Today, we’re announcing new capabilities of CrowdStrike Falcon® Identity Protection to further strengthen our industry-leading identity threat detection and response (ITDR) technology and help customers secure their cloud-based identity environments from cyberattacks.
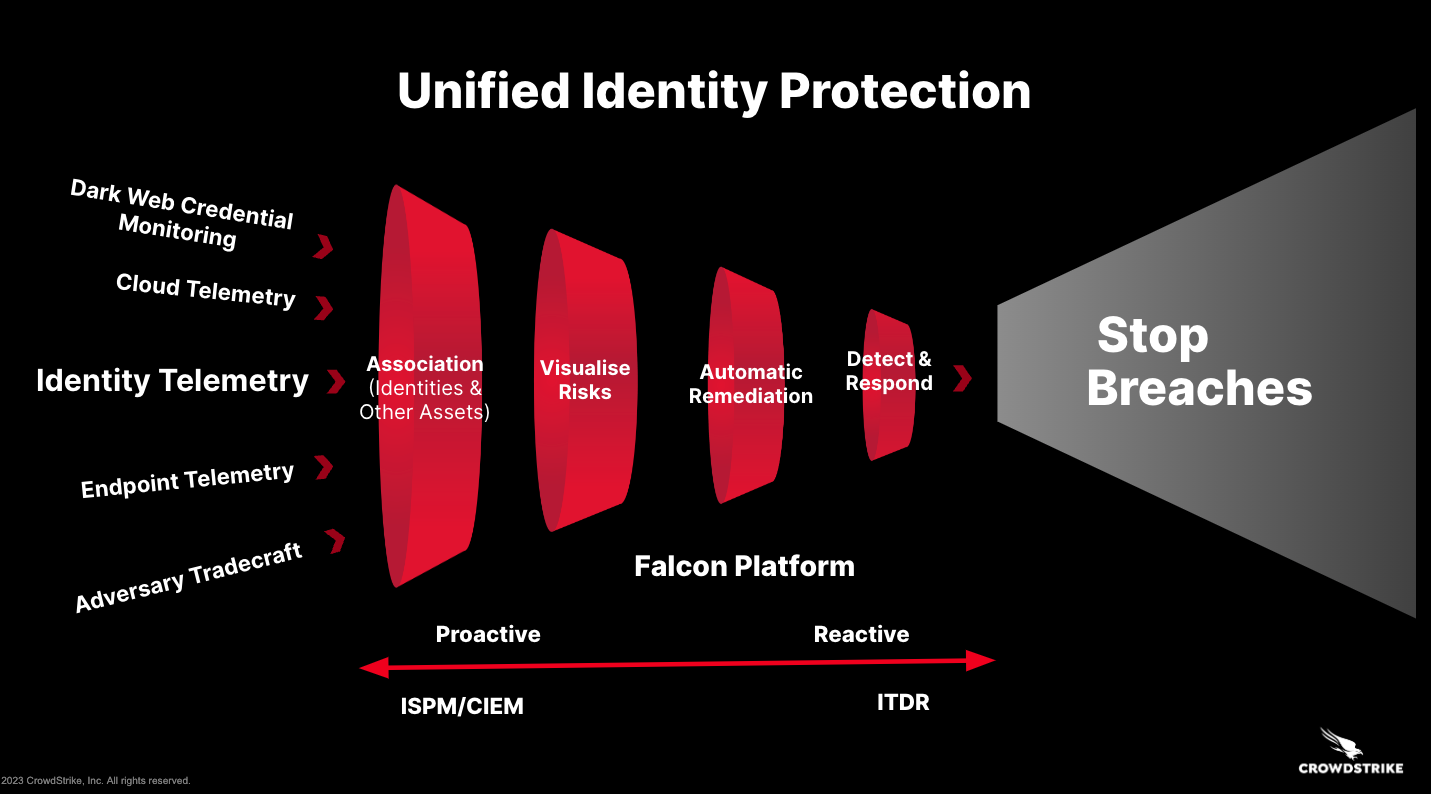
CrowdStrike pioneered ITDR to stop modern identity-based attacks with the industry’s first and only unified platform for identity, endpoint, cloud and data security powered by threat intelligence and adversary tradecraft — all delivered on a single agent.
Organizations can get up to 85% faster detections with this unified approach and also end up saving money by consolidating their SOC.* This approach contrasts with point products for ITDR and security solutions with disjointed architecture, which drive up cost and complexity without improving security outcomes.
Last month, our holistic approach to ITDR helped us win KuppingerCole’s Leadership Compass, Identity Threat Detection and Response (ITDR) 2024: IAM Meets the SOC. In the report, CrowdStrike was positioned furthest to the right of all vendors evaluated, demonstrating our continued leadership in identity security.
Innovations to Stop Identity Attacks
Cloud identity stores such as Microsoft Entra ID are the new target of opportunity. As such, customers are seeking a trustworthy, security-focused partner to protect these attack surfaces. Here are four product innovations to help secure your cloud-based identity providers.
1. Pioneering ITDR protection for cloud-based identity providers
Instantly detect and respond to identity-based attacks in Entra ID, Okta and Ping, including session hijacking and account takeovers. Oust adversaries by revoking live sessions and apply conditional access for legitimate users to securely log back in.
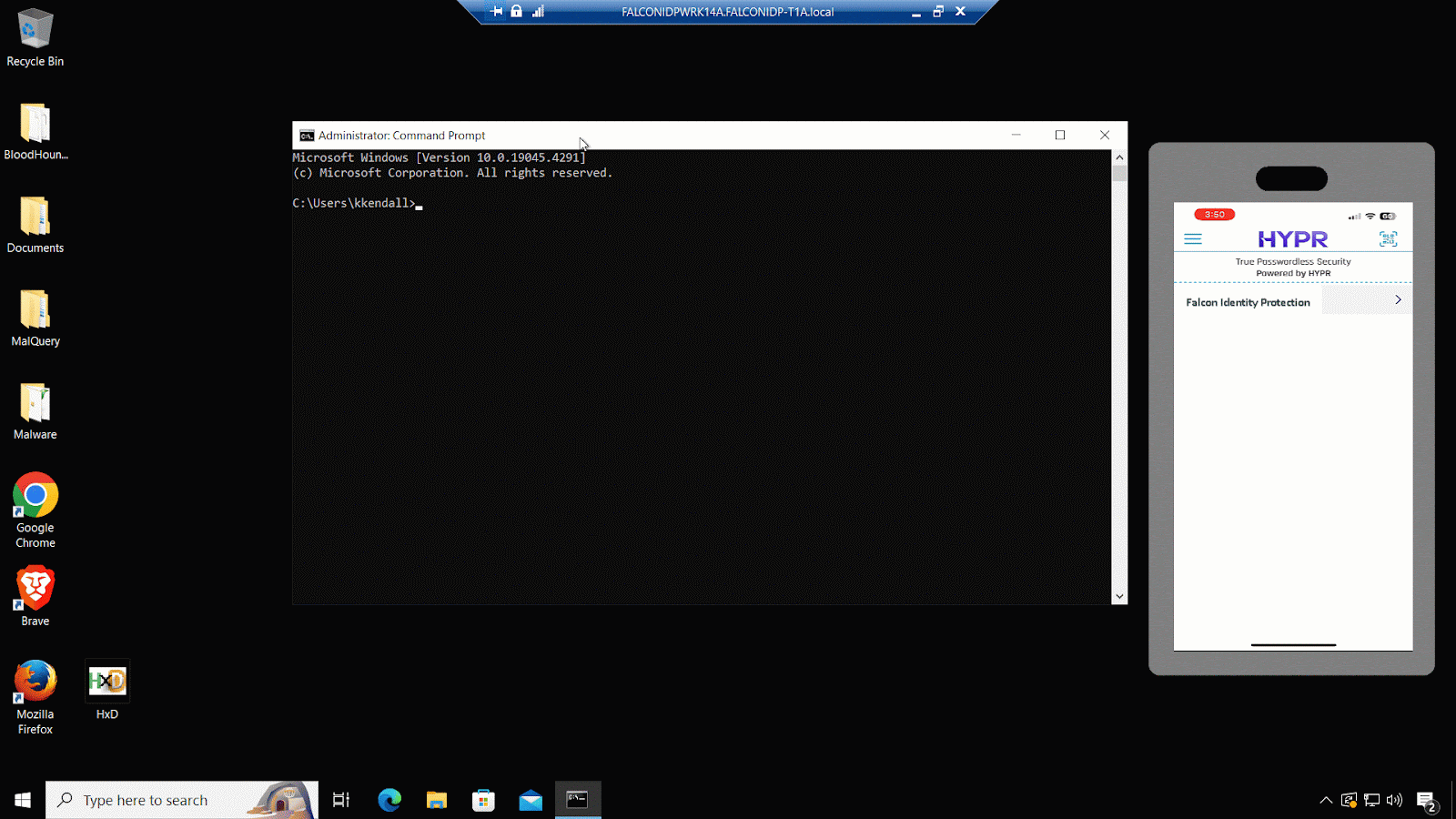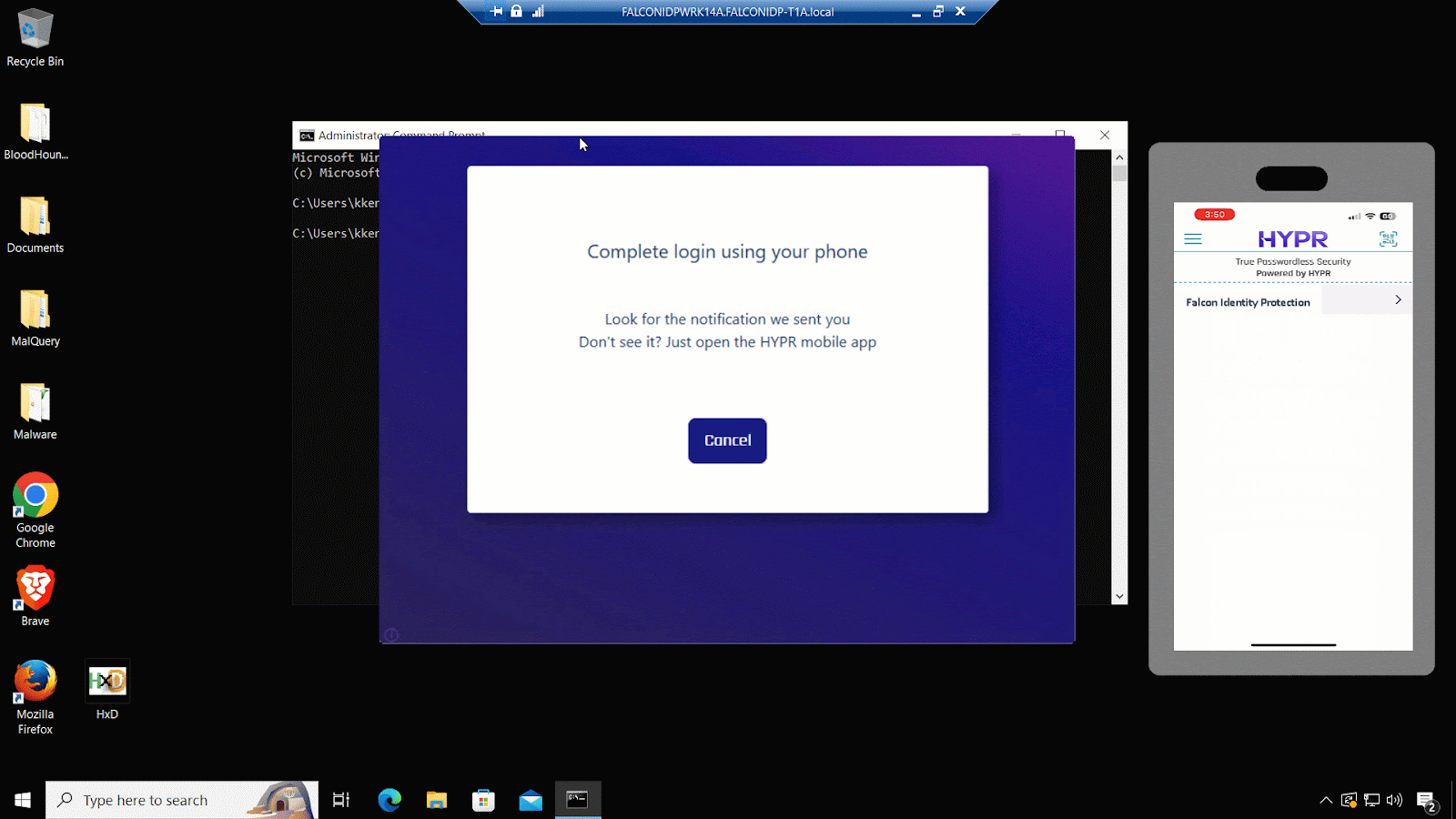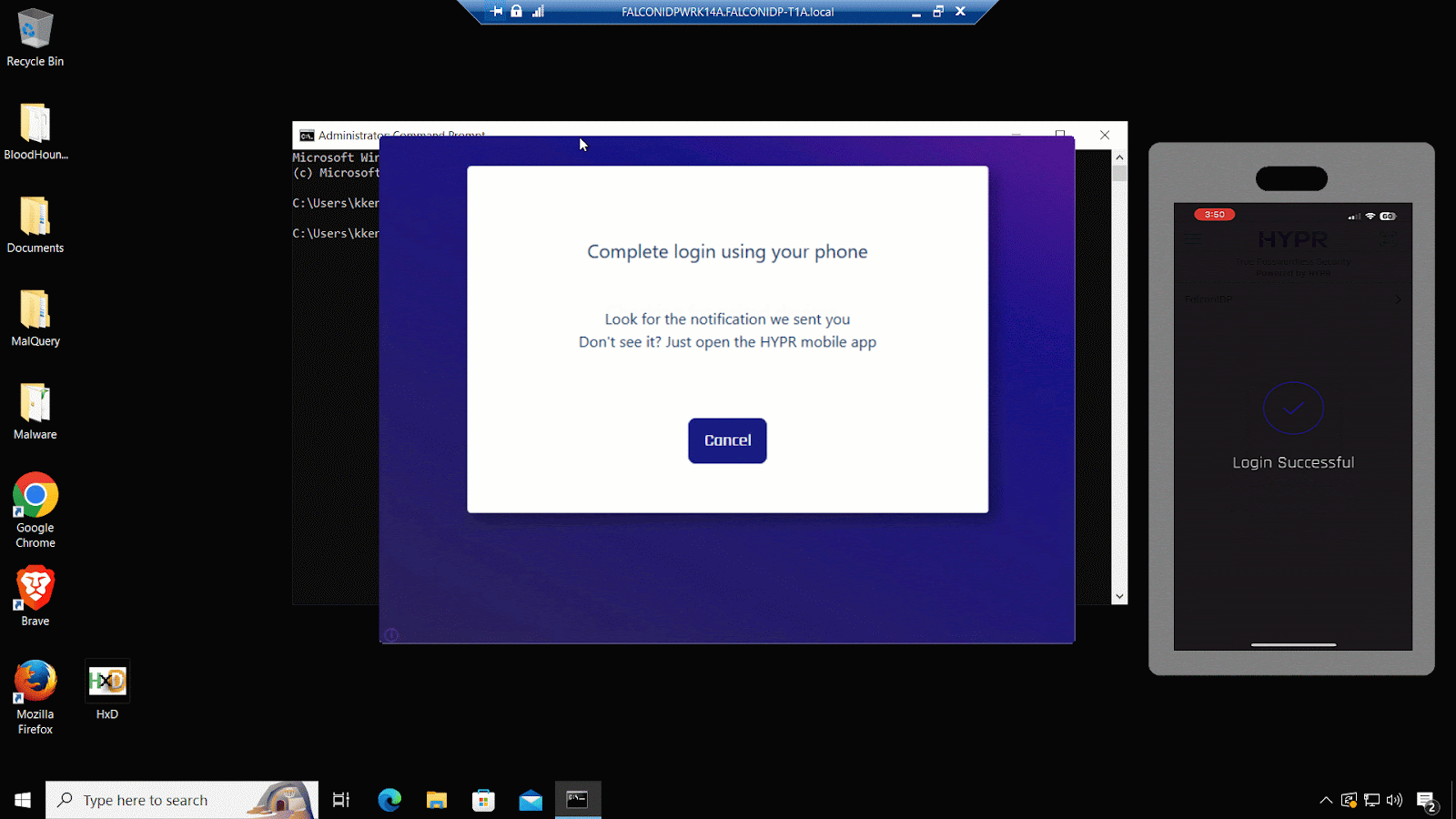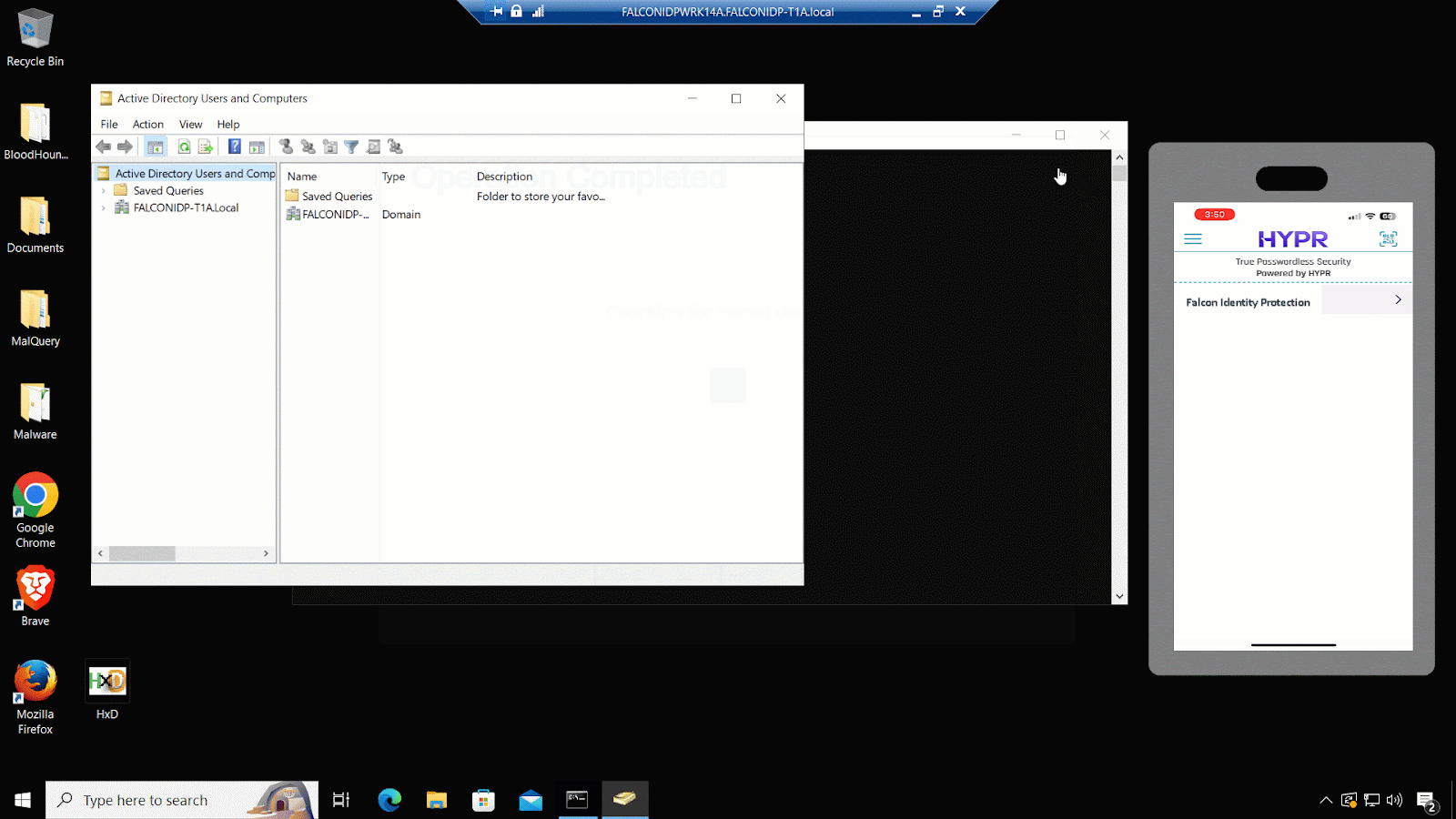
2. Native support for FIDO-based phishing-resistant multifactor authentication (MFA)
Reduce your identity attack surface and streamline your journey toward passwordless authentication. Falcon Identity Protection natively supports FIDO authentication options such as Hypr and Yubikey to mitigate the risk of remote hacking and phishing attacks.
3. Active Directory Audit to eliminate AD compliance point products
Protect against risky activity in AD — whether malicious or unintentional — by recording every change made in AD to rapidly understand and remediate potential gaps and eliminate point products for AD audit compliance.
4. Integration with Entra ID external authentication method (EAM) for real-time response across Microsoft identity environments
Take immediate action on identity detections across Microsoft cloud identity environments with support for new EAM actions in Entra ID. Building on existing workflow automation capabilities, this new integration will further extend risk-based conditional access to Entra ID, leveraging the power of the CrowdStrike Falcon® platform telemetry and threat intel to establish user and device trust in real time.
Visit CrowdStrike at Identiverse 2024
At Identiverse in Las Vegas this week? Stop by CrowdStrike booth #1300 to see Falcon Identity Protection in action and speak with one of our identity security experts about how these new product innovations can fortify your cloud identity stores.
Also, don’t miss CrowdStrike’s presentation at Tech Theater 3 (Pinyon) on May 29 at 5:40 p.m. to learn how to stop modern cyberattacks with unified identity protection.
Additional Resources
- Register for a complimentary Identity Security Risk Review.
- Check out the Identity Security Risk Review infographic.
- Stream the “COZY BEAR on the Prowl” CrowdCast.
- Visit the Falcon Identity Protection product page to learn more.
*These numbers are projected estimates of average benefits based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)
![Endpoint Protection and Threat Intelligence: The Way Forward [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/GK-Blog_Images-1)