Assessing the Sunburst Vulnerability with CrowdStrike

Introduction
As new vulnerabilities are announced every day, security teams are often called upon to quickly investigate and access any potential impact. With CrowdStrike’s detailed event data, customers get immediate, useful results through a number of search and reporting options. Specifically for the SolarWinds Sunburst vulnerability, CrowdStrike issued a tech alert that outlines multiple ways that the platform can be used to assess the impact of the vulnerability and collect information needed for efficient remediation. In this demonstration, we will look at a few of those use cases.
Video
Indicator Searches
The main Investigate menu provides access to standard searches for hunting suspect IP addresses, hashes, and domains. These easy to use searches can be leveraged anytime to hunt for specific indicators across the environment.
Custom Vulnerability Report
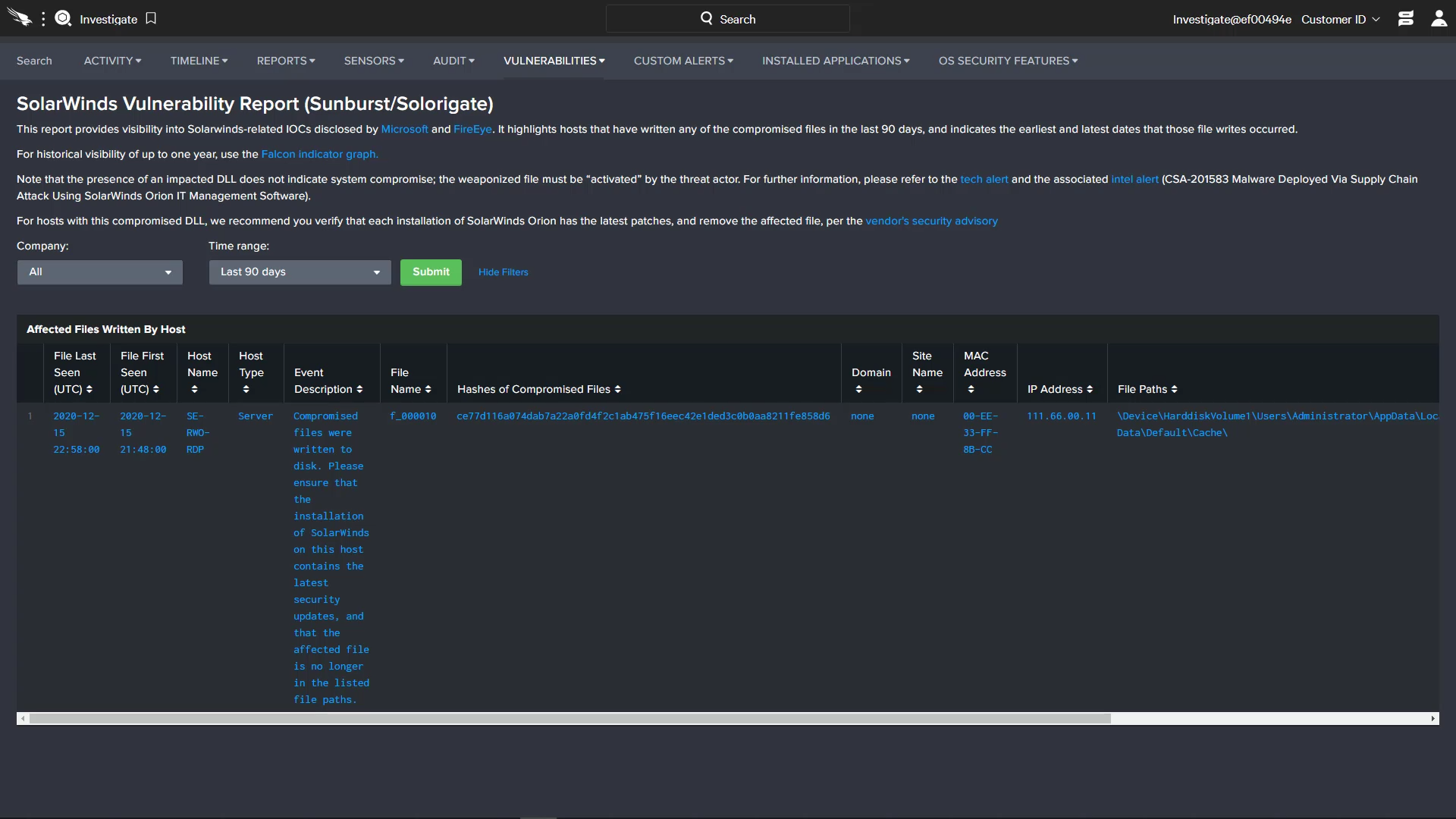
CrowdStrike has also built a custom report specifically for this high profile Sunburst / Solorigate exploit. Available from the Investigate app under the top Vulnerabilities menu, Falcon Insight customers can quickly see a report of all hosts that have written any of the compromised files over the last 90 days. While the presence of a file does not necessarily indicate that a system is compromised, it does highlight any systems that need to be verified for the latest patches and remediation steps.
Indicator Graph
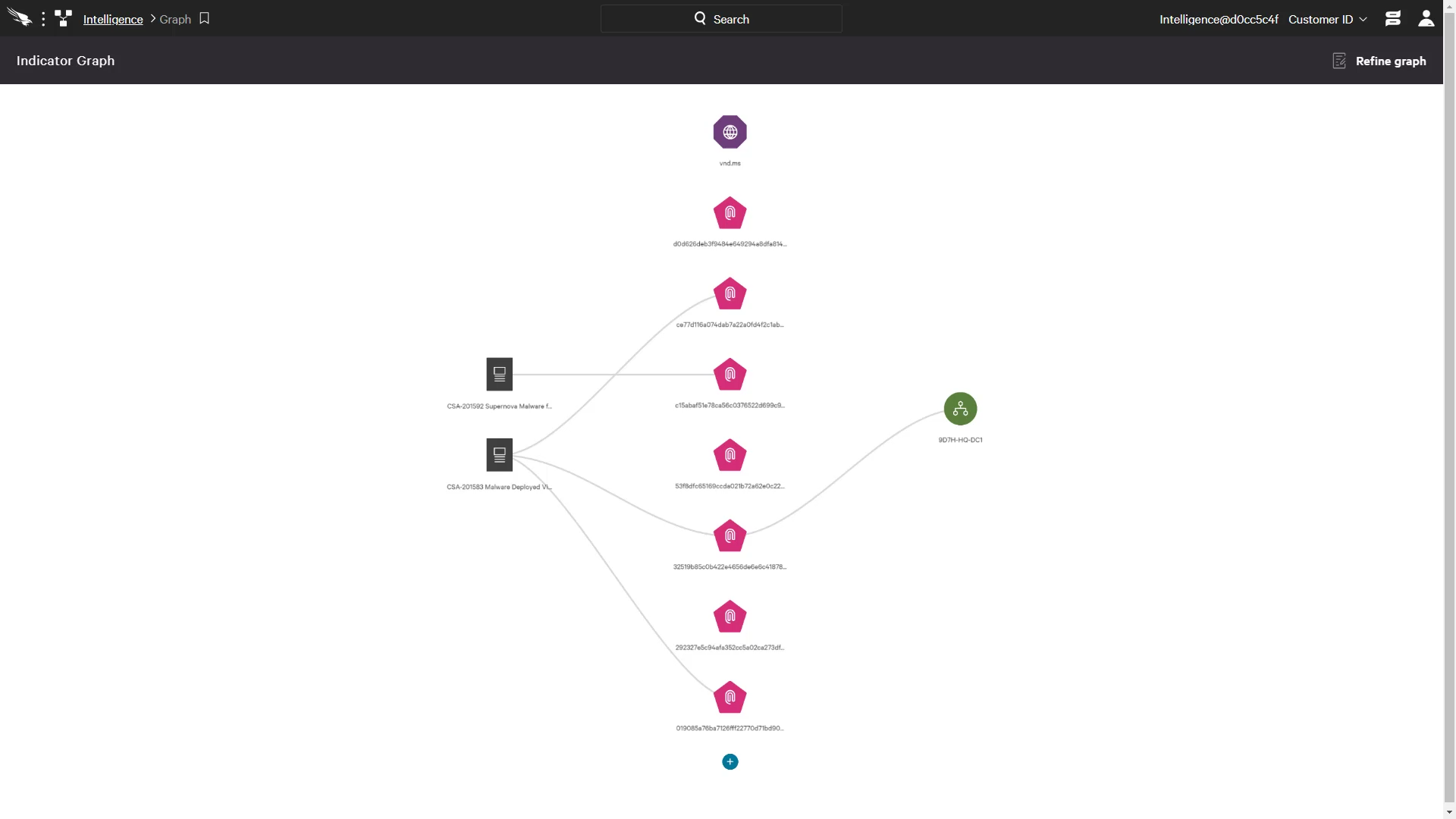
The CrowdStrike CrowdScrape extension for Chrome can be used to quickly scan sources for useful indicators, copy those indicators or graph them in the Falcon UI.

This indicator graph illustrates how a published domain and list of hashes map to CrowdStrike data points. On the left, is correlation to CrowdStrike intelligence reports while the right side reveals a single impacted host. There are also options to review the intelligence data or drill down on the host to access Host Management, Network Containment or Real Time Response.
Note: The option to create an indicator graph can also be found under “Intelligence -> Indicators”.
Conclusion
CrowdStrike understands that threat hunting, reliable indicators and intelligence reporting are critical assets when responding to a high priority security announcement. The Falcon platform is a powerful collection of host, event and intelligence data that can quickly be searched for accurate and reliable information when time is of the essence.


