How to Generate Your First Detection

The greatest minds in cybersecurity are at Fal.Con in Las Vegas, Sept. 18-21.
Register now to build skills at hands-on workshops and learn from skilled threat hunters.
Introduction
In this document and video, you’ll see how to generate your first detection. You will also see how Falcon adds context to alerts, empowering the security admin to take appropriate corrective action.
Video
Prerequisites
Windows system with falcon sensor installed.
Generating a Test Alert
To generate an alert open cmd.exe clicking on the windows icon or hitting the windows button on your keyboard. Then type “cmd.”
In the Command Prompt window type
In the Command Prompt window, type the following commands:
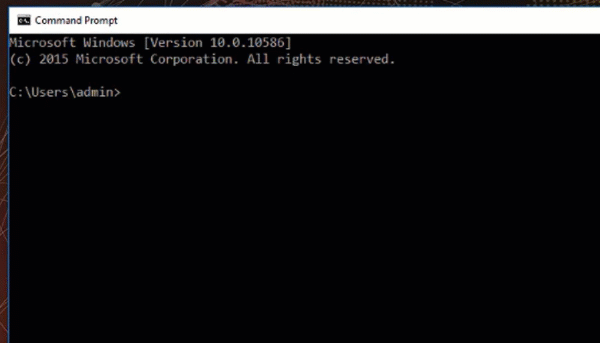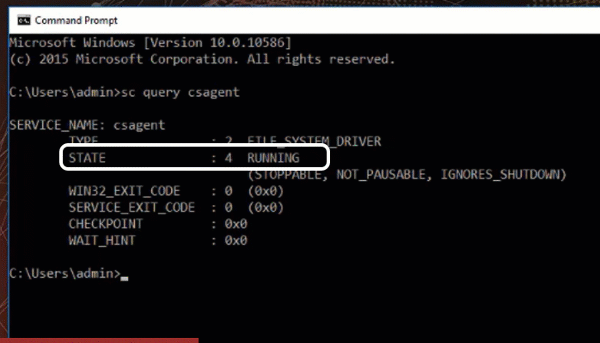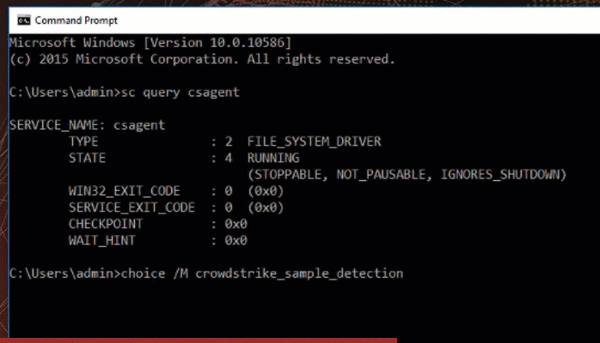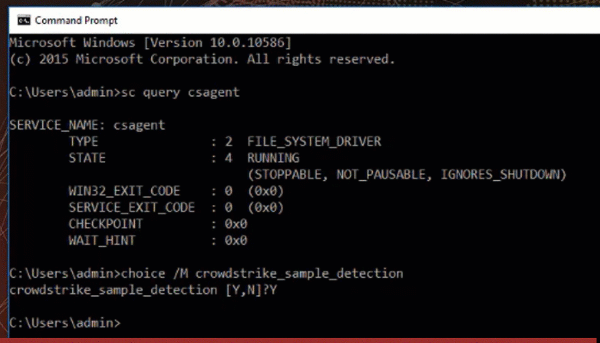
“Sc query csagent”
You should see a that the Falcon Agent is installed and running
Next type:
“choice /m crowdstrike_sample_detection”
Type “Y”
The Falcon User Interface
In the Falcon UI a new alert appears in the Activity App.
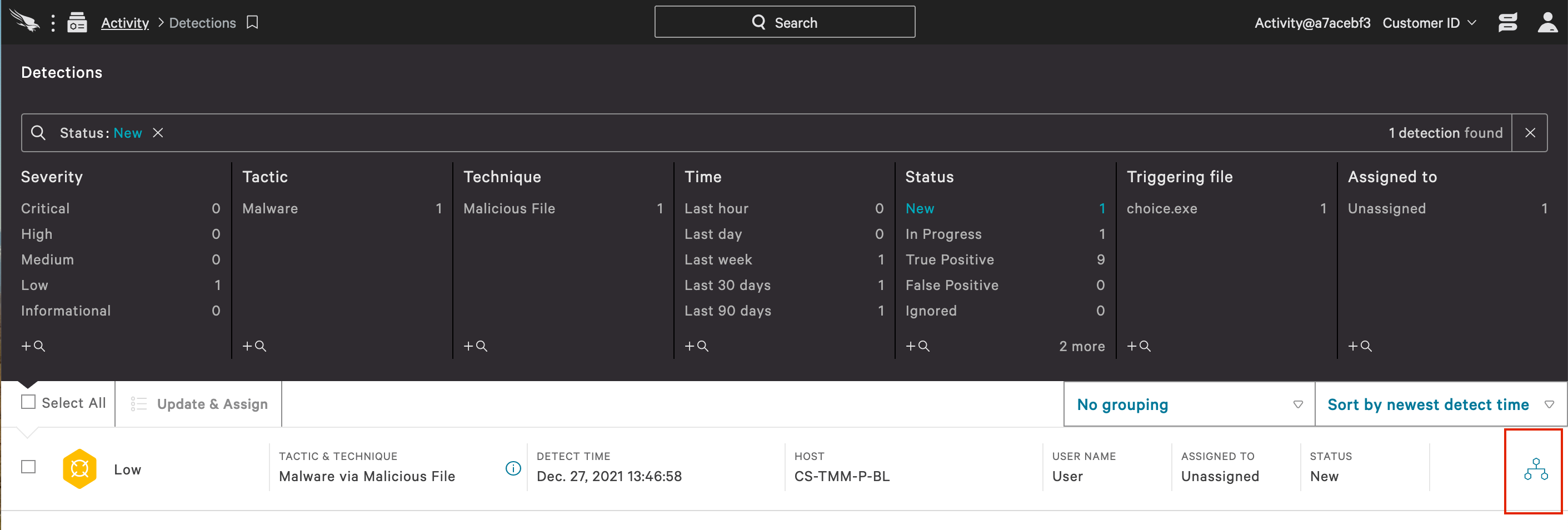
This alert is rated as “Low” and also has a Falcon icon associated with it. This indicates that Falcon OverWatch has flagged this activity as suspicious. Had this not been a test detection, it would have been accompanied by an email from the OverWatch team with additional detail.
Click on the alert expands the detection for additional details
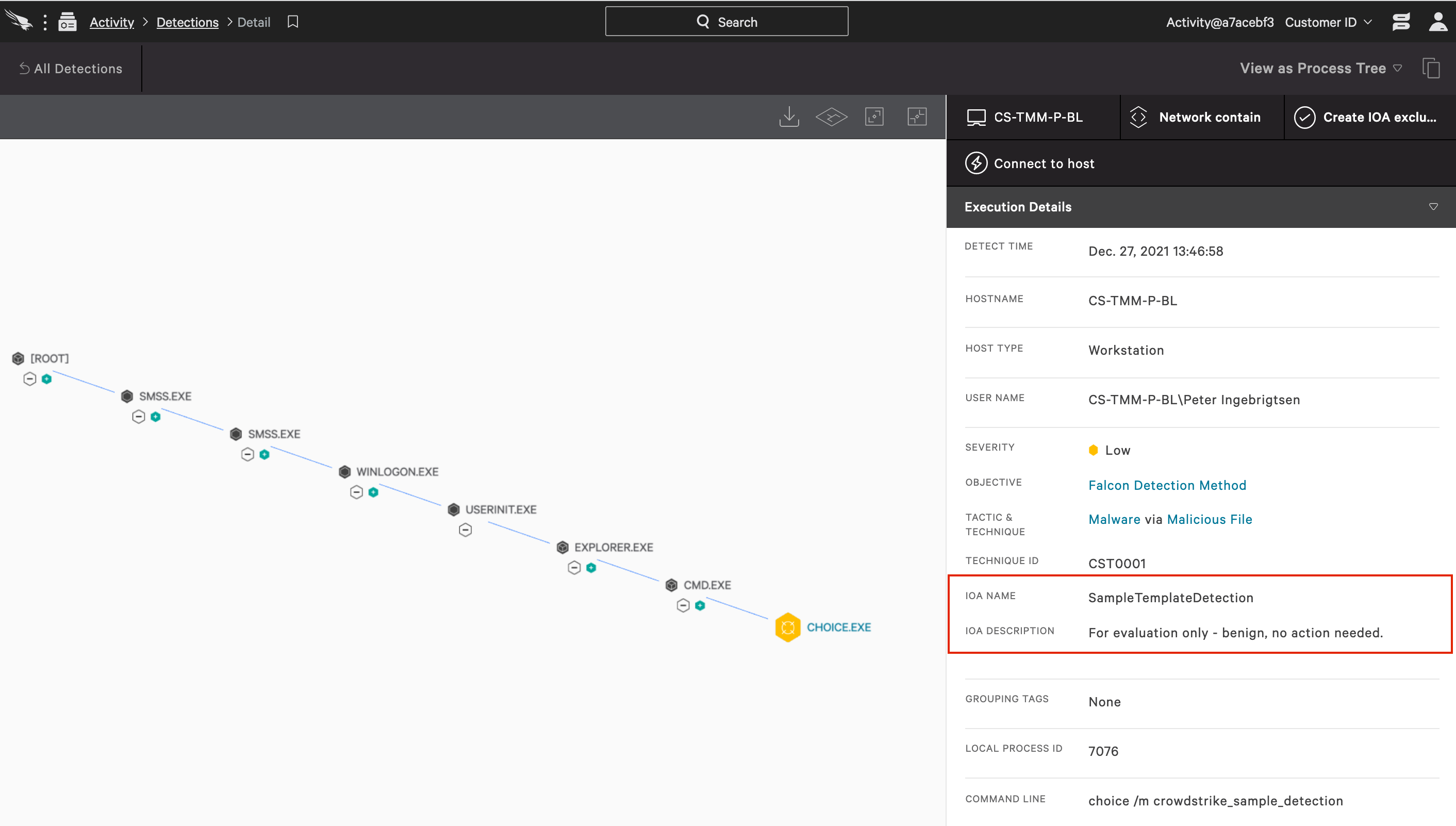
This additional detail is important to determine if a seemingly routine command is associated with everyday activity or part of a larger, malicious attack. Click on each node and watch the execution details pane on the right update to provide information on each executable in the process tree.
Conclusion
CrowdStrike Falcon® goes above and beyond to provide relevant information so that our customers have more information at their fingertips to quickly and effectively make important security decisions.
More resources
- CrowdStrike 15-Day Free Trial
- Request a demo
- Guide to AV Replacement
- CrowdStrike Products
- CrowdStrike Cloud Security