How to Prevent Ransomware with CrowdStrike Falcon® Endpoint Protection

Introduction
CrowdStrike Falcon offers protection against ransomware. This feature becomes increasingly valuable as the popularity of ransomware continues to rise. Our approach with this feature is to actually stop ransomware from infecting a system and encrypting its files. We believe a prevention approach is absolutely necessary because decryption is often impossible, and because nobody wants to pay the ransom or restore from backups.
CrowdStrike uses its endpoint sensor to detect ransomware behaviors and then terminates the offending process before it can accomplish its goal of encrypting files. This is done using CrowdStrike Indicator of Attack (IoA) patterns on the endpoint. These work both online and offline, and are effective against new variants and polymorphic variants of ransomware that often bypass legacy antivirus signatures.
Video
Step by step procedure to stop ransomware
Ransomware protection is enabled in Falcon by enabling three features.
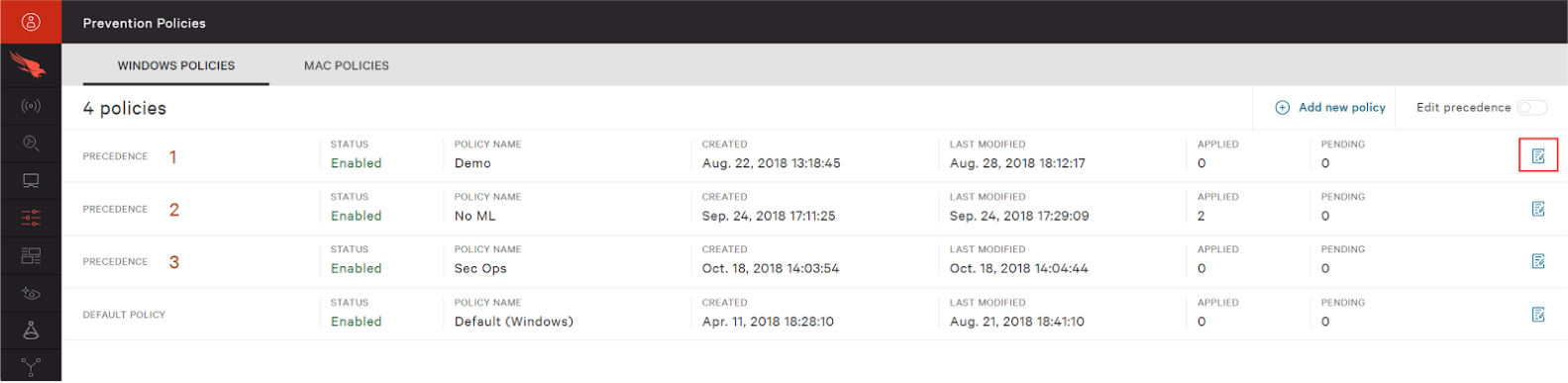
1. Go to https://falcon.crowdstrike.com
2. Login to Falcon UI
3. Navigate to Configuration App –> Prevention Policies then select the policy or policies that you’d like to enable prevention for by clicking on the edit policy icon.
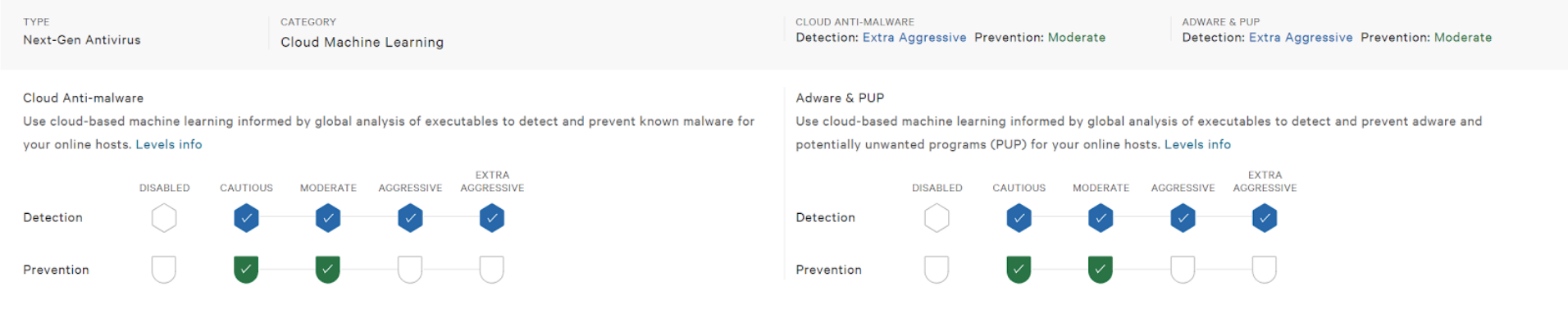
4. Enable Cloud Machine Learning – Anti-Malware Sensor Configuration. In this section the user is able to adjust detection and prevention for both File Attribution Analysis and File Analysis. Note that you will not not be able to enable prevention at a higher setting than detection. Select your desired settings and save any changes.
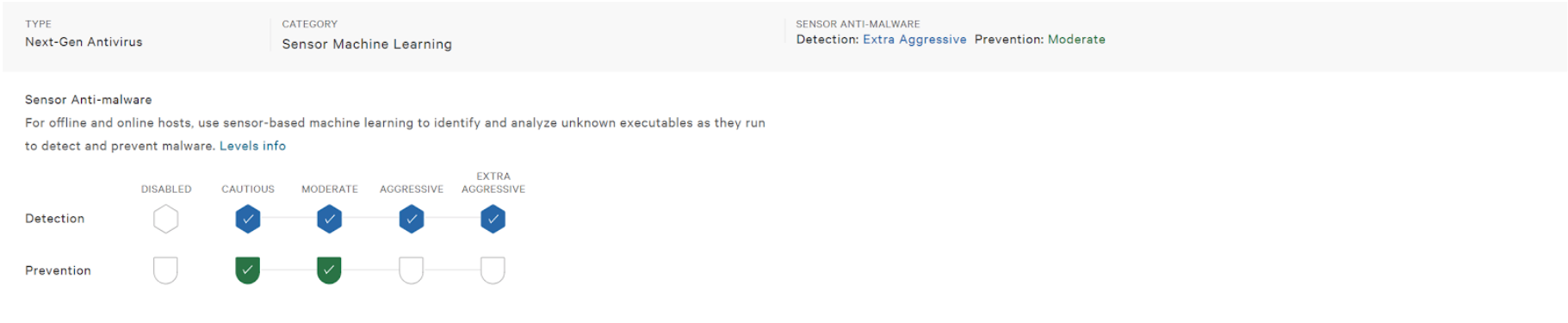
5. Machine Learning – On sensor ML provides protection when systems can’t be connected to the cloud, including protection against ransomware. To make changes in this section start first by enabling the “Next-Gen Antivirus” toggle. The remaining toggles will then become active and changes permitted.
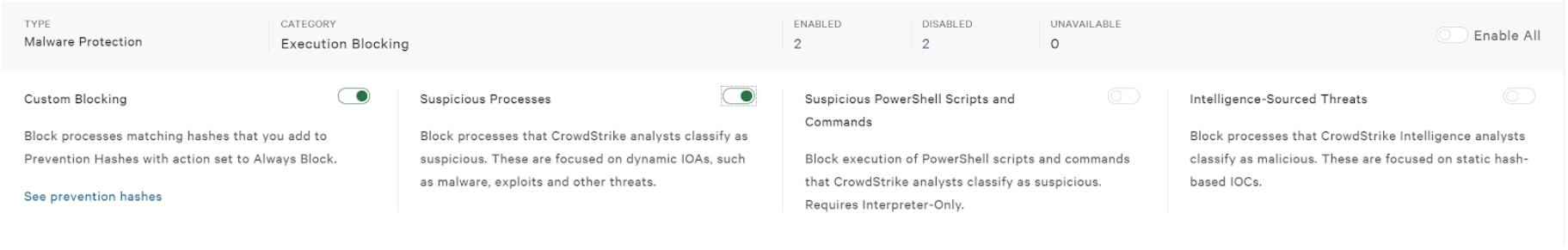
6. Suspicious Process Blocking – Falcon uses multiple detection capabilities to stop breaches not just machine learning or “artificial intelligence”. One of these is being able to identify suspicious processes and stopping them. This is useful in many types of malware and ransomware. To enable scroll down past Machine Machine learning and find the “Malware Protection – Prevent Suspicious Processes.”
NOTE: the “Custom Blocking” section allows IOCs to become block-able events. If this toggle is not enabled they are detection events.
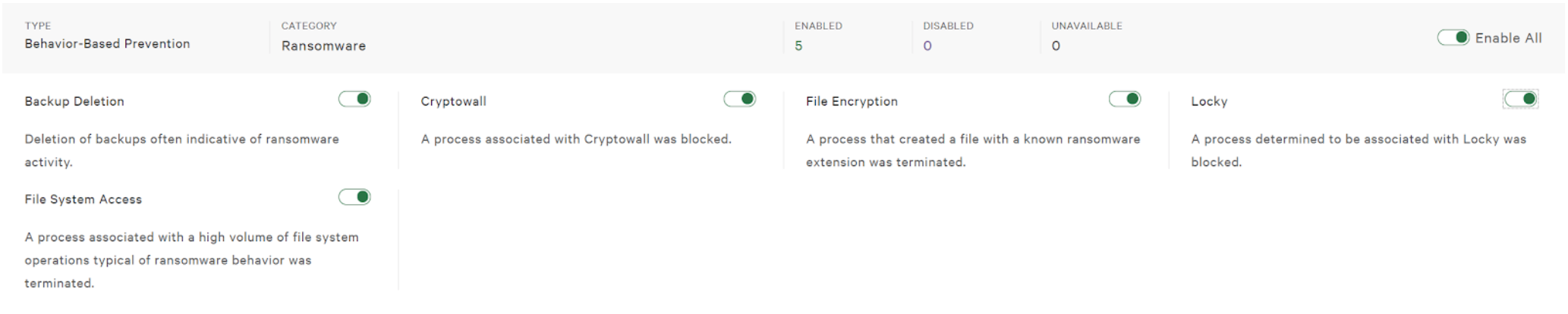
7. Behavior-Based Protection – Ransomware. This section enables detection of ransomware based on behaviors. We often refer to these as Indicators of Attack or IOA’s. CrowdStrike can identify 100’s of different indicators of attack and stop them in their tracks. Ransomware has some behaviors that are fairly typical such as backup deletion and file encryption. Using IOAs when these and other important contextual data is observed allows us to protect customers from ransomware even when other detection methods are bypassed. To enable Ransomware Prevention continue to scroll down on the prevention policy page. In the “Behavior-Based Prevention – Ransomware” section enable all toggles.
8. After enabling the features, click “save” in the upper right hand corner of the page to update all hosts in the policy.
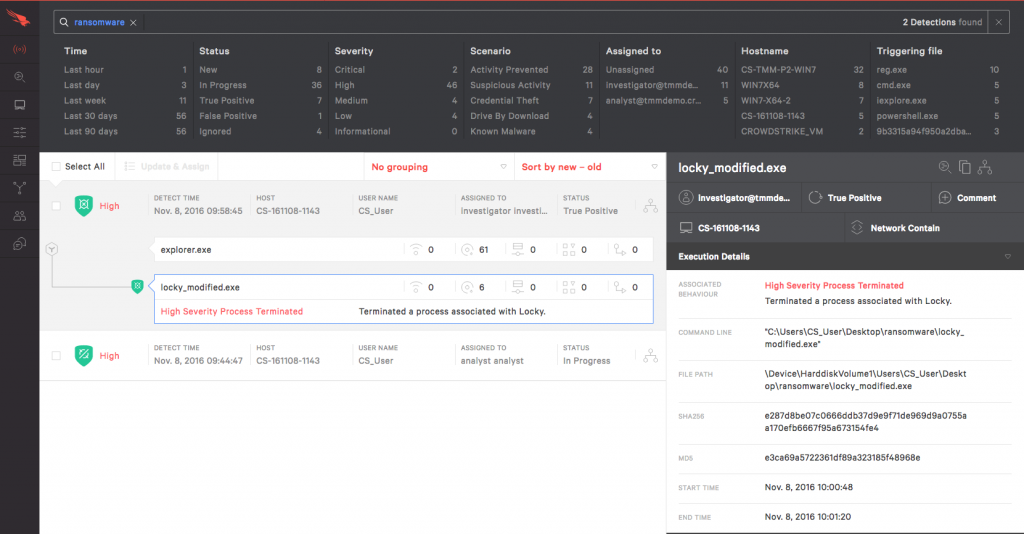
Falcon will stop the execution of the ransomware, but this will be invisible to the end user. There is no end user messaging or client side user interface elements. Validate that Falcon stopped the ransomware by looking in the admin console. Go into the Detections app and see an event near the top of the list. It will show that ransomware attempted to run and was stopped by Falcon.
Four technologies on the Falcon platform that stop WannaCry
WanaCry ransomware exploded onto the ransomware scene on 12 May 2017 with a mass campaign impacting organizations in many countries. This second variant of the ransomware has been leveraging the EternalBlue (MS-17010) vulnerability, released by the Shadow Brokers actors (see CSA-17082), in order to spread over victim networks via the Windows file sharing protocol, Server Message Block (SMB), following an initial infection. CrowdStrike Falcon® offers protection for this variant through two types of coverage. Falcon has a Machine Learning layer (at the Moderate Level) and a Behavioral IOA layer (Suspicious Process). To ensure this ransomware is prevented, the Prevention Policies must be turned on (enabled).
CrowdStrike customers are protected against this ransomware variant with current technology in the CrowdStrike Falcon® platform. Falcon’s advanced endpoint protection – with next-gen antivirus (NGAV) that incorporates machine learning augmented with behavioral analysis that looks for indicators of attack — detects suspicious behavior before an attack occurs. These prevention features block the WannaCry ransomware and keep it from executing and encrypting the target organization’s data.
Machine Learning in the Cloud
The broadest and easiest way to enable prevention of WannaCry in Falcon is to enable “Prevention” on the machine learning toggles. To do this Navigate to Configuration App –> Prevention Policies then select the policy or policies that you’d like to enable prevention for. Scroll down to the “Machine Learning – Anti-Malware Sensor Configuration” section and enable Prevention to “moderate”. By default your Detection settings must at least match your preventions settings.
On Sensor Machine Learning
When systems are not connected to the internet, Falcon can still provide against WannaCry and other threats via the On-Sensor Machine Learning engine. To enable on sensor machine learning again navigate to Configuration App –> Prevention Policies then select the policy or policies that you’d like to enable. Under the “Malware Protection – Anti-Malware Sensor Configuration” section enable the “On-sensor ML” protection to the moderate level.
Suspicious Process Blocking
In addition to machine learning capabilities Falcon also provides protection via Suspicious Process Blocking. When WannaCry executes and machine learning isn’t enabled there is an additional protection capability in place that will protect customers against infection. Falcon identifies the processes associated with this variant of ransomware as suspicious and blocks it. Enabling this capability is in the same section as machine learning; Configuration App –> Prevention Policies then select the policy or policies that you’d like to enable. Under the “Malware Protection -Prevent Suspicious Processes” section and ensure the “Prevent Suspicious Process” toggle is enabled.
Behavior-Based Prevention
Finally, most ransomware has some predictable behavior. We use this behavior to our advantage and provide protection capabilities in addition to machine learning. On the same Prevention Policy page scroll down to “Behavior-Based Protection – Ransomware” and enable the toggles in this section.
Don’t forget to save your changes to push the new policy out to all the hosts.
Conclusion
It is possible to stop ransomware, and Falcon makes it easy for you to do this. By enabling the ransomware protection features, all endpoints protected by Falcon will be protected. This is possible because CrowdStrike offers Indicator of Attack (IoA) patterns for ransomware. This kind of protection ensures that protection is available both when the client is online and offline, and the patterns are more persistent and durable than antivirus signatures – so you don’t need to bother with daily updates. This approach ensures that the protection is both effective and easy to use.