[…]
New Partner Applications to Accelerate Your SOC’s Security Transformation
Every security operations center (SOC) is different and has unique traits; however, most share similar challenges. Each SOC has its own set of security tools, some use internal or external expertise, […]
Supercharge Your Security Transformation: Kill Complexity in Your Security Stack
The year 2020 will be known as one of hyper-accelerated digital transformation, marked by organizations delivering many years’ worth of migrations and implementations over an accelerated time period. […]
Investment Banking Firm Greenhill Uses Falcon Complete to Protect Global Clients’ Data
Greenhill, an investment bank with global clients, estimates it has reduced alerts by 75% and saved $300,000 annually following deployment of CrowdStrike Falcon®️ products. Early on, its CIO knew the […]
CrowdStrike and EY Join Forces to Boost Organizational Resiliency
The evolution of today’s remote workforces requires organizations to establish comprehensive and reliable cybersecurity strategies and operations to stay on top of the increasingly complex cyber risk […]
CrowdStrike Falcon® Continues Impressive Record with Highest AAA Rating in SE Labs Enterprise Endpoint Protection Report
AAA rating In Q1 SE Labs Enterprise Endpoint Protection report 100% legitimate accuracy rating 100% protection against targeted attacks Track record of 10 AAA ratings in SE Labs Enterprise Endpoint pr[…]
Falcon Extends Protection for macOS as Threats Surge
MacOS is ubiquitous in enterprise environments, with no signs of slowing down. Recent IDC analysis shows macOS devices have reached a whopping 23% utilization in enterprises (with 1,000+ employees) du[…]
Virgin Hyperloop Protects IP, Augments Team with Falcon Complete and Falcon OverWatch Managed Services
Virgin Hyperloop, a global startup with a world-changing mass transit vision and the intellectual property (IP) to make it happen, remediates “no malware whatsoever” after deploying CrowdStrike Falcon[…]
OverWatch Threat Hunters Win the Race Against Carbanak in MITRE ATT&CK Evaluation
How will your security team react when a sophisticated adversary has you in their sights? Will your team act in time to stop the breach? In last year’s MITRE Engenuity ATT&CK® Evaluation vs. COZY BEAR[…]
Leave No Blind Spot Unseen: Unified Endpoint and Network Detection and Response for Defense in Depth
With cloud adoption surging and workforces becoming increasingly remote, it is more critical than ever for organizations to maintain comprehensive real-time visibility of their digital assets — regard[…]
Enhanced Industrial Threat Detection: Get Early Warnings of Adversaries in Your Enterprise Networks
In our interconnected world, the growth of threats to industrial control systems (ICS) and operational technology (OT) continues to rise, putting organizations and critical infrastructure at risk of a[…]
Go Beyond the Perimeter: Frictionless Zero Trust With CrowdStrike and Zscaler
With today’s workforce moving outside of the physical office, modern security architectures have moved away from the “hard exterior, soft interior” model where there is a well-defined perimeter that i[…]
One Size Does Not Fit All: Flexible Response Capabilities Matter
If all threats were equal, it might be possible to make the entire remediation process autonomous. But all cybersecurity professionals know that threats and incidents vary in complexity and potential […]
Stop Breaches With Complete Confidence? Customers Say Falcon Complete Can
In our recent blog, “See the COMPLETE Picture: New Study Reveals the Benefits of Fully Managed Detection and Response,” we reviewed Forrester’s analysis that explains how CrowdStrike Falcon® Complete™[…]
How to Shrink Your SOC’s Response Time With Workflows and Real Time Response
As attack surfaces grow and threats become more sophisticated, your SOC team is challenged with detecting, understanding and containing an attack faster than ever to protect the organization from crit[…]
See the COMPLETE Picture: New Study Reveals the Benefits of Fully Managed Detection and Response
“I’ve looked at a number of them. Falcon Complete is the most complete security model I’ve seen.“ — CISO, Building Products What benefits are you seeing for your cybersecurity investments? Are they wo[…]
Who Needs Another Alert? CrowdScore Hunts Attackers Hidden in the Data
There’s another alert. It’s the 587th one that your security operations center (SOC) has received just today. Is it a threat actor working their way through your enterprise, an attack that was success[…]
CrowdStrike Falcon® Intelligence Recon: Mitigating Digital Risk on the Deep, Dark Web and Beyond
Organizations face a myriad of risks brought about by the digital transformation of their business. These risks include digital fraud, data theft exposure, social media impersonations and phishing att[…]
Check for Vulnerability Exposure to CVE-2021-3156 (Baron Samedit) with Falcon Spotlight
A new, significant vulnerability was recently discovered, hiding in plain sight. CVE 2021-3156, also known as Baron Samedit, is considered potentially serious. The Cybersecurity & Infrastructure Secur[…]
CrowdStrike Sets Highest Possible Standard in SE Labs Breach Response Test
At CrowdStrike, our mission is to stop breaches. For us to be successful in our mission, not only do we rigorously test our product internally against the latest real-world threats discovered by the C[…]
CrowdStrike Falcon® Forensics: Ditch Inefficient Incident Response Tools for Good
There’s nothing like the pressure incident responders encounter when an attacker attempts to breach their organization. They often struggle with numerous tools and manual, time-consuming efforts to co[…]
CrowdStrike Falcon® Supports New macOS Big Sur
This year, Apple announced a major overhaul of macOS calling it “the biggest update to design in more than a decade.” The version number jumped from macOS 10.x to 11.0, and it touches every element of[…]
CrowdStrike Integrated Intelligence and Deployment Automation Enhance New AWS Network Firewall
CrowdStrike is thrilled to be attending the AWS re:Invent 2020 virtual event as an AWS Partner Network (APN) sponsor and delighted to be named as a launch partner for the recently announced AWS Networ[…]
Webcast: Unique Security Coalition Aims to Guide Work-From-Home Transition
CSOs, CISOs and security professionals everywhere are contending with a “new normal” due to the global pandemic. Employees are increasingly working from home, an abrupt and often unplanned shift for m[…]
Expert Insights From the Fal.Con 2020 Election Protection Panel
This eye-opening discussion exposes the real threats targeting global election processes and, more broadly, democracies around the world. Shawn Henry, CrowdStrike Chief Security Officer and President […]
Start Your Fal.Con 2020 Experience
Fal.Con 2020 is almost here, and the Fal.Con 2020 virtual experience has already started! You can now log in to the event environment to customize Fal.Con according to your interests and goals — build[…]
CrowdStrike Falcon® Named Best EDR by SE Labs, Delivering 100% Detection, 0% Noise
Proving safety is challenging in any industry, whether you’re talking about automobiles, baby furniture or protective helmets. It requires special equipment and knowledge around how things can fail in[…]
Custom Dashboard Offers Greater Visibility for Zerologon Vulnerability
A serious and potentially dire patch warning has been issued by the Department of Homeland Security (DHS) advisory team, the Cybersecurity and Infrastructure Security Agency (CISA). The alert, labeled[…]
Pandemic Response Presents “Good Timing” for a Security Review, Says CrowdStrike’s Ian McShane
The global pandemic has security pros everywhere grappling with a “new normal.” As if more staff suddenly working remotely hasn’t been enough to deal with, many infosec conferences have gone virtual, […]
Why Cybercrime Remains a Worrying Business Challenge in a COVID-lockdown World
The following is an article that was originally published in Intelligent CIO Magazine and is republished here with its consent. With cybercriminals intent on exploiting organizations to regain access […]
Accelerate Your Digital Transformation With the Falcon Platform’s Unified Approach to Security
CrowdStrike continues to deliver a variety of innovative solutions from trusted technology partners, and we’ve just added three new applications from Illumio, Obsidian and SecurityAdvisor. These appli[…]
Join CrowdStrike at the Black Hat 2020 Virtual Event
Black Hat 2020 will be a virtual event for the first time in its 23-year history, and CrowdStrike is thrilled to be a Titanium sponsor for this iconic conference. Even though this year’s event is virt[…]
Weaponized Disk Image Files: Analysis, Trends and Remediation
Throughout 2019 and the beginning of 2020, the CrowdStrike® Falcon CompleteTM team continuously observed a spike in the delivery of weaponized disk image files. Files such as ISO and IMG were sent to […]
The Human Element of Detection and Response
MITRE’s recent ATT&CK® Evaluation test against Russian adversary COZY BEAR (aka APT29) has raised some interesting questions about the proper role of humans in detecting and understanding sophisticate[…]
Global Survey: The Cybersecurity Reality of the COVID-19 Remote Workforce
For many organizations, the rapid transition to an entirely remote workforce due to shelter-in-place orders has brought on a slew of sudden and profound cybersecurity challenges. On one hand, organiza[…]
CrowdStrike Receives Highest Overall Score in Gartner Peer Insights for EDR for the Second Year in a Row
We did it again. In the May 2020 Gartner Peer Insights “Voice of the Customer” Endpoint Detection and Response Solutions (EDR), CrowdStrike is once again the highest-rated vendor based on overall rati[…]
Which Way Did She Go? Speeding Up Lateral Movement Investigations
One of the biggest challenges facing security investigators is creating a full picture of a threat, piecing together disparate pieces of information that may occur across a range of time and hosts. At[…]
CrowdStrike Falcon® Dominance Evident in MITRE ATT&CK Evaluation With 100% Detection Across All 19 Attack Phases
This week marks the release of results from the second iteration of MITRE’s recurring ATT&CK Evaluation program, and I could not be prouder of how CrowdStrike Falcon® performed. MITRE’s results have o[…]
Online Learning: Staying Ahead of Cyber Threats Anytime and Anywhere
While COVID-19 is requiring many people to remain at home, cyber threats are continuing — and even escalating as adversaries seek to take advantage of the global upheaval resulting from the new corona[…]
On-demand Webcast: CrowdStrike Experts on COVID-19 Cybersecurity Challenges and Recommendations
A new on-demand webcast, “Cybersecurity in the Time of COVID-19,” features CrowdStrike® CTO Mike Sentonas, VP of Intelligence Adam Meyers and Sr. Director of Product Management Brian Trombley as they […]
CrowdStrike Store Partners: Committed to Securing Your Remote Workforce
Due to the global COVID-19 pandemic, an increasing number of workers are sequestered at home while continuing their regular duties using online collaboration tools. Cybersecurity has become a primary […]
Forrester Names CrowdStrike a Leader in the 2020 Wave for Enterprise Detection And Response
“Customers buy an EDR solution for its detection capabilities, and there simply are no other vendors in the space that have an intelligence organization of CrowdStrike’s scale to enable the developmen[…]
CrowdStrike Announces Two New Programs to Help Organizations Secure Remote Workers During COVID-19 Crisis
Extraordinary times call for extraordinary responses. As companies around the world respond to the challenge posed by COVID-19 by recommending or requiring remote work for employees, CrowdStrike wants[…]
CrowdStrike Delivers Protection for Critical Windows Certificate Spoofing Vulnerability
Microsoft recently disclosed a critical vulnerability (CVE-2020-0601) that could be leveraged for a wide range of malicious actions including spoofing trusted websites or software. The word “critical”[…]
CrowdStrike Webcast with Mercedes-AMG Petronas Motorsport Focuses on the Need for Speed in Cybersecurity
An on-demand webcast featuring CrowdStrike Sr. Engineer Zeki Turedi and Mercedes-AMG Petronas Head of IT Matt Harris details why speed, just as in Formula One racing, is a critical element in effectiv[…]
Organizations See Dramatic Reductions in Alert Fatigue With CrowdScore
Organizations face enormous challenges in prioritizing, understanding and responding quickly to a deluge of alerts triggered by a wide range of modern threats. CrowdStrike’s new CrowdScoreTM capabilit[…]
For the Second Year in a Row, CrowdStrike Has Highest Overall Rating Among Vendors Named a November 2019 Gartner Peer Insights Customer’s Choice
In the latest Customer’s Choice recognition for endpoint protection platforms (EPP), CrowdStrike has the highest overall rating among vendors named a November 2019 Gartner Peer Insights Customers’ Cho[…]
Outpacing the Adversary: Three Tips on How Mature Organizations Can Continuously Improve Cybersecurity
A new survey conducted by Lloyds Banking Group reveals that improving cybersecurity ranks as the top concern for banks, edging out last year’s priorities of reducing operating costs and improving cust[…]
New CrowdStrike Report Reveals Organizations’ Attitudes Toward Cybersecurity Readiness
A new report from independent research firm Vanson Bourne titled The 2019 Global Security Attitude Survey studies how organizations assess their cybersecurity readiness in the face of an increasingly […]
New Apps in the CrowdStrike Store Expand Value for Customers
The CrowdStrike® Store continues to execute on its vision of extending the power of the Falcon platform for our customers and partners. Today, we are proud to announce an exciting lineup of new third-[…]
Forrester Total Economic Impact™ Study Shows 316% ROI for CrowdStrike Falcon®
Payback Period of Under Three Months “CrowdStrike delivers superior exploit and behavioral detection capabilities, and its OverWatch service provides proactive threat hunting to uncover the most steal[…]
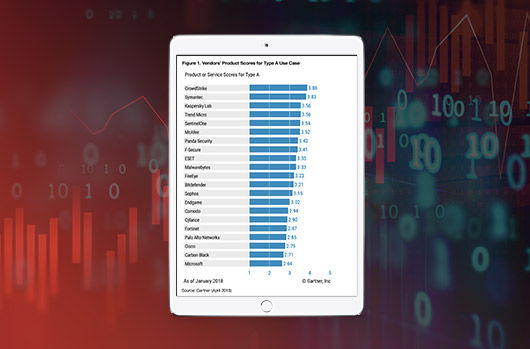
CrowdStrike Scores Highest Overall for Use Case Type A or “Forward-Leaning” Organizations in Gartner’s 2019 Critical Capabilities for Endpoint Protection Platforms
Gartner just released its 2019 Critical Capabilities for Endpoint Protection Platforms (EPP) report, showing CrowdStrike® with the highest overall score out of 20 vendors for Type A use case. Type A o[…]
Falcon Complete and CrowdStrike Adversary Emulation Pen Testing Recognized as “Cyber Catalysts” in Marsh Cyber Risk Evaluation
Marsh, one of the world’s leading insurance broker and risk adviser, has named CrowdStrike® as a recipient of its first-ever “Cyber Catalyst" designations. CrowdStrike achieved designations for Falcon[…]
CrowdStrike Named a Leader in the 2019 Forrester Wave for Endpoint Security Suites
CrowdStrike secures the highest possible score in seventeen criteria and the top score overall in the strategy category. “CrowdStrike has the most fully featured endpoint security suite with an EDR li[…]
CrowdStrike Store’s New Dragos App Provides Early Visibility of OT Threats Across IT Environments
Traditionally, information technology (IT) and operational technology (OT) environments have been separate, with their networking and security requirements managed by two different teams within the or[…]
CSO Australia: How Nation-State Cyber Wars Increase Business Risk
A recent article in CSO Australia by David Braue is titled “Businesses Risk Becoming “Collateral Damage” in Nation-State Cyber Wars.” The author interviewed CrowdStrike CSO Shawn Henry on why organiza[…]
CrowdStrike Positioned as a Magic Quadrant “Leader” and Furthest for “Completeness of Vision” in the 2019 Gartner Magic Quadrant for EPP
We are thrilled and honored to be positioned as a “Leader” in the 2019 Gartner Magic Quadrant for Endpoint Protection Platforms (EPP). This recognition from Gartner, which we believe is among the most[…]
CrowdStrike Receives Highest Ranking in Recent Third-Party Tests
We are thrilled that the CrowdStrike Falcon®® platform continues to receive stellar evaluations in third-party testing. Our recent participation in several highly-regarded industry evaluations reflect[…]
Credential Theft: An Adversary Favorite
Stealthy and Powerful CrowdStrike frequently observes adversaries using valid account credentials across the attack lifecycle. In fact, credential dumping, an illegal way to obtain account credentials[…]
Noise Is the Problem — CrowdScore Is the Solution
Sometimes we humans are faced with problems so pervasive and persistent that it is difficult to even recognize them as problems. We assume the situation cannot be improved and simply fail to seek a re[…]
Why Machine Learning Is a Critical Defense Against Malware
Dr. Sven Krasser, CrowdStrike® chief scientist, has called machine learning (ML) the first line of defense against modern threats. That statement, which he made a couple of years ago, is even truer to[…]
Where Do CISOs Belong in the IT Org Chart?
This article originally appeared on InformationWeek.com and is published here with their permission. As security breaches continue to impact the bottom lines of major businesses and institutions aroun[…]
How to Fill the Cybersecurity Skills Gap With Homegrown Talent
The Challenge The increasing sophistication and frequency of adversary infiltration and exploit attacks has forced many organizations to play a continuous high-stakes version of “whack-a-mole” with th[…]
Dark Reading: CrowdStrike’s Adam Meyers on eCrime Actors’ Pivot to Ransomware
A recent article on Dark Reading by CrowdStrike VP of Intelligence Adam Meyers is titled “The Big E-Crime Pivot.” It puts forth the argument that cybercriminals “have begun to recognize that enterpris[…]
Best practices for Mobile Device Security
This article appeared in Security Brief, New Zealand and is republished here with their permission. Mobile phones have a huge impact on the day-to-day lives and the way one communicates with the world[…]
ITProPortal: CrowdStrike Discusses Life Beyond Malware
This article, “Life Beyond Malware,” originally appeared on ITProPortal and is published here with their permission. The traditional cybersecurity model is an outdated one, focused on building up the […]
Gartner Report: Prepare for Endpoint Protection Shifting to the Cloud
“The endpoint protection market is undergoing its biggest transformation in the last 20 years.” — Gartner, the leading research and advisory company worldwide In a recent report titled, “Prepare for E[…]
CSO Online: Insights on Cyber Espionage From CrowdStrike VP Mike Sentonas
An article on CSO India titled “Cyber Espionage Shows No Signs of Slowing Down,” by Soumik Gosh, presents CrowdStrike® VP of Technology Strategy Mike Sentonas’ views on the growth of espionage as an o[…]
Going Beyond Malware: The Rise of “Living off the Land” Attacks
This article was originally published on CSO, April 30, 2019 If you’re living off the land, there are a few different methods you can use to survive, but you need to use what you find where you are. Y[…]
CrowdStrike Falcon®: First Endpoint Protection to Integrate Firmware Attack Detection Capability
Today’s endpoint security solutions have been designed primarily to look at the local operating system (OS) and the applications that reside on top of it, remaining blind to computing layers below the[…]
On-Demand Webcast Discusses “Making 60-Minute Remediation a Reality”
A new on-demand webcast features CrowdStrike Vice President of Managed Services Austin Murphy, and Sr. Product Director Con Mallon as they discuss how organizations can leverage technology and speed t[…]
Key Trends From the CrowdStrike 2019 Global Threat Report
Update: CrowdStrike's 2020 Global Threat Report is now available. Download the report to stay ahead of today's adversaries. The CrowdStrike® 2019 Global Threat Report: “Adversary Tradecraft and the Im[…]
ADP Trusts CrowdStrike Falcon® to Protect Payrolls and Workers Around the World
In this blog, former ADP Staff Vice President and Chief Security Officer Roland Cloutier discusses why ADP chose the CrowdStrike Falcon® platform and explains the powerful advantages the CrowdStrike® […]
Formula 1 Racing and Stopping Breaches
What in the world does stopping breaches have to do with Formula One™ racing? Quite a bit, actually. As a long time follower of Formula 1™ racing, I am excited by CrowdStrike's partnership with Merced[…]
Gartner Peer Insights “Voice of the Customer” for Endpoint Protection Platforms Speaks Volumes for CrowdStrike
Gartner just published its Gartner Peer Insights "Voice of the Customer" for Endpoint Protection Platforms report and CrowdStrike® is the highest-rated vendor (4.9 out of 5). Gartner Peer Insights is […]
What’s in Your Wallet? Resource-Draining Cryptojacking Attacks Are on the Rise
The popularity of legitimate cryptomining is being challenged by the rise of cryptojacking — its criminal cousin. The earning potential of a successful cryptojacking attack has made it an attractive p[…]
Visibility and Granular Control: The Secret to Securing USB Devices In the Workplace
Social engineering continues to be exploited by hackers and feared by security teams. Due to attackers’ subtlety and users’ natural curiosity, hackers succeed daily in baiting users to click on a link[…]
Big Data, Graph, and the Cloud: Three Keys to Stopping Today’s Threats
An edited version of this blog was published as an article in Teiss on December 12, 2018. Graph databases are having a bit of a moment in cybersecurity. With recent releases from industry juggernauts […]
MITRE ATT&CK Evaluation Reveals CrowdStrike Falcon® as the Most Effective EDR Solution
CrowdStrike delivers the most proactive detections, visibility, and context in MITRE ATT&CK™ Evaluation testing. At CrowdStrike, we believe strongly in third-party product testing and evaluations. Sin[…]
CrowdStrike Demystifies Threats with MITRE ATT&CK
The MITRE ATT&CK™ framework is an ambitious initiative that is working to bring clarity to how we talk about cyberattacks. CrowdStrike® is proud to support MITRE’s efforts to bring standardization to […]
CrowdStrike Receives Highest Overall Score in the 2018 Gartner Peer Insights Customers’ Choice for EPP
We are excited about some fantastic recognition we received today, when CrowdStrike® was named in the 2018 Gartner Peer Insights Customers’ Choice for Endpoint Protection Platforms. Although the Gartn[…]
Managed Threat Hunting Bridges the Talent Gap
This article was first published on November 4, 2018 in The Security Ledger and is republished with permission. Skilled operators make all the difference in incident response and threat hunting. With […]
CrowdStrike Provides Free Dashboard to Identify Vulnerable Macs
Image above is a screenshot of the CrowdStrike CVE-2018-4407 dashboard for macOS (click for larger image) The recent discovery of the Remote Code Execution (RCE) vulnerability CVE-2018-4407 in Apple’s[…]
OverWatch Insights: Reviewing a New Intrusion Targeting Mac Systems
Mac enterprise networks are not as common as Windows environments. As a result, detailed information about targeted adversary intrusions against Mac networks is somewhat limited compared to other oper[…]
Should You Worry About Software Supply Chain Attacks?
While there is much discussion today about potential weaknesses in the hardware supply chain, given the recent attacks attributed to China, the software supply chain has already proven to be vulnerabl[…]
Is There Such a Thing as a Malicious PowerShell Command?
PowerShell is a scripting language originally designed to automate Windows administrative tasks. In addition to running its native commands, it can call DLL functions, access any .NET framework type o[…]
Leading Global Brands Secure Themselves with CrowdStrike
CrowdStrike® recently recognized several of its valued customers as winners of the first CrowdStrike Customer Excellence Awards. They were announced on September 19 at the Fal.Con POWER UP 2018 cybers[…]
Uncovering The “Unknown Unknowns”: Why Threat Hunting is a Security Must-Have
If you’re living off the land, there are a few different methods you can use to survive, such as setting traps or finding edible plants. However, some animals are too smart to get caught and some plan[…]
Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]
  Since its inception as Qatar’s first private bank in 1974, Commercial Bank has forged a reputation for growth and innovation to attract sophisticated customers in one of the world’s most af[…]
Webcast Offers Guidance on Adopting the DevOps Model Without Sacrificing Security
An on-demand CrowdStrike® webcast titled “Security at the Speed of DevOps” offers an in-depth examination of the security implications that accompany organizations’ rapid adoption of DevOps as they re[…]
CrowdStrike Summer Release Brings New Modules and Features to the Falcon Platform
As CrowdStrike® continues its mission of stopping breaches by harnessing the cloud to deliver the most powerful and effective cybersecurity on the planet, I’m excited to share with you the incredible […]
Global Survey Reveals Supply Chain as a Rising and Critical New Threat Vector
A new global software supply chain survey from CrowdStrike®, conducted by independent research firm Vanson Bourne, reveals that cyberattacks are increasingly targeting the software supply chain, creat[…]
Forrester Names CrowdStrike a Leader in the 2018 Wave for Endpoint Detection And Response
"CrowdStrike understands and articulates the problem of combating sophisticated actors better than anyone." We've always known that to be true, now Forrester has confirmed it. These are the exact word[…]
Don’t Take The Vendor’s Word For It: The Importance of Third-Party Testing
The Buyer’s Dilemma It’s no secret that cybersecurity has become a crowded marketplace, particularly in the last several years. The endpoint protection market, for instance, now has more than 140 vend[…]
Taking Protection to a New Level: CrowdStrike Announces its $1 Million Breach Prevention Warranty
Although many industries have long offered product warranties to assure customers the products they purchase will function as advertised, this has not been true for cybersecurity. When a security prod[…]
CrowdStrike Scores Highest Overall for Use Case Type A or “Forward Leaning” Organizations in Gartner’s Critical Capabilities for Endpoint Protection Platforms
Gartner just released its inaugural Critical Capabilities for Endpoint Protection Platforms (EPP) report, showing CrowdStrike® with the highest overall score, out of 21 vendors for use case Type A or […]
Don't Even Think of Complying with the New NIST Cybersecurity Framework!
Guest blogger Steve Chabinsky, former CrowdStrike General Counsel and Chief Risk Officer, now serves as Global Chair of the Data, Privacy and Cybersecurity practice at White & Case LLP. For those not […]
Falcon Prevent Free Trial: Because Evaluating Next-Gen AV Solutions Should Be Fast and Easy
There is a sea change underway in the security industry. Organizations are moving away from legacy antivirus (AV) solutions because they are too slow, too complex and ultimately ineffective against mo[…]
Building Cybersecurity from the Ground Up — Part 2: The Technology Basics
Part 1 of this series, “The Business Perspective,” examined how to build a cybersecurity capability from the ground up by starting with the basic governance aspects of information security. It explain[…]
CrowdStrike on Dark Reading: Why “Breakout Time” Is Critical to Your Security Strategy
A new article by CrowdStrike Director of Product Marketing Scott Taschler, published on Dark Reading, discusses how the key metric known as “breakout time” sets the bar for how quickly security teams […]
Building Cybersecurity from the Ground Up — Part 1: The Business Perspective
“Where should I invest in security if I’m starting from scratch?” That’s a question CrowdStrike Services clients frequently ask us. We hear it from small businesses trying to weave security into their[…]
A Hunter’s Perspective: Detecting Formbook 3.8 Activity in Your Environment
Formbook is a tool that has been available for purchase from criminal forums for several years — it’s used to steal information from a victim’s environment. Recently CrowdStrike® Falcon Intelligence™ […]
GDPR Enforcement is Right Around the Corner — Is Your Organization Prepared?
The impending enforcement of the General Data Protection Regulation (GDPR) on May 25, 2018 has many organizations scrambling to ensure compliance before the clock runs out. Since cybersecurity will be[…]
The Hole in the Donut: Franchise Relationships Create Unique Cybersecurity Risks
In February 2018, the nation of Canada experienced an attack on a popular franchise chain that didn’t make the front page of most major newspapers. Treasured donut and coffee franchise, Tim Hortons, e[…]
CrowdStrike CTO: The Third Phase of Cyber Conflict and How to Address It
In a recent article on LinkedIn titled, “Addressing The Third Generation of Cyber Conflict,” CrowdStrike CTO and Co-founder Dmitri Alperovitch offers his analysis of the evolution of cyber conflict, d[…]
CrowdStrike Falcon® Offers Plug-and-Play Integration with ServiceNow
Since the inception of the CrowdStrike Falcon® platform, an API-first approach has always been a key strategy for providing customers with a robust solution that can easily integrate into any existing[…]
CrowdStrike CEO George Kurtz in Forbes: Creating a Balanced Cybersecurity Portfolio
Technology expert and author Dan Woods has published a series of articles in Forbes magazine that explore how companies can build effective, balanced cybersecurity portfolios. In his latest article in[…]
CrowdStrike Provides Spectre-Meltdown Dashboard to Help Customers Mitigate CPU Flaws
Click here for larger image The Spectre-Meltdown CPU design flaws continue to make news. CrowdStrike® security expert Alex Ionescu addressed these flaws in a recent blog, explaining that Spectre-Meltd[…]
New Gartner Report Redefines Endpoint Protection for 2018
A recent report from IT research and analysis firm Gartner offers new insights and perspective on the current state of endpoint security. In its report, titled “Redefining Endpoint Protection for 2017[…]
The 6 Requirements of True Next-Gen Endpoint Protection
If there’s one term that vendors love to attach to their security solutions, it’s “next-gen.” This is especially true for endpoint security products, which are routinely marketed as next-gen, or simpl[…]
5 Steps Endpoint Security Buyers are Taking to Improve Protection
For almost two decades, the world of endpoint security was business as usual. Early on, the products worked pretty well, but in the past two years, the market started to change. As the bad guys found […]
How Artificial Intelligence is Becoming a Key Weapon in the Cybersecurity War
This blog originally appeared as an article in PC World on October 13, 2017, written by Michael Sentonas, VP Technology, CrowdStrike®. It is reproduced with their permission. In the last 12 months, 60[…]
HIPAA PHI Getting Tougher to Safeguard but Compliance is Still Critical
The Health Insurance Portability and Accountability Act (HIPAA) has big consequences for organizations of all sizes. Companies and institutions that don’t guard employees’ healthcare data may be subje[…]
The Right Endpoint Detection and Response (EDR) Can Mitigate Silent Failure
In a recent webcast, “The Maturing of Endpoint Detection and Response (EDR): Choosing the Right Solution,” Forrester Senior Analyst Chris Sherman and CrowdStrike Senior Director of Product Marketing C[…]
Address Zero-Day Threats Long Before an Attack Occurs
A recent interview with CrowdStrike VP of Product Marketing Dan Larson, for the CyberWire Daily Podcast, focuses on “zero-day” attacks and how organizations can prepare for these stealthy and damaging[…]
Preventing Sophisticated Attacks: Tips From a Real-World Incident Responder
Robin Jackson, principal consultant for CrowdStrike, has had extensive experience investigating some of today’s most prolific threat actors. He’s also done security research for a number of organizati[…]
When Worlds Collide: The Impact of Cyber Threats Crossing Over to the Physical World
A recent article in Information Age, titled “As the digital and physical worlds collide it’s time for a security refresh,” offers cybersecurity readiness advice from Mike East, CrowdStrike’s vice pres[…]
CrowdStrike CEO and Co-founder George Kurtz Wins Ernst & Young Entrepreneur of the Year for Security
CrowdStrike added a prestigious award to its many achievements when CEO and co-founder, George Kurtz, was named Ernst & Young (EY) Entrepreneur of the Year in the security category for Northern Califo[…]
Defining the Value of Machine Learning for Endpoint Protection
Computer Business Review recently published an interview with CrowdStrike® Chief Scientist Dr. Sven Krasser, “Machine learning in cybersecurity: The first line of defense against modern threats,” in w[…]
Why IT Hygiene is Critical to Your Cybersecurity Readiness
Decluttering Your IT “Desk” There is an old adage that claims “a messy desk is the sign of genius.” Although many of us desk jockeys live by this creed, applying the “pile-system” (organization by cre[…]
Key Characteristics of Modern Fileless Attacks
One of the findings in the 2017 Verizon Data Breach Investigations Report (DBIR) is that only 51 percent of cyberattacks involve malware. The remaining 49 percent represent a major vulnerability conce[…]
SANS Institute Reviews CrowdStrike Falcon® Endpoint Protection
SANS Institute analysts have published a review of the CrowdStrike Falcon® platform, offering valuable third-party insight into Falcon capabilities to protect organizations from today’s most dangerous[…]
Approaching Zero Dwell Time: A Strategy for Finding and Stopping Attackers Before They Do Damage
The trouble with dwell time Dwell time, the period between when an attack occurs and when it is discovered, continues to be a serious problem for security professionals. The most recent Ponemon cost o[…]
CrowdStrike Falcon® Prevents WannaCry Ransomware
Blog updated: May 14th In this screenshot example from the Falcon UI, the detection process tree shows that the malicious file associated with WannaCryptor was launched from explorer.exe. The global r[…]
A Primer on Machine Learning in Endpoint Security
Although machine learning (ML) isn’t a new concept — it actually dates back to the origins of the computer itself — it has received more attention lately as cybersecurity vendors increasingly extol it[…]
Securing the Mac-Based Organization
Though PCs still dominate the workplace, Macs continue to gain ground as the platform of choice for many organizations. As an indication of this growing Mac popularity, an article in Computerworld sta[…]
W-2 Phishing Scam Adds a New Twist to Wire Transfer Fraud
Organizations have long been aware of their vulnerability when it comes to email and yet phishing scams continue to be profitable, as criminal hackers develop more sophisticated methods for thwarting […]
Understanding Indicators of Attack (IOAs): The Power of Event Stream Processing in CrowdStrike Falcon®
Event Stream Processing (ESP) has been a central component of CrowdStrike Falcon®’s IOA approach since CrowdStrike's inception. In this post we'll take a closer look at ESP — along with its utility an[…]
The Economics of Ransomware: How SCADA/ICS Changes the Equation
Recent reports of SCADA/ICS proof-of-concept ransomware have spurred fresh discussion on the topic. Few threats exceed the level of concern that ransomware generates in the minds of corporations. Ther[…]
Dark Reading: Why Ransomware Continues to Be a Serious Threat
A recent article on DarkReading.com, titled “4 Reasons Why You Should Take Ransomware Seriously,” outlines the persistence of ransomware as a significant threat to organizations, and explains why it w[…]
CrowdStrike Named "Visionary" in Gartner Magic Quadrant
"Visionaries not only believe that the impossible can be done, but that it must be done." — Bran Ferren. I am thrilled to announce that Gartner has named CrowdStrike a “Visionary” in the 2017 Magic Qu[…]
CrowdStrike Releases New Update To Falcon Orchestrator
Earlier this year, CrowdStrike released Falcon Orchestrator as a contribution to the open source community. By leveraging the robust Falcon Connect API ecosystem, organizations can easily extend the F[…]
Multi-Layered Prevention for the Endpoint
Benjamin Franklin wisely stated that, “An ounce of prevention is worth a pound of cure.” In keeping with this timeless principle, one can’t help wondering what is required to provide appropriate preve[…]
CrowdStrike and NIST 800-53: Now That’s What I Call a “Twofer”
“Twofer” has entered into the lexicon of everyday use. The Urban Dictionary defines it as the opportunity to receive the value of two, for the price, effort or quantity of one. Who wouldn’t find that […]
The Three Steps of Proactive Threat Hunting
Security teams in the private and public sector are increasingly recognizing the need to actively “hunt” for threats targeting their organizations. Larger, well resourced organizations may have the ab[…]
CrowdStrike evaluated in Gartner’s Comparison of Endpoint Detection and Response Technologies and Solutions
Leading analyst firm Gartner has recently published a comparative assessment called Comparison of Endpoint Detection and Response Technologies and Solutions*. This is the first direct competitive anal[…]
Moving beyond Indicators of Compromise (IOCs)
For the last few years, the security industry has become very enamored with Indicators of Compromise (IOCs) as a way to detect targeted intrusions and adversaries that are flying right past traditiona[…]
Can't Protect Your Data from Ransomware? Think Again.
All too often, I hear from executives of large and small organizations that aside from targeted attacks, impact from ransomware is their number one concern. That impact was starkly highlighted earlier[…]
4.0 Another Brick In The CryptoWall
Introduction For as long as there have been people using the World Wide Web, criminal groups have tried to extort money for performing or withholding some type of action. One of the earliest threats w[…]
What Sets Falcon Apart: Intelligent Host Sensors
It can be difficult to distinguish between “next-generation” endpoint security solutions currently available. Usually the technology lags marketing by a significant margin, and the marketing mostly so[…]
New Protection Capability of Falcon for Mac: Improving Security With SUIDGuard
A comprehensive Next-Generation Endpoint Protection strategy shouldn’t just be about reacting and responding to threats, but also be complemented by the ability to prevent such threats from successful[…]
Top 5 Cybersecurity Mistakes Companies Make and How to Avoid Them
Cybersecurity requires a holistic organizational approach. From the leadership to each rank-and-file employee, a concerted effort must be maintained to establish, execute and follow-through with a pla[…]
Brian Kelly, CSO of Rackspace, Shares Why He Chose CrowdStrike
  When you’re in charge of protecting not only your company’s critical business information, but also that of your company’s customers, there’s no option for a security breach. Brian Kelly, C[…]
Healthcare IT Security in the Spotlight: HIMMS 2015
April is an unbelievably busy month for IT security professionals. In addition to daily online combat with bears, kittens, pandas, and other adversaries, this month is full of security conferences. Fr[…]
Adapting Cyber Security in a New Era of Corporate Destruction
Corporations suffered more cyber attacks in 2014 than ever before, causing the loss of business intelligence and personally identifiable information at an alarming rate. As a result, confidentiality i[…]
The Prevention Continuum: Preventing Silent Failure
Many of my team members know that one of my favorite parts of running CrowdStrike is meeting with customers. It’s always fascinating to hear from customers about the challenges they face on a day-to-d[…]
Data Science & Machine Learning 101: Hunting the Unknown
Over the past year, the security industry has seen a renewed interest in Machine Learning and related techniques. The increased availability of threat and intelligence feeds has contributed to this tr[…]
Hunting Badness on OS X with CrowdStrike's Falcon Real-Time Forensic Capabilities
In this blog post, we’ll take a look at an example of a typical targeted attack with OS X malware as well as discover how to hunt for it in CrowdStrike’s Falcon Endpoint Activity Monitoring (EAM) appl[…]
Attending Black Hat USA 2013?
Attending Black Hat USA 2013? From briefings and trainings to adversary detections and book signings, CrowdStrike will be there in full force! See below for a full list of events to see CrowdStrike in[…]
- 1
- 2
- 3
- 4
- ...
- 32
- >





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)