CrowdStrike Falcon Next-Gen SIEM Unveils Advanced Detection of Ransomware Targeting VMware ESXi Environments

- CrowdStrike Falcon® Next-Gen SIEM enables companies to search, investigate and hunt down threats, including detection of advanced ransomware targeting VMware ESXi
- Initial access to the ESXi infrastructure1 is typically gained through lateral movement using valid credentials
- eCrime actors target and deploy ransomware in ESXi environments to increase the impact and scale of their attacks, which can be devastating for organizations
CrowdStrike Falcon Next-Gen SIEM, the definitive AI-native platform for detecting, investigating and hunting down threats, enables advanced detection of ransomware targeting VMware ESXi environments.
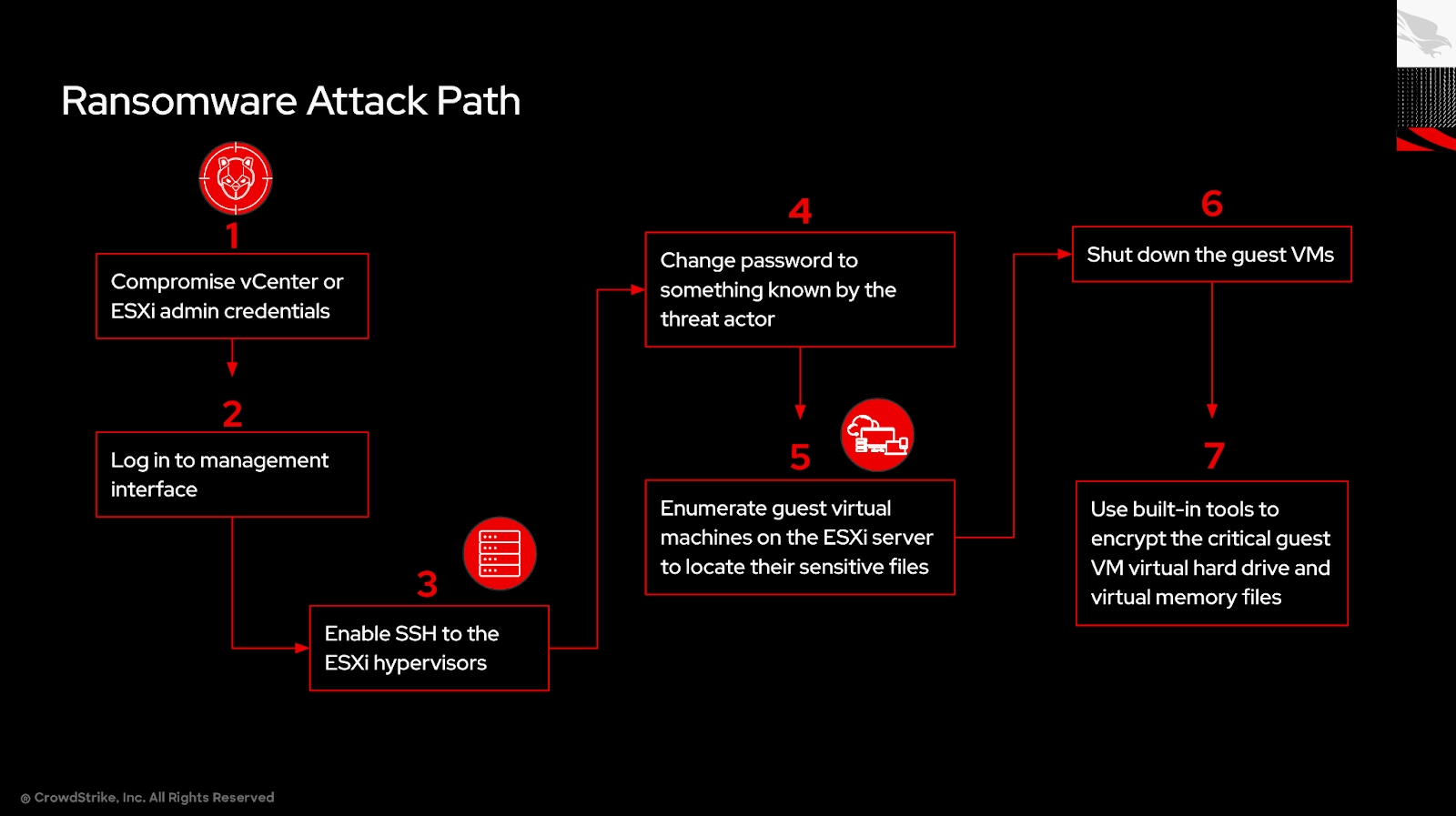
CrowdStrike has observed numerous eCrime actors exploiting ESXi infrastructure to encrypt virtual machine volumes from the hypervisor to deploy ransomware in organizations. Access to ESXi infrastructure typically takes place as part of lateral movement. For example, SCATTERED SPIDER often gains initial access to a Microsoft Entra ID identity via social engineering and then uses this identity to access internal information repositories such as SharePoint to search for ESXi related credentials.
CrowdStrike refers to this tactic to deploy ransomware as “Hypervisor Jackpotting,”2 as eCrime actors can use ESXi hosts to rapidly expand the scope of affected systems.
Falcon Next-Gen SIEM can ingest ESXi logs to reveal evidence of attacker activity, detect suspicious behavior related to use of encryption commands and tooling in near-real time, audit configuration changes and events indicative of early signs of pre-ransomware activity, and detect logins from malicious IP addresses to create and raise incidents for investigation.
Here, we provide an overview of how Falcon Next-Gen SIEM detects ransomware targeting ESXi environments.
Start With Log Forwarding and Configuration
Forwarding ESXi logs to Falcon Next-Gen SIEM can help detect ransomware targeting ESXi environments. By ingesting and alerting on authentication and shell logs that ship with ESXi, we can find evidence of attackers gaining interactive shell access to the ESXi servers, running basic enumeration commands, shutting down virtual machines and using built-in tools like openssl to encrypt the virtual machine volumes.
We recommend using a syslog aggregation point, like the CrowdStrike® Falcon LogScale™ Collector, to forward logs to Falcon Next-Gen SIEM. Detailed instructions for doing this can be found in the CrowdStrike Tech Center.3
Once your log collector is set up, you can configure the ESXi infrastructure to forward the logs to your log collector. The default configuration for syslog for VMware ESXi 7.x and VMware vCenter 7.x is sufficient to get the correct logs to the unified, AI-native CrowdStrike Falcon® platform. You can find the instructions on how to enable remote syslog forwarding in VMware’s knowledge base.4
Detect the Use of Built-In Encryption Tools
Most of the activity prior to the encryption of critical virtual machine guest files could potentially be normal behavior like listing and shutting down virtual machines. These are important events to capture in an incident, but they are not indicative of an attack on their own.
To create a detection, we need to identify an event with a high enough confidence. The use of a tool like openssl with the encrypt option (enc) being run from the command line on critical guest virtual machine files is a high-confidence event that indicates something malicious is happening in our environment.
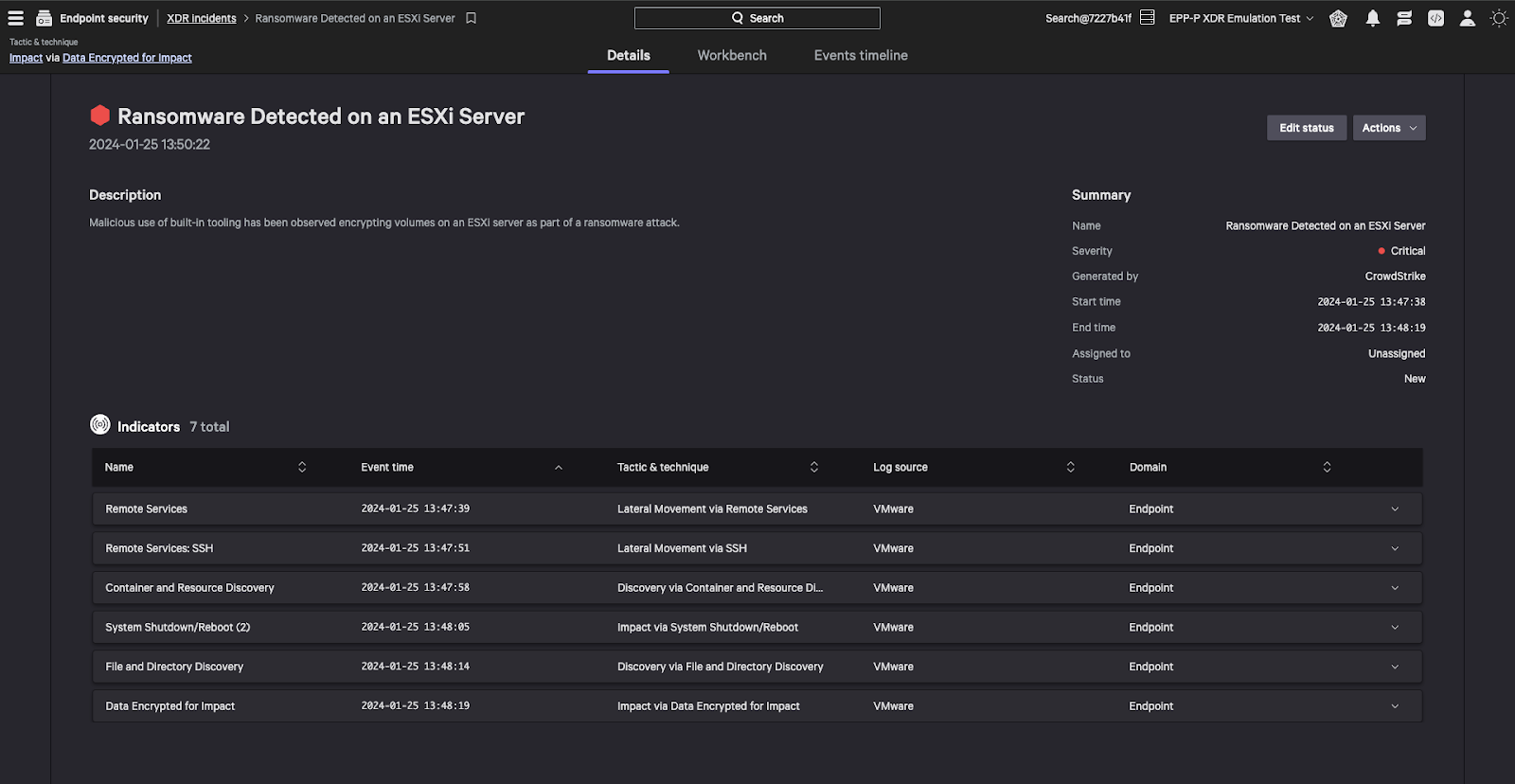
Falcon Next-Gen SIEM will detect this activity in near real time and create an incident for you. It will also gather surrounding activity that has happened on that host and include it in the incident.
In this detection, we see the use of openssl to encrypt sensitive files, the SSH connection, some virtual machine enumeration and the virtual machines being shut down before encryption.
Gain Insights Into Early Ransomware Signs
Detecting an in-progress attack within your environment is critical, but it is always better to get insights into a pending attack before it starts. We can look for configuration changes to an environment, especially those that don’t comply with best practices or that degrade the security posture of the environment.
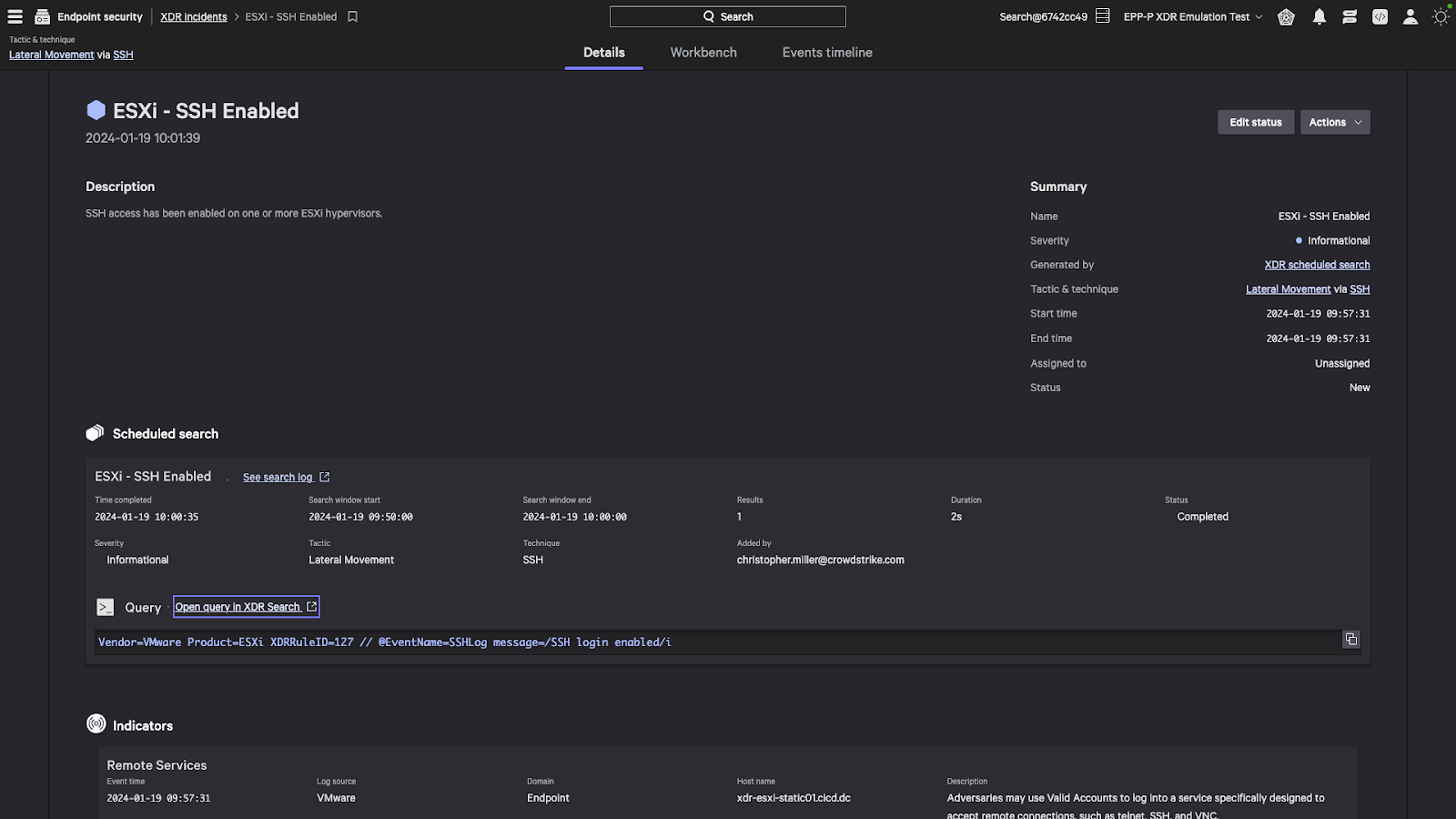
One easily detectable signal would be if a user enables SSH on one of your servers running ESXi. In a best-case scenario, this is an auditable event that the security team can confirm is legitimate behavior. In a worst-case scenario, it is the first tip that someone has compromised your ESXi infrastructure. We can easily surface this activity by creating a scheduled search looking for the specific indicator. Running it on a short interval with an overlapping time period will ensure we get timely notifications without missing events.
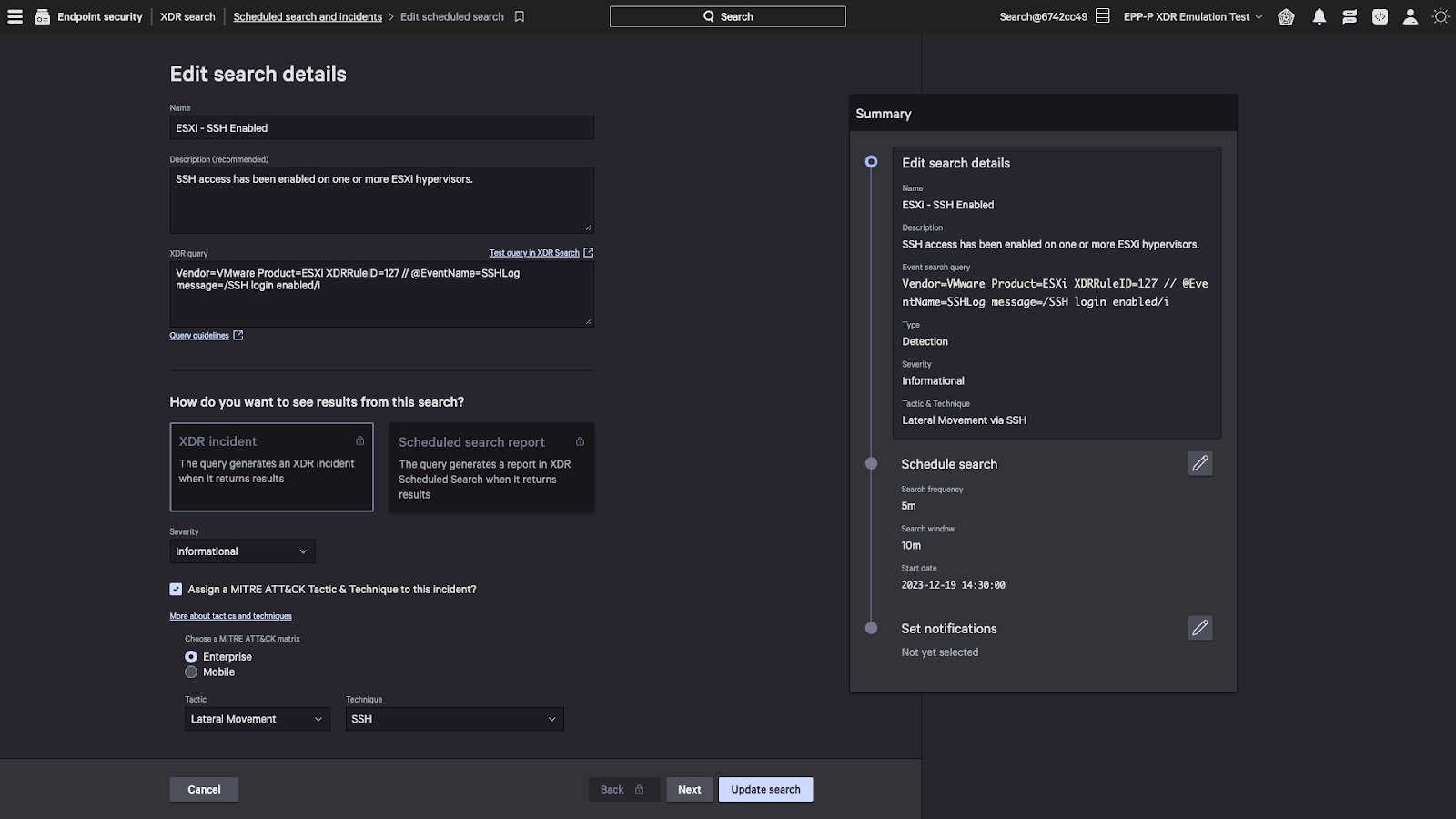
Figure 3. Extended detection and response (XDR) scheduled search configuration in the Falcon platform (click to enlarge)
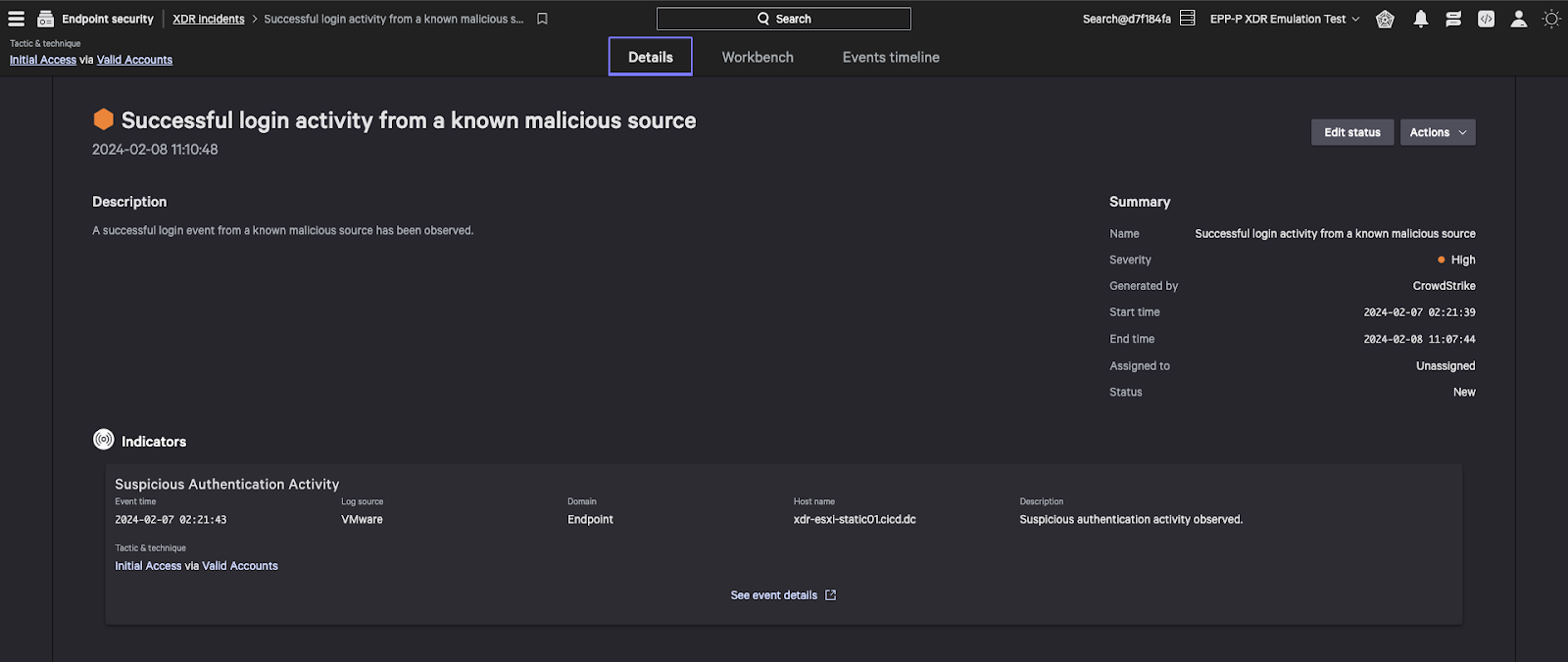
Reveal Unauthorized Logins from Malicious IP Addresses
Another indicator of a pending attack is the detection of logins to the ESXi management console that come from known malicious IP addresses where the console is purposely or accidentally exposed to the internet. Falcon Next-Gen SIEM leverages CrowdStrike’s integrated threat intelligence to identify any known indicators of compromise (IOCs) in critical data. By combining this with the ESXi login entries sent to the Falcon platform, we can detect the login attempts from known malicious sources.
CrowdStrike Falcon Next-Gen SIEM Exposes Ransomware Targeting ESXi
By leveraging Falcon Next-Gen SIEM, you can provide your organization with multiple layers of detections, get unparalleled visbility into your ESXi infrastructure and get ahead of adversaries. Falcon Next-Gen SIEM leaves adversaries targeting ESXi environments with nowhere to hide, detecting suspicious behavior as early as possible, preventing attacks and stopping breaches.
Additional Resources
- Learn how to stop breaches with Falcon Next-Gen SIEM by visiting the webpage.
- Join our next biweekly next-gen SIEM showcase to view a live demo of Falcon Next-Gen SIEM.
- Download the CrowdStrike eBook, 8 Things Your Next SIEM Must Do, to understand the critical capabilities to look for when evaluating SIEM solutions.
- See Falcon LogScale in action by watching this fast-paced demo.
Sources
- https://www.crowdstrike.com/blog/carbon-spider-sprite-spider-target-esxi-servers-with-ransomware/
- https://www.crowdstrike.com/blog/hypervisor-jackpotting-ecrime-actors-increase-targeting-of-esxi-servers/
- https://www.crowdstrike.com/blog/tech-center/importing-logs-log-collector/
- https://kb.vmware.com/s/article/2003322