- Log4Shell, the latest critical vulnerability, found in the Log4j2 Apache Logging Services library, poses a serious threat to organizations
- Active attempts to exploit the vulnerability were identified in the wild, currently making it the most severe threat
- CrowdStrike utilizes indicators of attack (IOAs) and machine learning to protect our customers
- CrowdStrike continues to track and monitor the evolution of Log4Shell and will update and deploy any countermeasures necessary to protect customers
- Organizations using Log4j2 are strongly encouraged to update the library to the latest Log4j2 (2.16.0) version published on December 14, 2021
- No updates or mitigations are required for CrowdStrike Falcon® deployments. For more details, customers can visit our Knowledge Base.
Recent CrowdStrike Intelligence team findings regarding the Log4Shell (CVE-2021-44228, CVE-2021-45046) vulnerabilities indicate wide-ranging impact. CrowdStrike helps protect customers from threats delivered via this vulnerability using both machine learning and indicators of attack (IOAs). Log4Shell is a vulnerability in a prevalent Java library, found everywhere from online games to cloud infrastructure. Active and ongoing attempts to exploit the vulnerability have been observed by CrowdStrike Falcon® OverWatch™. Financially motivated adversaries have quickly adopted publicly available proof-of-concept (POC) code to deploy malicious payloads on vulnerable target systems, with most deployed payloads involving XMRig miners, reverse shells, remote access trojans and botnets.
CrowdStrike uses various mechanisms to protect customers from payloads abusing the Log4j2 vulnerability. CrowdStrike Falcon®'s machine learning and IOAs have been preventing post-exploitation activity since CVE-2021-44228's disclosure. CrowdStrike continues to actively monitor the evolution of Log4Shell and will deploy countermeasures necessary to protect customers from post-exploitation activity as a result of the Log4j2 vulnerabilities.
Vulnerability Impact and Abuse
Log4j2 is an open-source library and part of the Apache Logging Services, written in Java, and used in various frameworks such as Elasticsearch, Flink and Kafka. Since Java is a cross-platform framework, the Log4j2 vulnerability is not limited to applications running on a specific operating system. Without proper mitigations or patching, attackers can use the vulnerability to deploy malware, reverse shells and other threats on impacted systems. Adversaries have started conducting active scanning and exploitation attempts targeting vulnerable systems and services, regardless of the operating system, according to CrowdStrike Intelligence. With Linux playing a critical role in cloud infrastructures, reports of payloads delivered using the Log4j2 vulnerability have revealed that botnets — such as Mirai and Muhstik — started targeting devices just days after the vulnerability became public. Industry reports of other threats targeting operating systems and frameworks vulnerable to the Log4j2 exploitation include beacons — such as Cobalt Strike and Metasploit — being deployed in an attempt to establish a foothold in target environments.
How Customers Can Use Falcon to Hunt for Log4j2
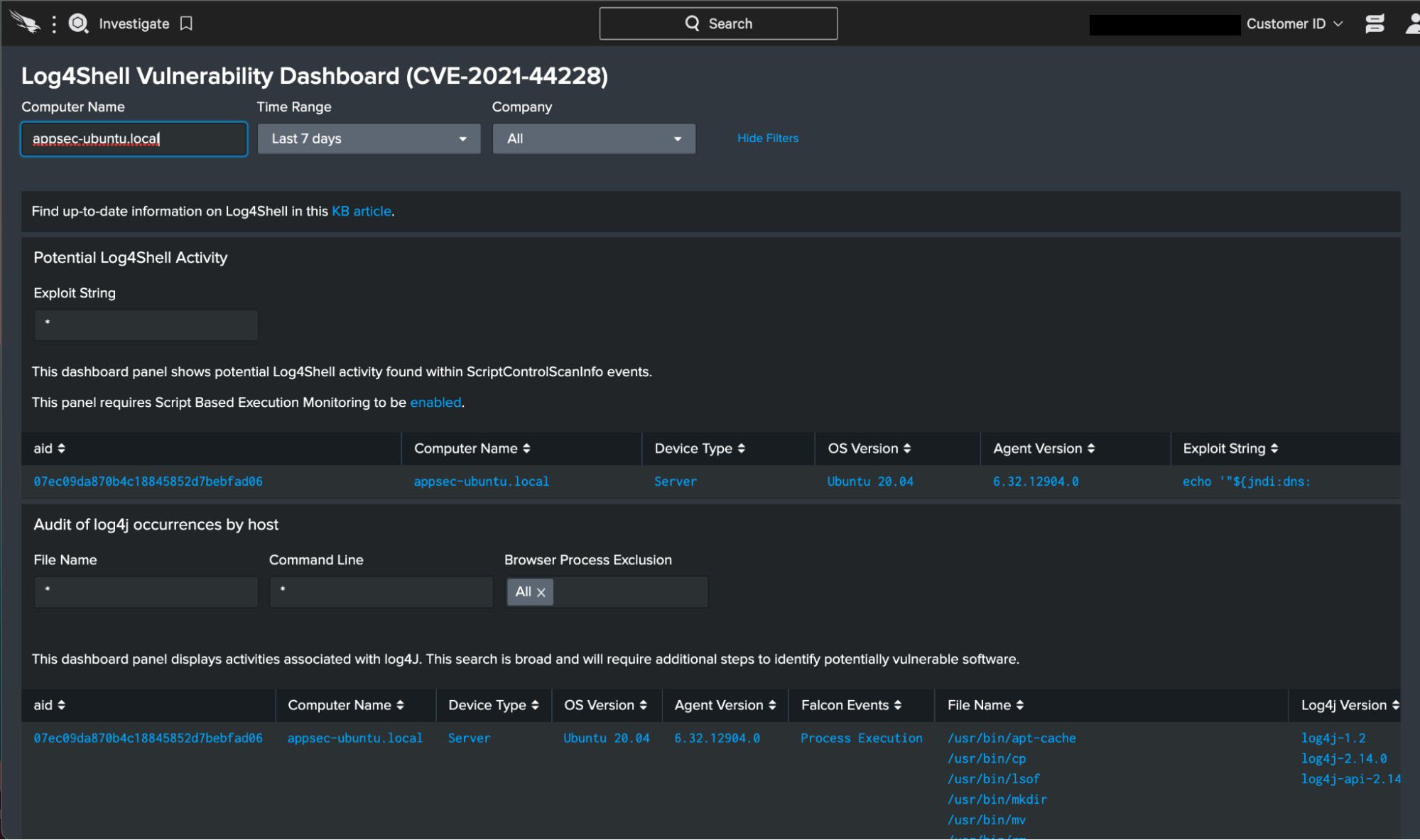
The module Log4j2 is bundled with a large number of third-party software packages. For this reason, hunting for the presence of Log4j2 will not be as simple as looking for its executable, SHA256, or file path. CrowdStrike Falcon® customers can use prebuilt dashboards for all supported operating systems to identify active exploitation of the Log4j2 vulnerability in their environments.
Besides dashboards, customers can use Falcon sensor telemetry and hunt for Log4j2 invocations in ways that correspond to how developers may be using it in their applications. Here is the Falcon Insight™ query to search for Log4j2 usage:
event_simpleName IN (ProcessRollup2, SyntheticProcessRollup2, JarFileWritten, NewExecutableWritten, PeFileWritten, ElfFileWritten)
| search *log4j*
| eval falconEvents=case(event_simpleName="ProcessRollup2", "Process Execution", event_simpleName="SyntheticProcessRollup2", "Process Execution", event_simpleName="JarFileWritten", "JAR File Write", event_simpleName="NewExecutableWritten", "EXE File Write", event_simpleName="PeFileWritten", "EXE File Write", event_simpleName=ElfFileWritten, "ELF File Write")
| fillnull value="-"
| stats dc(falconEvents) as totalEvents, values(falconEvents) as falconEvents, values(ImageFileName) as fileName, values(CommandLine) as cmdLine by aid, ProductType
| eval productType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server", event_platform = "Mac", "Workstation")
| lookup local=true aid_master aid OUTPUT Version, ComputerName, AgentVersion
| table aid, ComputerName, productType, Version, AgentVersion, totalEvents, falconEvents, fileName, cmdLine
| sort +productType, +ComputerName
Here is another query that looks for Log4j2 exploitation attempts:
search index=main event_simpleName=Script* cid=* ComputerName=*
| eval ExploitStringPresent = if(match(ScriptContent,"(env|jndi|ldap|rmi|ldaps|dns|corba|iiop|nis|nds)"),1,0)
| search ExploitStringPresent = 1
| rex field=ScriptContent "(?i)(?<ExploitString>.*j'?\}?(?:\$\{<^}>+:<'->?)?n'?\}?(?:\$\{<^}>+:<'->?)?d'?\}?(?:\$\{<^}>+:<'->?)?i'?\}?(?:\$\{<^}>+:<'->?)?:'?\}?<^/>+)"
| eval HostType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server", event_platform = "Mac", "Workstation")
| stats count by aid, ComputerName, HostType, ExploitString
| lookup local=true aid_master aid OUTPUT Version, ComputerName, AgentVersion
| table aid, ComputerName, HostType, Version, AgentVersion ExploitString
| rename ComputerName as "Computer Name", HostType as "Device Type", Version as "OS Version", AgentVersion as "Agent Version", ExploitString as "Exploit String"
| search "Exploit String"="***"
CrowdStrike Protects Customers Using Machine Learning and Indicators of Attack
CrowdStrike Falcon® mitigations target the tactics and techniques used by adversaries and testers rather than the specific exploits being used. CrowdStrike Falcon® provides coverage from various angles against malicious threats by leveraging machine learning and IOAs to target the behavior of malicious processes or scripts on an endpoint even when dealing with novel threats.
The unique leverage that machine learning brings is that it can identify both known and unknown malware or threats by understanding malicious intent based on the attributes of a file. The CrowdStrike Falcon® sensor leverages both on-sensor and in-the-cloud machine learning in Windows, Linux and macOS platforms to detect and prevent the threats currently deployed by adversaries leveraging the Log4j2 vulnerability, and it is highly effective in protecting against a variety of malware families such as ransomware, cryptocurrency miners, trojans and botnets.
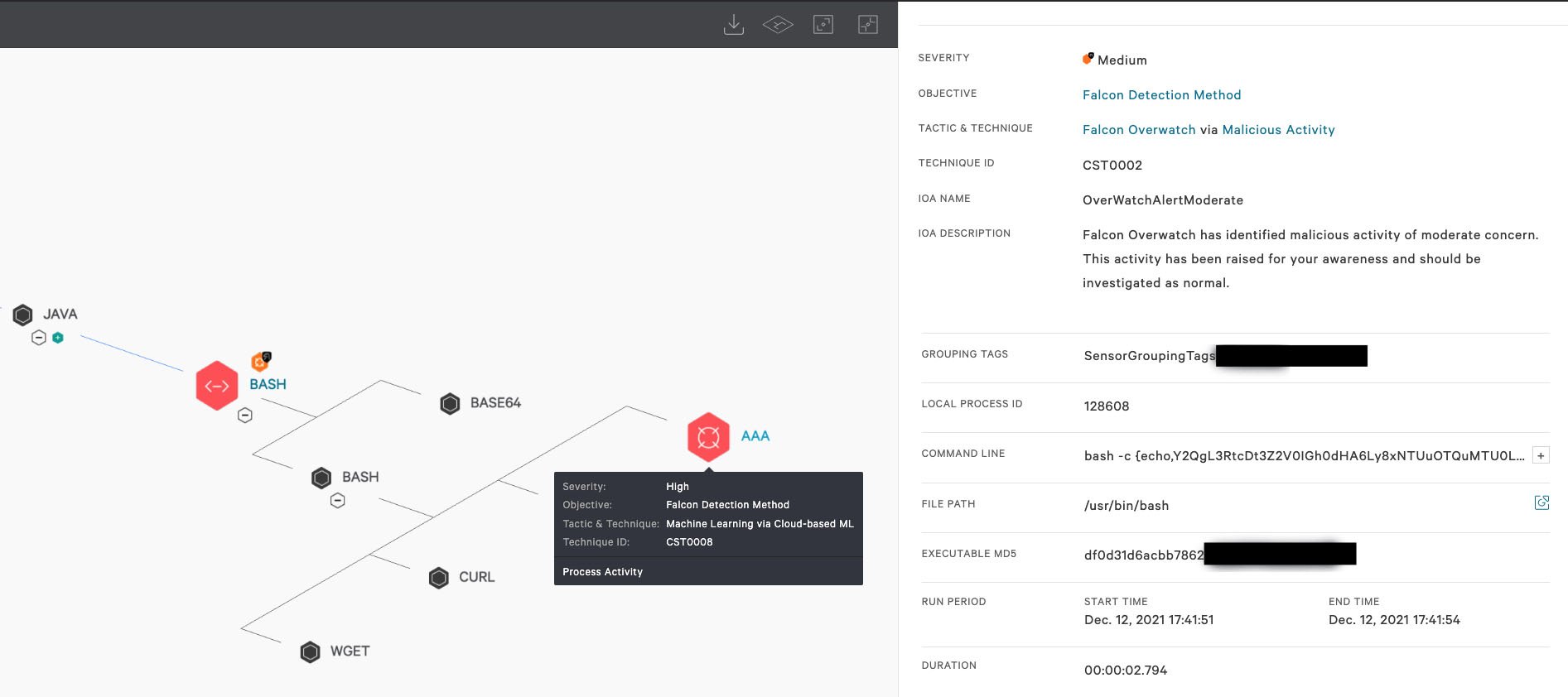 Figure 1. Screenshot displaying OverWatch notification on the malicious Bash process as well as ML detection on the subsequent downloaded payload (Click to enlarge)
Figure 1. Screenshot displaying OverWatch notification on the malicious Bash process as well as ML detection on the subsequent downloaded payload (Click to enlarge)Figure 1 shows successful post-exploitation activity as a result of the Log4j2 vulnerability. As we can see, the bash process under Java is responsible for utilizing the wget and cURL utilities to download the first-stage payload as denoted by AAA, which is successfully prevented from executing by Falcon’s on-sensor machine learning model. Of note, Falcon’s machine learning provided proactive coverage of the post-exploitation activity prior to the announcement of the Log4j2 vulnerability. In addition to machine learning prevention, the screenshot also shows the Falcon OverWatch team detecting and pushing an alert on the malicious bash process under Java, exemplifying the multi-layered approach CrowdStrike uses to protect our customers. IOAs are an important part of the strategy that Falcon employs when it comes to detecting threats, including ones recently deployed by attackers exploiting the Log4j2 vulnerability. This approach focuses on detecting the intent of what the attacker is trying to accomplish, regardless of the malware explicitly used in the attack. For example, the CrowdStrike Falcon® sensor was able to prevent multiple deployed threats using an existing IOA. By observing and focusing on the series of actions and tactics that adversaries attempt to conduct, CrowdStrike Falcon® can successfully detect and block new and unknown threats that exhibit similar behavior.
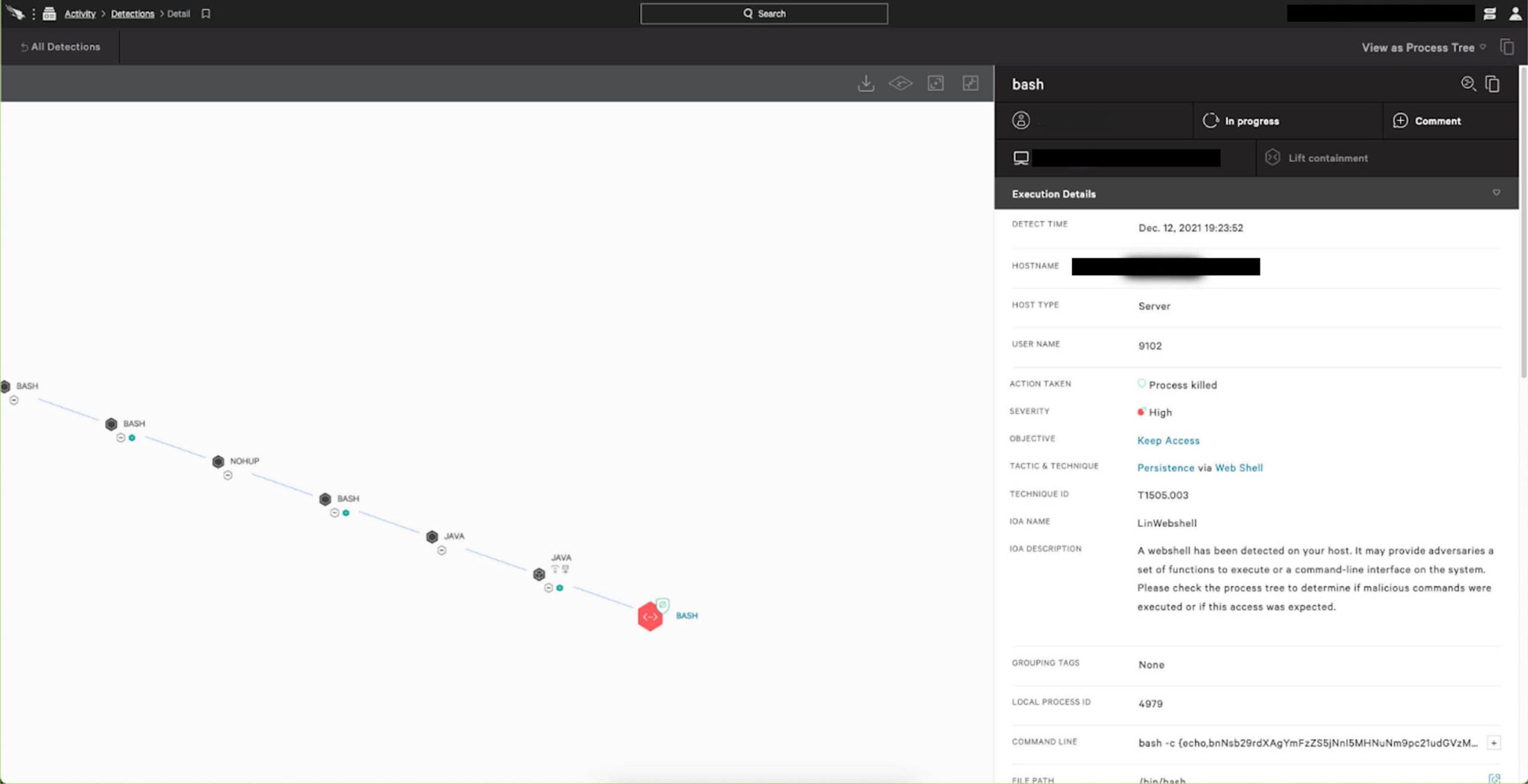 Figure 2. Screenshot demonstrating Falcon IOA successfully preventing Log4j2 post-exploit malicious activity (Click to enlarge)
Figure 2. Screenshot demonstrating Falcon IOA successfully preventing Log4j2 post-exploit malicious activity (Click to enlarge)Figure 2 shows a Falcon IOA successfully preventing and killing the same malicious activity before the process was able to pull the payload. As a consequence of this prevention, no subsequent malicious post-exploitation activity occurred on the endpoint. As IOAs can be deployed dynamically and don’t require sensor updates, the CrowdStrike Content Research & Response team was able to release more than two dozen new IOAs within hours of vulnerability disclosure, enhancing Falcon existing detection coverage against Log4j2 post-exploitation activities.
Whether it’s on Windows, Linux or macOS, the CrowdStrike Falcon® sensor leverages the power of behavioral detection, machine learning and advanced exploit prevention to protect customers and stop breaches.
Recommendations
- Organizations using Log4j2 are strongly encouraged to update the library to the latest Log4j2 (2.16.0) version published on December 14, 2021
- Audit the entire infrastructure, software applications and software supply chain for dependencies on Apache Log4j2 logging framework
- Ensure your CrowdStrike Falcon® prevention policies are configured per best practices
- Identify critical applications/services and remain up-to-date with vendor-specific recommendations as the situation develops
Note: CrowdStrike Falcon® customers can turn to our Support Portal for detailed instructions on how to identify and mitigate systems vulnerable to Log4j2/Log4Shell.
Additional Resources
- For more information about Log4Shell vulnerabilities, read the blog from the CrowdStrike Intelligence team.
- Find out how to stop adversaries targeting your industry — schedule a free 1:1 intel briefing with a CrowdStrike threat intelligence expert today.
- To request more information or speak with a CrowdStrike Services representative, complete and submit this form.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ to see for yourself how true next-gen AV performs against today’s most sophisticated threats.






![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1?wid=530&hei=349&fmt=png-alpha&qlt=95,0&resMode=sharp2&op_usm=3.0,0.3,2,0)