- CrowdStrike’s Advanced Memory Scanning detected BRc4 execution in the wild.
- CrowdStrike has integrated new indicators of attack (IOAs) for modern endpoint detection and response (EDR) evasion techniques.
- CrowdStrike’s best-in-class detection content targets suspicious processes using Advanced Memory Scanning.
As CrowdStrike’s Advanced Memory Scanning capability has matured, so have its applications. CrowdStrike detection engineers and researchers work tirelessly to ensure the CrowdStrike Falcon® platform’s detection content stays ahead of adversaries. The following case study describes how CrowdStrike leverages memory scanning in combination with new IOAs to provide world-class protection to our customers.
Case Study from the Field
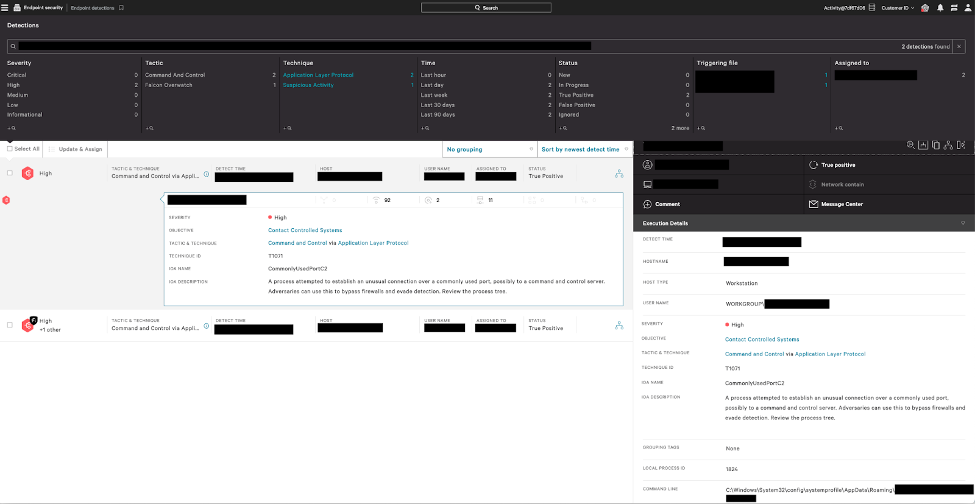
A recent intrusion at a telecommunications customer demonstrates the effectiveness of the Falcon platform at alerting on a pre-existing compromise, as well as multiple attempts by the threat actor to move laterally across their network, establish new persistence and gain a foothold via the commercial red-teaming and adversarial attack simulation tool Brute Ratel C4 (BRc4). When the threat actor attempted to use BRc4, the Falcon platform detection capability prevented the malicious activity, allowing the CrowdStrike® Falcon OverWatch™ managed threat hunting team and CrowdStrike Falcon® Complete managed detection and response (MDR) team to secure the endpoint and analyze the adversary tactics, techniques and procedures (TTPs).
CrowdStrike provides a memory scanning capability that can identify threat actors that execute tradecraft in-memory. In this case study, we discuss attempts by the adversary to load BRc4, how the CrowdStrike team found it, and what new in-memory detection capabilities we now provide to our customers.
BRc4 is a commercial attack emulation tool that first appeared in December 2020 and is similar in purpose to other tools such as Cobalt Strike, Sliver and Mythic. It was designed to incorporate features by default to avoid detection by EDR and antivirus (AV) capabilities, and it deploys agents called “Badgers” to facilitate an adversary’s objectives across the entire kill-chain including lateral movement, privilege escalation and persistence (https://attack.mitre.org/software/S1063/).
During analysis of this intrusion, it was determined an unmanaged endpoint was used to establish a beachhead using a malicious binary. At the time of execution, this activity was unknown to the customer — however, once the Falcon sensor was installed, the customer gained visibility into the malicious behavior occurring within their environment. The Falcon platform immediately identified suspicious network traffic coming from two binaries: one located in the Users AppData directory and another running under the SYSTEM profile.
Investigation identified a related intrusion activity on another endpoint five days earlier, where the Falcon platform had detected a cluster of suspicious operations including indicators of reconnaissance via a webshell, copying of malicious binaries to the endpoint, and attempts at persistence via registry modifications. The Falcon sensor successfully killed and quarantined the malware and blocked the registry modifications.
The adversary returned to this same endpoint a few days later and attempted to gain another foothold. In this incident, they remotely copied multiple remote access trojans (RATs) from another unmanaged endpoint to C:\Windows. Once again, the Falcon sensor prevented and quarantined the malware and blocked modification attempts to the HKCU\Environment\UserInitMprLogonScript registry key used for persistence at system boot.
Using valid credentials (T1078.002), the threat actor then copied several binaries to a sub-directory of %APPDATALOCAL% including Microsoft Windows netsh.exe, a malicious, packed (via VMProtect1) DLL masquerading as a legitimate copy of Microsoft’s ifmon.dll, and an encoded BRc4 Badger v1.62 payload, cache.dat. A subsequent comparison of the malicious DLL and the benign Microsoft version determined the file metadata is largely duplicative, except for a substantial file size difference.
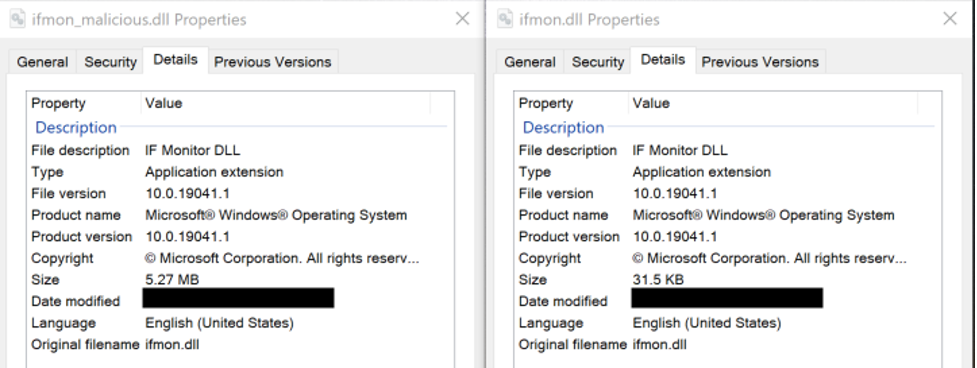 Figure 4. A comparison of the file meta data between the malicious
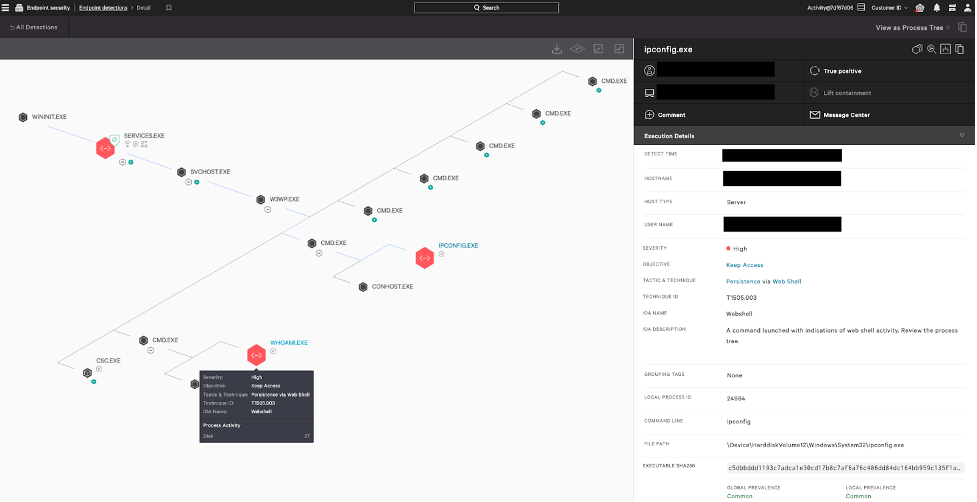
Figure 4. A comparison of the file meta data between the malicious ifmon.dll (left) and the non-malicious ifmon.dll (right) (click to enlarge)Finally, the threat actor executed netsh.exe, which forced the malicious ifmon.dll to be loaded into process memory via DLL sideloading (T1574.002). The DLL decoded the BRc4 payload and transferred control of netsh.exe to BRc4 Badger. Once loaded, Falcon’s Advanced Memory Scanning promptly detected Badger in-memory and successfully prevented and killed the netsh.exe process.
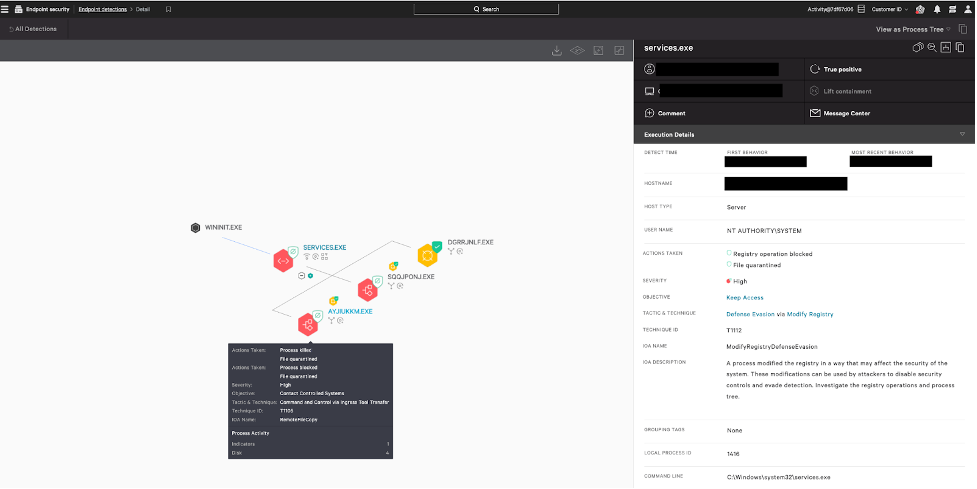
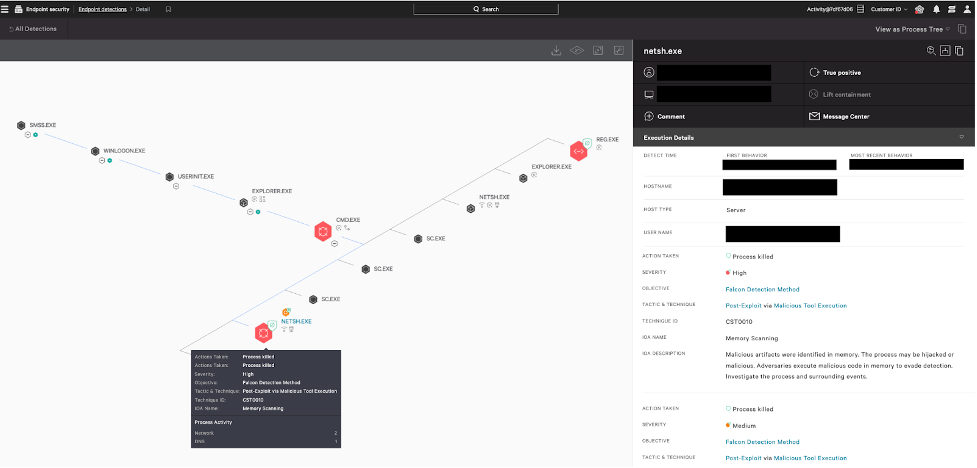 Figure 5. Prevented
Figure 5. Prevented reg.exe persistence and netsh.exe DLL sideload of BRc4 loader (click to enlarge)How CrowdStrike Is Protecting You
As EDR solutions increasingly cover fileless attacks and suspicious Windows API usage, attacker behavior is constantly evolving to implement alternative Reflective Code Loading (T1620) and Process Injection (T1055) methods. Attackers are leveraging OS-native functionality to covertly establish a foothold on the endpoint and persist within the environment.
Offensive techniques that seek to bypass user mode EDR hooks have become ubiquitous and simple to integrate with existing tooling. Operations such as API unhooking and using system calls abuse the fact that without user-mode API introspection, an EDR solution’s visibility and efficacy may be reduced. EDR bypass techniques are typically used in conjunction with fileless attacks to load implants in-memory.
Acknowledging this, researchers and engineers across CrowdStrike collaborated with the Gap Analysis Team to investigate these trends with the goal of improving detection content that mitigates bypass techniques conducted in user mode. Coupled with Falcon's best-in-class detection content, Advanced Memory Scanning demonstrates an evolution in capability for detecting fileless malware attempting to evade EDR.
Additional Resources
- Read more about Advanced Memory Scanning: Enhances Fileless Attack Detection with Intel Accelerated Memory Scanning Feature.
- Read about a CrowdStrike Falcon feature, Hardware Enhanced Exploit Detection, that leverages a CPU feature, Intel Processor Trace (Intel PT), to detect and prevent code reuse exploits: CrowdStrike Strengthens Exploit Protection Using Intel CPU Telemetry.
- Visit the product website to learn how the powerful CrowdStrike Falcon platform provides comprehensive protection across your organization, workers, data and identities.
- Get a full-featured free trial of CrowdStrike Falcon Prevent and learn how true next-gen AV performs against today’s most sophisticated threats.
- VMProtect is a commercial software protection tool that obfuscates and compresses a binary using a variety of proprietary mechanisms. It can be used legitimately by software applications to enforce copyright but has also been observed used by threat actors to add complexity and time to any reverse engineering or to defeat machine learning products.
- This determination was made through reverse engineering the BRc4 Badger and comparing its capabilities to public documentation and release notes for different BRc4 versions.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)