Detect the undetectable with CrowdStrike® Signal
CrowdStrike Signal uses self-learning to build AI models for every host in your environment, looking beyond the benign to identify unknown threats. It pinpoints subtle, early-stage threat activity and takes action earlier in the attack chain to catch threats others miss.


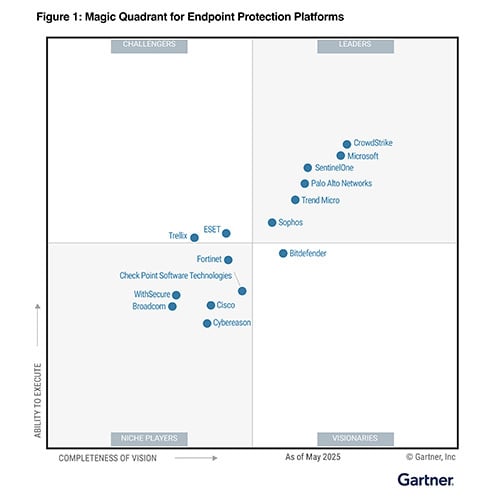
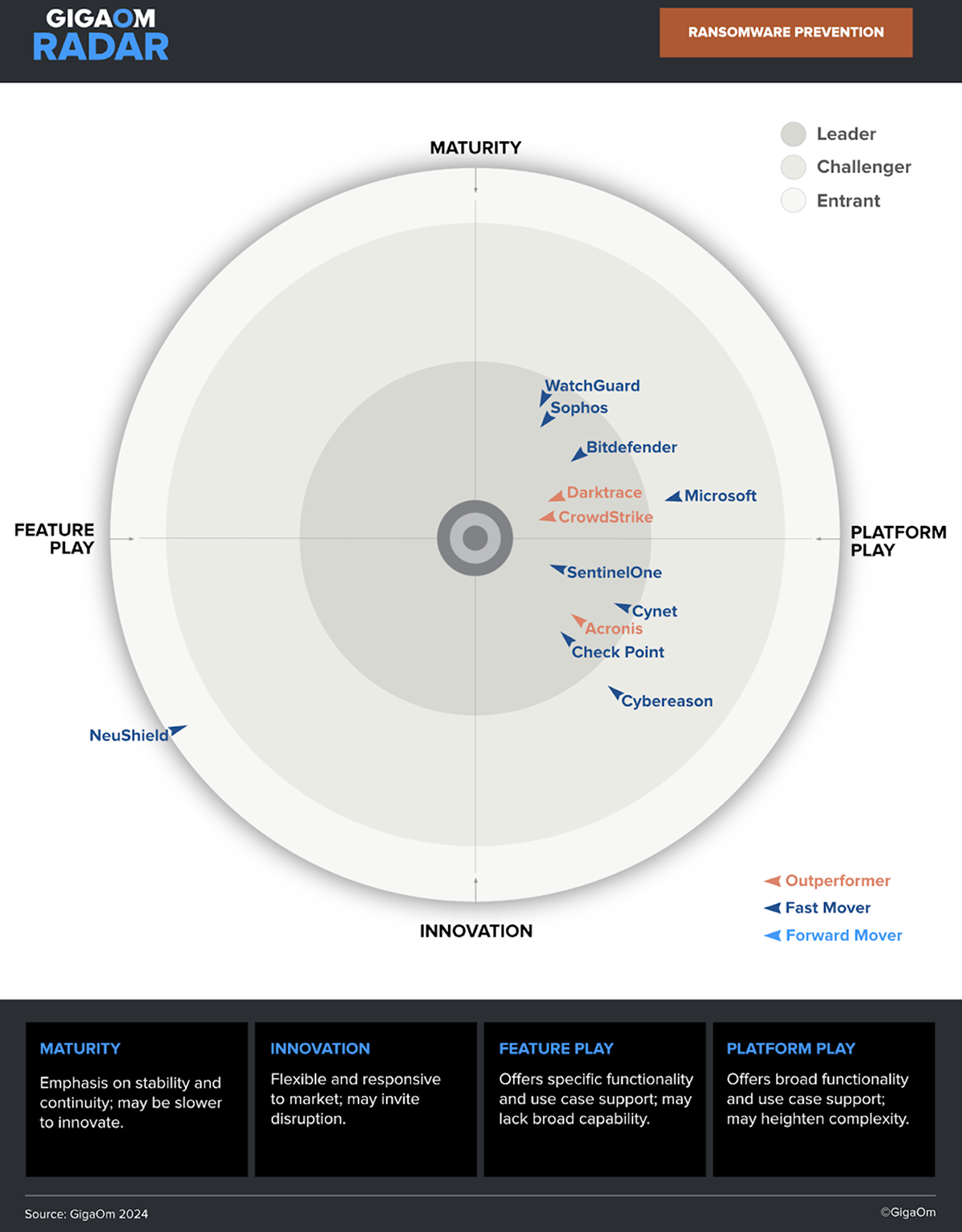
The leader in endpoint security
Only CrowdStrike combines AI-powered detection, adversary intelligence, and pioneering indicators of attack to identify and stop modern attacks — catching ransomware, lateral movement, and stealthy intrusions alike.
Stop cross-domain attacks
CrowdStrike extends protection beyond endpoints, unifying visibility across the CrowdStrike Falcon® platform to expose hidden threats that siloed tools miss. Expand protection with 10GB/day of third-party data ingest free via CrowdStrike Falcon® Next-Gen SIEM.


Precision detection meets autonomous response
CrowdStrike pioneered EDR to quickly stop advanced attacks. Our adversary-driven approach delivers precise, context-rich detections, while agentic AI automates detection triage, investigations, and response — cutting MTTR from hours to minutes.
One agent. Zero complexity. Full coverage.
Skip the complexity and tool sprawl. CrowdStrike’s single lightweight agent deploys in minutes and protects every major operating system, delivering instant security, fleet-wide visibility, and seamless scale.


AI that transforms security operations
CrowdStrike® Charlotte AI™ uses generative and agentic AI to act with the instincts of a seasoned analyst — crafting queries, building workflows, and responding autonomously with accuracy and speed. It’s like having your best security analyst on every alert, 24/7.
Customer Stories
See why organizations trust CrowdStrike Endpoint Security.
What's new
22024 SE Labs Enterprise Advanced Security (EDR) Ransomware Test
3These numbers are projected estimates of average benefits based on recorded metrics provided by customers during pre-sale motions that compare the value of CrowdStrike with the customer’s incumbent solution. Actual realized value will depend on individual customer’s module deployment and environment.
4Results are from IDC Business Value Report. Individual results may vary by customer.
5CrowdStrike 2025 Threat Hunting Report