How to Contain an Incident

Introduction
This document and video will define breakout time and a challenge for companies to quickly detect, understand and eradicate incidents in their environment to avoid a breach.
Video
Breakout Time
The 2018 Global Threat Report included our latest findings around the timing of an outbreak. On average, the time between initial access and the first lateral movement is 1 hour and 58 minutes. We call that Breakout Time.
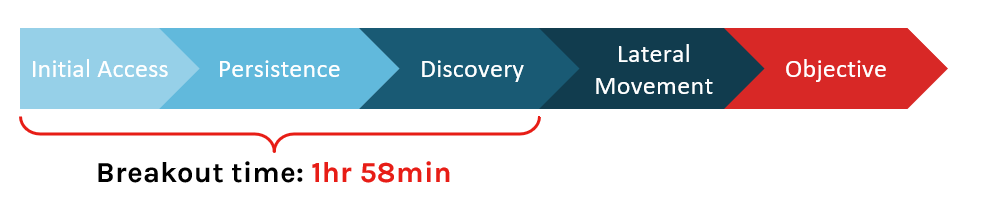
The 1-10-60 Challenge
The resulting challenge is to get ahead of the adversary and identify an any incidents before they become full scale breaches. That means detecting the threat, understanding it, and then eliminating it. By doing that in under 1 hour and 58 minutes, you can stop an attack before it spreads and causes real damage. Organizations need to hone tools and processes to be able to regularly achieve that goal.
By setting goals to detect incidents in under 1 minute, understand events within 10 minutes and eradicate threats within 60 minutes, we can prepare ourselves to beat the 1 hour and 58 minute mark with time to spare.
Falcon Insight Capabilities
CrowdStrike’s Falcon Insight offers a complete EDR solution providing the information, context and tools necessary for fast, effective incident response.
Detect
CrowdStrike’s single, lightweight endpoint agent communicates full event details to the cloud platform in real time. Fueled with that event data, the CrowdStrike UI provides a dashboard view with immediate visibility into the newest detections, malware incidents by host and malware incidents by user. Having awareness of the newest events within 1 minute is critical to meeting the breakout time challenge.
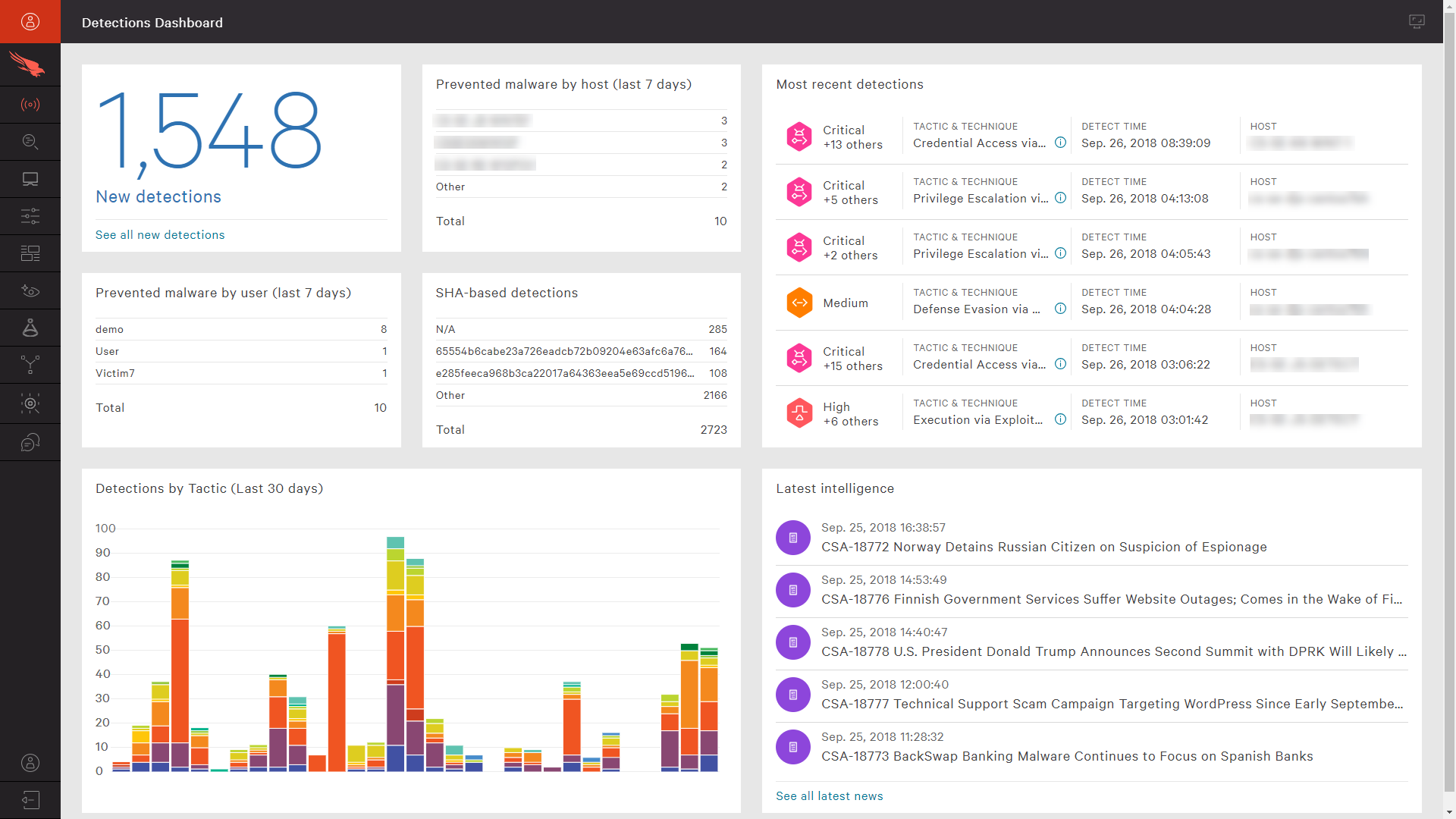
Understand
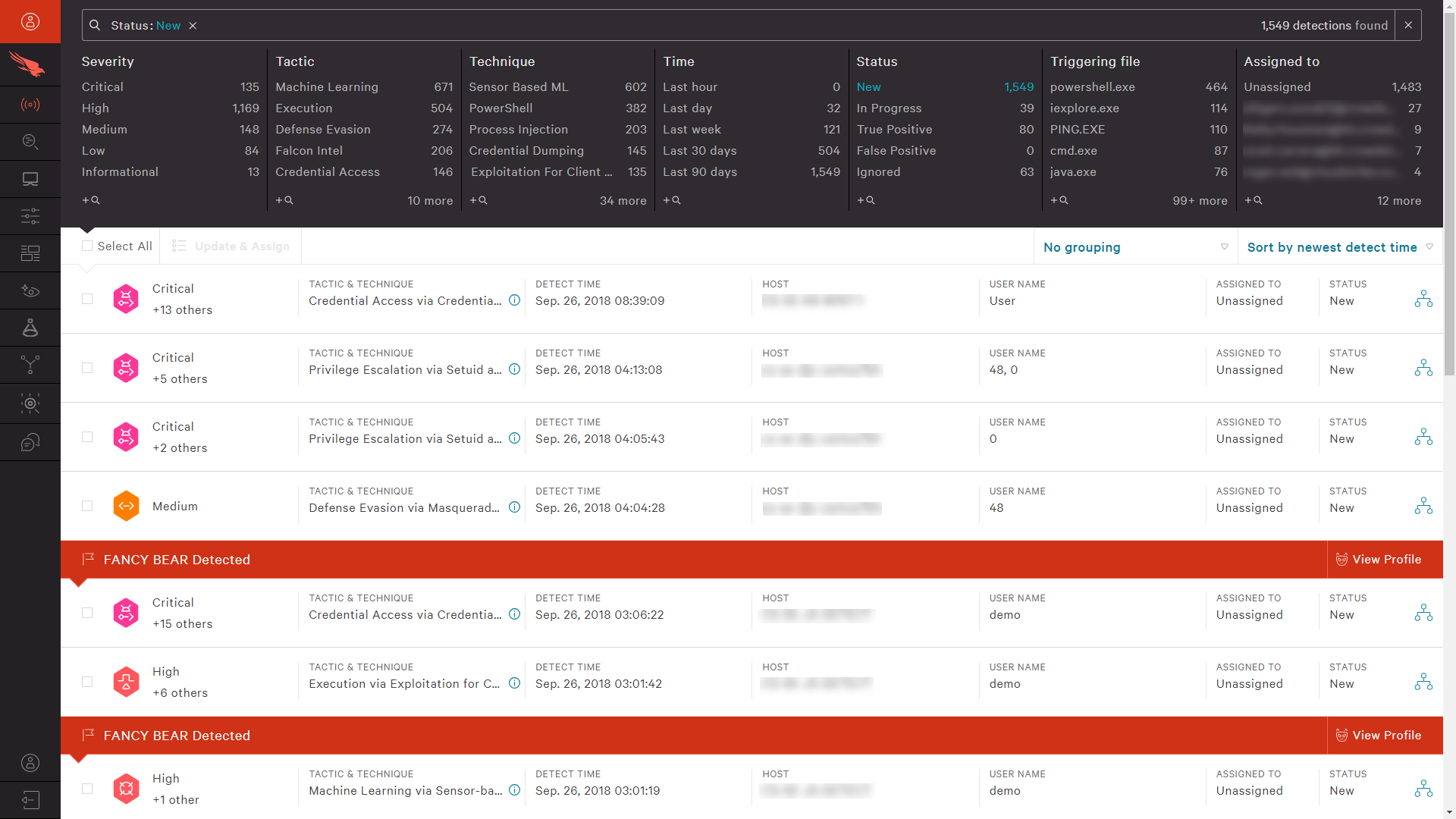
Looking into a specific event, CrowdStrike provides unparalleled context including the full event details, the parent processes, full command file details, and prevalence – all in the context of the MITRE framework. This level of insight helps you understand the event within 10 minutes so that you take quick, decisive remediation action.
Respond
Falcon Insight offers all of the information and tools needed to protect your environment and remediate impacted systems.
Network Containment helps ensure that impacted systems are unable to communicate with outside systems or risk lateral movement.
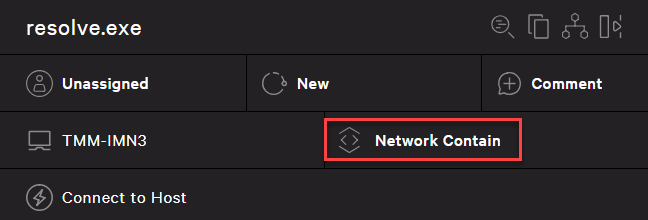
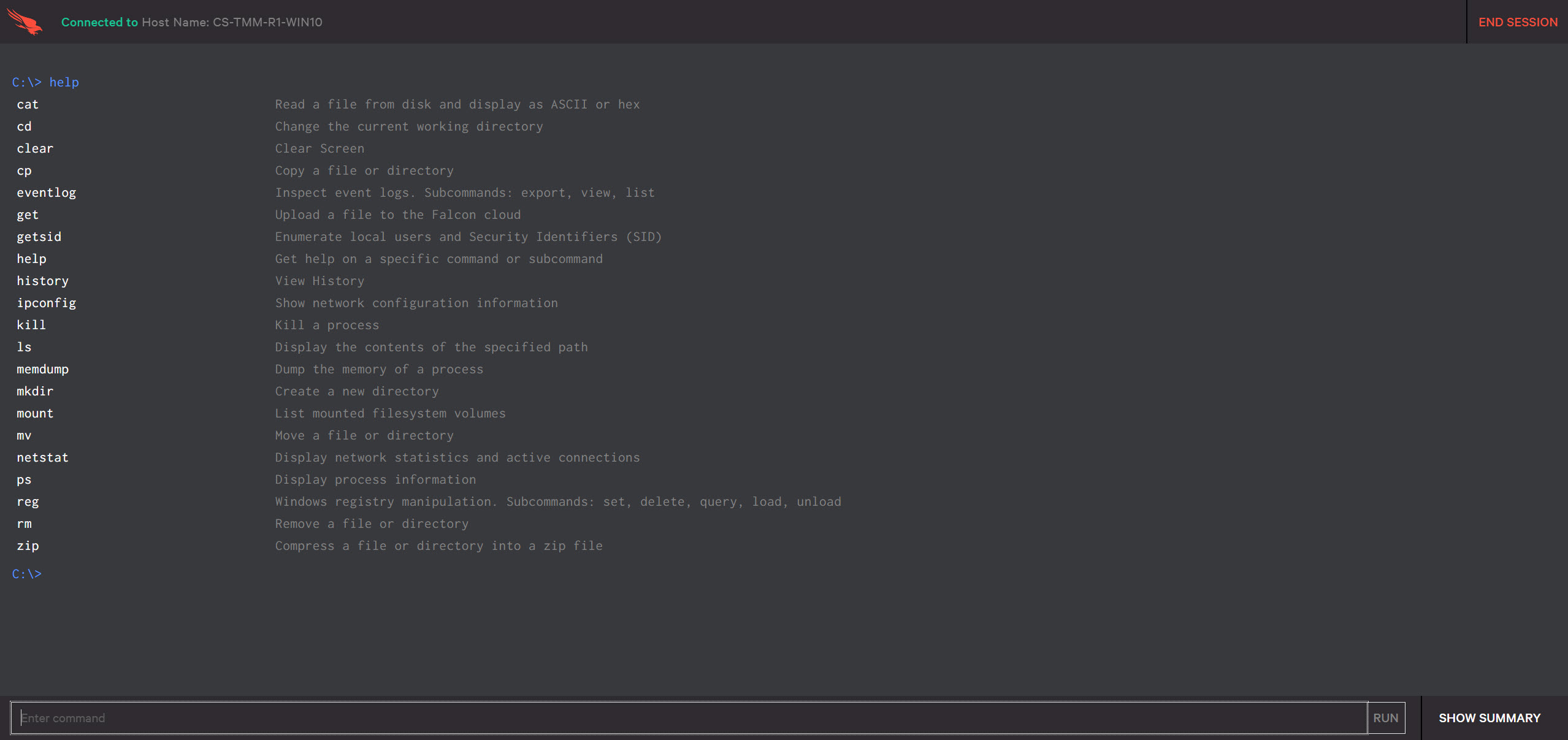
Real Time Response makes it possible to remotely remediate systems using the command below while minimizing the costs of downtime and lost productivity.
- Navigate the file system, upload or delete files, and perform many file system operations
- List running processes and kill processes
- Retrieve memory dumps, event logs, or any other files
- Show network connections
- Query, create, or modify registry keys
Conclusion
CrowdStrike’s Falcon Insight provides incident responders with a complete EDR solution that equips them with complete and timely data. By quickly detecting, understanding and remediating incidents, your organization can get ahead of breakout time and prevent an incident from becoming a breach.


